Policy Enforcer Backup and Restore
Policy Enforcer provides the option of backing-up all Policy Enforcer configuration and storing it as a .tar file. In the event of any unforeseen circumstances such as a malicious attack or system failure you can use the backup file to restore Policy Enforcer to a previously saved configuration. You can also take a backup before you change some configuration in Policy Enforcer, and revert to the backed up configuration, if needed. You can take multiple backups and choose to restore the Policy Enforcer configuration from any of these backup files.
Policy Enforcer backup includes Policy Enforcer configurations such as .yml files, databases or sequences, and device configurations. Policy Enforcer also communicates with multiple components to obtain information, as shown in Figure 1.
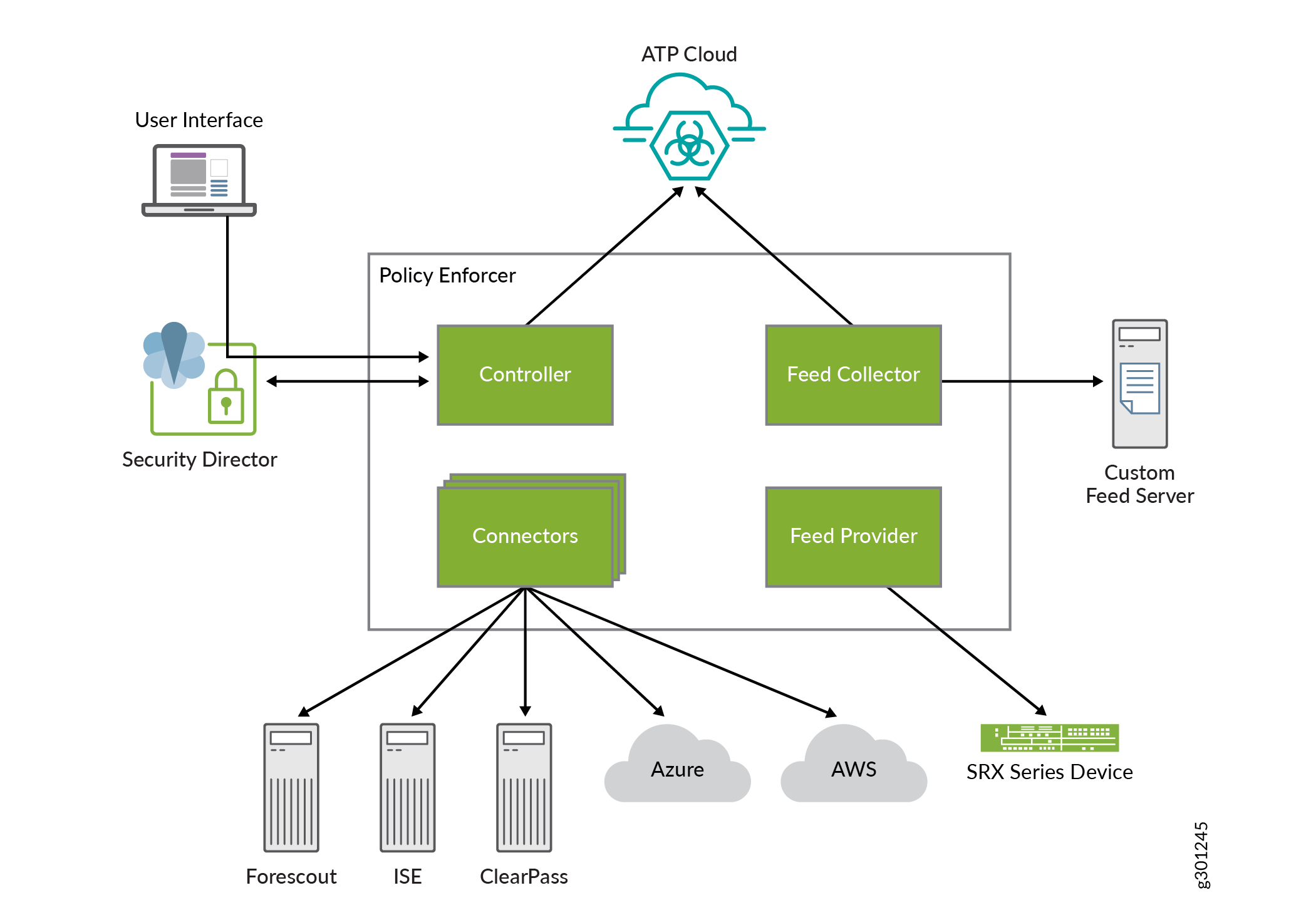
Policy Enforcer communicates with:
-
Juniper ATP Cloud/ ATP Appliance for feeds
-
Security Director for profiles and configurations
-
Junos Space Network Management Platform and Security Director to discover network connectivity like endhosts
-
Connectors to connect to AWS, Azure, ClearPass, Contrail, PulseSecure, and Forescout
Policy Enforcer backup includes the backup of all these configurations and dependencies. When you backup Policy Enforcer, both Policy Enforcer and Security Director configurations are backed up.
Policy Enforcer backup does not include feed data.
Backing-Up Policy Enforcer
Before You Begin
You must be aware of the following before you initiate a Policy Enforcer backup:
-
When you initiate a backup/restore, Policy Enforcer goes into maintenance mode and will be unresponsive until the backup/restore process is complete. Ensure that you complete all the tasks with Policy Enforcer before you start the backup/restore process.
-
If you are saving the backup .tar file on a remote server, ensure that there is enough space for the file on that server.
-
Ensure that Policy Enforcer and Security Director backups are taken and restored at the same time to prevent unexpected application behavior.
-
Ensure Policy Enforcer and connected Junos Space Security Director database backups are taken at the same time and no changes are made when backups are happening.
To take a backup of Policy Enforcer:
A job is created to execute the backup process. To see the progress of the backup, go to the Job Management page.
Policy Enforcer will be in maintenance mode and will be unavailable till the backup process is complete.
After the backup process is complete, the backup .tar file is listed on the Backup and Restore page.
|
Field |
Description |
|---|---|
|
Server Type |
Select whether you want to save the backup .tar file to a local server or to a remote server.
|
|
Description |
Enter a description; maximum length is 1024 characters. Make this description as useful as possible for everyone. |
|
Username |
Enter the username of the remote server where you want to save the backup .tar file. |
|
Password |
Enter the password for the selected remote server. |
|
IP Address |
Enter the IPv4 or IPv6 address of the remote server where you want to save the backup .tar file. |
|
Directory |
Enter the filepath and folder name on the remote server where you want to save the backup .tar file. |
|
Schedule Backup |
To select a schedule for the backup:
You can also edit or delete the backup schedule by clicking Edit or Delete, respectively. |
Restoring Policy Enforcer from a Backup File
Before You Begin
You must be aware of the following before you restore Policy Enforcer from a backup file:
-
When you initiate a backup/restore, Policy Enforcer goes into maintenance mode and will be unresponsive until the backup/restore process is complete. Ensure that you complete all the tasks with Policy Enforcer before you start the backup/restore process.
-
Ensure that Policy Enforcer and Security Director backups are taken and restored at the same time to prevent unexpected application behavior.
-
When you restore Policy Enforcer from a backup file, ensure the matching Security Director backup is also restored at the same time. Do not make any changes to managed devices in Security Director or devices connected to Policy Enforcer as the system does not check for this.
To restore Policy Enforcer from a backup file:
