- play_arrow Overview
- play_arrow Platform Considerations
- play_arrow WAN Configuration for SRX Series Firewalls
- WAN Assurance Configuration Overview
- Configure Sites and Variables for SRX Series Firewalls
- Configure Applications for SRX Series Firewalls
- Configure Networks for SRX Series Firewalls
- Configure Application Policies on SRX Series Firewalls
- Configure Hub Profiles for SRX Series Firewalls
- Configure WAN Edge Templates for SRX Series Firewalls
- Routing Configuration on SRX Series Firewalls
- Onboard SRX Series Firewalls for WAN Configuration
- IDP-Based Threat Detection for SRX Series Firewalls
- Enable Application Visibility on SRX Series Firewalls
- Monitor the Service Status of SRX Series Firewalls
- Upgrade a WAN Edge SRX Series Firewalls
- Configure a Custom VR for SRX Series Firewalls
- Revoke DHCP Lease on a WAN Edge Device
- Reserve DHCP IP Address
- play_arrow WAN Assurance Design
- play_arrow Secure Edge Connector
- play_arrow Cellular Edges
- play_arrow Monitor and Troubleshoot
- WAN Assurance Monitoring, SLE, and Troubleshooting Overview
- Monitor SRX Series Firewall Deployed as WAN Edge
- Monitor Session Smart Router Deployed as WAN Edge
- Service-Level Experiences for Session Smart Router Deployed as WAN Edge
- Troubleshoot Session Smart Router Deployed as WAN Edge
- Speed Tests for Session Smart Router Deployed as a WAN Edge (BETA)
- Dynamic and Manual Packet Captures
- Troubleshoot SRX Series Firewalls
- Replace a WAN Edge Device
- WAN Edge Testing Tools
Configure WAN Edge Templates for Session Smart Routers
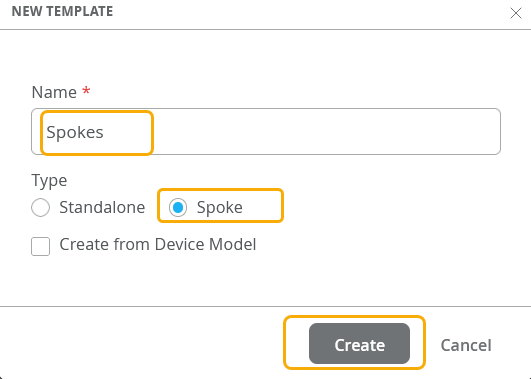
The WAN edge template in Juniper Mist™ WAN Assurance enables you to define common spoke characteristics including WAN interfaces, traffic-steering rules, and access policies. You then apply these configurations to the Juniper® Session Smart™ Router deployed as a WAN edge device. When you assign a WAN edge device to a site, the device automatically adopts the configuration from the associated template. This automatic process enables you to manage and apply consistent and standardized configurations across your network infrastructure, streamlining the configuration process.
You can have one or more templates for your spoke devices.
In this task, you create and configure a WAN edge template for a spoke device in the Juniper Mist™ cloud portal.
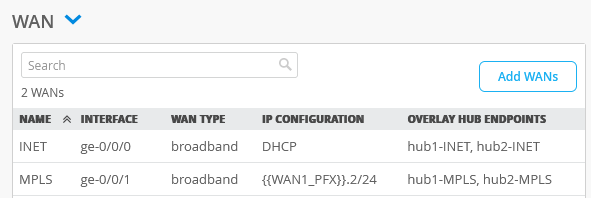
Add WAN Interfaces to the Template
In this task, add two WAN interfaces to the WAN edge template. You can add interfaces in device details page also (In the Juniper Mist portal, click WAN Edges> WAN Edges)
To add WAN interfaces to the template:
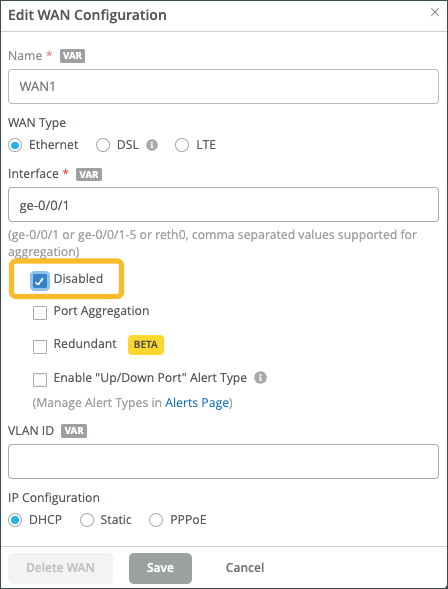
Configure LTE Interface
Juniper Mist SD-WAN allows organizations to integrate LTE connectivity seamlessly. LTE connectivity provides an alternate path for multipath routing; either as a primary path in locations that have no access to circuits or as a path of last resort in the event that the primary circuit has failed.
For example: In a retail store with a primary MPLS connection for business-critical applications. Juniper Mist SD-WAN can add an LTE link as a backup. If the MPLS link experiences issues, Juniper Mist dynamically switches traffic to the LTE link. This ensures continuous connectivity and minimizes disruptions.
On Session Smart Routers, the LTE support is provided through the in-built LTE module that operates on both 3G and 4G networks. See LTE and Dual LTE Configuration on setting up LTE on Session Smart Routers.
To have LTE link for Juniper Mist SD-WAN, you need an LTE interface setup on your Session Smart Routers and SRX Series Firewalls and insert the Subscriber Identity Module (SIM) in the LTE card.
To add an LTE interface as WAN link:
Configure LAN
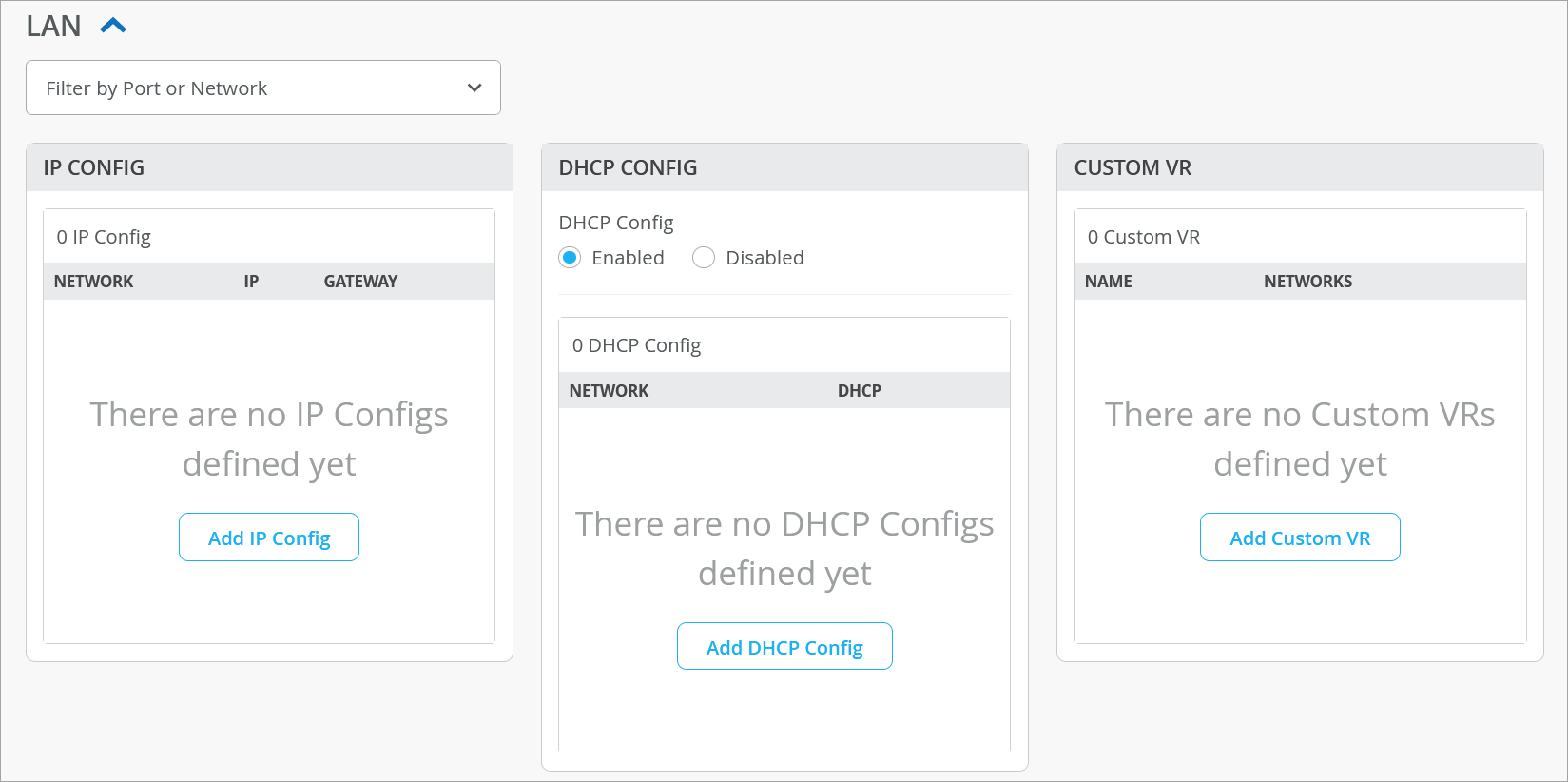
LAN interface configuration identifies your request source from the name of the network you specify in the LAN configuration.
The LAN configuration section includes the components for IP Configuration, DHCP Configuration, Custom VR, and LAN interface configuration. The LAN configuration section enables more flexibility by allowing you to override each configuration component (such as IP configuration) separately without touching other components.
The LAN Configuration section also provides a filter for you to easily search for configurations per port or network.
To configure LAN:
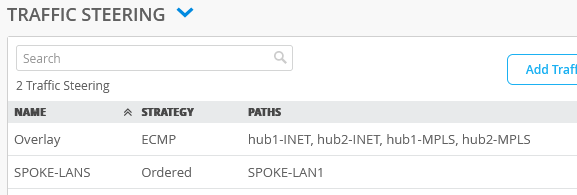
Configure Traffic-Steering Policies
Just like with hub profiles, traffic steering in a Juniper Mist network is where you define the different paths that application traffic can take to traverse the network. The paths that you configure within traffic steering also determine the destination zone.
To configure traffic-steering policies:
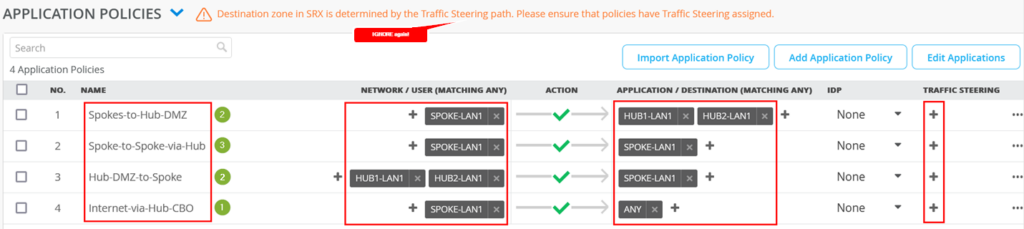
Configure Application Policies
In a Mist network, application policies are where you define which network and users can access which applications, and according to which traffic-steering policy. The Networks/Users settings determine the source zone. The Application + Traffic Steering settings determine the destination zone. Additionally, you can assign an action of Permit or Deny. Mist evaluates and applies application policies in the order in which you list them.
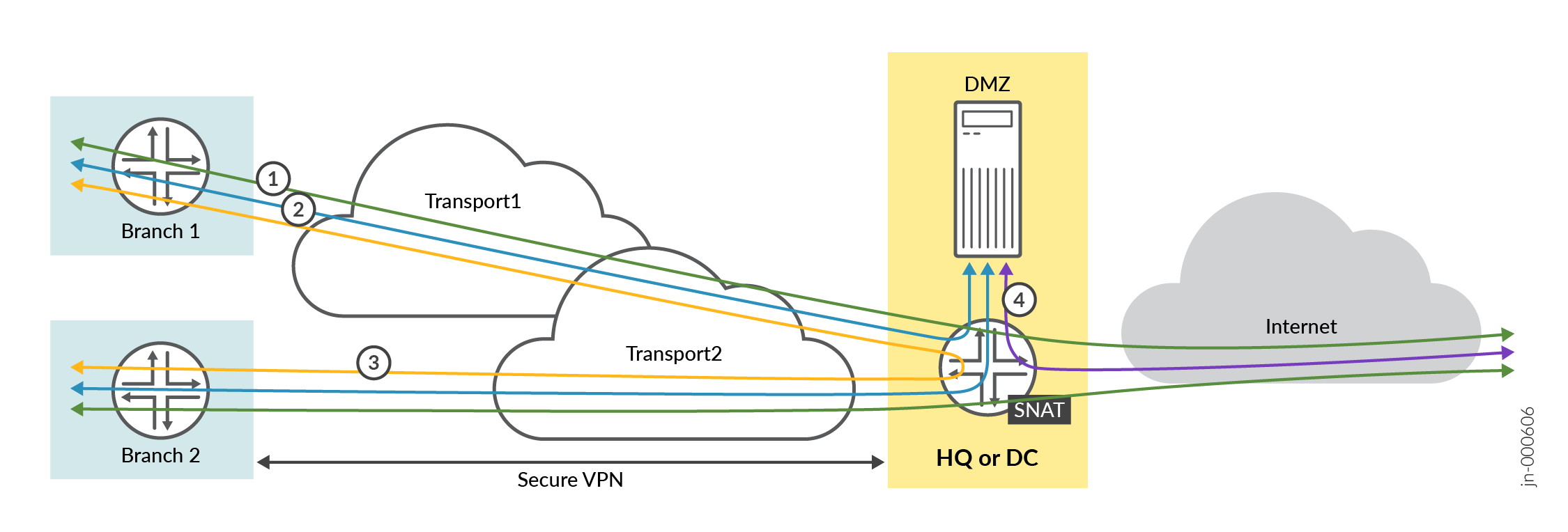
Consider the traffic-flow requirements in Figure 5. The image depicts a basic initial traffic model for a corporate VPN setup (third spoke device and second hub device are not shown).
To meet the preceding requirements, you need to create the following application rules:
Policy 1—Allows traffic from spoke sites to the hub. In this case, the destination prefix used in address groups represents the LAN interface of two hubs.
Policy 2—Allows spoke-to-spoke traffic through the corporate LAN through an overlay.
Note:This may not be feasible in the real world except on expensive MPLS networks with managed IPs. Managed IPs send traffic directly to the other spoke. This type of traffic usually flows through a hub device
Policy 3—Allows traffic from both the hub and the DMZ attached to the hub to the spoke devices.
Policy 4—Allows Internet-bound traffic to flow from spoke devices to the hub device. From there, the traffic breaks out to the Internet. In this case, the hub applies source NAT to the traffic and routes traffic to a WAN interface, as defined in the hub profile. This rule is general, so you should place it after the specific rules. Juniper Mist cloud evaluates and applies application policies in the order in which the policies are listed.
Order of application policies do not have any effect on Session Smart Router configuration. As good practice, we recommend you to place global rules towards the end of the policy rules list.
Traffic steering on each rule is not a mandatory for Session Smart Routers. When you use Session Smart Router, the system announces all routes on each LAN interface using the iBGP-based route distribution.
Use the same name for network on both sides for Session Smart Router for traffic to traverse between a hub and a spoke. The network name for the Session Smart Router must be identical to the security tenant used for traffic isolation. Because of this, the network name must match on both sides.
To create an application policy:
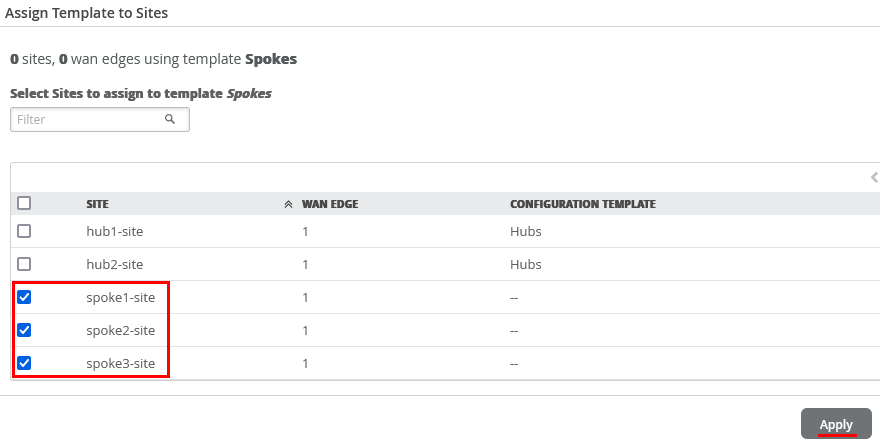
Assign Spoke Templates to Sites
The template now exists in the Juniper Mist cloud as an object that can be attached to one or more sites.
You can apply the same template to multiple sites.
If a site already has a template assigned to it, assigning another template will replace the existing template (in other words, one site cannot have two templates).
To assign the spoke template to site:
Configure Device-Specific WAN Edge Templates
Device configuration is simplified with WAN Edge Templates following your device onboarding process. These WAN Edge templates can be customized to unique deployments across all edge devices. Juniper Networks Mist AI is positioned uniquely in the industry as Mist AI WAN Edge templates can be applied to any model, regardless of vendor. Additionally, WAN Edge templates can mix and match different models under a single template, streamlining your configuration and deployment phase.
To manually configure your WAN Edge templates for the Session Smart Router, see Configure a WAN Edge Template.
Device-Specific WAN Edge Templates
There is a significant benefit to leveraging Juniper Networks hardware with Mist AI SD-WAN. Configuration is simplified for many Juniper Networks® Session Smart™ Routers, and Juniper Networks® SRX Series Firewalls, which have device-specific templates that automatically assign WAN and LAN interfaces and define LAN Networks for connectivity.
These templates are unique for each device model. With zero manual input after device selection and naming the WAN Edge, a user’s specified WAN Edge device is pre-populated with the values.
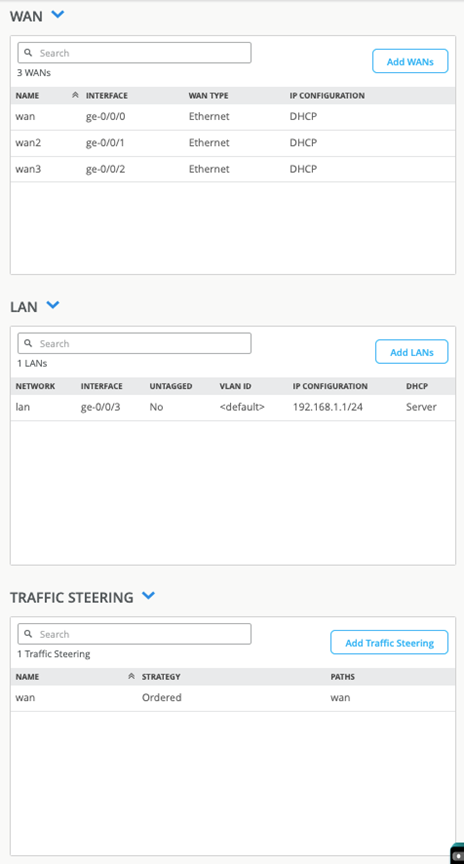
For example, Figure 10 shows that the SSR120 WAN Edge template generates several values, including Ethernet interfaces for LAN and WAN with relevant DHCP and IP values:
- wan ge-0/0/0
- wan2 ge-0/0/1
- wan3 ge-0/0/2
- lan ge-0/03
Additionally, we see in Figure 10 that the Juniper Mist portal populates a traffic steering policy. This enables Juniper Mist to send traffic over our wan connection to an any Mist Application with a quad zero catch-all destination.
Upon applying a WAN Edge template, application policies, networks, and applications receive automatic updates as shown in Figure 11, Figure 12, and Figure 13.
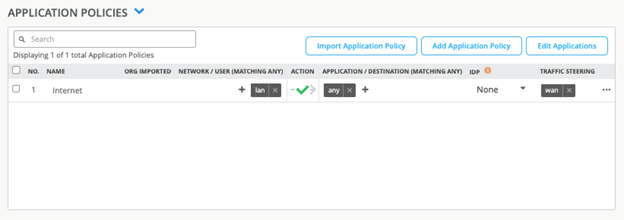
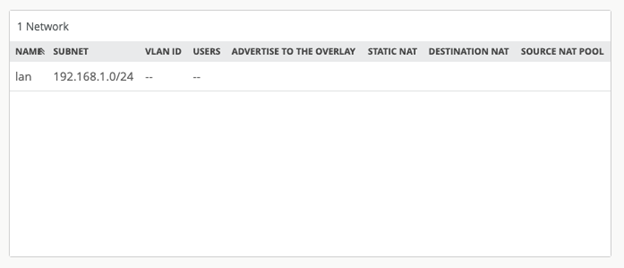
Juniper Mist AI SD-WAN includes the following device models with pre-configured WAN Edge templates for Session Smart Routers:
- SSR120
- SSR130
- SSR1200
- SSR1300
- SSR1400
- SSR1500
The WAN Edge device specific templates provide basic network configuration in a single step and allow for re-usable and consistent configuration for Session Smart Router and SRX Series Firewall device you deploy. The template provides device-specific, pre-configured WAN interfaces, LAN interfaces, a traffic steering policy, and an application policy. All you have to do is name the template and select the device type.
To select a device-specific WAN Edge template:
- In the Juniper Mist portal, select Organization > WAN > WAN Edge Templates.
- Select Create Template in the upper right corner to open a new template page.
- Enter the name for the template.
- Click the Create from Device Model check-box.
- Select your device model from the drop-down box. Figure 14: Configure Device-Specific WAN Edge Template
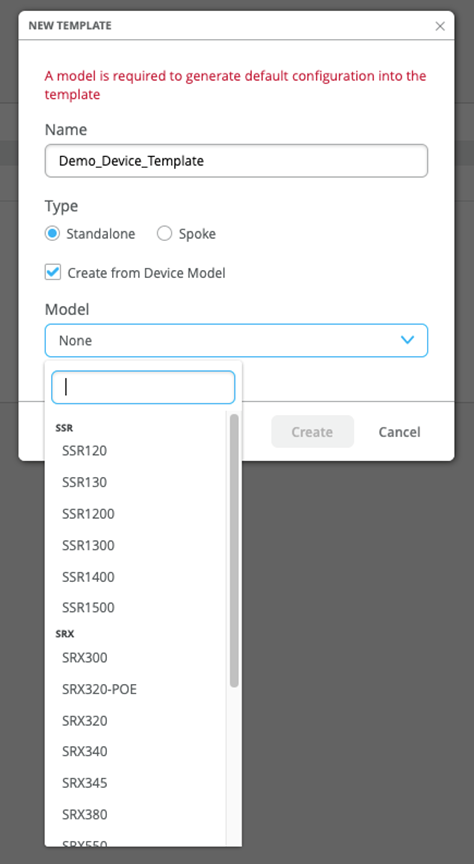
- Click Create.
Juniper Mist UI displays the completed device template. You now have a working WAN Edge template that you can apply to many sites and devices across your organization.
Assign to Site
With your template set up, you need to save and assign it to the site where your WAN edge device will be deployed.
- Click the Assign to Site button at the top of the template page.
- Select a site from the list where you want the template applied.
- Click Apply.
- Finally, all that remains is to associate the device with your Site: Onboard Session Smart Routers for WAN Configuration