ON THIS PAGE
Example: Setting Up Captive Portal Authentication on an EX Series Switch
Designing a Captive Portal Authentication Login Page on Switches
Configuring Captive Portal Authentication (CLI Procedure) on an EX Series Switche with ELS Support
Example: Setting Up Captive Portal Authentication on an EX Series Switch with ELS Support
Captive Portal Authentication
You can control access to your network through a switch by using several different authentication methods. Junos OS switches support 802.1X, MAC RADIUS, and captive portal authentication. You can set up captive portal authentication on a switch to redirect web browser requests to a login page that requires the user to input a username and password.
Example: Setting Up Captive Portal Authentication on an EX Series Switch
You can set up captive portal authentication (hereafter referred to as captive portal) on a switch to redirect Web browser requests to a login page that requires the user to input a username and password. Upon successful authentication, the user is allowed to continue with the original page request and subsequent access to the network.
This example describes how to set up captive portal on an EX Series switch:
Requirements
This example uses the following hardware and software components:
An EX Series switch that supports captive portal
Junos OS Release 10.1 or later for EX Series switches
Before you begin, be sure you have:
Performed basic bridging and VLAN configuration on the switch. See Example: Setting Up Basic Bridging and a VLAN for an EX Series Switch.
Generated an SSL certificate and installed it on the switch. See Generating SSL Certificates to Be Used for Secure Web Access (EX Series Switch).
Designed your captive portal login page. See Designing a Captive Portal Authentication Login Page on Switches.
Overview and Topology
This example shows the configuration required on the switch to enable captive portal on an interface. To permit a printer connected to the captive portal interface to access the LAN without going through captive portal, add its MAC address to the authentication allowlist. The MAC addresses in this list are permitted access on the interface without captive portal.
Topology
The topology for this example consists of one EX Series switch connected to a RADIUS authentication server. One interface on the switch is configured for captive portal. In this example, the interface is configured in multiple supplicant mode.
Configuration
To configure captive portal on your switch:
CLI Quick Configuration
To quickly configure captive portal on the switch after completing the tasks in the Requirements section, copy the following commands and paste them into the switch terminal window:
[edit] set access radius-server 10.204.96.165 port 1812 set access radius-server 10.204.96.165 secret "ABC123" set access profile profile1 authentication-order radius set access profile profile1 radius authentication-server 10.204.96.165 set system services web-management http set system services web-management https local-certificate my-signed-cert set services captive-portal secure-authentication https set services captive-portal interface ge-0/0/10.0 supplicant multiple set services captive-portal authentication-profile-name profile1 set ethernet-switching-options authentication-whitelist 00:10:12:e0:28:22 set services captive-portal custom-options post-authentication-url http://www.my-home-page.com
Procedure
Step-by-Step Procedure
To configure captive portal on the switch:
Define the server IP address, the server authentication port number, and configure the secret password. The secret password on the switch must match the secret password on the server:
[edit] user@switch# set access radius-server 10.204.96.165 port 1812 [edit] user@switch# set access radius-server 10.204.96.165 secret "ABC123"
Configure the authentication order, making
radiusthe first method of authentication:[edit] user@switch# set access profile profile1 authentication-order radius
Configure the server IP address to be tried in order to authenticate the supplicant:
[edit] user@switch# set access profile profile1 radius authentication-server 10.204.96.165
Enable HTTP access on the switch:
[edit] user@switch# set system services web-management http
To create a secure channel for Web access to the switch, configure captive portal for HTTPS:
Note:You can enable HTTP without enabling HTTPS, but we recommend HTTPS for security purposes.
Step-by-Step Procedure
Associate the security certificate with the Web server and enable HTTPS access on the switch:
[edit] user@switch# set system services web-management https local-certificate my-signed-cert
Configure captive portal to use HTTPS:
[edit] user@switch# set services captive-portal secure-authentication https
Enable an interface for captive portal:
[edit] user@switch# set services captive-portal interface ge-0/0/10 supplicant multiple
Specify the name of the access profile to be used for captive portal authentication:
[edit] user@switch# set services captive-portal authentication-profile-name profile1
(Optional) Allow specific clients to bypass captive portal:
Note:If the client is already attached to the switch, you must clear its MAC address from the captive portal authentication by using the
clear captive-portal mac-address mac-addresscommand after adding its MAC address to the allowlist. Otherwise the new entry for the MAC address will not be added to the Ethernet switching table and authentication bypass will not be allowed.[edit] user@switch# set ethernet-switching-options authentication-whitelist 00:10:12:e0:28:22
Note:Optionally, you can use
set ethernet-switching-options authentication-whitelist 00:10:12:e0:28:22 interface ge-0/0/10.0to limit the scope to the interface.(Optional) To redirect clients to a specified page rather than the page they originally requested, configure the post-authentication URL:
[edit] user@switch# set services captive-portal custom-options post-authentication-url http://www.my-home-page.com
Results
Display the results of the configuration:
[edit]
user@switch> show
system {
services {
web-management {
http;
https {
local-certificate my-signed-cert;
}
}
}
}
security {
certificates {
local {
my-signed-cert {
"-----BEGIN RSA PRIVATE KEY-----ABC123
...
ABC123-----END CERTIFICATE-----\n"; ## SECRET-DATA
}
}
}
}
services {
captive-portal {
interface {
ge-0/0/10.0 {
supplicant multiple;
}
}
secure-authentication https;
}
}
ethernet-switching-options {
authentication-whitelist {
00:10:12:e0:28:22/48;
}
}
Verification
To confirm that captive portal is configured and working properly, perform these tasks:
- Verifying That Captive Portal Is Enabled on the Interface
- Verify That Captive Portal Is Working Correctly
Verifying That Captive Portal Is Enabled on the Interface
Purpose
Verify that captive portal is configured on interface ge-0/0/10.
Action
Use the operational mode command show captive-portal
interface interface-name detail:
user@switch> show captive-portal interface ge-0/0/10.0 detail ge-0/0/10.0 Supplicant mode: Multiple Number of retries: 3 Quiet period: 60 seconds Configured CP session timeout: 3600 seconds Server timeout: 15 seconds
Meaning
The output confirms that captive portal is configured on interface ge-0/0/10 with the default settings for number of retries, quiet period, CP session timeout, and server timeout.
Verify That Captive Portal Is Working Correctly
Purpose
Verify that captive portal is working on the switch.
Action
Connect a client to interface ge-0/0/10. From the client, open a Web browser and request a webpage. The captive portal login page that you designed should be displayed. After you enter your login information and are authenticated against the RADIUS server, the Web browser should display either the page you requested or the post-authentication URL that you configured.
Troubleshooting
To troubleshoot captive portal, perform these tasks:
Troubleshooting Captive Portal
Problem
The switch does not return the captive portal login page when a user connected to a captive portal interface on the switch requests a Web page.
Solution
You can examine the ARP, DHCP, HTTPS, and DNS counters—if one or more of these counters are not incrementing, this provides an indication of where the problem lies. For example, if the client cannot get an IP address, check the switch interface to determine whether the DHCP counter is incrementing—if the counter increments, the DHCP packet was received by the switch.
user@switch> show captive-portal firewall ge-0/0/10.0 ge-0/0/10.0 Filter name: dot1x_ge-0/0/10 Counters: Name Bytes Packets dot1x_ge-0/0/10_CP_arp 7616 119 dot1x_ge-0/0/10_CP_dhcp 0 0 dot1x_ge-0/0/10_CP_http 0 0 dot1x_ge-0/0/10_CP_https 0 0 dot1x_ge-0/0/10_CP_t_dns 0 0 dot1x_ge-0/0/10_CP_u_dns 0 0
Configuring Captive Portal Authentication (CLI Procedure)
Configure captive portal authentication (hereafter referred to as captive portal) on an EX Series switch so that users connected to the switch are authenticated before being allowed to access the network. When the user requests a web page, a login page is displayed that requires the user to input a username and password. Upon successful authentication, the user is allowed to continue with the original page request and subsequent access to the network.
Before you begin, be sure you have:
Performed basic bridging and VLAN configuration on the switch. See Example: Setting Up Basic Bridging and a VLAN for an EX Series Switch.
Generated an SSL certificate and installed it on the switch. See Generating SSL Certificates to Be Used for Secure Web Access (EX Series Switch).
Configured basic access between the EX Series switch and the RADIUS server. See Example: Connecting a RADIUS Server for 802.1X to an EX Series Switch.
Designed your captive portal login page. See Designing a Captive Portal Authentication Login Page on Switches.
This topic includes the following tasks:
- Configuring Secure Access for Captive Portal
- Enabling an Interface for Captive Portal
- Configuring Bypass of Captive Portal Authentication
Configuring Secure Access for Captive Portal
To configure secure access for captive portal:
Enabling an Interface for Captive Portal
To enable an interface for captive portal:
[edit] user@switch# set services captive-portal interface interface-name
For example, to enable captive portal on the interface ge-0/0/10:
[edit] user@switch# set services captive-portal interface ge-0/0/10
Configuring Bypass of Captive Portal Authentication
To allow specific clients to bypass captive portal:
[edit] user@switch# set ethernet-switching-options authentication-whitelist mac-address
For example, to allow specific clients to bypass captive portal:
[edit] user@switch# set ethernet-switching-options authentication-whitelist 00:10:12:e0:28:22
Optionally, you can use set ethernet-switching-options
authentication-whitelist 00:10:12:e0:28:22 interface ge-0/0/10.0 to limit the scope to the interface.
If the client is already attached to the switch, you must
clear its MAC address from the captive portal authentication by using
the clear captive-portal mac-address mac-address command after adding its MAC address to the allowlist. Otherwise
the new entry for the MAC address will not be added to the Ethernet
switching table and authentication bypass will not be allowed.
Designing a Captive Portal Authentication Login Page on Switches
You can set up captive portal authentication on your switch to redirect all Web browser requests to a login page that requires users to input a username and password before they are allowed access. Upon successful authentication, users are allowed access to the network and redirected to the original page requested.
Junos OS provides a customizable template for the captive portal window that allows you to easily design and modify the look of the captive portal login page. You can modify the design elements of the template to change the look of your captive portal login page and to add instructions or information to the page. You can also modify any of the design elements of a captive portal login page.
The first screen displayed before the captive login page requires the user to read the terms and conditions of use. By clicking the Agree button, the user can access the captive portal login page.
Figure 1 shows an example of a captive portal login page:
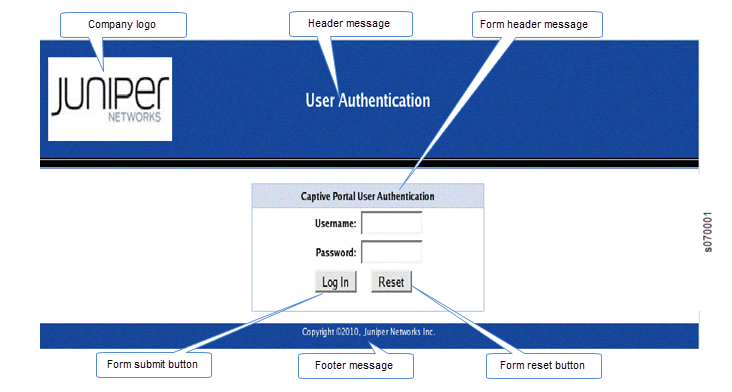
Table 1 summarizes the configurable elements of a captive portal login page.
| Element | CLI Statement | Description |
|---|---|---|
Footer background color |
footer-bgcolor hex-color |
The HTML hexadecimal code for the background color of the captive portal login page footer. |
Footer message |
footer-message text-string |
Text displayed in the footer of the captive portal login page. You can include copyright information, links, and additional information such as help instructions, legal notices, or a privacy policy The default text shown in the footer is Copyright @2010, Juniper Networks Inc. |
Footer text color |
footer- text-color color |
Color of the text in the footer. The default color is white. |
Form header background color |
form-header-bgcolor hex-color |
The HTML hexadecimal code for the background color of the header bar across the top of the form area of the captive portal login page. |
Form header message |
form-header-message text-string |
Text displayed in the header of the captive portal login page. The default text is Captive Portal User Authentication . |
Form header text color |
form-header- text- color color |
Color of the text in the form header. The default color is black. |
Form reset button label |
form-reset-label label-name |
Using the Reset button, the user can clear the username and password fields on the form. |
Form submit button label |
form-submit-label label-name |
Using the Login button, the user can submit the login information. |
Header background color |
header-bgcolor hex-color |
The HTML hexadecimal code for the background color of the captive portal login page header. |
Header logo |
header-logo filename |
Filename of the file containing the image of the logo that you want to appear in the header of the captive portal login page. The image file can be in GIF, JPEG, or PNG format. You can upload a logo image file to the switch. Copy the logo to the /var/tmp directory on the switch (during commit, the files are saved to persistent locations). If you do not specify a logo image, the Juniper Networks logo is displayed. |
Header message |
header-message text-string |
Text displayed in the page header. The default text is User Authentication. |
Header text color |
header-text- colorcolor |
Color of the text in the header. The default color is white. |
Post-authentication URL |
post-authentication-url url |
URL to which the users are directed on successful authentication. By default, users are directed to the page they had originally requested. |
To design the captive portal login page:
Now you can commit the configuration.
For the custom options that you do not specify, the default value is used.
See Also
Configuring Captive Portal Authentication (CLI Procedure) on an EX Series Switche with ELS Support
This task uses Junos OS for switches with support for the Enhanced Layer 2 Software (ELS) configuration style. If your switch runs software that does not support ELS, see Configuring Captive Portal Authentication (CLI Procedure). For ELS details, see Using the Enhanced Layer 2 Software CLI.
Configure captive portal authentication (hereafter referred to as captive portal) on a switch so that users connected to the switch are authenticated before being allowed to access the network. When the user requests a webpage, a login page is displayed that requires the user to input a username and password. Upon successful authentication, the user is allowed to continue with the original page request and subsequent access to the network.
Before you begin, be sure you have:
Performed basic bridging and VLAN configuration on the switch. See Example: Setting Up Basic Bridging and a VLAN for an EX Series Switch with ELS Support .
Generated an SSL certificate and installed it on the switch. See Generating SSL Certificates to Be Used for Secure Web Access (EX Series Switch).
Configured basic access between the switch and the RADIUS server. See Example: Connecting a RADIUS Server for 802.1X to an EX Series Switch.
Designed your captive portal login page. See Designing a Captive Portal Authentication Login Page on Switches.
This topic includes the following tasks:
- Configuring Secure Access for Captive Portal
- Enabling an Interface for Captive Portal
- Configuring Bypass of Captive Portal Authentication
Configuring Secure Access for Captive Portal
To configure secure access for captive portal:
Enabling an Interface for Captive Portal
To enable an interface for use with captive portal authentication:
[edit] user@switch# set services captive-portal interface interface-name
Configuring Bypass of Captive Portal Authentication
You can allow specific clients to bypass captive portal authentication:
[edit] user@switch# set switch-options authentication-whitelist mac-address
Optionally, you can use set switch-options authentication-whitelist mac-address interface interface-name to limit the scope to the interface.
If the client is already attached to the switch, you must
clear its MAC address from the captive portal authentication by using
the clear captive-portal mac-address session-mac-addr command after adding its MAC address to the allowlist. Otherwise,
the new entry for the MAC address is not added to the Ethernet switching
table and the authentication bypass is not allowed.
Example: Setting Up Captive Portal Authentication on an EX Series Switch with ELS Support
This example uses Junos OS for EX Series switches with support for the Enhanced Layer 2 Software (ELS) configuration style. If your switch runs software that does not support ELS, see Example: Setting Up Captive Portal Authentication on an EX Series Switch. For ELS details, see Using the Enhanced Layer 2 Software CLI.
You can set up captive portal authentication (hereafter referred to as captive portal) on a switch to redirect Web browser requests to a login page that requires the user to input a username and password. Upon successful authentication, the user is allowed to continue with the original page request and subsequent access to the network.
This example describes how to set up captive portal on an EX Series switch:
Requirements
This example uses the following software and hardware components:
Junos OS Release 13.2X50 or later for EX Series switches
An EX Series switch with support for ELS
Before you begin, be sure you have:
Performed basic bridging and VLAN configuration on the switch. See Example: Setting Up Basic Bridging and a VLAN for an EX Series Switch with ELS Support .
Generated an SSL certificate and installed it on the switch. See Generating SSL Certificates to Be Used for Secure Web Access (EX Series Switch).
Configured basic access between the EX Series switch and the RADIUS server. See Example: Connecting a RADIUS Server for 802.1X to an EX Series Switch.
Designed your captive portal login page. See Designing a Captive Portal Authentication Login Page on Switches.
Overview and Topology
This example shows the configuration required on the switch to enable captive portal on an interface. To permit a printer connected to the captive portal interface to access the LAN, add its MAC address to the authentication allowlist and assign it to a VLAN, vlan1. The MAC addresses on this list are permitted access on the interface without captive portal authentication.
Topology
The topology for this example consists of one EX Series switch connected to a RADIUS authentication server. One interface on the switch is configured for captive portal. In this example, the interface is configured in multiple supplicant mode.
Configuration
To configure captive portal on your switch:
CLI Quick Configuration
To quickly configure captive portal on the switch after completing the tasks in the Requirements section, copy the following commands and paste them into the switch terminal window:
[edit] set system services web-management https local-certificate my-signed-cert set services captive-portal secure-authentication https set services captive-portal interface ge-0/0/10.0 supplicant multiple set switch-options authentication-whitelist 00:10:12:e0:28:22 vlan-assignment vlan1 set custom-options post-authentication-url http://www.my-home-page.com
Procedure
Step-by-Step Procedure
To create a secure channel for Web access to the switch, configure captive portal for HTTPS:
Step-by-Step Procedure
Associate the security certificate with the Web server and enable HTTPS on the switch:
[edit] user@switch# set system services web-management https local-certificate my-signed-cert
Note:You can enable HTTP instead of HTTPS, but we recommend that you enable HTTPS for security purposes.
Configure captive portal to use HTTPS:
[edit] user@switch# set services captive-portal secure-authentication https
Enable an interface for captive portal:
[edit] user@switch# set services captive-portal interface ge-0/0/10 supplicant multiple
(Optional) Allow specific clients to bypass captive portal authentication:
Note:If the client is already attached to the switch, you must clear its MAC address from the captive portal authentication by using the
clear captive-portal mac-address mac-addresscommand after adding its MAC address to the allowlist. Otherwise, the new entry for the MAC address will not be added to the Ethernet switching table and the authentication bypass will not be allowed.[edit] user@switch# set switch-options authentication-whitelist 00:10:12:e0:28:22 vlan-assignment vlan1
Note:Optionally, you can use set switch-options authentication-whitelist 00:10:12:e0:28:22 vlan-assignment vlan1 interface ge-0/0/10.0 to limit the scope to the interface.
(Optional) To redirect clients to a specified page rather than the page they originally requested, configure the post-authentication URL:
[edit services captive-portal] user@switch# set custom-options post-authentication-url http://www.my-home-page.com
Results
Display the results of the configuration:
[edit]
user@switch# show
system {
services {
web-management {
https {
local-certificate my-signed-cert;
}
}
}
}
security {
certificates {
local {
my-signed-cert {
"-----BEGIN RSA PRIVATE KEY-----\ABC123
ABC123ABC123ABC123 ... ABC123
----END CERTIFICATE-----\n"; ## SECRET-DATA
}
}
}
}
services {
captive-portal {
interface {
ge-0/0/10.0 {
supplicant multiple;
}
}
secure-authentication https;
custom-options {
post-authentication-url http://www.my-home-page.com;
}
}
}
switch-options {
authentication-whitelist {
00:10:12:e0:28:22/48 {
vlan-assignment vlan1;
}
}
}
Verification
To confirm that captive portal authentication is configured and working properly, perform these tasks:
- Verifying That Captive Portal Is Enabled on the Interface
- Verify That Captive Portal Is Working Correctly
Verifying That Captive Portal Is Enabled on the Interface
Purpose
Verify that captive portal is configured on the interface ge-0/0/10.
Action
Use the operational mode command show captive-portal
interface interface-name detail:
user@switch> show captive-portal interface ge-0/0/10.0 detail ge-0/0/10.0 Supplicant mode: Multiple Number of retries: 3 Quiet period: 60 seconds Configured CP session timeout: 3600 seconds Server timeout: 15 seconds
Meaning
The output confirms that captive portal is configured
on the interface ge-0/0/10, with the
default settings for number of retries, quiet period, CP session timeout,
and server timeout.
Verify That Captive Portal Is Working Correctly
Purpose
Verify that captive portal is working on the switch.
Action
Connect a client to the interface ge-0/0/10. From the client, open a Web browser and request a webpage. The captive portal login page that you designed should be displayed. After you enter your login information and are authenticated against the RADIUS server, the Web browser should display either the page you requested or the post-authentication URL that you configured.
Troubleshooting
To troubleshoot captive portal, perform this task:
Troubleshooting Captive Portal
Problem
The switch does not return the captive portal login page when a user connected to a captive portal interface on the switch requests a webpage.
Solution
You can examine the ARP, DHCP, HTTPS, and DNS counters—if one or more of these counters are not incrementing, this provides an indication of where the problem lies. For example, if the client cannot get an IP address, you might check the switch interface to determine whether the DHCP counter is incrementing—if the counter increments, the DHCP packet was received by the switch.
user@switch> show captive-portal firewall ge-0/0/10.0 ge-0/0/10.0 Filter name: dot1x_ge-0/0/10 Counters: Name Bytes Packets dot1x_ge-0/0/10_CP_arp 7616 119 dot1x_ge-0/0/10_CP_dhcp 0 0 dot1x_ge-0/0/10_CP_http 0 0 dot1x_ge-0/0/10_CP_https 0 0 dot1x_ge-0/0/10_CP_t_dns 0 0 dot1x_ge-0/0/10_CP_u_dns 0 0
