ON THIS PAGE
IEEE 1588v2 PTP Boundary Clock Overview
The IEEE 1588v2 standard defines the Precision Time Protocol (PTP), which is used to synchronize clocks throughout a network. The standard describes the PTP boundary clock’s hierarchical primary/client architecture for the distribution of time-of-day.
IEEE 1588v2 PTP Boundary Clock
Starting with Junos OS Release 17.3R1, IEEE 1588v2 boundary clock is supported on QFX10002 switches. An IEEE 1588v2 boundary clock has multiple network connections and can act as a source (primary) and a destination (client) for synchronization messages. It synchronizes itself to a best primary clock through a client port and supports synchronization of remote clock clients to it on primary ports. Boundary clocks can improve the accuracy of clock synchronization by reducing the number of 1588v2-unaware hops between the primary and the client. Boundary clocks can also be deployed to deliver better scale because they reduce the number of sessions and the number of packets per second on the primary.
The boundary clock intercepts and processes all PTP messages
and passes all other traffic. The best primary clock algorithm (BMCA)
is used by the boundary clock to select the best configured acceptable
primary clock that a boundary client port can see. To configure a
boundary clock, include the boundary statement at the [edit protocols ptp clock-mode] hierarchy level and at least
one primary with the master statement and at least one
client with the slave statement at the [edit protocols
ptp] hierarchy level.
ACX5448 router supports PTP boundary clocks for phase and time synchronization using IEEE-1588 Precision Timing Protocol (PTP). The ACX5448 router supports the following features:
PTP over IPv4 (IEEE-1588v2)
PTP ordinary and boundary clocks
One step clock mode operation for PTP Primary
10Mhz and 1PPS output for measurement purpose
All PTP packets uses the best-effort queue instead of network control queue.
If clksyncd-service restart is initiated, then the show ptp lock status detail CLI command output of Clock
reference state and 1pps reference state fields shows
incorrect information. The following is a sample of output for show ptp lock status detail:
user@host> show ptp lock-status detail Lock Status: Lock State : 5 (PHASE ALIGNED) Phase offset : 0.000000010 sec State since : 2018-11-22 00:38:56 PST (00:10:18 ago) Selected Master Details: Upstream Master address : 12.0.0.1 Slave interface : xe-0/0/20.0 Clock reference state : Clock locked 1pps reference state : Clock qualified
Figure 1 illustrates two boundary clocks in a network in which the clock flow is from the upstream node (BC-1) to the downstream node (BC-2).
This figure also applies to MX Series routers and QFX Series switches.
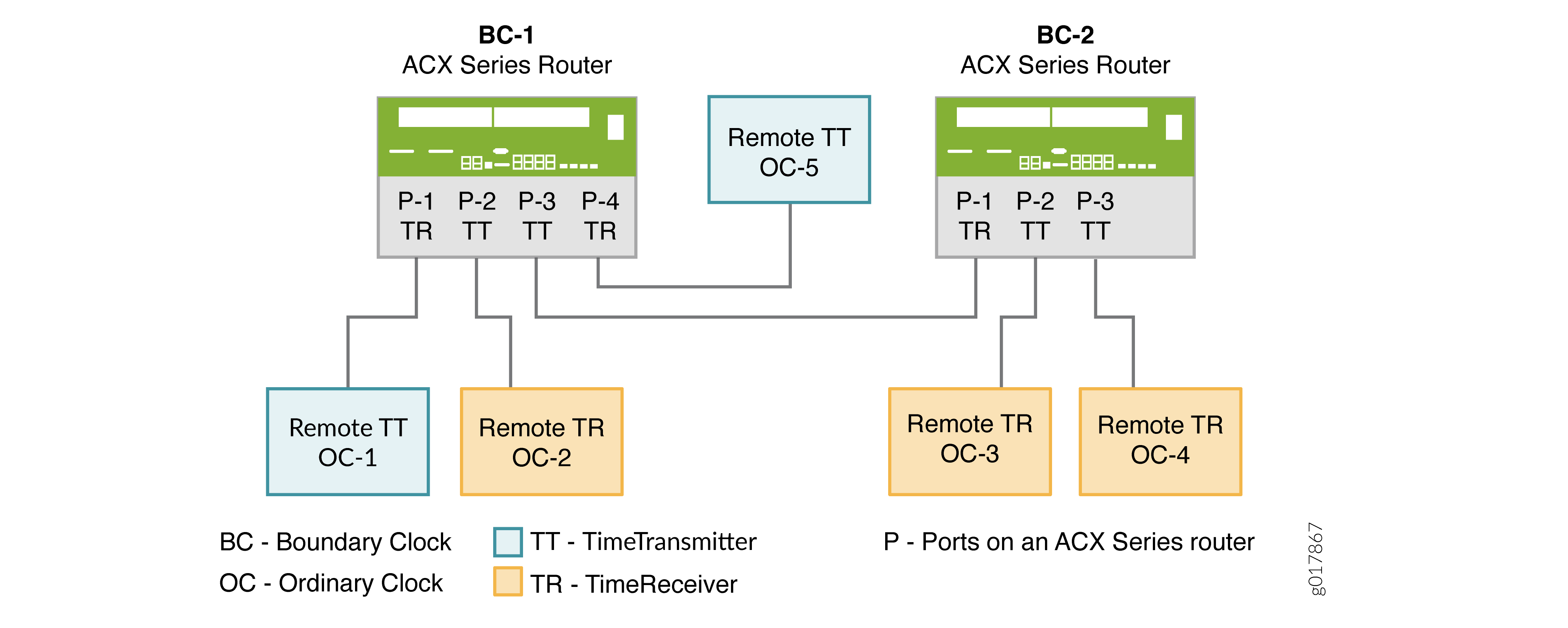
The first boundary clock—BC-1—has four ports. Each port is configured as follows:
BC-1 P-1 and BC-1 P-4 are boundary client ports connected to two reference clocks—OC-1 and OC-5. The reference clocks are included as the clock sources in the client port configurations. From the packets received on the client ports, BC-1 selects the best primary, synchronizes its clock, and generates PTP packets, which are sent over the primary ports—BC-1 P-2 and BC-1 P-3—to the downstream clients.
BC-1 P-2, a primary port, is connected to OC-2, an ordinary remote client. OC-2 is included as a clock client in BC-1 P-2’s primary configuration, and so receives PTP packets from BC-1 P-2.
BC-1 P-3, a primary port, is connected to BC-2 P-1, a remote boundary client port. In this situation, the primary port—BC-1 P-3—is included as a clock source in the configuration of the boundary client port—BC-2 P-1. In addition, the boundary client port—BC-2 P-1—is included as a clock client in the configuration of the primary port—BC-1 P-3. With this configuration, the boundary client—BC-2 P1—receives PTP packets from BC-1 P3.
The second boundary clock—BC-2—has three ports. Each port is configured as follows:
BC-2 P-1 is a boundary client port connected to the upstream primary port—BC-1 P3. As described previously, BC-2 P-1 receives PTP packets from BC-1 P3. The primary ports—BC-2 P-2 and BC-2 P-3—synchronize their time from the packets received from BC-2 P1.
BC-2 P-2 and BC-2 P-3, boundary primary ports, are connected to ordinary remote slaves—OC-3 and OC-4. OC-3 and OC-4 are included as clock clients in the configuration of the primary ports—BC-2 P2 and BC-2 P-3. Both slaves receive PTP packets from the primary boundary port to which they are connected.
In this example, the boundary clock synchronizes its clock from the packets received on its client ports from the upstream primary. The boundary clock then generates PTP packets, which are sent over the primary port to downstream clients. These packets are timestamped by the boundary clock by using its own time, which is synchronized to the selected upstream primary.
Clock Clients
A clock client is the remote PTP host, which receives time from the PTP primary and is in a client relationship to the primary.
The term client is sometimes used to refer to the clock client.
An device acting as a primary boundary clock supports the following types of downstream clients:
Automatic client—An automatic client is configured with an IP address, which includes the subnet mask, indicating that any remote PTP host belonging to that subnet can join the primary clock through a unicast negotiation. To configure an automatic client, include the subnet mask in the
clock-client ip-addressstatement at the [edit protocols ptp master interface interface-name unicast-mode] hierarchy level.Manual client—A manual client is configured with the
manualstatement at the [edit protocols ptp master interface interface-name unicast-mode clock-client ip-address local-ip-address local-ip-address] hierarchy level. A manual client does not use unicast negotiation to join the primary clock. Themanualstatement overrides theunicast negotiationstatement configured at the [edit protocols ptp] hierarchy level. As soon as you configure a manual client, it starts receiving announce and synchronization packets.Secure client—A secure client is configured with an exact IP address of the remote PTP host, after which it joins a primary clock through unicast negotiation. To configure a secure client, include the exact IP address in the
clock-client ip-addressstatement at the [edit protocols ptp master interface interface-name unicast-mode] hierarchy level.
You can configure the maximum number of clients (512 ) in the following combination:
Automatic clients 256.
Manual and secure clients 256—Any combination of manual and secure clients is allowed as long as the combined total amounts to 256.
Change History Table
Feature support is determined by the platform and release you are using. Use Feature Explorer to determine if a feature is supported on your platform.
