Example: Configuring PVLANs with Secondary VLAN Trunk Ports and Promiscuous Access Ports on a QFX Series Switch
This example shows how to configure secondary VLAN trunk ports and promiscuous access ports as part of a private VLAN configuration. Secondary VLAN trunk ports carry secondary VLAN traffic.
This example uses Junos OS for switches that do not support the Enhanced Layer 2 Software (ELS) configuration style. For more about ELS, see Using the Enhanced Layer 2 Software CLI.
For a given private VLAN, a secondary VLAN trunk port can carry traffic for only one secondary VLAN. However, a secondary VLAN trunk port can carry traffic for multiple secondary VLANs as long as each secondary VLAN is a member of a different private (primary) VLAN. For example, a secondary VLAN trunk port can carry traffic for a community VLAN that is part of primary VLAN pvlan100 and also carry traffic for an isolated VLAN that is part of primary VLAN pvlan400.
To configure a trunk port to carry secondary VLAN traffic, use
the isolated and interface statements, as shown in steps 12 and 13 of the example configuration
for Switch 1.
When traffic egresses from a secondary VLAN trunk port, it normally carries the tag of the primary VLAN that the secondary port is a member of. If you want traffic that egresses from a secondary VLAN trunk port to retain its secondary VLAN tag, use the extend-secondary-vlan-id statement.
A promiscuous access port carries untagged traffic and can be a member of only one primary VLAN. Traffic that ingresses on a promiscuous access port is forwarded to the ports of the secondary VLANs that are members of the primary VLAN that the promiscuous access port is a member of. This traffic carries the appropriate secondary VLAN tags when it egresses from the secondary VLAN ports if the secondary VLAN port is a trunk port.
To configure an access port to be promiscuous, use the promiscuous statement, as shown in step 12 of the example configuration for Switch 2.
If traffic ingresses on a secondary VLAN port and egresses on a promiscuous access port, the traffic is untagged on egress. If tagged traffic ingresses on a promiscuous access port, the traffic is discarded.
Requirements
This example uses the following hardware and software components:
Two QFX devices
Junos OS Release 12.2 or later for the QFX Series
Overview and Topology
Figure 1 shows the topology used in this example. Switch 1 includes several primary and secondary private VLANs and also includes two secondary VLAN trunk ports configured to carry secondary VLANs that are members of primary VLANs pvlan100 and pvlan400.
Switch 2 includes the same private VLANs. The figure shows xe-0/0/0 on Switch 2 as configured with promiscuous access ports or promiscuous trunk ports. The example configuration included here configures this port as a promiscuous access port.
The figure also shows how traffic would flow after ingressing on the secondary VLAN trunk ports on Switch 1.
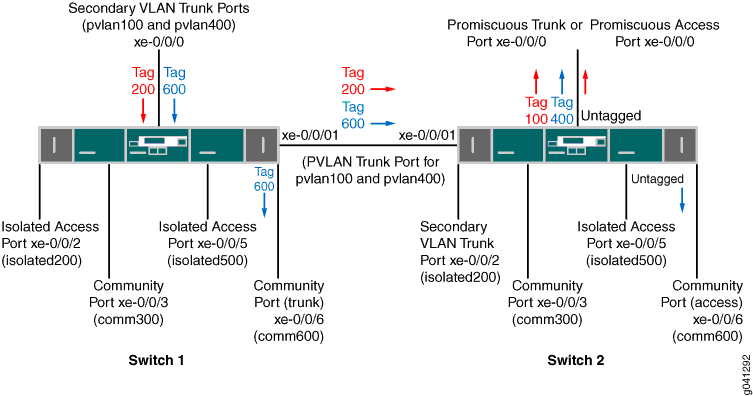
Table 1 and Table 2 list the settings for the example topology on both switches.
| Component | Description |
|---|---|
pvlan100, ID 100 |
Primary VLAN |
pvlan400, ID 400 |
Primary VLAN |
comm300, ID 300 |
Community VLAN, member of pvlan100 |
comm600, ID 600 |
Community VLAN, member of pvlan400 |
isolation-vlan-id 200 |
VLAN ID for isolated VLAN, member of pvlan100 |
isolation–vlan-id 500 |
VLAN ID for isolated VLAN, member of pvlan400 |
xe-0/0/0.0 |
Secondary VLAN trunk port for primary VLANs pvlan100 and pvlan400 |
xe-0/0/1.0 |
PVLAN trunk port for primary VLANs pvlan100 and pvlan400 |
xe-0/0/2.0 |
Isolated access port for pvlan100 |
xe-0/0/3.0 |
Community access port for comm300 |
xe-0/0/5.0 |
Isolated access port for pvlan400 |
xe-0/0/6.0 |
Community trunk port for comm600 |
| Component | Description |
|---|---|
pvlan100, ID 100 |
Primary VLAN |
pvlan400, ID 400 |
Primary VLAN |
comm300, ID 300 |
Community VLAN, member of pvlan100 |
comm600, ID 600 |
Community VLAN, member of pvlan400 |
isolation-vlan-id 200 |
VLAN ID for isolated VLAN, member of pvlan100 |
isolation–vlan-id 500 |
VLAN ID for isolated VLAN, member of pvlan400 |
xe-0/0/0.0 |
Promiscuous access port for primary VLANs pvlan100 |
xe-0/0/1.0 |
PVLAN trunk port for primary VLANs pvlan100 and pvlan400 |
xe-0/0/2.0 |
Secondary trunk port for isolated VLAN, member of pvlan100 |
xe-0/0/3.0 |
Community access port for comm300 |
xe-0/0/5.0 |
Isolated access port for pvlan400 |
xe-0/0/6.0 |
Community access port for comm600 |
Configuring the PVLANs on Switch 1
CLI Quick Configuration
To quickly create and configure the PVLANs on Switch 1, copy the following commands and paste them into a switch terminal window:
[edit] set interfaces xe-0/0/0 unit 0 family ethernet-switching port-mode trunk set interfaces xe-0/0/1 unit 0 family ethernet-switching port-mode trunk set interfaces xe-0/0/1 unit 0 family ethernet-switching vlan members pvlan100 set interfacesxe-0/0/1 unit 0 family ethernet-switching vlan members pvlan400 set interfaces xe-0/0/2 unit 0 family ethernet-switching port-mode access set interfaces xe-0/0/3 unit 0 family ethernet-switching port-mode access set interfaces xe-0/0/5 unit 0 family ethernet-switching port-mode access set interfaces xe-0/0/6 unit 0 family ethernet-switching port-mode trunk set vlans pvlan100 vlan-id 100 set vlans pvlan400 vlan-id 400 set vlans pvlan100 pvlan set vlans pvlan400 pvlan set vlans pvlan100 interface xe-0/0/1.0 pvlan-trunk set vlans pvlan400 interface xe-0/0/1.0 pvlan-trunk set vlans comm300 vlan-id 300 set vlans comm300 primary-vlan pvlan100 set vlans comm300 interface xe-0/0/3.0 set vlans comm600 vlan-id 600 set vlans comm600 primary-vlan pvlan400 set vlans comm600 interface xe-0/0/6.0 set vlans pvlan100 pvlan isolation-vlan-id 200 set vlans pvlan400 pvlan isolation-vlan-id 500 set vlans pvlan100 interface xe-0/0/0.0 isolated set vlans pvlan400 interface xe-0/0/0.0 isolated set vlans comm600 interface xe-0/0/0.0 set vlans pvlan100 interface xe-0/0/2.0 isolated set vlans pvlan400 interface xe-0/0/5.0 isolated
Procedure
Step-by-Step Procedure
To configure the private VLANs and secondary VLAN trunk ports:
Configure the interfaces and port modes:
[edit interfaces] user@switch# set xe-0/0/0 unit 0 family ethernet-switching port-mode trunk user@switch# set xe-0/0/1 unit 0 family ethernet-switching port-mode trunk user@switch# set xe-0/0/1 unit 0 family ethernet-switching vlan members pvlan100 user@switch# set xe-0/0/1 unit 0 family ethernet-switching vlan members pvlan400 user@switch# set xe-0/0/2 unit 0 family ethernet-switching port-mode access user@switch# set xe-0/0/3 unit 0 family ethernet-switching port-mode access user@switch# set xe-0/0/5 unit 0 family ethernet-switching port-mode access user@switch# set xe-0/0/6 unit 0 family ethernet-switching port-mode access
Create the primary VLANs:
[edit vlans] user@switch# set pvlan100 vlan-id 100 user@switch# set pvlan400 vlan-id 400
Note:Primary VLANs must always be tagged VLANs, even if they exist on only one device.
Configure the primary VLANs to be private:
[edit vlans] user@switch# set pvlan100 pvlan user@switch# set pvlan400 pvlan
Configure the PVLAN trunk port to carry the private VLAN traffic between the switches:
[edit vlans] user@switch# set pvlan100 interface xe-0/0/1.0 pvlan-trunk user@switch# set pvlan400 interface xe-0/0/1.0 pvlan-trunk
Create secondary VLAN comm300 with VLAN ID 300:
[edit vlans] user@switch# set comm300 vlan-id 300
Configure the primary VLAN for comm300:
[edit vlans] user@switch# set comm300 primary-vlan pvlan100
Configure the interface for comm300:
[edit vlans] user@switch# set comm300 interface xe-0/0/3.0
Create secondary VLAN comm600 with VLAN ID 600:
[edit vlans] user@switch# set comm600 vlan-id 600
Configure the primary VLAN for comm600:
[edit vlans] user@switch# set comm600 primary-vlan pvlan400
Configure the interface for comm600:
[edit vlans] user@switch# set comm600 interface xe-0/0/6.0
Configure the interswitch isolated VLANs:
[edit vlans] user@switch# set pvlan100 pvlan isolation-vlan-id 200 user@switch# set pvlan400 pvlan isolation-vlan-id 500
Note:When you configure a secondary VLAN trunk port to carry an isolated VLAN, you must also configure an isolation-vlan-id. This is true even if the isolated VLAN exists only on one switch.
Enable trunk port xe-0/0/0 to carry secondary VLANs for the primary VLANs:
[edit vlans] user@switch# set pvlan100 interface xe-0/0/0.0 isolated user@switch# set pvlan400 interface xe-0/0/0.0 isolated
Configure trunk port xe-0/0/0 to carry comm600 (member of pvlan400):
[edit vlans] user@switch# set comm600 interface xe-0/0/0.0
Note:You do not need to explicitly configure xe-0/0/0 to carry the isolated VLAN traffic (tags 200 and 500) because all the isolated ports in pvlan100 and pvlan400–including xe-0/0/0.0–are automatically included in the isolated VLANs created when you configured
isolation-vlan-id 200andisolation-vlan-id 500.Configure xe-0/0/2 and xe-0/0/6 to be isolated:
[edit vlans] user@switch# set pvlan100 interface xe-0/0/2.0 isolated user@switch# set pvlan400 interface xe-0/0/5.0 isolated
Results
Check the results of the configuration on Switch 1:
[edit]
user@switch# show
interfaces {
xe-0/0/0 {
unit 0 {
family ethernet-switching {
port-mode trunk;
vlan {
members pvlan100;
members pvlan400;
}
}
}
}
xe-0/0/1 {
unit 0 {
family ethernet-switching {
port-mode trunk;
vlan {
members pvlan100;
members pvlan400;
}
}
}
}
xe-0/0/2 {
unit 0 {
family ethernet-switching {
port-mode access;
}
}
}
xe-0/0/3 {
unit 0 {
family ethernet-switching {
port-mode access;
}
}
}
xe-0/0/5 {
unit 0 {
family ethernet-switching {
port-mode access;
}
}
}
xe-0/0/6 {
unit 0 {
family ethernet-switching {
port-mode trunk;
}
}
}
}
vlans {
comm300 {
vlan-id 300;
interface {
xe-0/0/3.0;
}
primary-vlan pvlan100;
}
comm600 {
vlan-id 600;
interface {
xe-0/0/6.0;
}
primary-vlan pvlan400;
}
pvlan100 {
vlan-id 100;
interface {
xe-0/0/0.0;
xe-0/0/2.0;
xe-0/0/3.0;
xe-0/0/1.0 {
pvlan-trunk;
}
}
no-local-switching;
isolation-id 200;
}
pvlan400 {
vlan-id 400;
interface {
xe-0/0/0.0;
xe-0/0/5.0;
xe-0/0/6.0;
xe-0/0/1.0 {
pvlan-trunk;
}
}
no-local-switching;
isolation-id 500;
}
}
Configuring the PVLANs on Switch 2
The configuration for Switch 2 is almost identical to the configuration for Switch 1. The most significant difference is that xe-0/0/0 on Switch 2 is configured as a promiscuous trunk port or a promiscuous access port, as Figure 1 shows. In the following configuration, xe-0/0/0 is configured as a promiscuous access port for primary VLAN pvlan100.
If traffic ingresses on VLAN-enabled port and egresses on a promiscuous access port, the VLAN tags are dropped on egress and the traffic is untagged at that point. For example, traffic for comm600 ingresses on the secondary VLAN trunk port configured on xe-0/0/0.0 on Switch 1 and carries tag 600 as it is forwarded through the secondary VLAN. When it egresses from xe-0/0/0.0 on Switch 2, it will be untagged if you configure xe-0/0/0.0 as a promiscuous access port as shown in this example. If you instead configure xe-0/0/0.0 as a promiscuous trunk port (port-mode trunk), the traffic for comm600 carries its primary VLAN tag (400) when it egresses.
CLI Quick Configuration
To quickly create and configure the PVLANs on Switch 2, copy the following commands and paste them into a switch terminal window:
[edit] set interfaces xe-0/0/0 unit 0 family ethernet-switching port-mode access set interfaces xe-0/0/1 unit 0 family ethernet-switching port-mode trunk set interfaces xe-0/0/1 unit 0 family ethernet-switching vlan members pvlan100 set interfaces xe-0/0/1 unit 0 family ethernet-switching vlan members pvlan400 set interfaces xe-0/0/2 unit 0 family ethernet-switching port-mode trunk set interfaces xe-0/0/3 unit 0 family ethernet-switching port-mode access set interfaces xe-0/0/5 unit 0 family ethernet-switching port-mode access set interfaces xe-0/0/6 unit 0 family ethernet-switching port-mode access set vlans pvlan100 vlan-id 100 set vlans pvlan400 vlan-id 400 set vlans pvlan100 pvlan set vlans pvlan400 pvlan set vlans pvlan100 interface xe-0/0/1.0 pvlan-trunk set vlans pvlan400 interface xe-0/0/1.0 pvlan-trunk set vlans comm300 vlan-id 300 set vlans comm300 primary-vlan pvlan100 set vlans comm300 interface xe-0/0/3.0 set vlans comm600 vlan-id 600 set vlans comm600 primary-vlan pvlan400 set vlans comm600 interface xe-0/0/6.0 set vlans pvlan100 pvlan isolation-vlan-id 200 set vlans pvlan400 pvlan isolation-vlan-id 500 set vlans pvlan100 interface xe-0/0/0.0 promiscuous set vlans pvlan100 interface xe-0/0/2.0 isolated set vlans pvlan400 interface xe-0/0/5.0 isolated
Procedure
Step-by-Step Procedure
To configure the private VLANs and secondary VLAN trunk ports:
Configure the interfaces and port modes:
[edit interfaces] user@switch# set xe-0/0/0 unit 0 family ethernet-switching port-mode access
user@switch# set xe-0/0/1 unit 0 family ethernet-switching port-mode trunk user@switch# set xe-0/0/1 unit 0 family ethernet-switching vlan members pvlan100 user@switch# set xe-0/0/1 unit 0 family ethernet-switching vlan members pvlan400 user@switch# set xe-0/0/2 unit 0 family ethernet-switching port-mode trunk user@switch# set xe-0/0/3 unit 0 family ethernet-switching port-mode access user@switch# set xe-0/0/5 unit 0 family ethernet-switching port-mode access user@switch# set xe-0/0/6 unit 0 family ethernet-switching port-mode access
Create the primary VLANs:
[edit vlans] user@switch# set pvlan100 vlan-id 100 user@switch# set pvlan400 vlan-id 400
Configure the primary VLANs to be private:
[edit vlans] user@switch# set pvlan100 pvlan user@switch# set pvlan400 pvlan
Configure the PVLAN trunk port to carry the private VLAN traffic between the switches:
[edit vlans] user@switch# set pvlan100 interface xe-0/0/1.0 pvlan-trunk user@switch# set pvlan400 interface xe-0/0/1.0 pvlan-trunk
Create secondary VLAN comm300 with VLAN ID 300:
[edit vlans] user@switch# set comm300 vlan-id 300
Configure the primary VLAN for comm300:
[edit vlans] user@switch# set comm300 primary-vlan pvlan100
Configure the interface for comm300:
[edit vlans] user@switch# set comm300 interface xe-0/0/3.0
Create secondary VLAN comm600 with VLAN ID 600:
[edit vlans] user@switch# set comm600 vlan-id 600
Configure the primary VLAN for comm600:
[edit vlans] user@switch# set comm600 primary-vlan pvlan400
Configure the interface for comm600:
[edit vlans] user@switch# set comm600 interface xe-0/0/6.0
- Configuring the PVLANs on Switch 1
Configure the interswitch isolated VLANs:
[edit vlans] user@switch# set pvlan100 pvlan isolation-vlan-id 200 user@switch# set pvlan400 pvlan isolation-vlan-id 500
Configure access port xe-0/0/0 to be promiscuous for pvlan100:
[edit vlans] user@switch# set pvlan100 interface xe-0/0/0.0 promiscuous
Note:A promiscuous access port can be a member of only one primary VLAN.
Configure xe-0/0/2 and xe-0/0/6 to be isolated:
[edit vlans] user@switch# set pvlan100 interface xe-0/0/2.0 isolated user@switch# set pvlan400 interface xe-0/0/5.0 isolated
Results
Check the results of the configuration on Switch 2:
[edit]
user@switch# show
interfaces {
xe-0/0/0 {
unit 0 {
family ethernet-switching {
port-mode access;
vlan {
members pvlan100;
}
}
}
}
xe-0/0/1 {
unit 0 {
family ethernet-switching {
port-mode trunk;
vlan {
members pvlan100;
members pvlan400;
}
}
}
}
xe-0/0/2 {
unit 0 {
family ethernet-switching {
port-mode trunk;
}
}
}
xe-0/0/3 {
unit 0 {
family ethernet-switching {
port-mode access;
}
}
}
xe-0/0/5 {
unit 0 {
family ethernet-switching {
port-mode access;
}
}
}
xe-0/0/6 {
unit 0 {
family ethernet-switching {
port-mode access;
}
}
}
vlans {
comm300 {
vlan-id 300;
interface {
xe-0/0/3.0;
}
primary-vlan pvlan100;
}
comm600 {
vlan-id 600;
interface {
xe-0/0/6.0;
}
primary-vlan pvlan400;
}
pvlan100 {
vlan-id 100;
interface {
xe-0/0/0.0;
xe-0/0/2.0;
xe-0/0/3.0;
xe-0/0/1.0 {
pvlan-trunk;
}
}
no-local-switching;
isolation-id 200;
}
pvlan400 {
vlan-id 400;
interface {
xe-0/0/5.0;
xe-0/0/6.0;
xe-0/0/1.0 {
pvlan-trunk;
}
}
no-local-switching;
isolation-id 500;
}
}
Verification
To confirm that the configuration is working properly, perform these tasks:
- Verifying That the Private VLAN and Secondary VLANs Were Created
- Verifying The Ethernet Switching Table Entries
Verifying That the Private VLAN and Secondary VLANs Were Created
Purpose
Verify that the primary VLAN and secondary VLANs were properly created on Switch 1.
Action
Use the show vlans command:
user@switch> show vlans private-vlan Name Role Tag Interfaces pvlan100 Primary 100 xe-0/0/0.0, xe-0/0/1.0, xe-0/0/2.0, xe-0/0/3.0 __iso_pvlan100__ Isolated 200 xe-0/0/2.0 comm300 Community 300 xe-0/0/3.0 pvlan400 Primary 400 xe-0/0/0.0, xe-0/0/1.0, xe-0/0/5.0, xe-0/0/6.0 __iso_pvlan400__ Isolated 500 xe-0/0/5.0 comm600 Community 600 xe-0/0/6.0
Meaning
The output shows that the private VLANs were created and identifies the interfaces and secondary VLANs associated with them.
Verifying The Ethernet Switching Table Entries
Purpose
Verify that the Ethernet switching table entries were created for primary VLAN pvlan100.
Action
Show the Ethernet switching table entries for pvlan100.
user@switch> show ethernet-switching table vlan pvlan100 private-vlan Ethernet-switching table: 0 unicast entries pvlan100 * Flood - All-members pvlan100 00:10:94:00:00:02 Learn xe-0/0/2.0 __iso_pvlan100__ * Flood - All-members __iso_pvlan100__ 00:10:94:00:00:02 Replicated - xe-0/0/2.0
