Juniper ATP Cloud Overview
Juniper ATP Cloud is a cloud-based solution that integrates with Policy Enforcer. Cloud environments are flexible and scalable, and a shared environment ensures that everyone benefits from new threat intelligence in near real-time. Your sensitive data is secured even though it is in a cloud shared environment. Security administrators can update their defenses when new attack techniques are discovered and distribute the threat intelligence with very little delay.
Juniper ATP Cloud offers the following features:
-
Communicates with firewalls and switches to simplify threat prevention policy deployment and enhance the anti-threat capabilities across the network.
-
Delivers protection against “zero-day” threats using a combination of tools to provide robust coverage against sophisticated, evasive threats.
-
Checks inbound and outbound traffic with policy enhancements that allow users to stop malware, quarantine infected systems, prevent data exfiltration, and disrupt lateral movement.
-
Provides deep inspection, actionable reporting, and inline malware blocking.
-
Provides feeds for GeoIP, C&C, allowlist and blocklist, infection hosts, custom configured feeds and file submission.
Figure 1 lists the Juniper ATP Cloud components.
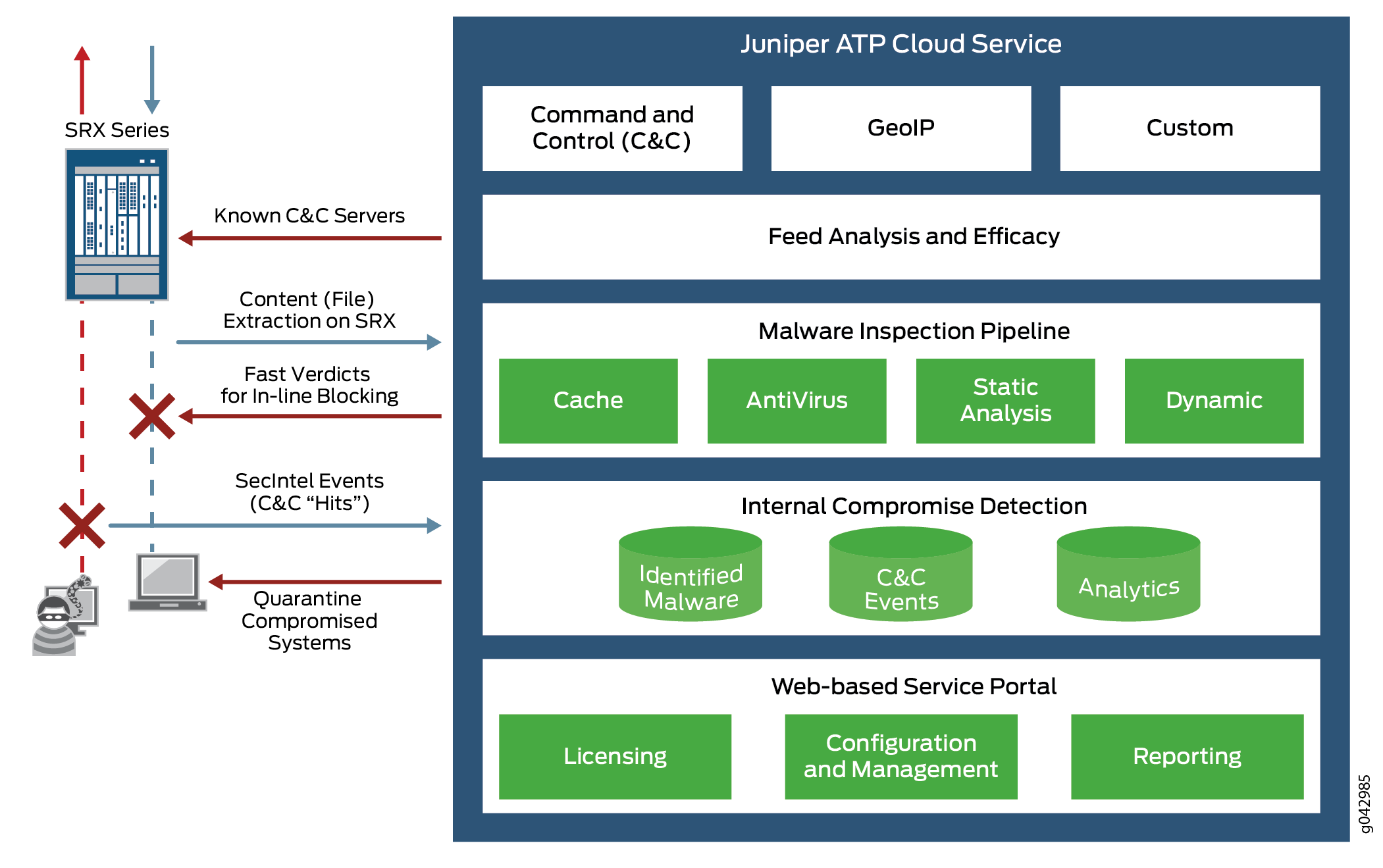
Table 1 briefly describes each Juniper ATP Cloud component’s operation.
|
Component |
Operation |
|---|---|
|
Command and control (C&C) cloud feeds |
C&C feeds are essentially a list of servers that are known command and control for botnets. The list also includes servers that are known sources for malware downloads. See Command and Control Servers Overview. |
|
GeoIP cloud feeds |
GeoIP feeds is an up-to-date mapping of IP addresses to geographical regions. This gives you the ability to filter traffic to and from specific geographies in the world. |
|
Infected host cloud feeds |
Infected hosts indicate local devices that are potentially compromised because they appear to be part of a C&C network or other exhibit other symptoms. See Infected Hosts Overview. |
|
Custom Feeds |
Lists you customize by adding IP addresses, domains, and URLs to your own lists. See Custom Feed Sources Overview. |
|
Allowlist and blocklists |
An allowlist is simply a list of known IP addresses that you trust and a blocklist is a list that you do not trust. |
|
Malware inspection pipeline |
Performs malware analysis and threat detection. |
|
Internal compromise detection |
Inspects files, metadata, and other information. |
