ON THIS PAGE
Configuring VLANs on QFX Series Switches without Enhanced Layer 2 Support
Example: Setting Up Basic Bridging and a VLAN for an EX Series Switch with ELS Support
Example: Setting Up Basic Bridging and a VLAN for an EX Series Switch
Example: Setting Up Bridging with Multiple VLANs on Switches
Example: Connecting Access Switches with ELS Support to a Distribution Switch with ELS Support
Example: Setting Up Bridging with Multiple VLANs for EX Series Switches
Example: Connecting an Access Switch to a Distribution Switch
Configuring the Native VLAN Identifier on Switches With ELS Support
Bridging and VLANs
Understanding Bridging and VLANs on Switches
Network switches use Layer 2 bridging protocols to discover the topology of their LAN and to forward traffic toward destinations on the LAN. This topic explains the following concepts regarding bridging and VLANs:
For Ethernet, Fast Ethernet, Tri-Rate Ethernet copper, Gigabit Ethernet, 10-Gigabit Ethernet, and aggregated Ethernet interfaces supporting VPLS, the Junos OS supports a subset of the IEEE 802.1Q standard for channelizing an Ethernet interface into multiple logical interfaces, allowing many hosts to be connected to the same Gigabit Ethernet switch, but preventing them from being in the same routing or bridging domain.
- Benefits of Using VLANs
- History of VLANs
- How Bridging of VLAN Traffic Works
- Packets Are Either Tagged or Untagged
- Switch Interface Modes—Access, Trunk, or Tagged Access
- Maximum VLANs and VLAN Members Per Switch
- Assigning Traffic to VLANs
- Forwarding VLAN Traffic
- VLANs Communicate with Integrated Routing and Bridging Interfaces
- VPLS Ports
Benefits of Using VLANs
In addition to reducing traffic and thereby speeding up the network, VLANs have the following advantages:
VLANs provide segmentation services traditionally provided by routers in LAN configurations, thereby reducing hardware equipment costs.
Packets coupled to a VLAN can be reliably identified and sorted into different domains. You can contain broadcasts within parts of the network, thereby freeing up network resources. For example, when a DHCP server is plugged into a switch and starts broadcasting its presence, you can prevent some hosts from accessing it by using VLANs to split up the network.
For security issues, VLANs provide granular control of the network because each VLAN is identified by a single IP subnetwork. All packets passing in and out of a VLAN are consistently tagged with the VLAN ID of that VLAN, thereby providing easy identification, because a VLAN ID on a packet cannot be altered.
VLANs react quickly to host relocation—this is also due to the persistent VLAN tag on packets.
On an Ethernet LAN, all network nodes must be physically connected to the same network. In VLANs, the physical location of nodes is not important—you can group network devices in any way that makes sense for your organization, such as by department or business function, types of network nodes, or physical location.
History of VLANs
Ethernet LANs were originally designed for small, simple networks that primarily carried text. However, over time, the type of data carried by LANs grew to include voice, graphics, and video. This more complex data, when combined with the ever-increasing speed of transmission, eventually became too much of a load for the original Ethernet LAN design. Multiple packet collisions were significantly slowing down the larger LANs.
The IEEE 802.1D-2004 standard helped evolve Ethernet LANs to cope with the higher data and transmission requirements by defining the concept of transparent bridging (generally called simply bridging). Bridging divides a single physical LAN (now called a single broadcast domain) into two or more virtual LANs, or VLANs. Each VLAN is a collection of some of the LAN nodes grouped together to form individual broadcast domains.
When VLANs are grouped logically by function or organization, a significant percentage of data traffic stays within the VLAN. This relieves the load on the LAN because all traffic no longer has to be forwarded to all nodes on the LAN. A VLAN first transmits packets within the VLAN, thereby reducing the number of packets transmitted on the entire LAN. Because packets whose origin and destination are in the same VLAN are forwarded only within the local VLAN, packets that are not destined for the local VLAN are the only ones forwarded to other broadcast domains. This way, bridging and VLANs limit the amount of traffic flowing across the entire LAN by reducing the possible number of collisions and packet retransmissions within VLANs and on the LAN as a whole.
How Bridging of VLAN Traffic Works
Because the objective of the IEEE 802.1D-2004 standard was to reduce traffic and therefore reduce potential transmission collisions for Ethernet, a system was implemented to reuse information. Instead of having a switch go through a location process every time a frame is sent to a node, the transparent bridging protocol allows a switch to record the location of known nodes. When packets are sent to nodes, those destination node locations are stored in address-lookup tables called Ethernet switching tables. Before sending a packet, a switch using bridging first consults the switching tables to see if that node has already been located. If the location of a node is known, the frame is sent directly to that node.
Transparent bridging uses five mechanisms to create and maintain Ethernet switching tables on the switch:
Learning
Forwarding
Flooding
Filtering
Aging
The key bridging mechanism used by LANs and VLANs is learning. When a switch is first connected to an Ethernet LAN or VLAN, it has no information about other nodes on the network. As packets are sent, the switch learns the embedded MAC addresses of the sending nodes and stores them in the Ethernet switching table, along with two other pieces of information—the interface (or port) on which the traffic was received on the destination node and the time the address was learned.
Learning allows switches to then do forwarding. By consulting the Ethernet switching table to see whether the table already contains the frame’s destination MAC address, switches save time and resources when forwarding packets to the known MAC addresses. If the Ethernet switching table does not contain an entry for an address, the switch uses flooding to learn that address.
Flooding finds a particular destination MAC address without using the Ethernet switching table. When traffic originates on the switch and the Ethernet switching table does not yet contain the destination MAC address, the switch first floods the traffic to all other interfaces within the VLAN. When the destination node receives the flooded traffic, it can send an acknowledgment packet back to the switch, allowing it to learn the MAC address of the node and add the address to its Ethernet switching table.
Filtering, the fourth bridging mechanism, is how broadcast traffic is limited to the local VLAN whenever possible. As the number of entries in the Ethernet switching table grows, the switch pieces together an increasingly complete picture of the VLAN and the larger LAN—it learns which nodes are in the local VLAN and which are on other network segments. The switch uses this information to filter traffic. Specifically, for traffic whose source and destination MAC addresses are in the local VLAN, filtering prevents the switch from forwarding this traffic to other network segments.
To keep entries in the Ethernet switching table current, the switch uses a fifth bridging mechanism, aging. Aging is the reason that the Ethernet switching table entries include timestamps. Each time the switch detects traffic from a MAC address, it updates the timestamp. A timer on the switch periodically checks the timestamp, and if it is older than a user-configured value, the switch removes the node's MAC address from the Ethernet switching table. This aging process eventually flushes unavailable network nodes out of the Ethernet switching table.
Packets Are Either Tagged or Untagged
When an Ethernet LAN is divided into VLANs, each VLAN is identified by a unique 802.1Q ID. The number of available VLANs and VLAN IDs are listed below:
On a switch running ELS software, except EX4100 switch, you can configure 4094 VLANs using VLAN IDs 1 through 4094. EX4100 switches support 1022 VLANs. VLAN IDs 0 and 4095 are reserved by Junos OS and cannot be assigned.
On a switch running non-ELS software, you can configure 4094 VLANs using VLAN IDs 1-4094.
Ethernet packets include a tag protocol identifier (TPID) EtherType field, which identifies the protocol being transported. When a device within a VLAN generates a packet, this field includes a value of 0x8100, which indicates that the packet is a VLAN-tagged packet. The packet also has a VLAN ID field that includes the unique 802.1Q ID, which identifies the VLAN to which the packet belongs.
Junos OS switches support the TPID value 0x9100 for Q-in-Q on switches. In addition to the TPID EtherType value of 0x8100, EX Series switches that do not support the Enhanced Layer 2 Software (ELS) configuration style also support values of 0x88a8 (Provider Bridging and Shortest Path Bridging) and 0x9100 (Q-inQ).
For a simple network that has only a single VLAN, all packets include a default 802.1Q tag, which is the only VLAN membership that does not mark the packet as tagged. These packets are untagged packets.
Q-in-Q tunnelling is not supported on NFX150 devices.
Switch Interface Modes—Access, Trunk, or Tagged Access
Ports, or interfaces, on a switch operate in one of three modes:
Access mode
Trunk mode
Tagged-access mode
Access Mode
An interface in access mode connects a switch to a single network device, such as a desktop computer, an IP telephone, a printer, a file server, or a security camera. Access interfaces accept only untagged packets.
By default, when you boot a switch that runs Junos OS that supports ELS and uses the factory default configuration, or when you boot the switch and do not explicitly configure a port mode, all interfaces on the switch are in access mode and accept only untagged packets from the default VLAN. You can optionally configure another VLAN and use that VLAN instead of the default VLAN.
On an EX Series switch that does not support ELS, the default VLAN is not created. Therefore, on such switches, you must explicitly configure at least one VLAN, even if your network is simple and you want only one broadcast domain to exist. You must also explicitly configure the interface in access mode. After you assign the interface to a VLAN, the interface functions in access mode.
For switches that run either type of software, you can also configure a trunk port or interface to accept untagged packets from a user-configured VLAN. For details about native VLAN, see Trunk Mode and Native VLAN.
Trunk Mode
Trunk mode interfaces are generally used to connect switches to one another. Traffic sent between switches can then consist of packets from multiple VLANs, with those packets multiplexed so that they can be sent over the same physical connection. Trunk interfaces usually accept only tagged packets and use the VLAN ID tag to determine both the packets’ VLAN origin and VLAN destination.
On an EX Series switch that runs software that does not support ELS, an untagged packet is not recognized on a trunk port unless you configure additional settings on that port.
On a switch that runs Junos OS that supports ELS, a trunk port recognizes untagged control packets for protocols such as the Link Aggregation Control Protocol (LACP) and the Link Layer Discovery Protocol (LLDP). However, the trunk port does not recognize untagged data packets unless you configure additional settings on that port.
LACP is not supported on NFX150 devices.
In the rare case where you want untagged packets to be recognized by a trunk port on switches that run either type of software, you must configure the single VLAN on a trunk port as a native VLAN. For more information about native VLANs, see Trunk Mode and Native VLAN.
Trunk Mode and Native VLAN
On an EX Series switch that runs Junos OS that does not support ELS, a trunk port does not recognize packets that do not include VLAN tags, which are also known an untagged packets. On a switch that runs Junos OS that supports ELS, a trunk port recognizes untagged control packets, but it does not recognize untagged data packets. With native VLAN configured, untagged packets that a trunk port normally does not recognize are sent over the trunk interface. In a situation where packets pass from a device, such as an IP phone or printer, to a switch in access mode, and you want those packets sent from the switch over a trunk port, use native VLAN mode. Create a native VLAN by configuring a VLAN ID for it, and specify that the trunk port is a member of the native VLAN.
The switch’s trunk port will then treat those packets differently than the other tagged packets. For example, if a trunk port has three VLANs, 10, 20, and 30, assigned to it with VLAN 10 being the native VLAN, packets on VLAN 10 that leave the trunk port on the other end have no 802.1Q header (tag).
To configure the native VLAN identifier, see Layer 2 Networking.
You can have the switch add tags for the untagged packets and remove tags from the tagged packets. For example, if you have two interfaces, and an untagged packet passes into the first interface with a user-configured native VLAN ID, it passes out of the second interface with the same VLAN ID as the tagged packet. A tagged packet that passes into the second interface passes out of the first interface as an untagged packet.
Tagged-Access Mode
Starting in Junos OS Release 15.2, only SRX firewalls and EX Series switches that run Junos OS and in the non-ELS configuration style support tagged-access mode.
Maximum VLANs and VLAN Members Per Switch
Starting in Junos OS Release 17.3 on QFX10000 switches, the number of vmembers has increased to 256k for integrated routing and bridging interfaces and aggregated Ethernet interfaces.
Starting in Junos OS Release 22.3R2-S2, the number of active VLANs allowed for EX4100-48t is less than 1000.
The number of VLANs supported per switch varies for each switch. Use the configuration-mode command set vlans vlan-name vlan-id ? to determine the maximum number of VLANs allowed on a switch. You cannot exceed this VLAN limit because you have to assign a specific ID number when you create a VLAN—you could overwrite one of the numbers, but you cannot exceed the limit.
You can, however, exceed the recommended VLAN member maximum for a switch.
On an EX Series switch that runs Junos OS that does not support the ELS configuration style, the maximum number of VLAN members allowed on the switch is eight times the maximum number of VLANs that the switch supports (vmember limit = vlan max * 8). If the configuration of the switch exceeds the recommended VLAN member maximum, a warning message appears when you commit the configuration. If you commit the configuration despite the warning, the commit succeeds, but there is a risk of the Ethernet switching process (eswd) failing as a result of memory allocation failure.
On most switches running Junos OS that supports ELS, the maximum number of VLAN members allowed on the switch is 24 times the maximum number of VLANs that the switch supports (vmember limit = vlan max * 24). If the configuration of the switch exceeds the recommended VLAN member maximum, a warning message appears in the system log (syslog).
The maximum number of VLAN members allowed on these switches are as follows:
EX2300—8 times the maximum number of VLANs that the switch supports (vmember limit = vlan max * 8)
EX3400—16 times the maximum number of VLANs that the switch supports (vmember limit = vlan max * 16)
EX4100—64 times the maximum number of VLANs that the switch supports (vmember limit = vlan max * 1)
EX4300—24 times the maximum number of VLANs that the switch supports (vmember limit = vlan max * 24)
EX4400—64 times the maximum number of VLANs that the switch supports (vmember limit = vlan max * 1)
A QFabric system supports up to 131,008 VLAN members (vmembers) on a single network node group, server node group, or redundant server node group. The number of vmembers is calculated by multiplying the maximum number of VLANs by 32.
For example, to calculate how many interfaces are required to support 4,000 VLANs, divide the maximum number of vmembers (128,000) by the number of configured VLANs (4,000). In this case, 32 interfaces are required.
On network Node groups and server Node groups, you can configure link aggregation groups (LAGs) across multiple interfaces. Each LAG and VLAN combination is considered a vmember.
LAG is not supported on NFX150 devices.
A Virtual Chassis Fabric supports up to 512,000 vmembers. The number of vmembers is based on the number of VLANs, and the number of interfaces configured in each VLAN.
You cannot configure a default VLAN on NFX150 devices.
Assigning Traffic to VLANs
You can assign traffic on any switch to a particular VLAN by referencing either the interface port of the traffic or the MAC addresses of devices sending traffic.
Two logical interfaces that are configured on the same physical interface cannot be mapped to the same VLAN.
- Assign VLAN Traffic According to the Interface Port Source
- Assign VLAN Traffic According to the Source MAC Address
Assign VLAN Traffic According to the Interface Port Source
This method is most commonly used to assign traffic to VLANs. In this case, you specify that all traffic received on a particular switch interface is assigned to a specific VLAN. You configure this VLAN assignment when you configure the switch, by using either the VLAN number (called a VLAN ID) or by using the VLAN name, which the switch then translates into a numeric VLAN ID. This method is referred to ascreating a VLAN membership,because it is the most commonly used method, and is used for switches running Junos OS that supports ELS. For EX Series switches running Junos OS that do not support ELS, you can configure the switch only by using the VLAN number.
Assign VLAN Traffic According to the Source MAC Address
In this case, all traffic destined for a specific MAC address is forwarded to a specific egress interface (next hop) on the switch. MAC-based VLANs are either static (via configuration) or dynamic (via 802.1X authentication).
To configure a static MAC-based VLAN on a switch that supports ELS, see Adding a Static MAC Address Entry to the Ethernet Switching Table.To configure a static MAC-based VLAN on a switch that does not support ELS, see Adding a Static MAC Address Entry to the Ethernet Switching Table.
For information about using 802.1X authentication to authenticate end devices and allow access to dynamic VLANs configured on a RADIUS server, see Understanding Dynamic VLAN Assignment Using RADIUS Attributes. You can optionally implement this feature to offload the manual assignment of VLAN traffic to automated RADIUS server databases.
Forwarding VLAN Traffic
To pass traffic within a VLAN, the switch uses Layer 2 forwarding protocols, including IEEE 802.1Q spanning-tree protocols.
To pass traffic between two VLANs, the switch uses standard Layer 3 routing protocols, such as static routing, OSPF, and RIP. The same interfaces that support Layer 2 bridging protocols also support Layer 3 routing protocols, providing multilayer switching.
To pass traffic from a single device on an access port to a switch and then pass those packets on a trunk port, use the native mode configuration previously discussed under Trunk Mode.
VLANs Communicate with Integrated Routing and Bridging Interfaces
Traditionally, switches sent traffic to hosts that were part of the same broadcast domain (VLAN) but routers were needed to route traffic from one broadcast domain to another. Also, only routers performed other Layer 3 functions such as traffic engineering.
Switches perform inter-VLAN routing functions using an integrated routing and bridging (IRB) interface named irb. These interfaces detect both MAC addresses and IP addresses and route data to Layer 3 interfaces, thereby frequently eliminating the need to have both a switch and a router.
To configure the IRB interface, see Layer 2 Networking.
VPLS Ports
You can configure VPLS ports in a virtual switch instead of a dedicated routing instance of type vpls so that the logical interfaces of the Layer 2 VLANs in the virtual switch can handle VPLS routing instance traffic. Packets received on a Layer 2 trunk interface are forwarded within a VLAN that has the same VLAN identifier.
See Also
Enabling a VLAN
A VLAN must include a set of logical interfaces that participate in Layer 2 learning and forwarding. You can optionally configure a VLAN identifier and a Layer 3 interface for the VLAN to also support Layer 3 IP routing. To configure a VLAN, see Layer 2 Networking.
To enable a VLAN, include the following statements:
[edit]
vlans {
vlan-name {
interface interface-name;
l3-interface interface-name;
vlan-id (none | all | number);
vlan-id-list [ vlan-id-numbers ];
vlan-tags outer number inner number);
}
}
You cannot use the slash (/) character in VLAN names. If you do, the configuration does not commit and an error is generated.
For the vlan-id statement, you can specify either
a valid VLAN identifier or the none or all options.
To include one or more logical interfaces in the VLAN, specify
an interface-name for an Ethernet interface
you configured at the [edit interfaces] hierarchy level.
A maximum of 4096 active logical interfaces are supported for a VLAN or on each mesh group in a virtual private LAN service (VPLS) instance configured for Layer 2 bridging.
By default, each VLAN maintains a Layer 2 forwarding database that contains media access control (MAC) addresses learned from packets received on the ports that belong to the VLAN. You can modify Layer 2 forwarding properties, for example, disabling MAC learning for the entire system or a VLAN, adding static MAC addresses for specific logical interfaces, and limiting the number of MAC addresses learned by the entire system, the VLAN, or a logical interface.
You can also configure spanning tree protocols to prevent forwarding loops.
Configuring VLANs on Switches with Enhanced Layer 2 Support
Switches use VLANs to make logical groupings of network nodes with their own broadcast domains. You can use VLANs to limit the traffic flowing across the entire LAN and reduce collisions and packet retransmissions. To configure layer 2 interfaces, see Layer 2 Networking.
These steps are also applicable to ACX routers, SRX firewalls, and NFX series devices.
For ELS details, see Using the Enhanced Layer 2 Software CLI.
Starting with Junos OS Release 17.1R3, on QFX10000 switches, you cannot configure an
interface with both family ethernet-switching and
flexible-vlan-tagging. This configuration is not supported, and a warning
will be issued if you try to commit this configuration.
Two logical interfaces that are configured on the same physical interface cannot be mapped to the same VLAN or have an overlapping VLAN ID.
For each endpoint on the VLAN, configure the following VLAN parameters on the corresponding interface:
See Also
Configuring VLANs on QFX Series Switches without Enhanced Layer 2 Support
Switches use VLANs to make logical groupings of network nodes with their own broadcast domains. You can use VLANs to limit the traffic flowing across the entire LAN and reduce collisions and packet retransmissions.
For each endpoint on the VLAN, configure the following VLAN parameters on the corresponding interface:
See Also
Example: Configuring VLANs on Security Devices
This example shows you how to configure a VLAN.
Requirements
Before you begin:
Determine which interfaces to use and verify that they are in switching mode. See Understanding VLANs.
Determine what ports to use on the device and how to segment your network. See Ethernet Ports Switching Overview for Security Devices.
Overview
In this example, you create a new VLAN and then configure its attributes. You can configure one or more VLANs to perform Layer 2 switching. The Layer 2 switching functions include integrated routing and bridging (IRB) for support for Layer 2 switching and Layer 3 IP routing on the same interface. SRX Series Firewalls can function as Layer 2 switches, each with multiple switching or broadcast domains that participate in the same Layer 2 network.
Configuration
Procedure
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set interfaces ge-0/0/1 unit 0 family ethernet-switching interface-mode access set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members v10 set vlans v10 vlan-id 10 set vlans v10 l3-interface irb.10 set interfaces irb unit 10 family inet address 198.51.100.0/24
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode in the CLI User Guide.
To configure a VLAN:
Configure a Gigabit Ethernet interface or a 10-Gigabit Ethernet interface as a access interface:
[edit interfaces] user@host# set ge-0/0/1 unit 0 family ethernet-switching interface-mode access
Assign an interface to the VLAN by specifying the logical interface (with the unit statement) and specifying the VLAN name as the member.
[edit interfaces] user@host# set ge-0/0/1 unit 0 family ethernet-switching vlan members v10
Create the VLAN by setting the unique VLAN name and configuring the VLAN ID.
[edit] user@host# set vlans v10 vlan-id 10
Bind a Layer 3 interface with the VLAN.
[edit] user@host# set vlans v10 l3-interface irb.10
Create the subnet for the VLAN’s broadcast domain.
[edit interfaces] user@host# set irb unit 10 family inet address 198.51.100.0/24
Results
From configuration mode, confirm your configuration
by entering the show vlans command. If the output does
not display the intended configuration, repeat the configuration instructions
in this example to correct it.
[edit]
user@host# show vlans
v10 {
vlan-id 10;
l3-interface irb.10;
}
user@host# show interfaces
ge-0/0/1 {
unit 0 {
family ethernet-switching {
interface-mode access;
vlan {
members v10;
}
}
}
irb {
unit 10 {
family inet {
address 198.51.100.0/24;
}
}
}
}If you are done configuring the device, enter commit from configuration mode.
Verification
Verifying VLANs
Purpose
Verify that VLANs are configured and assigned to the interfaces.
Action
From operational mode, enter the show vlans command.
user@host> show vlans
Routing instance VLAN name Tag Interfaces
default-switch default 1
default-switch v10 10
ge-0/0/1.0Meaning
The output shows the VLAN is configured and assigned to the interface.
Example: Setting Up Basic Bridging and a VLAN for an EX Series Switch with ELS Support
This example uses Junos OS for EX Series switches with support for the Enhanced Layer 2 Software (ELS) configuration style. If your switch runs Junos OS that does not support ELS, see Example: Setting Up Basic Bridging and a VLAN for an EX Series Switch. For ELS details, see Using the Enhanced Layer 2 Software CLI.
EX Series switches use bridging and virtual LANs (VLANs) to connect network devices in a LAN—desktop computers or laptops, IP telephones, printers, file servers, wireless access points, and others—and to segment the LAN into smaller broadcast domains.
This example describes how to configure basic bridging and a VLAN on an EX Series switch:
Requirements
This example uses the following hardware and software components:
One EX Series switch
Junos OS Release 13.2X50-D10 or later for EX Series switches
Before you set up bridging and a VLAN, be sure you have:
Installed your EX Series switch. See the installation instructions for your switch.
Performed the initial switch configuration. See Connecting and Configuring an EX Series Switch (CLI Procedure).
Overview and Topology
EX Series switches connect network devices in an office LAN or a data center LAN to provide sharing of common resources such as printers and file servers and to enable wireless devices to connect to the LAN through wireless access points. Without bridging and VLANs, all devices on the Ethernet LAN are in a single broadcast domain, and all the devices detect all the packets on the LAN. Bridging creates separate broadcast domains on the LAN, creating VLANs, which are independent logical networks that group together related devices into separate network segments. The grouping of devices on a VLAN is independent of where the devices are physically located in the LAN.
To use an EX Series switch to connect network devices on a LAN, you must, at a minimum, explicitly configure at least one VLAN, even if your network is simple and you want only one broadcast domain to exist, as is the case with this example. You must also assign all needed interfaces to the VLAN, after which the interfaces function in access mode. After the VLAN is configured, you can plug access devices—such as desktop or laptop computers, IP telephones, file servers, printers, and wireless access points—into the switch, and they are joined immediately into the VLAN, and the LAN is up and running.
The topology used in this example consists of one EX4300-24P switch, which has a total of 24 ports. All ports support Power over Ethernet (PoE), which means they provide both network connectivity and electric power for the device connecting to the port. To these ports, you can plug in devices requiring PoE, such as Avaya VoIP telephones, wireless access points, and some IP cameras. (Avaya phones have a built-in hub that allows you to connect a desktop PC to the phone, so the desktop and phone in a single office require only one port on the switch.) Table 1 details the topology used in this configuration example.
| Property | Settings |
|---|---|
Switch hardware |
EX4300-24P switch, with 24 Gigabit Ethernet ports: in this example, 8 ports are used as PoE ports (ge-0/0/0 through ge-0/0/7 ) and 16 ports used as non-PoE ports (ge-0/0/8 through ge-0/0/23) |
VLAN name |
employee-vlan |
VLAN ID |
10 |
Connection to wireless access point (requires PoE) |
ge-0/0/0 |
Connections to Avaya IP telephone—with integrated hub, to connect phone and desktop PC to a single port (requires PoE) |
ge-0/0/1 through ge-0/0/7 |
Direct connections to desktop PCs and laptops (no PoE required) |
ge-0/0/8 through ge-0/0/12 |
Connections to file servers (no PoE required) |
ge-0/0/17 and ge-0/0/18 |
Connections to integrated printer/fax/copier machines (no PoE required) |
ge-0/0/19 through ge-0/0/20 |
Unused ports (for future expansion) |
ge-0/0/13 through ge-0/0/16, and ge-0/0/21 through ge-0/0/23 |
Topology
Configuration
To set up basic bridging and a VLAN:
Procedure
CLI Quick Configuration
To quickly configure a VLAN, copy the following commands and paste them into the switch terminal window:
[edit] set vlans employee-vlan vlan-id 10 set interfaces ge-0/0/0 unit 0 family ethernet-switching vlan members employee-vlan set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members employee-vlan set interfaces ge-0/0/2 unit 0 family ethernet-switching vlan members employee-vlan set interfaces ge-0/0/3 unit 0 family ethernet-switching vlan members employee-vlan set interfaces ge-0/0/4 unit 0 family ethernet-switching vlan members employee-vlan set interfaces ge-0/0/5 unit 0 family ethernet-switching vlan members employee-vlan set interfaces ge-0/0/6 unit 0 family ethernet-switching vlan members employee-vlan set interfaces ge-0/0/7 unit 0 family ethernet-switching vlan members employee-vlan set interfaces ge-0/0/8 unit 0 family ethernet-switching vlan members employee-vlan set interfaces ge-0/0/9 unit 0 family ethernet-switching vlan members employee-vlan set interfaces ge-0/0/10 unit 0 family ethernet-switching vlan members employee-vlan set interfaces ge-0/0/11 unit 0 family ethernet-switching vlan members employee-vlan set interfaces ge-0/0/12 unit 0 family ethernet-switching vlan members employee-vlan set interfaces ge-0/0/17 unit 0 family ethernet-switching vlan members employee-vlan set interfaces ge-0/0/18 unit 0 family ethernet-switching vlan members employee-vlan set interfaces ge-0/0/19 unit 0 family ethernet-switching vlan members employee-vlan set interfaces ge-0/0/20 unit 0 family ethernet-switching vlan members employee-vlan
You must then plug the wireless access point into PoE-enabled
port ge-0/0/0 and the Avaya IP phones into the PoE-enabled
ports ge-0/0/1 through ge-0/0/7. Also, plug the
PCs, file servers, and printers into ports ge-0/0/8 through ge-0/0/12 and ge-0/0/17 through ge-0/0/20.
Step-by-Step Procedure
To set up basic bridging and a VLAN:
Create a VLAN named employee-vlan and specify the VLAN ID of 10 for it:
[edit vlans] user@switch# set employee-vlan vlan-id 10
Assign interfaces ge-0/0/0 through ge-0/0/12, and ge-0/0/17 through ge-0/0/20 to the employee-vlan VLAN:
[edit interface] user@switch# set ge-0/0/0 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set ge-0/0/1 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set ge-0/0/2 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set ge-0/0/3 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set ge-0/0/4 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set ge-0/0/5 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set ge-0/0/6 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set ge-0/0/7 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set ge-0/0/8 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set ge-0/0/9 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set ge-0/0/10 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set ge-0/0/11 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set ge-0/0/12 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set ge-0/0/17 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set ge-0/0/18 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set ge-0/0/19 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set ge-0/0/20 unit 0 family ethernet-switching vlan members employee-vlan
Connect the wireless access point to switch port ge-0/0/0.
Connect the seven Avaya phones to switch ports ge-0/0/1 through ge-0/0/7.
Connect the five PCs to ports ge-0/0/8 through ge-0/0/12.
Connect the two file servers to ports ge-0/0/17 and ge-0/0/18.
Connect the two printers to ports ge-0/0/19 and ge-0/0/20.
Results
Check the results of the configuration:
user@switch> show configuration
ge-0/0/0 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
ge-0/0/1 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
ge-0/0/2 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
ge-0/0/3 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
ge-0/0/4 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
ge-0/0/5 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
ge-0/0/6 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
ge-0/0/7 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
ge-0/0/8 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
ge-0/0/9 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
ge-0/0/10 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
ge-0/0/11 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
ge-0/0/12 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
ge-0/0/17 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
ge-0/0/18 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
ge-0/0/19 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
ge-0/0/20 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}Verification
To verify that switching is operational and
that employee-vlan has been created, perform these tasks:
- Verifying That the VLAN Has Been Created
- Verifying That Interfaces Are Associated with the Proper VLANs
Verifying That the VLAN Has Been Created
Purpose
Verify that the VLAN named employee-vlan has been created on the switch.
Action
List all VLANs configured on the switch:
user@switch> show vlans
Routing instance VLAN name Tag Interfaces
default-switch employee-vlan 10
ge-0/0/0.0
ge-0/0/1.0
ge-0/0/2.0
ge-0/0/3.0
ge-0/0/4.0
ge-0/0/5.0
ge-0/0/6.0
ge-0/0/7.0
ge-0/0/8.0
ge-0/0/9.0
ge-0/0/10.0
ge-0/0/11.0
ge-0/0/12.0
ge-0/0/17.0
ge-0/0/18.0
ge-0/0/19.0
ge-0/0/20.0
...
Meaning
The show vlans command lists the VLANs configured
on the switch. This output shows that the VLAN employee-vlan has been created.
Verifying That Interfaces Are Associated with the Proper VLANs
Purpose
Verify that Ethernet switching is enabled on switch interfaces and that all interfaces are included in the VLAN.
Action
List all interfaces on which switching is enabled:
user@switch> show ethernet-switching interfaces
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
ge-0/0/0.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
ge-0/0/1.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
ge-0/0/2.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
ge-0/0/3.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
ge-0/0/4.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
ge-0/0/5.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
ge-0/0/6.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
ge-0/0/7.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
ge-0/0/8.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
ge-0/0/9.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
ge-0/0/10.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
ge-0/0/11.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
ge-0/0/12.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
ge-0/0/17.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
ge-0/0/18.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
ge-0/0/19.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
ge-0/0/20.0 65535 untagged
employee-vlan 10
65535 Discarding
...Meaning
The show ethernet-switching interfaces command
lists all interfaces on which switching is enabled (in the Logical
interface column), along with the VLANs that are active on the
interfaces (in the VLAN members column). The output in this
example shows all the connected interfaces, ge-0/0/0 through ge-0/0/12
and ge-0/0/17 through ge-0/0/20 and that they are all part of VLAN employee-vlan. Notice that the interfaces listed are the logical
interfaces, not the physical interfaces. For example, the output shows
ge-0/0/0.0 instead of ge-0/0/0. This is because Junos OS creates VLANs
on logical interfaces, not directly on physical interfaces.
Example: Setting Up Basic Bridging and a VLAN on Switches
The QFX Series products use bridging and virtual LANs (VLANs) to connect network devices—storage devices, file servers, and other LAN components—in a LAN and to segment the LAN into smaller bridging domains.
To segment traffic on a LAN into separate broadcast domains, you create separate virtual LANs (VLANs) on a switch. Each VLAN is a collection of network nodes. When you use VLANs, frames whose origin and destination are in the same VLAN are forwarded only within the local VLAN, and only frames not destined for the local VLAN are forwarded to other broadcast domains. VLANs thus limit the amount of traffic flowing across the entire LAN, reducing the possible number of collisions and packet retransmissions within the LAN.
You cannot configure more than one logical interface that belongs to the same physical interface in the same bridge domain.
This example describes how to configure basic bridging and VLANs for the QFX Series:
Requirements
This example uses the following software and hardware components:
Junos OS Release 11.1 or later for the QFX Series
A configured and provisioned QFX Series product
Overview and Topology
To use a switch to connect network devices on a LAN, you must at a minimum configure bridging and VLANs. By default, bridging is enabled on all switch interfaces, all interfaces are in access mode, and all interfaces belong to a VLAN called employee-vlan, which is automatically configured. When you plug in access devices—such as desktop computers, file servers, and printers—they are joined immediately into the employee-vlan VLAN, and the LAN is up and running.
The topology used in this example consists of a single QFX3500 switch, with a total of 48 10-Gbps Ethernet ports. (For the purposes of this example, the QSFP+ ports Q0-Q3, which are ports xe-0/1/0 through xe-0/1/15, are excluded.) You use the ports to connect devices that have their own power sources. Table 1 details the topology used in this configuration example.
Property |
Settings |
|---|---|
Switch hardware |
QFX3500 switch, with 48 10-Gbps Ethernet ports |
VLAN name |
employee-vlan |
VLAN ID |
10 |
Connections to file servers |
xe-0/0/17 and xe-0/0/18 |
Direct connections to desktop PCs and laptops |
xe-0/0/0 through xe-0/0/16 |
Connections to integrated printer/fax/copier machines |
xe-0/0/19 through xe-0/0/40 |
Unused ports |
xe-0/0/41 through xe-0/0/47 |
Topology
Configuration
Procedure
CLI Quick Configuration
To quickly configure a VLAN, copy the following commands and paste them into the switch terminal window:
[edit] set vlans employee-vlan vlan-id 10 set interfaces xe-0/0/0 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/1 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/2 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/3 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/4 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/5 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/6 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/7 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/8 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/9 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/10 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/11 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/12 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/13 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/14 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/15 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/16 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/17 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/18 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/19 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/20 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/21 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/22 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/23 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/24 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/25 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/26 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/27 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/28 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/29 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/30 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/31 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/32 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/33 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/34 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/35 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/36 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/37 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/38 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/39 unit 0 family ethernet-switching vlan members employee-vlan set interfaces xe-0/0/40 unit 0 family ethernet-switching vlan members employee-vlan
Step-by-Step Procedure
To set up basic bridging and a VLAN:
Create a VLAN named employee-vlan and specify the VLAN ID of 10 for it:
[edit vlans] user@switch# set employee-vlan vlan-id 10
Assign interfaces xe-0/0/0 through xe-0/0/40 to the employee-vlan VLAN:
[edit interface] user@switch# set xe-0/0/0 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/1 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/2 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/3 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/4 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/5 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/6 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/7 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/8 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/9 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/10 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/11 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/12 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/13 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/14 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/15 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/16 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/17 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/18 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/19 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/20 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/21 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/22 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/23 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/24 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/25 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/26 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/27 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/28 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/29 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/30 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/31 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/32 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/33 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/34 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/35 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/36 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/37 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/38 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/39 unit 0 family ethernet-switching vlan members employee-vlan user@switch# set xe-0/0/40 unit 0 family ethernet-switching vlan members employee-vlan
Connect the two file servers to ports xe-0/0/17 and xe-0/0/18.
Connect the desktop PCs and laptops to ports xe-0/0/0 through xe-0/0/16.
Connect the integrated printer/fax/copier machines to ports xe-0/0/19 through xe-0/0/40.
Results
Check the results of the configuration:
user@switch> show configuration
xe-0/0/0 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/1 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/2 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/3 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/4 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/5 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/6 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/7 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/8 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/9 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/10 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/11 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/12 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/13 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/14 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/15 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/16 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/17 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/18 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/19 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/20 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/21 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/22 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/23 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/24 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/25 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/26 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/27 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/28 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/29 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/30 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/31 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/32 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/33 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/34 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/35 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/36 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/37 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/38 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/39 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}
xe-0/0/40 {
unit 0 {
family ethernet-switching {
vlan {
members employee-vlan;
}
}
}
}Verification
To verify that switching is operational and
that employee-vlan has been created, perform these tasks:
- Verifying That the VLAN Has Been Created
- Verifying That Interfaces Are Associated with the Proper VLANs
Verifying That the VLAN Has Been Created
Purpose
Verify that the VLAN named employee-vlan has been created on the switch.
Action
List all VLANs configured on the switch:
user@switch> show vlans
Routing instance VLAN name Tag Interfaces
default-switch employee-vlan 10
xe-0/0/0.0
xe-0/0/1.0
xe-0/0/2.0
xe-0/0/3.0
xe-0/0/4.0
xe-0/0/5.0
xe-0/0/6.0
xe-0/0/7.0
xe-0/0/8.0
xe-0/0/9.0
xe-0/0/10.0
xe-0/0/11.0
xe-0/0/12.0
xe-0/0/13.0
xe-0/0/14.0
xe-0/0/15.0
xe-0/0/16.0
xe-0/0/17.0
xe-0/0/18.0
xe-0/0/19.0
xe-0/0/20.0
xe-0/0/21.0
xe-0/0/22.0
xe-0/0/23.0
xe-0/0/24.0
xe-0/0/25.0
xe-0/0/26.0
xe-0/0/27.0
xe-0/0/28.0
xe-0/0/29.0
xe-0/0/30.0
xe-0/0/31.0
xe-0/0/32.0
xe-0/0/33.0
xe-0/0/34.0
xe-0/0/35.0
xe-0/0/36.0
xe-0/0/37.0
xe-0/0/38.0
xe-0/0/39.0
xe-0/0/40.0
...
Meaning
The show vlans command lists the VLANs configured
on the switch. This output shows that the VLAN employee-vlan has been created.
Verifying That Interfaces Are Associated with the Proper VLANs
Purpose
Verify that Ethernet switching is enabled on switch interfaces and that all interfaces are included in the VLAN.
Action
List all interfaces on which switching is enabled:
user@switch> show ethernet-switching interfaces
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/0.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/1.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/2.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/3.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/4.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/5.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/6.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/7.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/8.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/9.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/10.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/11.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/12.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/13.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/14.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/15.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/16.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/17.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/18.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/19.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/20.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/21.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/22.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/23.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/24.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/25.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/26.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/27.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/28.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/29.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/30.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/31.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/32.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/33.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/34.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/35.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/36.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/37.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/38.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/39.0 65535 untagged
employee-vlan 10
65535 Discarding
Routing Instance Name : default-switch
Logical Interface flags (DL - disable learning, AD - packet action drop,
LH - MAC limit hit, DN - interface down )
Logical Vlan TAG MAC STP Logical Tagging
interface members limit state interface flags
xe-0/0/40.0 65535 untagged
employee-vlan 10
65535 Discarding
...Meaning
The show ethernet-switching interfaces command
lists all interfaces on which switching is enabled (in the Logical
interface column), along with the VLANs that are active on the
interfaces (in the VLAN members column). The output in this
example shows all the connected interfaces, xe-0/0/0 through xe-0/0/40,
are all part of VLAN employee-vlan. Notice that the interfaces
listed are the logical interfaces, not the physical interfaces. For
example, the output shows xe-0/0/0.0 instead of xe-0/0/0. This is
because Junos OS creates VLANs on logical interfaces, not directly
on physical interfaces.
Example: Setting Up Basic Bridging and a VLAN for an EX Series Switch
This example uses Junos OS for EX Series switches that does not support the Enhanced Layer 2 Software (ELS) configuration style. If your switch runs software that supports ELS, see Example: Setting Up Basic Bridging and a VLAN for an EX Series Switch with ELS Support . For ELS details, see Using the Enhanced Layer 2 Software CLI
EX Series switches use bridging and virtual LANs (VLANs) to connect network devices in a LAN—desktop computers, IP telephones, printers, file servers, wireless access points, and others—and to segment the LAN into smaller bridging domains. The switch's default configuration provides a quick setup of bridging and a single VLAN.
This example describes how to configure basic bridging and VLANs for an EX Series switch:
Requirements
This example uses the following software and hardware components:
Junos OS Release 9.0 or later for EX Series switches
One EX4200 Virtual Chassis switch
Before you set up bridging and a VLAN, be sure you have:
Performed the initial switch configuration. See Connecting and Configuring an EX Series Switch (J-Web Procedure).
Overview and Topology
EX Series switches connect network devices in an office LAN or a data center LAN to provide sharing of common resources such as printers and file servers and to enable wireless devices to connect to the LAN through wireless access points. Without bridging and VLANs, all devices on the Ethernet LAN are in a single broadcast domain, and all the devices detect all the packets on the LAN. Bridging creates separate broadcast domains on the LAN, creating VLANs, which are independent logical networks that group together related devices into separate network segments. The grouping of devices on a VLAN is independent of where the devices are physically located in the LAN.
To use an EX Series switch to connect network devices on a LAN, you must, at a minimum, configure bridging and VLANs. If you simply power on the switch and perform the initial switch configuration using the factory-default settings, bridging is enabled on all the switch's interfaces, all interfaces are in access mode, and all interfaces belong to a VLAN called default, which is automatically configured. When you plug access devices—such as desktop computers, Avaya IP telephones, file servers, printers, and wireless access points—into the switch, they are joined immediately into the default VLAN and the LAN is up and running.
The topology used in this example consists of one EX4200-24T switch, which has a total of 24 ports. Eight of the ports support Power over Ethernet (PoE), which means they provide both network connectivity and electric power for the device connecting to the port. To these ports, you can plug in devices requiring PoE, such as Avaya VoIP telephones, wireless access points, and some IP cameras. (Avaya phones have a built-in hub that allows you to connect a desktop PC to the phone, so the desktop and phone in a single office require only one port on the switch.) The remaining 16 ports provide only network connectivity. You use them to connect devices that have their own power sources, such as desktop and laptop computers, printers, and servers. Table 3 details the topology used in this configuration example.
| Property | Settings |
|---|---|
Switch hardware |
EX4200-24T switch, with 24 Gigabit Ethernet ports: 8 PoE ports (ge-0/0/0 through ge-0/0/7) and 16 non-PoE ports (ge-0/0/8 through ge-0/0/23) |
VLAN name |
default |
Connection to wireless access point (requires PoE) |
ge-0/0/0 |
Connections to Avaya IP telephone—with integrated hub, to connect phone and desktop PC to a single port (requires PoE) |
ge-0/0/1 through ge-0/0/7 |
Direct connections to desktop PCs (no PoE required) |
ge-0/0/8 through ge-0/0/12 |
Connections to file servers (no PoE required) |
ge-0/0/17 and ge-0/0/18 |
Connections to integrated printer/fax/copier machines (no PoE required) |
ge-0/0/19 through ge-0/0/20 |
Unused ports (for future expansion) |
ge-0/0/13 through ge-0/0/16, and ge-0/0/21 through ge-0/0/23 |
Topology
Configuration
Procedure
CLI Quick Configuration
By default, after you perform the initial configuration on the EX4200 switch, switching is enabled on all interfaces, a VLAN named default is created, and all interfaces are placed into this VLAN. You do not need to perform any other configuration on the switch to set up bridging and VLANs. To use the switch, simply plug the Avaya IP phones into the PoE-enabled ports ge-0/0/1 through ge-0/0/7, and plug in the PCs, file servers, and printers to the non-PoE ports, ge-0/0/8 through ge-0/0/12 and ge-0/0/17 through ge-0/0/20.
Step-by-Step Procedure
To configure bridging and VLANs:
Make sure the switch is powered on.
Connect the wireless access point to switch port ge-0/0/0.
Connect the seven Avaya phones to switch ports ge-0/0/1 through ge-0/0/7.
Connect the five PCs to ports ge-0/0/8 through ge-0/0/12.
Connect the two file servers to ports ge-0/0/17 and ge-0/0/18.
Connect the two printers to ports ge-0/0/19 and ge-0/0/20.
Results
Check the results of the configuration:
user@switch> show configuration
## Last commit: 2008-03-06 00:11:22 UTC by triumph
version 9.0;
system {
root-authentication {
encrypted-password "$1$urmA7AFM$x5SaGEUOdSI3u1K/iITGh1"; ## SECRET-DATA
}
syslog {
user * {
any emergency;
}
file messages {
any notice;
authorization info;
}
file interactive-commands {
interactive-commands any;
}
}
commit {
factory-settings {
reset-chassis-lcd-menu;
reset-virtual-chassis-configuration;
}
}
}
interfaces {
ge-0/0/0 {
unit 0 {
family ethernet-switching;
}
}
ge-0/0/1 {
unit 0 {
family ethernet-switching;
}
}
ge-0/0/2 {
unit 0 {
family ethernet-switching;
}
}
ge-0/0/3 {
unit 0 {
family ethernet-switching;
}
}
ge-0/0/4 {
unit 0 {
family ethernet-switching;
}
}
ge-0/0/5 {
unit 0 {
family ethernet-switching;
}
}
ge-0/0/6 {
unit 0 {
family ethernet-switching;
}
}
ge-0/0/7 {
unit 0 {
family ethernet-switching;
}
}
ge-0/0/8 {
unit 0 {
family ethernet-switching;
}
}
ge-0/0/9 {
unit 0 {
family ethernet-switching;
}
}
ge-0/0/10 {
unit 0 {
family ethernet-switching;
}
}
ge-0/0/11 {
unit 0 {
family ethernet-switching;
}
}
ge-0/0/12 {
unit 0 {
family ethernet-switching;
}
}
ge-0/0/13 {
unit 0 {
family ethernet-switching;
}
}
ge-0/0/14 {
unit 0 {
family ethernet-switching;
}
}
ge-0/0/15 {
unit 0 {
family ethernet-switching;
}
}
ge-0/0/16 {
unit 0 {
family ethernet-switching;
}
}
ge-0/0/17 {
unit 0 {
family ethernet-switching;
}
}
ge-0/0/18 {
unit 0 {
family ethernet-switching;
}
}
ge-0/0/19 {
unit 0 {
family ethernet-switching;
}
}
ge-0/0/20 {
unit 0 {
family ethernet-switching;
}
}
ge-0/0/21 {
unit 0 {
family ethernet-switching;
}
}
ge-0/0/22 {
unit 0 {
family ethernet-switching;
}
}
ge-0/0/23 {
unit 0 {
family ethernet-switching;
}
}
ge-0/1/0 {
unit 0 {
family ethernet-switching;
}
}
xe-0/1/0 {
unit 0 {
family ethernet-switching;
}
}
ge-0/1/1 {
unit 0 {
family ethernet-switching;
}
}
xe-0/1/1 {
unit 0 {
family ethernet-switching;
}
}
ge-0/1/2 {
unit 0 {
family ethernet-switching;
}
}
ge-0/1/3 {
unit 0 {
family ethernet-switching;
}
}
}
protocols {
lldp {
interface all;
}
rstp;
poe {
interface all;
}
}Verification
To verify that switching is operational and that a VLAN has been created, perform these tasks:
- Verifying That the VLAN Has Been Created
- Verifying That Interfaces Are Associated with the Proper VLANs
Verifying That the VLAN Has Been Created
Purpose
Verify that the VLAN named default has been created on the switch.
Action
List all VLANs configured on the switch:
user@switch> show vlans
Name Tag Interfaces
default
ge-0/0/0.0*, ge-0/0/1.0, ge-0/0/2.0, ge-0/0/3.0,
ge-0/0/4.0, ge-0/0/5.0, ge-0/0/6.0, ge-0/0/7.0,
ge-0/0/8.0*, ge-0/0/9.0, ge-0/0/10.0, ge-0/0/11.0*,
ge-0/0/12.0, ge-0/0/13.0, ge-0/0/14.0, ge-0/0/15.0,
ge-0/0/16.0, ge-0/0/17.0, ge-0/0/18.0, ge-0/0/19.0*,
ge-0/0/20.0, ge-0/0/21.0, ge-0/0/22.0, ge-0/0/23.0,
ge-0/1/0.0*, ge-0/1/1.0*, ge-0/1/2.0*, ge-0/1/3.0*
mgmt
me0.0*
Meaning
The show vlans command lists the VLANs configured
on the switch. This output shows that the VLAN default has
been created.
Verifying That Interfaces Are Associated with the Proper VLANs
Purpose
Verify that Ethernet switching is enabled on switch interfaces and that all interfaces are included in the VLAN.
Action
List all interfaces on which switching is enabled:
user@switch> show ethernet-switching interfaces Interface State VLAN members Blocking ge-0/0/0.0 up default unblocked ge-0/0/1.0 down default blocked - blocked by STP/RTG ge-0/0/2.0 down default blocked - blocked by STP/RTG ge-0/0/3.0 down default blocked - blocked by STP/RTG ge-0/0/4.0 down default blocked - blocked by STP/RTG ge-0/0/5.0 down default blocked - blocked by STP/RTG ge-0/0/6.0 down default blocked - blocked by STP/RTG ge-0/0/7.0 down default blocked - blocked by STP/RTG ge-0/0/8.0 up default unblocked ge-0/0/9.0 down default blocked - blocked by STP/RTG ge-0/0/10.0 down default blocked - blocked by STP/RTG ge-0/0/11.0 up default unblocked ge-0/0/12.0 down default blocked - blocked by STP/RTG ge-0/0/13.0 down default blocked - blocked by STP/RTG ge-0/0/14.0 down default blocked - blocked by STP/RTG ge-0/0/15.0 down default blocked - blocked by STP/RTG ge-0/0/16.0 down default blocked - blocked by STP/RTG ge-0/0/17.0 down default blocked - blocked by STP/RTG ge-0/0/18.0 down default blocked - blocked by STP/RTG ge-0/0/19.0 up default unblocked ge-0/0/20.0 down default blocked - blocked by STP/RTG ge-0/0/21.0 down default blocked - blocked by STP/RTG ge-0/0/22.0 down default blocked - blocked by STP/RTG ge-0/0/23.0 down default blocked - blocked by STP/RTG ge-0/1/0.0 up default unblocked ge-0/1/1.0 up default unblocked ge-0/1/2.0 up default unblocked ge-0/1/3.0 up default unblocked me0.0 up mgmt unblocked
Meaning
The show ethernet-switching interfaces command
lists all interfaces on which switching is enabled (in the Interfaces column), along with the VLANs that are active on the interfaces
(in the VLAN members column). The output in this example
shows all the connected interfaces, ge-0/0/0 through ge-0/0/12 and ge-0/0/17 through ge-0/0/20 and
that they are all part of VLAN default. Notice that the interfaces
listed are the logical interfaces, not the physical interfaces. For
example, the output shows ge-0/0/0.0 instead of ge-0/0/0. This is because Junos OS creates VLANs on logical interfaces, not
directly on physical interfaces.
Example: Setting Up Bridging with Multiple VLANs
The QFX Series products use bridging and virtual LANs (VLANs) to connect network devices in a LAN—storage devices, file servers, and other network components—and to segment the LAN into smaller bridging domains.
To segment traffic on a LAN into separate broadcast domains, you create separate virtual LANs (VLANs) on a switch. Each VLAN is a collection of network nodes. When you use VLANs, frames whose origin and destination are in the same VLAN are forwarded only within the local VLAN, and only frames not destined for the local VLAN are forwarded to other broadcast domains. VLANs thus limit the amount of traffic flowing across the entire LAN, reducing the possible number of collisions and packet retransmissions within the LAN.
This task uses Junos OS for QFX3500 and QFX3600 switches does not support the Enhanced Layer 2 Software (ELS) configuration style. If your switch runs software that supports ELS, see Example: Setting Up Bridging with Multiple VLANs on Switches.
This example describes how to configure bridging for the QFX Series and how to create two VLANs to segment the LAN:
Requirements
This example uses the following hardware and software components:
A configured and provisioned QFX3500 switch
Junos OS Release 11.1 or later for the QFX Series
Overview and Topology
Switches connect all devices in an office or data center into a single LAN to provide sharing of common resources such as file servers. The default configuration creates a single VLAN, and all traffic on the switch is part of that broadcast domain. Creating separate network segments reduces the span of the broadcast domain and enables you to group related users and network resources without being limited by physical cabling or by the location of a network device in the building or on the LAN.
This example shows a simple configuration to illustrate the basic steps for creating two VLANs on a single switch. One VLAN, called sales, is for the sales and marketing group, and a second, called support, is for the customer support team. The sales and support groups each have their own dedicated file servers and other resources. For the switch ports to be segmented across the two VLANs, each VLAN must have its own broadcast domain, identified by a unique name and tag (VLAN ID). In addition, each VLAN must be on its own distinct IP subnet.
Topology
The topology used in this example consists of a single QFX3500 switch, with a total of 48 10-Gbps Ethernet ports. (For the purposes of this example, the QSFP+ ports Q0-Q3, which are ports xe-0/1/0 through xe-0/1/15, are excluded.)
Property |
Settings |
|---|---|
Switch hardware |
QFX3500 switch configured with 48 10-Gbps Ethernet ports (xe-0/0/0 through xe-0/0/47) |
VLAN names and tag IDs |
sales, tag 100 support, tag 200 |
VLAN subnets |
sales: 192.0.2.0/25 (addresses 192.0.2.1 through 192.0.2.126) support: 192.0.2.128/25 (addresses 192.0.2.129 through 192.0.2.254) |
Interfaces in VLAN sales |
File servers: xe-0/0/20 and xe-0/0/21 |
Interfaces in VLAN support |
File servers: xe-0/0/46 and xe-0/0/47 |
Unused interfaces |
xe-0/0/2 and xe-0/0/25 |
This configuration example creates two IP subnets, one for the sales VLAN and the second for the support VLAN. The switch bridges traffic within a VLAN. For traffic passing between two VLANs, the switch routes the traffic using a Layer 3 routing interface on which you have configured the address of the IP subnet.
To keep the example simple, the configuration steps show only a few devices in each of the VLANs. Use the same configuration procedure to add more LAN devices.
Configuration
Procedure
CLI Quick Configuration
To quickly configure Layer 2 switching for the two VLANs (sales and support) and to quickly configure Layer 3 routing of traffic between the two VLANs, copy the following commands and paste them into the switch terminal window:
[edit]
set interfaces xe-0/0/0 unit 0 family ethernet-switching vlan members sales
set interfaces xe-0/0/3 unit 0 family ethernet-switching vlan members sales
set interfaces xe-0/0/22 unit 0 family ethernet-switching vlan members sales
set interfaces xe-0/0/20 unit 0 description “Sales file server port”
set interfaces xe-0/0/20 unit 0 family ethernet-switching vlan members sales
set interfaces xe-0/0/24 unit 0 family ethernet-switching vlan members support
set interfaces xe-0/0/26 unit 0 family ethernet-switching vlan members support
set interfaces xe-0/0/44 unit 0 family ethernet-switching vlan members support
set interfaces xe-0/0/46 unit 0 description “Support file server port”
set interfaces xe-0/0/46 unit 0 family ethernet-switching vlan members support
set interfaces irb unit 0 family inet address 192.0.2.0/25
set interfaces irb unit 1 family inet address 192.0.2.128/25
set vlans sales l3–interface irb.0
set vlans sales vlan-id 100
set vlans support vlan-id 200
set vlans support l3-interface irb.1 Step-by-Step Procedure
Configure the switch interfaces and the VLANs to which they belong. By default, all interfaces are in access mode, so you do not have to configure the port mode.
Configure the interface for the file server in the sales VLAN:
[edit interfaces xe-0/0/20 unit 0] user@switch# set description “Sales file server port” user@switch# set family ethernet-switching vlan members sales
Configure the interface for the file server in the support VLAN:
[edit interfaces xe-0/0/46 unit 0] user@switch# set description “Support file server port” user@switch# set family ethernet-switching vlan members support
Create the subnet for the sales broadcast domain:
[edit interfaces] user@switch# set irb unit 0 family inet address 192.0.2.1/25
Create the subnet for the support broadcast domain:
[edit interfaces] user@switch# set irb unit 1 family inet address 192.0.2.129/25
Configure the VLAN tag IDs for the sales and support VLANs:
[edit vlans] user@switch# set sales vlan-id 100 user@switch# set support vlan-id 200
To route traffic between the sales and support VLANs, define the interfaces that are members of each VLAN and associate a Layer 3 interface:
[edit vlans] user@switch# set sales l3-interface irb.0 user@switch# set support l3-interface irb.1
Results
Display the results of the configuration:
user@switch> show configuration
interfaces {
xe-0/0/20 {
unit 0 {
description “Sales file server port”;
family ethernet-switching {
vlan members sales;
}
}
}
xe-0/0/46 {
unit 0 {
description “Support file server port”;
family ethernet-switching {
vlan members support;
}
}
}
irb {
unit 0 {
family inet address 192.0.2.1/25;
}
unit 1 {
family inet address 192.0.2.129/25;
}
}
vlans {
sales {
vlan-id 100;
interface xe-0/0/0.0:
interface xe-0/0/3/0;
interface xe-0/0/20.0;
interface xe-0/0/22.0;
l3-interface irb.0;
}
support {
vlan-id 200;
interface xe-0/0/24.0:
interface xe-0/0/26.0;
interface xe-0/0/44.0;
interface xe-0/0/46.0;
l3-interface irb.1;
}
}
}To quickly configure the sales and support VLAN interfaces,
issue the load merge terminal command. Then copy the hierarchy
and paste it into the switch terminal window.
Verification
Verify that the sales and support VLANs have been created and are operating properly, perform these tasks:
- Verifying That the VLANs Have Been Created and Associated with the Correct Interfaces
- Verifying That Traffic Is Being Routed Between the Two VLANs
- Verifying That Traffic Is Being Switched Between the Two VLANs
Verifying That the VLANs Have Been Created and Associated with the Correct Interfaces
Purpose
Verify that the sales and support VLANs have been created on the switch and that all connected interfaces on the switch are members of the correct VLAN.
Action
To list all VLANs configured on the switch, use the show vlans command:
user@switch> show vlans Name Tag Interfaces default xe-0/0/1.0, xe-0/0/2.0, xe-0/0/4.0, xe-0/0/5.0, xe-0/0/6.0, xe-0/0/7.0, xe-0/0/8.0, xe-0/0/9.0, xe-0/0/10.0*, xe-0/0/11.0, xe-0/0/12.0, xe-0/0/13.0*, xe-0/0/14.0, xe-0/0/15.0, xe-0/0/16.0, xe-0/0/17.0, xe-0/0/18.0, xe-0/0/19.0, xe-0/0/21.0, xe-0/0/23.0*, xe-0/0/25.0, xe-0/0/27.0, xe-0/0/28.0, xe-0/0/29.0, xe-0/0/30.0, xe-0/0/31.0, xe-0/0/32.0, xe-0/0/33.0, xe-0/0/34.0, xe-0/0/35.0, xe-0/0/36.0, xe-0/0/37.0, xe-0/0/38.0, xe-0/0/39.0, xe-0/0/40.0, xe-0/0/41.0, xe-0/0/42.0, xe-0/0/43.0, xe-0/0/45.0, xe-0/0/47.0, xe-0/1/0.0*, xe-0/1/1.0*, xe-0/1/2.0*, xe-0/1/3.0* sales 100 xe-0/0/0.0*, xe-0/0/3.0, xe-0/0/20.0, xe-0/0/22.0 support 200 xe-0/0/0.24, xe-0/0/26.0, xe-0/0/44.0, xe-0/0/46.0* mgmt me0.0*
Meaning
The show vlans command lists all VLANs configured
on the switch and which interfaces are members of each VLAN. This
command output shows that the sales and support VLANs
have been created. The sales VLAN has a tag ID of 100 and
is associated with interfaces xe-0/0/0.0, xe-0/0/3.0, xe-0/0/20.0, and xe-0/0/22.0. VLAN support has a tag ID of 200 and is associated with interfaces xe-0/0/24.0, xe-0/0/26.0, xe-0/0/44.0, and xe-0/0/46.0.
Verifying That Traffic Is Being Routed Between the Two VLANs
Purpose
Verify routing between the two VLANs.
Action
List the Layer 3 routes in the switch Address Resolution Protocol (ARP) table:
user@switch> show arp MAC Address Address Name Flags 00:00:0c:06:2c:0d 192.0.2.3 irb.0 None 00:13:e2:50:62:e0 192.0.2.11 irb.1 None
Meaning
Sending IP packets on a multiaccess network requires mapping from an IP address to a MAC address (the physical or hardware address). The ARP table displays the mapping between the IP address and MAC address for both irb.0 (associated with sales) and irb.1 (associated with support). These VLANs can route traffic to each other.
Verifying That Traffic Is Being Switched Between the Two VLANs
Purpose
Verify that learned entries are being added to the Ethernet switching table.
Action
List the contents of the Ethernet switching table:
user@switch> show ethernet-switching table Ethernet-switching table: 8 entries, 5 learned VLAN MAC address Type Age Interfaces default * Flood - All-members default 00:00:05:00:00:01 Learn - xe-0/0/10.0 default 00:00:5e:00:01:09 Learn - xe-0/0/13.0 default 00:19:e2:50:63:e0 Learn - xe-0/0/23.0 sales * Flood - All-members sales 00:00:5e:00:07:09 Learn - xe-0/0/0.0 support * Flood – All–members support 00:00:5e:00:01:01 Learn – xe-0/0/46.0
Meaning
The output shows that learned entries for the sales and support VLANs have been added to the Ethernet switching table, and are associated with interfaces xe-0/0/0.0 and xe-0/0/46.0. Even though the VLANs were associated with more than one interface in the configuration, these interfaces are the only ones that are currently operating.
Example: Setting Up Bridging with Multiple VLANs on Switches
The QFX Series products use bridging and virtual LANs (VLANs) to connect network devices in a LAN—storage devices, file servers, and other network components—and to segment the LAN into smaller bridging domains.
To segment traffic on a LAN into separate broadcast domains, you create separate virtual LANs (VLANs) on a switch. Each VLAN is a collection of network nodes. When you use VLANs, frames whose origin and destination are in the same VLAN are forwarded only within the local VLAN, and only frames not destined for the local VLAN are forwarded to other broadcast domains. VLANs thus limit the amount of traffic flowing across the entire LAN, reducing the possible number of collisions and packet retransmissions within the LAN.
This example describes how to configure bridging for the QFX Series and how to create two VLANs to segment the LAN:
This task supports the Enhanced Layer 2 Software (ELS) configuration style. For ELS details, see Using the Enhanced Layer 2 Software CLI. If your switch runs software that does not supports ELS, see Example: Setting Up Bridging with Multiple VLANs.
Requirements
This example uses the following hardware and software components:
A configured and provisioned QFX3500 switch
Junos OS Release 13.2X50-D15 or later for the QFX Series
Overview and Topology
Switches connect all devices in an office or data center into a single LAN to provide sharing of common resources such as file servers. The default configuration creates a single VLAN, and all traffic on the switch is part of that broadcast domain. Creating separate network segments reduces the span of the broadcast domain and enables you to group related users and network resources without being limited by physical cabling or by the location of a network device in the building or on the LAN.
This example shows a simple configuration to illustrate the basic steps for creating two VLANs on a single switch. One VLAN, called sales, is for the sales and marketing group, and a second, called support, is for the customer support team. The sales and support groups each have their own dedicated file servers and other resources. For the switch ports to be segmented across the two VLANs, each VLAN must have its own broadcast domain, identified by a unique name and tag (VLAN ID). In addition, each VLAN must be on its own distinct IP subnet.
Topology
The topology used in this example consists of a single QFX3500 switch, with a total of 48 10-Gbps Ethernet ports. (For the purposes of this example, the QSFP+ ports Q0-Q3, which are ports xe-0/1/0 through xe-0/1/15, are excluded.)
Property |
Settings |
|---|---|
Switch hardware |
QFX3500 switch configured with 48 10-Gbps Ethernet ports (xe-0/0/0 through xe-0/0/47) |
VLAN names and tag IDs |
sales, tag 100 support, tag 200 |
VLAN subnets |
sales: 192.0.2.0/25 (addresses 192.0.2.1 through 192.0.2.126) support: 192.0.2.128/25 (addresses 192.0.2.129 through 192.0.2.254) |
Interfaces in VLAN sales |
File servers: xe-0/0/20 and xe-0/0/21 |
Interfaces in VLAN support |
File servers: xe-0/0/46 and xe-0/0/47 |
Unused interfaces |
xe-0/0/2 and xe-0/0/25 |
This configuration example creates two IP subnets, one for the sales VLAN and the second for the support VLAN. The switch bridges traffic within a VLAN. For traffic passing between two VLANs, the switch routes the traffic using a Layer 3 routing interface on which you have configured the address of the IP subnet.
To keep the example simple, the configuration steps show only a few devices in each of the VLANs. Use the same configuration procedure to add more LAN devices.
Configuration
Procedure
CLI Quick Configuration
To quickly configure Layer 2 switching for the two VLANs (sales and support) and to quickly configure Layer 3 routing of traffic between the two VLANs, copy the following commands and paste them into the switch terminal window:
[edit]
set interfaces xe-0/0/0 unit 0 family ethernet-switching vlan members sales
set interfaces xe-0/0/3 unit 0 family ethernet-switching vlan members sales
set interfaces xe-0/0/22 unit 0 family ethernet-switching vlan members sales
set interfaces xe-0/0/20 unit 0 description “Sales file server port”
set interfaces xe-0/0/20 unit 0 family ethernet-switching vlan members sales
set interfaces xe-0/0/24 unit 0 family ethernet-switching vlan members support
set interfaces xe-0/0/26 unit 0 family ethernet-switching vlan members support
set interfaces xe-0/0/44 unit 0 family ethernet-switching vlan members support
set interfaces xe-0/0/46 unit 0 description “Support file server port”
set interfaces xe-0/0/46 unit 0 family ethernet-switching vlan members support
set interfaces irb unit 0 family inet address 192.0.2.0/25
set interfaces irb unit 1 family inet address 192.0.2.128/25
set vlans sales l3–interface irb.0
set vlans sales vlan-id 100
set vlans support vlan-id 200
set vlans support l3-interface irb.1 Step-by-Step Procedure
Configure the switch interfaces and the VLANs to which they belong. By default, all interfaces are in access mode, so you do not have to configure the port mode.
Configure the interface for the file server in the sales VLAN:
[edit interfaces xe-0/0/20 unit 0] user@switch# set description “Sales file server port” user@switch# set family ethernet-switching vlan members sales
Configure the interface for the file server in the support VLAN:
[edit interfaces xe-0/0/46 unit 0] user@switch# set description “Support file server port” user@switch# set family ethernet-switching vlan members support
Create the subnet for the sales broadcast domain:
[edit interfaces] user@switch# set irb unit 0 family inet address 192.0.2.1/25
Create the subnet for the support broadcast domain:
[edit interfaces] user@switch# set irb unit 1 family inet address 192.0.2.129/25
Configure the VLAN tag IDs for the sales and support VLANs:
[edit vlans] user@switch# set sales vlan-id 100 user@switch# set support vlan-id 200
To route traffic between the sales and support VLANs, define the interfaces that are members of each VLAN and associate a Layer 3 interface:
[edit vlans] user@switch# set sales l3-interface irb.0 user@switch# set support l3-interface irb.1
Configuration Results
Display the results of the configuration:
user@switch> show configuration
interfaces {
xe-0/0/20 {
unit 0 {
description “Sales file server port”;
family ethernet-switching {
vlan members sales;
}
}
}
xe-0/0/46 {
unit 0 {
description “Support file server port”;
family ethernet-switching {
vlan members support;
}
}
}
irb {
unit 0 {
family inet address 192.0.2.1/25;
}
unit 1 {
family inet address 192.0.2.129/25;
}
}
}
vlans {
sales {
vlan-id 100;
interface xe-0/0/0.0:
interface xe-0/0/3/0;
interface xe-0/0/20.0;
interface xe-0/0/22.0;
l3-interface irb.0;
}
support {
vlan-id 200;
interface xe-0/0/24.0:
interface xe-0/0/26.0;
interface xe-0/0/44.0;
interface xe-0/0/46.0;
l3-interface irb.1;
}
} To quickly configure the sales and support VLAN interfaces,
issue the load merge terminal command. Then copy the hierarchy
and paste it into the switch terminal window.
Verification
Verify that the sales and support VLANs have been created and are operating properly, perform these tasks:
- Verifying That the VLANs Have Been Created and Associated with the Correct Interfaces
- Verifying That Traffic Is Being Routed Between the Two VLANs
- Verifying That Traffic Is Being Switched Between the Two VLANs
Verifying That the VLANs Have Been Created and Associated with the Correct Interfaces
Purpose
Verify that the sales and support VLANs have been created on the switch and that all connected interfaces on the switch are members of the correct VLAN.
Action
To list all VLANs configured on the switch, use the show vlans command:
user@switch> show vlans Name Tag Interfaces default xe-0/0/1.0, xe-0/0/2.0, xe-0/0/4.0, xe-0/0/5.0, xe-0/0/6.0, xe-0/0/7.0, xe-0/0/8.0, xe-0/0/9.0, xe-0/0/10.0*, xe-0/0/11.0, xe-0/0/12.0, xe-0/0/13.0*, xe-0/0/14.0, xe-0/0/15.0, xe-0/0/16.0, xe-0/0/17.0, xe-0/0/18.0, xe-0/0/19.0, xe-0/0/21.0, xe-0/0/23.0*, xe-0/0/25.0, xe-0/0/27.0, xe-0/0/28.0, xe-0/0/29.0, xe-0/0/30.0, xe-0/0/31.0, xe-0/0/32.0, xe-0/0/33.0, xe-0/0/34.0, xe-0/0/35.0, xe-0/0/36.0, xe-0/0/37.0, xe-0/0/38.0, xe-0/0/39.0, xe-0/0/40.0, xe-0/0/41.0, xe-0/0/42.0, xe-0/0/43.0, xe-0/0/45.0, xe-0/0/47.0, xe-0/1/0.0*, xe-0/1/1.0*, xe-0/1/2.0*, xe-0/1/3.0* sales 100 xe-0/0/0.0*, xe-0/0/3.0, xe-0/0/20.0, xe-0/0/22.0 support 200 xe-0/0/0.24, xe-0/0/26.0, xe-0/0/44.0, xe-0/0/46.0* mgmt me0.0*
Meaning
The show vlans command lists all VLANs configured
on the switch and which interfaces are members of each VLAN. This
command output shows that the sales and support VLANs
have been created. The sales VLAN has a tag ID of 100 and
is associated with interfaces xe-0/0/0.0, xe-0/0/3.0, xe-0/0/20.0, and xe-0/0/22.0. VLAN support has a tag ID of 200 and is associated with interfaces xe-0/0/24.0, xe-0/0/26.0, xe-0/0/44.0, and xe-0/0/46.0.
Verifying That Traffic Is Being Routed Between the Two VLANs
Purpose
Verify routing between the two VLANs.
Action
List the Layer 3 routes in the switch Address Resolution Protocol (ARP) table:
user@switch> show arp MAC Address Address Name Flags 00:00:0c:06:2c:0d 192.0.2.3 irb.0 None 00:13:e2:50:62:e0 192.0.2.11 irb.1 None
Meaning
Sending IP packets on a multiaccess network requires mapping from an IP address to a MAC address (the physical or hardware address). The ARP table displays the mapping between the IP address and MAC address for both irb.0 (associated with sales) and irb.1 (associated with support). These VLANs can route traffic to each other.
Verifying That Traffic Is Being Switched Between the Two VLANs
Purpose
Verify that learned entries are being added to the Ethernet switching table.
Action
List the contents of the Ethernet switching table:
user@switch> show ethernet-switching table Ethernet-switching table: 8 entries, 5 learned VLAN MAC address Type Age Interfaces default * Flood - All-members default 00:00:05:00:00:01 Learn - xe-0/0/10.0 default 00:00:5e:00:01:09 Learn - xe-0/0/13.0 default 00:19:e2:50:63:e0 Learn - xe-0/0/23.0 sales * Flood - All-members sales 00:00:5e:00:07:09 Learn - xe-0/0/0.0 support * Flood – All–members support 00:00:5e:00:01:01 Learn – xe-0/0/46.0
Meaning
The output shows that learned entries for the sales and support VLANs have been added to the Ethernet switching table, and are associated with interfaces xe-0/0/0.0 and xe-0/0/46.0. Even though the VLANs were associated with more than one interface in the configuration, these interfaces are the only ones that are currently operating.
Example: Connecting Access Switches with ELS Support to a Distribution Switch with ELS Support
This example uses Junos OS for EX Series switches with support for the Enhanced Layer 2 Software (ELS) configuration style. For ELS details, see Using the Enhanced Layer 2 Software CLI.
In large local area networks (LANs), you commonly need to aggregate traffic from a number of access switches into a distribution switch.
This example describes how to connect access switches to a distribution switch:
- Requirements
- Overview and Topology
- Configuring the Access Switch
- Configuring the Distribution Switch
- Verification
Requirements
This example uses the following hardware and software components:
Three EX Series access switches.
One EX Series distribution switch.
Note:In an access switch-distribution switch topology, you can connect EX Series switches that run a version of Junos OS that supports ELS with EX Series switches that do not run a version of Junos OS that supports ELS. However, this example uses switches running ELS only to show how to configure this topology using the ELS CLI.
Junos OS Release 12.3R2 or later that supports ELS for EX Series switches.
Before you connect an access switch to a distribution switch, be sure you have:
Installed the switches. See the installation instructions for your switch.
Performed the initial software configuration on both switches. For information about the initial software configuration for all EX Series switches except the EX9200 Series switches, see Connecting and Configuring an EX Series Switch (CLI Procedure). For information about the initial software configuration for the EX9200 Series switches, see Connecting and Configuring an EX9200 Switch (CLI Procedure).
Overview and Topology
In a large office that is spread across several floors or buildings, or in a data center, you commonly aggregate traffic from a number of access switches into a distribution switch. This configuration example shows a simple topology to illustrate how to connect three access switches to a distribution switch.
In the topology, the LAN is segmented into two VLANs, one for the sales department and the second for the support team. One 1-Gigabit Ethernet port on one of the access switch's uplink modules connects to the distribution switch, to one 1-Gigabit Ethernet port on the distribution switch.
Figure 1 shows an EX9200 distribution switch that is connected to three EX4300 access switches.
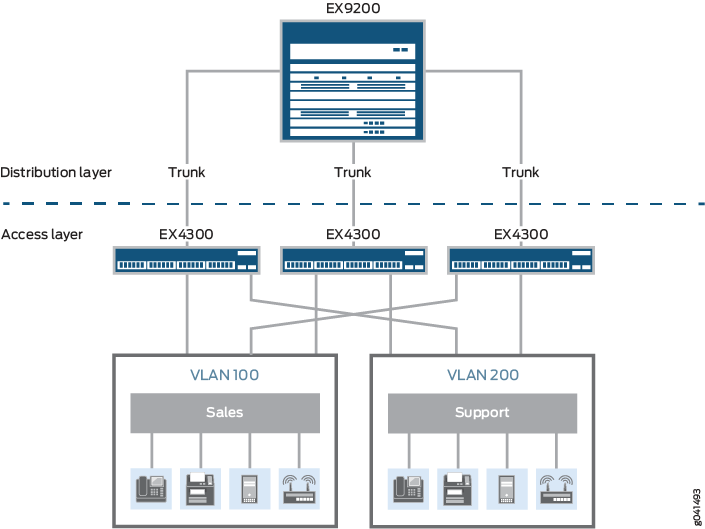
Topology
Table 6 describes the components of the example topology. The example shows how to configure one of the three access switches. The other access switches could be configured in the same manner.
| Property | Settings |
|---|---|
Access switch hardware |
Three EX4300 switches, each with an uplink module with 1-Gigabit Ethernet ports.. |
Distribution switch hardware |
One EX9208 with up to three EX9200-40T line cards installed, which at full duplex, can provide up to 240 1-Gigabit ports. |
VLAN names and tag IDs |
sales, tag 100support, tag 200 |
VLAN subnets |
sales: 192.0.2.0/25 (addresses 192.0.2.1 through 192.0.2.126)support: 192.0.2.128/25 (addresses 192.0.2.129 through 192.0.2.254) |
Trunk port interfaces |
On the access switch: ge-0/2/0On the distribution switch: ge-0/0/0 |
Access port interfaces in VLAN sales (on access switch) |
Avaya IP telephones: ge-0/0/3 through ge-0/0/19Wireless access points: ge-0/0/0 and ge-0/0/1Printers: ge-0/0/22 and ge-0/0/23File servers: ge-0/0/20 and ge-0/0/21 |
Access port interfaces in VLAN support (on access switch) |
Avaya IP telephones: ge-0/0/25 through ge-0/0/43Wireless access points: ge-0/0/24Printers: ge-0/0/44 and ge-0/0/45File servers: ge-0/0/46 and ge-0/0/47 |
Configuring the Access Switch
To configure the access switch:
Procedure
CLI Quick Configuration
To quickly configure the access switch, copy the following commands and paste them into the switch terminal window:
[edit]
set interfaces ge-0/0/0 unit 0 description "Sales wireless access point port"
set interfaces ge-0/0/0 unit 0 family ethernet-switching vlan members sales
set interfaces ge-0/0/3 unit 0 description "Sales phone port"
set interfaces ge-0/0/3 unit 0 family ethernet-switching vlan members sales
set interfaces ge-0/0/22 unit 0 description "Sales printer port"
set interfaces ge-0/0/22 unit 0 family ethernet-switching vlan members sales
set interfaces ge-0/0/20 unit 0 description "Sales file server port"
set interfaces ge-0/0/20 unit 0 family ethernet-switching vlan members sales
set interfaces ge-0/0/24 unit 0 description "Support wireless access point port"
set interfaces ge-0/0/24 unit 0 family ethernet-switching vlan members support
set interfaces ge-0/0/26 unit 0 description "Support phone port"
set interfaces ge-0/0/26 unit 0 family ethernet-switching vlan members support
set interfaces ge-0/0/44 unit 0 description "Support printer port"
set interfaces ge-0/0/44 unit 0 family ethernet-switching vlan members support
set interfaces ge-0/0/46 unit 0 description "Support file server port"
set interfaces ge-0/0/46 unit 0 family ethernet-switching vlan members support
set interfaces ge-0/2/0 unit 0 description "Uplink module port connection to distribution switch"
set interfaces ge-0/2/0 unit 0 family ethernet-switching interface-mode trunk
set interfaces ge-0/2/0 native-vlan-id 1
set interfaces ge-0/2/0 unit 0 family ethernet-switching vlan members [sales support]
set interfaces ge-0/2/0 unit 0 family ethernet-switching vlan members 1
set interfaces irb unit 0 family inet address 192.0.2.1/25
set interfaces irb unit 1 family inet address 192.0.2.129/25
set vlans sales description “Sales VLAN”
set vlans sales l3-interface irb.0
set vlans sales vlan-id 100
set vlans support description “Support VLAN”
set vlans support vlan-id 200
set vlans support l3-interface irb.1 Step-by-Step Procedure
To configure the access switch:
Configure the 1-Gigabit Ethernet interface on the uplink module to be the trunk port that connects to the distribution switch:
[edit interfaces] user@access-switch# set ge-0/2/0 unit 0 description "Uplink module port connection to distribution switch" user@access-switch# set ge-0/2/0 unit 0 family ethernet-switching interface-mode trunk
Specify the VLANs to be aggregated on the trunk port:
[edit interfaces] user@access-switch# set ge-0/2/0 unit 0 family ethernet-switching vlan members [ sales support ]
To handle untagged packets that are received on the trunk port, create a native VLAN by configuring a VLAN ID and specifying that the trunk port is a member of the native VLAN:
[edit interfaces] user@access-switch# set ge-0/2/0 native-vlan-id 1 user@access-switch# set ge-0/2/0 unit 0 family ethernet-switching vlan members 1
Configure the sales VLAN:
[edit vlans] user@access-switch# set sales description "Sales VLAN" user@access-switch# set sales vlan-id 100 user@access-switch# set sales l3-interface irb.0
Configure the support VLAN:
[edit vlans] user@access-switch# set support description "Support VLAN" user@access-switch# set support vlan-id 200 user@access-switch# set support l3-interface irb.1
Create the subnet for the sales VLAN:
[edit interfaces] user@access-switch# set irb unit 0 family inet address 192.0.2.1/25
Create the subnet for the support VLAN:
[edit interfaces] user@access-switch# set irb unit 1 family inet address 192.0.2.129/25
Configure the interfaces in the sales VLAN:
[edit interfaces] user@access-switch# set ge-0/0/0 unit 0 description "Sales wireless access point port" user@access-switch# set ge-0/0/0 unit 0 family ethernet-switching vlan members sales user@access-switch# set ge-0/0/3 unit 0 description "Sales phone port" user@access-switch# set ge-0/0/3 unit 0 family ethernet-switching vlan members sales user@access-switch# set ge-0/0/20 unit 0 description "Sales file server port" user@access—switch# set ge-0/0/20 unit 0 family ethernet-switching vlan members sales user@access-switch# set ge-0/0/22 unit 0 description "Sales printer port" user@access-switch# set ge-0/0/22 unit 0 family ethernet-switching vlan members salesConfigure the interfaces in the support VLAN:
[edit interfaces] user@access-switch# set ge-0/0/24 unit 0 description "Support wireless access point port" user@access-switch# set ge-0/0/24 unit 0 family ethernet-switching vlan members support user@access-switch# set ge-0/0/26 unit 0 description "Support phone port" user@access-switch# set ge-0/0/26 unit 0 family ethernet-switching vlan members support user@access-switch# set ge-0/0/44 unit 0 description "Support printer port" user@access-switch# set ge-0/0/44 unit 0 family ethernet-switching vlan members support user@access-switch# set ge-0/0/46 unit 0 description "Support file server port" user@access-switch# set ge-0/0/46 unit 0 family ethernet-switching vlan members support
Results
Display the results of the configuration:
user@access-switch> show configuration
interfaces {
ge-0/0/0 {
unit 0 {
description "Sales wireless access point port";
family ethernet-switching {
vlan {
members sales;
}
}
}
}
ge-0/0/3 {
unit 0 {
description "Sales phone port";
family ethernet-switching {
vlan {
members sales;
}
}
}
}
ge-0/0/20 {
unit 0 {
description "Sales file server port";
family ethernet-switching {
vlan {
members sales;
}
}
}
}
ge-0/0/22 {
unit 0 {
description "Sales printer port";
family ethernet-switching {
vlan {
members sales;
}
}
}
}
ge-0/0/24 {
unit 0 {
description "Support wireless access point port";
family ethernet-switching {
vlan {
members support;
}
}
}
}
ge-0/0/26 {
unit 0 {
description "Support phone port";
family ethernet-switching {
vlan {
members support;
}
}
}
}
ge-0/0/44 {
unit 0 {
description "Support printer port";
family ethernet-switching {
vlan {
members support;
}
}
}
}
ge-0/0/46 {
unit 0 {
description "Support file server port";
family ethernet-switching {
vlan {
members support;
}
}
}
}
ge-0/2/0 {
native-vlan-id 1;
unit 0 {
description "Uplinking module connection to distribution switch";
family ethernet-switching {
interface-mode trunk;
vlan {
members [ 1 sales support ];
}
}
}
}
irb {
unit 0 {
family inet {
address 192.0.2.1/25;
}
}
unit 1 {
family inet {
address 192.0.2.129/25;
}
}
}
vlans {
sales {
description "Sales VLAN";
vlan-id 100;
l3-interface irb.0;
}
support {
description "Support VLAN";
vlan-id 200;
l3-interface irb.1;
}
}
}To quickly configure the access switch, issue the load merge terminal command, then copy the hierarchy and paste
it into the switch terminal window.
Configuring the Distribution Switch
To configure the distribution switch:
Procedure
CLI Quick Configuration
To quickly configure the distribution switch, copy the following commands and paste them into the switch terminal window:
set interfaces ge-0/0/0 unit 0 description "Connection to access switch"
set interfaces ge-0/0/0 unit 0 family ethernet-switching interface-mode trunk
set interfaces ge-0/0/0 unit 0 family ethernet-switching vlan members [ sales support ]
set interfaces ge-0/0/0 native-vlan-id 1
set interfaces ge-0/0/0 unit 0 family ethernet-switching vlan members 1
set interfaces irb unit 0 family inet address 192.0.2.2/25
set interfaces irb unit 1 family inet address 192.0.2.130/25
set vlans sales description "Sales VLAN"
set vlans sales vlan-id 100
set vlans sales l3-interface irb.0
set vlans support description "Support VLAN"
set vlans support vlan-id 200
set vlans support l3-interface irb.1 Step-by-Step Procedure
To configure the distribution switch:
Configure the interface on the switch to be the trunk port that connects to the access switch:
[edit interfaces] user@distribution-switch# set ge-0/0/0 unit 0 description "Connection to access switch" user@distribution-switch# set ge-0/0/0 unit 0 family ethernet-switching interface-mode trunk
Specify the VLANs to be aggregated on the trunk port:
[edit interfaces] user@distribution-switch# set ge-0/0/0 unit 0 family ethernet-switching vlan members [ sales support ]
To handle untagged packets that are received on the trunk port, create a native VLAN by configuring a VLAN ID and specifying that the trunk port is a member of the native VLAN:
[edit interfaces] user@distribution-switch# set ge-0/0/0 native-vlan-id 1 user@distribution-switch# set ge-0/0/0 unit 0 family ethernet-switching vlan members 1
Configure the sales VLAN:
[edit vlans] user@distribution-switch# set sales description "Sales VLAN" user@distribution-switch# set sales vlan-id 100 user@distribution-switch# set sales l3-interface irb.0
The VLAN configuration for the distribution switch includes the set l3-interface irb.0 command to route traffic between the sales and support VLANs. The VLAN configuration for the access switch does not include this statement because the access switch is not monitoring IP addresses. Instead, the access switch is passing the IP addresses to the distribution switch for interpretation.
Configure the support VLAN:
[edit vlans] user@distribution-switch# set support description "Support VLAN" user@distribution-switch# set support vlan-id 200 user@distribution-switch# set support l3-interface irb.1
The VLAN configuration for the distribution switch includes the set l3-interface irb.1 command to route traffic between the sales and support VLANs. The VLAN configuration for the access switch does not include this statement because the access switch is not monitoring IP addresses. Instead, the access switch is passing the IP addresses to the distribution switch for interpretation.
Create the subnet for the sales VLAN:
[edit interfaces] user@distribution-switch# set irb unit 0 family inet address 192.0.2.2/25
Create the subnet for the support VLAN:
[edit interfaces] user@distribution-switch# set irb unit 1 family inet address 192.0.2.130/25
Results
Display the results of the configuration:
user@distribution-switch> show configuration
interfaces {
ge-0/0/0 {
native-vlan-id 1;
unit 0 {
description "Connection to access switch";
family ethernet-switching {
interface-mode trunk;
vlan {
members [ 1 sales support ];
}
}
}
}
irb {
unit 0 {
family inet {
address 192.0.2.2/25;
}
}
unit 1 {
family inet {
address 192.0.2.130/25;
}
}
}
}
vlans {
sales {
description "Sales VLAN";
vlan-id 100;
l3-interface irb.0;
}
support {
description "Support VLAN";
vlan-id 200;
l3-interface irb.1;
}
}To quickly configure the distribution switch, issue the load merge terminal command, then copy the hierarchy and paste
it into the switch terminal window.
Verification
To confirm that the configuration is working properly, perform these tasks:
- Verifying the VLAN Members and Interfaces on the Access Switch
- Verifying the VLAN Members and Interfaces on the Distribution Switch
Verifying the VLAN Members and Interfaces on the Access Switch
Purpose
Verify that the sales and support VLANs have been created on the switch.
Action
List all VLANs configured on the switch:
user@access-switch> show vlans
Routing instance VLAN name Tag Interfaces
default-switch sales 100
ge-0/0/20.0
ge-0/0/22.0
ge-0/0/3.0*
ge-0/0/0.0*
ge-0/2/0.0*
default-switch support 200
ge-0/0/24.0
ge-0/0/26.0
ge-0/0/44.0*
ge-0/0/46.0*
ge-0/2/0.0*
Meaning
The output shows the sales and support VLANs and the interfaces that are configured as members of the respective VLANs.
Verifying the VLAN Members and Interfaces on the Distribution Switch
Purpose
Verify that the sales and support VLANs have been created on the switch.
Action
List all VLANs configured on the switch:
user@distribution-switch> show vlans
Routing instance VLAN name Tag Interfaces
default-switch sales 100
ge-0/0/0.0*
default-switch support 200
ge-0/0/0.0*
Meaning
The output shows the sales and support VLANs and the interface (ge-0/0/0.0) that is configured as a member of both VLANs. Interface ge-0/0/0.0 is also the trunk interface connected to the access switch.
Example: Setting Up Bridging with Multiple VLANs for EX Series Switches
To segment traffic on a LAN into separate broadcast domains, you create separate virtual LANs (VLANs) on an EX Series switch. Each VLAN is a collection of network nodes. When you use VLANs, frames whose origin and destination are in the same VLAN are forwarded only within the local VLAN, and only frames not destined for the local VLAN are forwarded to other broadcast domains. VLANs thus limit the amount of traffic flowing across the entire LAN, reducing the possible number of collisions and packet retransmissions within the LAN.
This example describes how to configure bridging for an EX Series switch and how to create two VLANs to segment the LAN:
Requirements
This example uses the following hardware and software components:
One EX4200-48P Virtual Chassis switch
Junos OS Release 9.0 or later for EX Series switches
Before you set up bridging and VLANs, be sure you have:
Performed the initial switch configuration. See Connecting and Configuring an EX Series Switch (J-Web Procedure).
Overview and Topology
EX Series switches connect all devices in an office or data center into a single LAN to provide sharing of common resources such as printers and file servers and to enable wireless devices to connect to the LAN through wireless access points. The default configuration creates a single VLAN, and all traffic on the switch is part of that broadcast domain. Creating separate network segments reduces the span of the broadcast domain and allows you to group related users and network resources without being limited by physical cabling or by the location of a network device in the building or on the LAN.
This example shows a simple configuration to illustrate the basic steps for creating two VLANs on a single switch. One VLAN, called sales, is for the sales and marketing group, and a second, called support, is for the customer support team. The sales and support groups each have their own dedicated file servers, printers, and wireless access points. For the switch ports to be segmented across the two VLANs, each VLAN must have its own broadcast domain, identified by a unique name and tag (VLAN ID). In addition, each VLAN must be on its own distinct IP subnet.
Topology
The topology for this example consists of one EX4200-48P switch, which has a total of 48 Gigabit Ethernet ports, all of which support Power over Ethernet (PoE). Most of the switch ports connect to Avaya IP telephones. The remainder of the ports connect to wireless access points, file servers, and printers. Table 7 explains the components of the example topology.
| Property | Settings |
|---|---|
Switch hardware |
EX4200-48P, 48 Gigabit Ethernet ports, all PoE-enabled (ge-0/0/0 through ge-0/0/47) |
VLAN names and tag IDs |
sales, tag 100 support, tag 200 |
VLAN subnets |
sales: 192.0.2.0/25 (addresses 192.0.2.1 through 192.0.2.126) support: 192.0.2.128/25 (addresses 192.0.2.129 through 192.0.2.254) |
Interfaces in VLAN sales |
Avaya IP telephones: ge-0/0/3 through ge-0/0/19Wireless access points: ge-0/0/0 and ge-0/0/1Printers: ge-0/0/22 and ge-0/0/23File servers: ge-0/0/20 and ge-0/0/21 |
Interfaces in VLAN support |
Avaya IP telephones: ge-0/0/25 through ge-0/0/43Wireless access points: ge-0/0/24Printers: ge-0/0/44 and ge-0/0/45File servers: ge-0/0/46 and ge-0/0/47 |
Unused interfaces |
ge-0/0/2 and ge-0/0/25 |
This configuration example creates two IP subnets, one for the sales VLAN and the second for the support VLAN. The switch bridges traffic within a VLAN. For traffic passing between two VLANs, the switch routes the traffic using a Layer 3 routing interface on which you have configured the address of the IP subnet.
To keep the example simple, the configuration steps show only a few devices in each of the VLANs. Use the same configuration procedure to add more LAN devices.
Configuration
Configure Layer 2 switching for two VLANs:
Procedure
CLI Quick Configuration
To quickly configure Layer 2 switching for the two VLANs (sales and support) and to quickly configure Layer 3 routing of traffic between the two VLANs, copy the following commands and paste them into the switch terminal window:
[edit]
set interfaces ge-0/0/0 unit 0 description “Sales wireless access point port”
set interfaces ge-0/0/0 unit 0 family ethernet-switching vlan members sales
set interfaces ge-0/0/3 unit 0 description “Sales phone port”
set interfaces ge-0/0/3 unit 0 family ethernet-switching vlan members sales
set interfaces ge-0/0/22 unit 0 description “Sales printer port”
set interfaces ge-0/0/22 unit 0 family ethernet-switching vlan members sales
set interfaces ge-0/0/20 unit 0 description “Sales file server port”
set interfaces ge-0/0/20 unit 0 family ethernet-switching vlan members sales
set interfaces ge-0/0/24 unit 0 description “Support wireless access point port”
set interfaces ge-0/0/24 unit 0 family ethernet-switching vlan members support
set interfaces ge-0/0/26 unit 0 description “Support phone port”
set interfaces ge-0/0/26 unit 0 family ethernet-switching vlan members support
set interfaces ge-0/0/44 unit 0 description “Support printer port”
set interfaces ge-0/0/44 unit 0 family ethernet-switching vlan members support
set interfaces ge-0/0/46 unit 0 description “Support file server port”
set interfaces ge-0/0/46 unit 0 family ethernet-switching vlan members support
set interfaces irb unit 0 family inet address 192.0.2.0/25
set interfaces irb unit 1 family inet address 192.0.2.128/25
set vlans sales l3–interface irb.0
set vlans sales vlan-id 100
set vlans support vlan-id 200
set vlans support l3-interface irb.1 Step-by-Step Procedure
Configure the switch interfaces and the VLANs to which they belong. By default, all interfaces are in access mode, so you do not have to configure the port mode.
Configure the interface for the wireless access point in the sales VLAN:
[edit interfaces ge-0/0/0 unit 0] user@switch# set description “Sales wireless access point port” user@switch# set family ethernet-switching vlan members sales
Configure the interface for the Avaya IP phone in the sales VLAN:
[edit interfaces ge-0/0/3 unit 0] user@switch# set description “Sales phone port” user@switch# set family ethernet-switching vlan members sales
Configure the interface for the printer in the sales VLAN:
[edit interfaces ge-0/0/22 unit 0] user@switch# set description “Sales printer port” user@switch# set family ethernet-switching vlan members sales
Configure the interface for the file server in the sales VLAN:
[edit interfaces ge-0/0/20 unit 0] user@switch# set description “Sales file server port” user@switch# set family ethernet-switching vlan members sales
Configure the interface for the wireless access point in the support VLAN:
[edit interfaces ge-0/0/24 unit 0] user@switch# set description “Support wireless access point port” user@switch# set family ethernet-switching vlan members support
Configure the interface for the Avaya IP phone in the support VLAN:
[edit interfaces ge-0/0/26 unit 0] user@switch# set description “Support phone port” user@switch# set family ethernet-switching vlan members support
Configure the interface for the printer in the support VLAN:
[edit interfaces ge-0/0/44 unit 0] user@switch# set description “Support printer port” user@switch# set family ethernet-switching vlan members support
Configure the interface for the file server in the support VLAN:
[edit interfaces ge-0/0/46 unit 0] user@switch# set description “Support file server port” user@switch# set family ethernet-switching vlan members support
Create the subnet for the sales broadcast domain:
[edit interfaces] user@switch# set irb unit 0 family inet address 192.0.2.1/25
Create the subnet for the support broadcast domain:
[edit interfaces] user@switch# set irb unit 1 family inet address 192.0.2.129/25
Configure the VLAN tag IDs for the sales and support VLANs:
[edit vlans] user@switch# set sales vlan-id 100 user@switch# set support vlan-id 200
To route traffic between the sales and support VLANs, define the interfaces that are members of each VLAN and associate a Layer 3 interface:
[edit vlans] user@switch# set sales l3-interface irb.0 user@switch# set support l3-interface irb.1
Results
Display the results of the configuration:
user@switch> show configuration
interfaces {
ge-0/0/0 {
unit 0 {
description “Sales wireless access point port”;
family ethernet-switching {
vlan members sales;
}
}
}
ge-0/0/3 {
unit 0 {
description “Sales phone port”;
family ethernet-switching {
vlan members sales;
}
}
}
ge-0/0/22 {
unit 0 {
description “Sales printer port”;
family ethernet-switching {
vlan members sales;
}
}
}
ge-0/0/20 {
unit 0 {
description “Sales file server port”;
family ethernet-switching {
vlan members sales;
}
}
}
ge-0/0/24 {
unit 0 {
description “Support wireless access point port”;
family ethernet-switching {
vlan members support;
}
}
}
ge-0/0/26 {
unit 0 {
description “Support phone port”;
family ethernet-switching {
vlan members support;
}
}
}
ge-0/0/44 {
unit 0 {
description “Support printer port”;
family ethernet-switching {
vlan members support;
}
}
}
ge-0/0/46 {
unit 0 {
description “Support file server port”;
family ethernet-switching {
vlan members support;
}
}
}
irb {
unit 0 {
family inet address 192.0.2.0/25;
}
unit 1 {
family inet address 192.0.2.128/25;
}
}
}
vlans {
sales {
vlan-id 100;
interface xe-0/0/0.0:
interface xe-0/0/3/0;
interface xe-0/0/20.0;
interface xe-0/0/22.0;
l3-interface irb.0;
}
support {
vlan-id 200;
interface xe-0/0/24.0:
interface xe-0/0/26.0;
interface xe-0/0/44.0;
interface xe-0/0/46.0;
l3-interface irb.1;
}
}To quickly configure the sales and support VLAN interfaces,
issue the load merge terminal command, then copy the hierarchy
and paste it into the switch terminal window.
Verification
To verify that the “sales” and “support” VLANs have been created and are operating properly, perform these tasks:
- Verifying That the VLANs Have Been Created and Associated to the Correct Interfaces
- Verifying That Traffic Is Being Routed Between the Two VLANs
- Verifying That Traffic Is Being Switched Between the Two VLANs
Verifying That the VLANs Have Been Created and Associated to the Correct Interfaces
Purpose
Verify that the VLANs sales and support have been created on the switch and that all connected interfaces on the switch are members of the correct VLAN.
Action
List all VLANs configured on the switch:
Use the operational mode commands:
user@switch> show vlans
Name Tag Interfaces
default
ge-0/0/1.0, ge-0/0/2.0, ge-0/0/4.0, ge-0/0/5.0,
ge-0/0/6.0, ge-0/0/7.0, ge-0/0/8.0, ge-0/0/9.0,
ge-0/0/10.0*, ge-0/0/11.0, ge-0/0/12.0, ge-0/0/13.0*,
ge-0/0/14.0, ge-0/0/15.0, ge-0/0/16.0, ge-0/0/17.0,
ge-0/0/18.0, ge-0/0/19.0, ge-0/0/21.0, ge-0/0/23.0*,
ge-0/0/25.0, ge-0/0/27.0, ge-0/0/28.0, ge-0/0/29.0,
ge-0/0/30.0, ge-0/0/31.0, ge-0/0/32.0, ge-0/0/33.0,
ge-0/0/34.0, ge-0/0/35.0, ge-0/0/36.0, ge-0/0/37.0,
ge-0/0/38.0, ge-0/0/39.0, ge-0/0/40.0, ge-0/0/41.0,
ge-0/0/42.0, ge-0/0/43.0, ge-0/0/45.0, ge-0/0/47.0,
ge-0/1/0.0*, ge-0/1/1.0*, ge-0/1/2.0*, ge-0/1/3.0*
sales 100
ge-0/0/0.0*, ge-0/0/3.0, ge-0/0/20.0, ge-0/0/22.0
support 200
ge-0/0/24.0, ge-0/0/26.0, ge-0/0/44.0, ge-0/0/46.0*
mgmt
me0.0*
Meaning
The show vlans command lists all VLANs configured
on the switch and which interfaces are members of each VLAN. This
command output shows that the sales and support VLANs
have been created. The sales VLAN has a tag ID of 100 and
is associated with interfaces ge-0/0/0.0, ge-0/0/3.0, ge-0/0/20.0, and ge-0/0/22.0. VLAN support has a tag ID of 200 and is associated with interfaces ge-0/0/24.0, ge-0/0/26.0, ge-0/0/44.0, and ge-0/0/46.0.
Verifying That Traffic Is Being Routed Between the Two VLANs
Purpose
Verify routing between the two VLANs.
Action
List the Layer 3 routes in the switch's Address Resolution Protocol (ARP) table:
user@switch> show arp MAC Address Address Name Flags 00:00:0c:06:2c:0d 192.0.2.3 irb.0 None 00:13:e2:50:62:e0 192.0.2.11 irb.1 None
Meaning
Sending IP packets on a multiaccess network requires mapping from an IP address to a MAC address (the physical or hardware address). The ARP table displays the mapping between the IP address and MAC address for both irb.0 (associated with sales) and irb.1 (associated with support). These VLANs can route traffic to each other.
Verifying That Traffic Is Being Switched Between the Two VLANs
Purpose
Verify that learned entries are being added to the Ethernet switching table.
Action
List the contents of the Ethernet switching table:
user@switch> show ethernet-switching table Ethernet-switching table: 8 entries, 5 learned VLAN MAC address Type Age Interfaces default * Flood - All-members default 00:00:05:00:00:01 Learn - ge-0/0/10.0 default 00:00:5e:00:01:09 Learn - ge-0/0/13.0 default 00:19:e2:50:63:e0 Learn - ge-0/0/23.0 sales * Flood - All-members sales 00:00:5e:00:07:09 Learn - ge-0/0/0.0 support * Flood – All–members support 00:00:5e:00:01:01 Learn – ge-0/0/46.0
Meaning
The output shows that learned entries for the sales and support VLANs have been added to the Ethernet switching table, and are associated with interfaces ge-0/0/0.0 and ge-0/0/46.0. Even though the VLANs were associated with more than one interface in the configuration, these interfaces are the only ones that are currently operating.
Example: Connecting an Access Switch to a Distribution Switch
In large local area networks (LANs), you commonly need to aggregate traffic from a number of access switches into a distribution switch.
This example describes how to connect an access switch to a distribution switch:
- Requirements
- Overview and Topology
- Configuring the Access Switch
- Configuring the Distribution Switch
- Verification
Requirements
This example uses the following hardware and software components:
For the distribution switch, one EX 4200-24F switch. This model is designed to be used as a distribution switch for aggregation or collapsed core network topologies and in space-constrained data centers. It has twenty-four 1-Gigabit Ethernet fiber SFP ports and an EX-UM-2XFP uplink module with two 10-Gigabit Ethernet XFP ports.
For the access switch, one EX 3200-24P, which has twenty-four 1-Gigabit Ethernet ports, all of which support Power over Ethernet (PoE), and an uplink module with four 1-Gigabit Ethernet ports.
Junos OS Release 11.1 or later for the QFX Series
Overview and Topology
In a large office that is spread across several floors or buildings, or in a data center, you commonly aggregate traffic from a number of access switches into a distribution switch. This configuration example shows a simple topology to illustrate how to connect a single access switch to a distribution switch.
In the topology, the LAN is segmented into two VLANs, one for the sales department and the second for the support team. One 1-Gigabit Ethernet port on the access switch's uplink module connects to the distribution switch, to one 1-Gigabit Ethernet port on the distribution switch.
Topology
Table 8 explains the components of the example topology. The example shows how to configure one of the three access switches. The other access switches could be configured in the same manner.
| Property | Settings |
Access switch hardware |
EX 3200-24P, 24 1-Gigabit Ethernet ports, all PoE-enabled (ge-0/0/0 through ge-0/0/23); one 4-port 1–Gigabit Ethernet uplink module (EX-UM-4SFP) |
Distribution switch hardware |
EX 4200-24F, 24 1-Gigabit Ethernet fiber SFP ports (ge-0/0/0 through ge-0/0/23); one 2–port 10–Gigabit Ethernet XFP uplink module (EX-UM-4SFP) |
VLAN names and tag IDs |
sales, tag 100support, tag 200 |
VLAN subnets |
sales: 192.0.2.0/25 (addresses 192.0.2.1 through 192.0.2.126)support: 192.0.2.128/25 (addresses 192.0.2.129 through 192.0.2.254) |
Trunk port interfaces |
On the access switch: ge-0/1/0On the distribution switch: ge-0/0/0 |
Access port interfaces in VLAN sales (on access switch) |
Avaya IP telephones: ge-0/0/3 through ge-0/0/19Wireless access points: ge-0/0/0 and ge-0/0/1Printers: ge-0/0/22 and ge-0/0/23File servers: ge-0/0/20 and ge-0/0/21 |
Access port interfaces in VLAN support (on access switch) |
Avaya IP telephones: ge-0/0/25 through ge-0/0/43Wireless access points: ge-0/0/24Printers: ge-0/0/44 and ge-0/0/45File servers: ge-0/0/46 and ge-0/0/47 |
Unused interfaces on access switch |
ge-0/0/2 and ge-0/0/25 |
Configuring the Access Switch
To configure the access switch:
Procedure
CLI Quick Configuration
To quickly configure the access switch, copy the following commands and paste them into the switch terminal window:
[edit]
set interfaces ge-0/0/0 unit 0 description “Sales Wireless access point port”
set interfaces ge-0/0/0 unit 0 family ethernet-switching vlan members sales
set interfaces ge-0/0/3 unit 0 description “Sales phone port”
set interfaces ge-0/0/3 unit 0 family ethernet-switching vlan members sales
set interfaces ge-0/0/22 unit 0 description “Sales printer port”
set interfaces ge-0/0/22 unit 0 family ethernet-switching vlan members sales
set interfaces ge-0/0/20 unit 0 description “Sales file server port”
set interfaces ge-0/0/20 unit 0 family ethernet-switching vlan members sales
set interfaces ge-0/0/24 unit 0 description “Support wireless access point port”
set interfaces ge-0/0/24 unit 0 family ethernet-switching vlan members support
set interfaces ge-0/0/26 unit 0 description “Support phone port”
set interfaces ge-0/0/26 unit 0 family ethernet-switching vlan members support
set interfaces ge-0/0/44 unit 0 description “Support printer port”
set interfaces ge-0/0/44 unit 0 family ethernet-switching vlan members support
set interfaces ge-0/0/46 unit 0 description “Support file server port”
set interfaces ge-0/0/46 unit 0 family ethernet-switching vlan members support
set interfaces ge-0/1/0 unit 0 description “Uplink module port connection to distribution switch”
set interfaces ge-0/1/0 unit 0 family ethernet-switching port-mode trunk
set interfaces ge-0/1/0 unit 0 family ethernet-switching native-vlan-id 1
set interfaces ge-0/1/0 unit 0 family ethernet switching vlan members [sales support]
set interfaces irb unit 0 family inet address 192.0.2.1/25
set interfaces irb unit 1 family inet address 192.0.2.129/25
set vlans sales interface ge-0/0/0.0
set vlans sales interface ge-0/0/3.0
set vlans sales interface ge-0/0/22.0
set vlans sales interface ge-0/0/20.0
set vlans sales l3-interface irb.0
set vlans sales vlan-id 100
set vlans sales vlan-description “Sales VLAN”
set vlans support interface ge-0/0/24.0
set vlans support interface ge-0/0/26.0
set vlans support interface ge-0/0/44.0
set vlans support interface ge-0/0/46.0
set vlans support vlan-id 200
set vlans support l3–interface irb.1
set vlans support vlan-description “Support VLAN” Step-by-Step Procedure
To configure the access switch:
Configure the 1-Gigabit Ethernet interface on the uplink module to be the trunk port that connects to the distribution switch:
[edit interfaces ge-0/1/0 unit 0]user@access-switch# setdescription “Uplink module port connection to distribution switch” user@access-switch# set ethernet-switching port-mode trunk
Specify the VLANs to be aggregated on the trunk port:
[edit interfaces ge-0/1/0 unit 0]user@access-switch# set ethernet-switching vlanmembers [ sales support ]
Configure the VLAN ID to use for packets that are received with no dot1q tag (untagged packets):
[edit interfaces ge-0/1/0 unit 0]user@access-switch# set ethernet-switching native-vlan-id 1
Configure the sales VLAN:
[edit vlans sales]user@access-switch# set vlan-description “Sales VLAN” user@access-switch# set vlan-id 100user@access-switch# set l3-interface (IRB) irb.0
Configure the support VLAN:
[edit vlans support]user@access-switch# set vlan-description “Support VLAN” user@access-switch# set vlan-id 200user@access-switch# set l3-interface (IRB) irb.1
Create the subnet for the sales broadcast domain:
[edit interfaces]user@access-switch# set irb unit 0 family inet address 192.0.2.1/25
Create the subnet for the support broadcast domain:
[edit interfaces]user@access-switch# set irb unit 1 family inet address 192.0.2.129/25
Configure the interfaces in the sales VLAN:
[edit interfaces]user@access-switch# set ge-0/0/0 unit 0 description “Sales wireless access point port” user@access-switch# set ge-0/0/0 unit 0 family ethernet-switching vlan members sales user@access-switch# set ge-0/0/3 unit 0 description “Sales phone port” user@access-switch# set ge-0/0/3 unit 0 family ethernet-switching vlan members sales user@access-switch# set ge-0/0/20 unit 0 description “Sales file server port” user@access—switch# set ge-0/0/20 unit 0 family ethernet-switching vlan members sales user@access-switch# set ge-0/0/22 unit 0 description “Sales printer port” user@access-switch# set ge-0/0/22 unit 0 family ethernet-switching vlan members sales
Configure the interfaces in the support VLAN:
[edit interfaces]user@access-switch# set ge-0/0/24 unit 0 description “Support wireless access point port” user@access-switch# set ge-0/0/24 unit 0 family ethernet-switching vlan members support user@access-switch# set ge-0/0/26 unit 0 description “Support phone port” user@access-switch# set ge-0/0/26 unit 0 family ethernet-switching vlan members support user@access-switch# set ge-0/0/44 unit 0 description “Support printer port” user@access-switch# set ge-0/0/44 unit 0 family ethernet-switching vlan members support user@access-switch# set ge-0/0/46 unit 0 description “Support file server port” user@access-switch# set ge-0/0/46 unit 0 family ethernet-switching vlan members support
Configure descriptions and VLAN tag IDs for the sales and support VLANs:
[edit vlans]user@access-switch# set sales vlan-description “Sales VLAN” user@access-switch# set sales vlan-id 100 user@access-switch# set support vlan-description “Support VLAN” user@access-switch# set support vlan-id 200
To route traffic between the sales and support VLANs and associate a Layer 3 interface with each VLAN:
[edit vlans]user@access-switch# set sales l3-interface irb.0 user@access-switch# set support l3-interface irb.1
Results
Display the results of the configuration:
user@access-switch> show
interfaces {
ge-0/0/0 {
unit 0 {
description “Sales wireless access point port”;
family ethernet-switching {
vlan members sales;
}
}
}
ge-0/0/3 {
unit 0 {
description “Sales phone port”;
family ethernet-switching {
vlan members sales;
}
}
}
ge-0/0/20 {
unit 0 {
description “Sales file server port”;
family ethernet-switching {
vlan members sales;
}
}
}
ge-0/0/22 {
unit 0 {
description “Sales printer port”;
family ethernet-switching {
vlan members sales;
}
}
}
ge-0/0/24 {
unit 0 {
description “Support wireless access point port”;
family ethernet-switching {
vlan members support;
}
}
}
ge-0/0/26 {
unit 0 {
description “Support phone port”;
family ethernet-switching {
vlan members support;
}
}
}
ge-0/0/44 {
unit 0 {
description “Support printer port”;
family ethernet-switching {
vlan members sales;
}
}
}
ge-0/0/46 {
unit 0 {
description “Support file server port”;
family ethernet-switching {
vlan members support;
}
}
}
ge-0/1/0 {
unit 0 {
description “Uplink module port connection to distribution switch”;
family ethernet-switching {
port-mode trunk;
vlan members [ sales support ];
native-vlan-id 1;
}
}
}
irb {
unit 0 {
family inet address 192.0.2.1/25;
}
unit 1 {
family inet address 192.0.2.129/25;
}
}
vlans {
sales {
vlan-id 100;
vlan-description “Sales VLAN”;
l3-interface irb.0;
}
support {
vlan-id 200;
vlan-description “Support VLAN”;
l3-interface irb.1;
}
}
}To quickly configure the distribution switch, issue the load merge terminal command, then copy the hierarchy and paste
it into the switch terminal window.
Configuring the Distribution Switch
To configure the distribution switch:
Procedure
CLI Quick Configuration
To quickly configure the distribution switch, copy the following commands and paste them into the switch terminal window:
set interfaces ge-0/0/0 description “Connection to access switch”
set interfaces ge-0/0/0 ethernet-switching port-mode trunk
set interfaces ge-0/0/0 ethernet-switching vlan members [ sales support ]
set interfaces ge-0/0/0 ethernet-switching native-vlan-id 1
set interfaces irb unit 0 family inet address 192.0.2.2/25
set interfaces irb unit 1 family inet address 192.0.2.130/25
set vlans sales vlan-description “Sales VLAN”
set vlans sales vlan-id 100
set vlans sales l3-interface irb.0
set vlans support vlan-description “Support VLAN”
set vlans support vlan-id 200
set vlans support l3-interface irb.1 Step-by-Step Procedure
To configure the distribution switch:
Configure the interface on the switch to be the trunk port that connects to the access switch:
[edit interfaces ge-0/0/0 unit 0]user@distribution-switch# set description “Connection to access switch” user@distribution-switch# set ethernet-switching port-mode trunk
Specify the VLANs to be aggregated on the trunk port:
[edit interfaces ge-0/0/0 unit 0]user@distribution-switch# set ethernet-switching vlanmembers [ sales support ]
Configure the VLAN ID to use for packets that are received with no dot1q tag (untagged packets):
[edit interfaces]user@distribution-switch# set ge-0/0/0 ethernet-switching native-vlan-id 1
Configure the sales VLAN:
[edit vlans sales]user@distribution-switch# set vlan-description “Sales VLAN” user@distribution-switch# set vlan-id 100user@distribution-switch# set l3-interface (IRB) irb.0
Configure the support VLAN:
[edit vlans support]user@distribution-switch# set vlan-description “Support VLAN” user@distribution-switch# set vlan-id 200user@distribution-switch# set l3-interface (IRB) irb.1
Create the subnet for the sales broadcast domain:
[edit interfaces]user@distribution-switch# set irb unit 0 family inet address 192.0.2.2/25
Create the subnet for the support broadcast domain:
[edit interfaces] user@distribution-switch# set irb unit 1 family inet address 192.0.2.130/25
Results
Display the results of the configuration:
user@distribution-switch> show
interfaces {
ge-0/0/0 {
description “Connection to access switch”;
unit 0 {
family ethernet-switching {
port-mode trunk;
vlan members [ sales support ];
native-vlan-id 1;
}
}
}
irb {
unit 0 {
family inet address 192.0.2.2/25;
}
unit 1 {
family inet address 192.0.2.130/25;
}
}
vlans {
sales {
vlan-id 100;
vlan-description “Sales VLAN”;
l3-interface irb.0;
}
support {
vlan-id 200;
vlan-description “Support VLAN”;
l3-interface irb.1;
}
}
}To quickly configure the distribution switch, issue the load merge terminal command, then copy the hierarchy and paste
it into the switch terminal window.
Verification
To confirm that the configuration is working properly, perform these tasks:
- Verifying the VLAN Members and Interfaces on the Access Switch
- Verifying the VLAN Members and Interfaces on the Distribution Switch
Verifying the VLAN Members and Interfaces on the Access Switch
Purpose
Verify that the sales and support have been created on the switch.
Action
List all VLANs configured on the switch:
user@switch> show vlans Name Tag Interfaces default ge-0/0/1.0, ge-0/0/2.0, ge-0/0/4.0, ge-0/0/5.0, ge-0/0/6.0, ge-0/0/7.0, ge-0/0/8.0*, ge-0/0/9.0, ge-0/0/10.0, ge-0/0/11.0*, ge-0/0/12.0, ge-0/0/13.0, ge-0/0/14.0, ge-0/0/15.0, ge-0/0/16.0, ge-0/0/17.0, ge-0/0/18.0, ge-0/0/19.0*,ge-0/0/21.0, ge-0/0/23.0, ge-0/0/25.0, ge-0/0/27.0*,ge-0/0/28.0, ge-0/0/29.0, ge-0/0/30.0, ge-0/0/31.0*,ge-0/0/32.0, ge-0/0/33.0, ge-0/0/34.0, ge-0/0/35.0*,ge-0/0/36.0, ge-0/0/37.0, ge-0/0/38.0, ge-0/0/39.0*,ge-0/0/40.0, ge-0/0/41.0, ge-0/0/42.0, ge-0/0/43.0*,ge-0/0/45.0, ge-0/0/47.0, ge-0/1/1.0*, ge-0/1/2.0*, ge-0/1/3.0* sales 100 ge-0/0/0.0*, ge-0/0/3.0, ge-0/0/20.0, ge-0/0/22.0, ge-0/1/0.0*, support 200 ge-0/0/24.0*, ge-0/0/26.0, ge-0/0/44.0, ge-0/0/46.0, mgmt me0.0*
Meaning
The output shows the sales and support VLANs and the interfaces associated with them.
Verifying the VLAN Members and Interfaces on the Distribution Switch
Purpose
Verify that the sales and support have been created on the switch.
Action
List all VLANs configured on the switch:
user@switch> show vlans Name Tag Interfaces default ge-0/0/1.0, ge-0/0/2.0, ge-0/0/3.0, ge-0/0/4.0, ge-0/0/5.0, ge-0/0/6.0, ge-0/0/7.0*, ge-0/0/8.0, ge-0/0/9.0, ge-0/0/10.0*, ge-0/0/11.0, ge-0/0/12.0, ge-0/0/13.0, ge-0/0/14.0, ge-0/0/15.0, ge-0/0/16.0, ge-0/0/17.0, ge-0/0/18.0*, ge-0/0/19.0, ge-0/0/20.0, ge-0/0/21.0, ge-0/0/22.0*, ge-0/0/23.0, ge-0/1/1.0*, ge-0/1/2.0*, ge-0/1/3.0* sales 100 ge-0/0/0.0* support 200 ge-0/0/0.0* mgmt me0.0*
Meaning
The output shows the sales and support VLANs associated to interface ge-0/0/0.0. Interface ge-0/0/0.0 is the trunk interface connected to the access switch.
Configuring a Logical Interface for Access Mode
Enterprise network administrators can configure a single logical interface to accept untagged packets and forward the packets within a specified VLAN. A logical interface configured to accept untagged packets is called an access interface or access port.
interface-mode access;
You can include this statement at the following hierarchy levels:
[edit interfaces interface-name unit logical-unit-number family ethernet-switching][edit logical-systems logical-system-name interfaces interface-name unit logical-unit-number family ethernet-switching]
When an untagged or tagged packet is received on an access interface, the packet is accepted, the VLAN ID is added to the packet, and the packet is forwarded within the VLAN that is configured with the matching VLAN ID.
The following example configures a logical interface as an access port with a VLAN ID of 20 on routers and switches that support the enhanced Layer 2 software:
[edit interfaces ge-1/2/0]
unit 1 {
family ethernet-switching {
interface-mode access;
vlan members 20;
}
}
See Also
Configuring the Native VLAN Identifier
This task uses Junos OS for EX Series switches and Junos OS for QFX3500 and QFX3600 switches that does not support the Enhanced Layer 2 Software (ELS) configuration style. If your switch runs software that supports ELS, see Configuring the Native VLAN Identifier on Switches With ELS Support. For ELS details, see Using the Enhanced Layer 2 Software CLI.
EX Series switches support receiving and forwarding routed or bridged Ethernet frames with 802.1Q VLAN tags. The logical interface on which untagged packets are to be received must be configured with the same native VLAN ID as that configured on the physical interface.
To configure the native VLAN ID using the CLI:
Configuring the Native VLAN Identifier on Switches With ELS Support
This task uses Junos OS for EX Series switches and Junos OS for QFX3500 and QFX3600 switches with support for the Enhanced Layer 2 Software (ELS) configuration style. If your switch runs software that does not support ELS, see Configuring the Native VLAN Identifier. For ELS details, see Using the Enhanced Layer 2 Software CLI.
Switches can receive and forward routed or bridged Ethernet frames with 802.1Q VLAN tags. Typically, trunk ports, which connect switches to each other, accept untagged control packets but do not accept untagged data packets. You can enable a trunk port to accept untagged data packets by configuring a native VLAN ID on the interface on which you want the untagged data packets to be received. The logical interface on which untagged packets are to be received must be configured with the same VLAN ID as the native VLAN ID configured on the physical interface.
To configure the native VLAN ID by using the command-line interface (CLI):
Configuring VLAN Encapsulation
To configure encapsulation on an interface, enter the encapsulation statement at the [edit interfaces interface-name] hierarchy level:
[edit interfaces interface-name] encapsulation type;
The following list contains important notes regarding encapsulation:
Ethernet interfaces in VLAN mode can have multiple logical interfaces. In CCC and VPLS modes, VLAN IDs from 1 through 511 are reserved for normal VLANs, and VLAN IDs 512 through 4094 are reserved for CCC or VPLS VLANs. For 4-port Fast Ethernet interfaces, you can use VLAN IDs 512 through 1024 for CCC or VPLS VLANs.
For encapsulation type flexible-ethernet-services, all VLAN IDs are valid.
For some encapsulation types, including flexible Ethernet services, Ethernet VLAN CCC, and VLAN VPLS, you can also configure the encapsulation type that is used inside the VLAN circuit itself. To do this, include the
encapsulationstatement:encapsulation (vlan-ccc | vlan-tcc | vlan-vpls);
You can include this statement at the following hierarchy levels:
[edit interfaces interface-name unit logical-unit-number][edit logical-systems logical-system-name interfaces interface-name unit logical-unit-number]
You cannot configure a logical interface with VLAN CCC or VLAN VPLS encapsulation unless you also configure the physical device with the same encapsulation or with flexible Ethernet services encapsulation. In general, the logical interface must have a VLAN ID of 512 or higher; if the VLAN ID is 511 or lower, it will be subject to the normal destination filter lookups in addition to source address filtering. However if you configure flexible Ethernet services encapsulation, this VLAN ID restriction is removed.
In general, you configure an interface’s encapsulation
at the [edit interfaces interface-name] hierarchy level.
- Example: Configuring VLAN Encapsulation on a Gigabit Ethernet Interface
- Example: Configuring VLAN Encapsulation on an Aggregated Ethernet Interface
Example: Configuring VLAN Encapsulation on a Gigabit Ethernet Interface
Configure VLAN CCC encapsulation on a Gigabit Ethernet interface:
interfaces ge-2/1/0 {
vlan-tagging;
encapsulation vlan-ccc;
unit 0 {
encapsulation vlan-ccc;
vlan-id 600;
}
}
Example: Configuring VLAN Encapsulation on an Aggregated Ethernet Interface
Configure VLAN CCC encapsulation on an aggregated Gigabit Ethernet interface:
interfaces ae0 {
vlan-tagging;
encapsulation vlan-vpls;
unit 0 {
vlan-id 100;
}
}
See Also
Change History Table
Feature support is determined by the platform and release you are using. Use Feature Explorer to determine if a feature is supported on your platform.
family ethernet-switching and flexible-vlan-tagging.