Example: Setting Up 802.1X for Single-Supplicant or Multiple-Supplicant Configurations on an EX Series Switch
802.1x port-based network access control (PNAC) authentication on EX Series switches provides three types of authentication to meet the access needs of your enterprise LAN:
Authenticate the first end device (supplicant) on an authenticator port, and allow all other end devices also connecting to have access to the LAN.
Authenticate only one end device on an authenticator port at one time.
Authenticate multiple end devices on an authenticator port. Multiple supplicant mode is used in VoIP configurations.
This example configures an EX Series switch to use IEEE 802.1X to authenticate end devices that use three different administrative modes.
Requirements
This example uses the following software and hardware components:
This example also applies to QFX5100 switches.
Junos OS Release 9.0 or later for EX Series switches
One EX Series switch acting as an authenticator port access entity (PAE). The ports on the authenticator PAE form a control gate that blocks all traffic to and from end devices until they are authenticated.
One RADIUS authentication server that supports 802.1X. The authentication server acts as the backend database and contains credential information for end devices (supplicants) that have permission to connect to the network.
Before you configure the ports for 802.1X authentication, be sure you have:
Performed the initial switch configuration. See Connecting and Configuring an EX Series Switch (CLI Procedure).
Performed basic bridging and VLAN configuration on the switch. See the documentation that describes setting up basic bridging and a VLAN for your switch. If you are using a switch that supports the Enhanced Layer 2 Software (ELS) configuration style, see Example: Setting Up Basic Bridging and a VLAN for an EX Series Switch with ELS Support or Example: Setting Up Basic Bridging and a VLAN on Switches. For all other switches, see Example: Setting Up Basic Bridging and a VLAN for an EX Series Switch.
Note:For more about ELS, see Using the Enhanced Layer 2 Software CLI.
Configured users on the authentication server.
Overview and Topology
As shown in Figure 1, the topology contains an EX4200 access switch connected to the authentication server on port ge-0/0/10. Interfaces ge-0/0/8, ge-0/0/9, and ge-0/0/11 will be configured for three different administrative modes.
This figure also applies to QFX5100 switches.
Topology
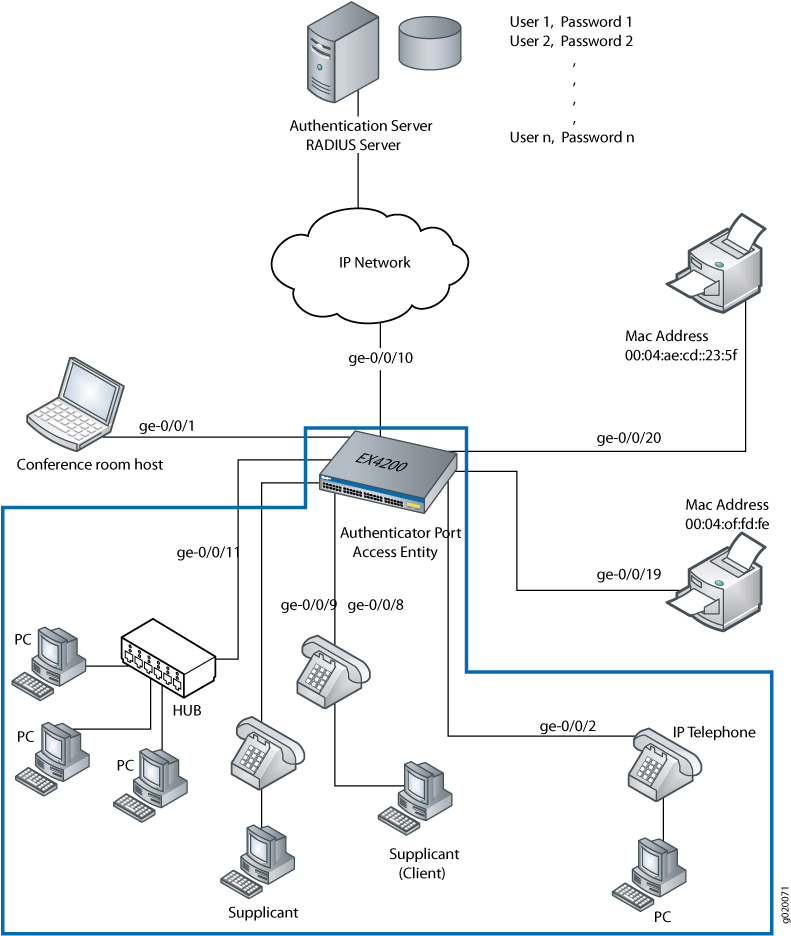
| Property | Settings |
|---|---|
Switch hardware |
EX4200 switch, 24 Gigabit Ethernet ports: 8 PoE ports (ge-0/0/0 through ge-0/0/7) and 16 non-PoE ports (ge-0/0/8 through ge-0/0/23) |
Connections to Avaya phones—with integrated hub, to connect phone and desktop PC to a single port; (requires PoE) |
ge-0/0/8, ge-0/0/9, and ge-0/0/11 |
To configure the administrative modes to support supplicants in different areas of the Enterprise network:
Configure access port ge-0/0/8 for single supplicant mode authentication.
Configure access port ge-0/0/9 for single secure supplicant mode authentication.
Configure access port ge-0/0/11 for multiple supplicant mode authentication.
Single supplicant mode authenticates only the first end device that connects to an authenticator port. All other end devices connecting to the authenticator port after the first has connected successfully, whether they are 802.1X-enabled or not, are permitted access to the port without further authentication. If the first authenticated end device logs out, all other end devices are locked out until an end device authenticates.
Single-secure supplicant mode authenticates only one end device to connect to an authenticator port. No other end device can connect to the authenticator port until the first logs out.
Multiple supplicant mode authenticates multiple end devices individually on one authenticator port. If you configure a maximum number of devices that can be connected to a port through port security, the lesser of the configured values is used to determine the maximum number of end devices allowed per port.
Configuration of 802.1X to Support Multiple Supplicant Modes
Procedure
CLI Quick Configuration
To quickly configure the ports with different 802.1X authentication modes, copy the following commands and paste them into the switch terminal window:
[edit] set protocols dot1x authenticator interface ge-0/0/8 supplicant single set protocols dot1x authenticator interface ge-0/0/9 supplicant single-secure set protocols dot1x authenticator interface ge-0/0/11 supplicant multiple
Step-by-Step Procedure
Configure the administrative mode on the interfaces:
Configure the supplicant mode as single on interface ge-0/0/8:
[edit protocols] user@switch# set dot1x authenticator interface ge-0/0/8 supplicant single
Configure the supplicant mode as single secure on interface ge-0/0/9:
[edit protocols] user@switch# set dot1x authenticator interface ge-0/0/9 supplicant single-secure
Configure multiple supplicant mode on interface ge-0/0/11:
[edit protocols] user@switch# set dot1x authenticator interface ge-0/0/11 supplicant multiple
Results
Check the results of the configuration:
[edit]
user@access-switch> show configuration
protocols {
dot1x {
authenticator {
interface {
ge-0/0/8.0 {
supplicant single;
)
ge-0/0/9.0 {
supplicant single-secure;
)
ge-0/0/11.0 {
supplicant multiple;
)
}
}
}
}
Verification
To confirm that the configuration is working properly, perform these tasks:
Verifying the 802.1X Configuration
Purpose
Verify the 802.1X configuration on interfaces ge-0/0/8, ge-0/0/9, and ge-0/0/11.
Action
Verify the 802.1X configuration by issuing the operational
mode command show dot1x interface:
user@switch> show dot1x interface ge-0/0/8.0 detail ge-0/0/8.0 Role: Authenticator Administrative state: Auto Supplicant mode: Single Number of retries: 3 Quiet period: 60 seconds Transmit period: 30 seconds Mac Radius: Disabled Mac Radius Restrict: Disabled Reauthentication: Enabled Configured Reauthentication interval: 3600 seconds Supplicant timeout: 30 seconds Server timeout: 30 seconds Maximum EAPOL requests: 2 Guest VLAN member: <not configured> user@switch> show dot1x interface ge-0/0/9.0 detail ge-0/0/9.0 Role: Authenticator Administrative state: Auto Supplicant mode: Single-Secure Number of retries: 3 Quiet period: 60 seconds Transmit period: 30 seconds Mac Radius: Disabled Mac Radius Restrict: Disabled Reauthentication: Enabled Configured Reauthentication interval: 3600 seconds Supplicant timeout: 30 seconds Server timeout: 30 seconds Maximum EAPOL requests: 2 Guest VLAN member: <not configured> Number of connected supplicants: 0 user@switch> show dot1x interface ge-0/0/11.0 detail ge-0/0/11.0 Role: Authenticator Administrative state: Auto Supplicant mode: Multiple Number of retries: 3 Quiet period: 60 seconds Transmit period: 30 seconds Mac Radius: Disabled Mac Radius Restrict: Disabled Reauthentication: Enabled Configured Reauthentication interval: 3600 seconds Supplicant timeout: 30 seconds Server timeout: 30 seconds Maximum EAPOL requests: 2 Guest VLAN member: <not configured> Number of connected supplicants: 0
Meaning
The Supplicant mode output field displays the configured administrative mode for each interface. Interface ge-0/0/8.0 displays Single supplicant mode. Interface ge-0/0/9.0 displays Single-Secure supplicant mode. Interface ge-0/0/11.0 displays Multiple supplicant mode.
