WAN Assurance Configuration Overview
This overview illustrates how to use the Juniper Mist™ cloud console (the GUI) to provision a simple hub-and-spoke network using Juniper® Session Smart™ Routers. Conceptually, you can think of the network as an enterprise with branch offices connecting over a provider WAN to on-premises data centers. Examples include an auto-parts store, a hospital, or a series of point-of-sale kiosks—anything that requires a remote extension of the corporate LAN for services such as authentication or access to applications.
We assume that before you begin configuring WAN Assurance in your sandbox, you have onboarded your hardware to the Juniper Mist cloud. We also assume and that the physical connections (cabling) needed to support the configuration are in place and that you know the interfaces, and VLANs are valid for your sandbox.
Figure 1 illustrates the workflow for configuring WAN using the Juniper Mist cloud portal.
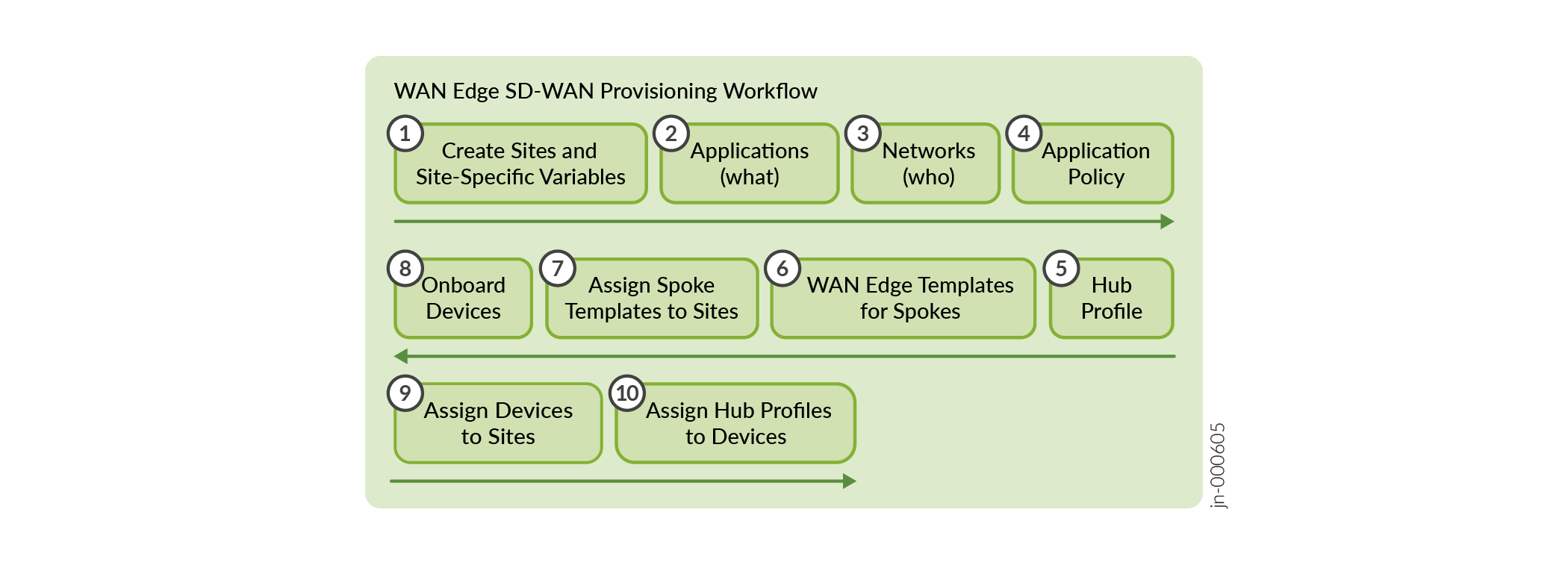
The sequence of configuration tasks in this example:
-
Create Sites and Variables—Create a site for the hubs and spokes. Configure site variables for each site. You use these variables later in the templates for WAN edge devices and the hub profile. See Configure Sites and Variables.
-
Setup Networks—Define the Networks. Networks are the source of traffic defined through IP prefixes. See Configure Networks.
-
Configure Applications—Applications are destinations that you define using IP prefixes. Applications represent traffic destinations. See Configure Applications.
-
Create Application Policies— Application policies determine which networks or users can access which applications, and according to which traffic steering policy. See Configure Application Policies.
-
Create hub profiles—You assign hub profile to standalone or clustered devices to automate overlay path creation. See Configure Hub Profiles.
-
Create WAN edge templates—WAN edge templates automatically configure repetitive information such as an IP address, gateway, or VLAN when applied to sites. See Configure WAN Edge Templates.
-
Onboard devices—Onboard your devices by assigning them to a site. Complete the onboarding by attaching hub profiles and spoke templates to the respective hub sites and spoke sites. This final step brings the topology together. See Assign Templates to Sites.
You can perform the following tasks on your devices for providing additional security measures:
Setup Secure Edge Connectors—Perform traffic inspection by Secure Edge for the WAN edge devices managed by Juniper Mist Cloud portal. See Set Up Secure Edge Connectors
.- Configure IDP-Based Threat Detection—Monitor the events occurring on your network and proactively stop attacks and prevent future attacks. See IDP-Based Threat Detection.
Upgrade software on your device to take advantage of new enhancements.
- Upgrade Software—Upgrade the software on your device through the Juniper Mist portal in a few simple steps. See Upgrade WAN Edge Device.
