Example: Configuring Group VPNs in Group VPNv2 on Routing Devices
Group VPNv2 is the name of the Group VPN technology on MX5, MX10, MX40, MX80, MX104, MX240, MX480, and MX960 routers. Group VPNv2 is different from the Group VPN technology implemented on SRX Security Gateways. The term Group VPN is sometimes used in this document to refer to the technology in general, not to the SRX technology.
This example shows how to configure Group VPNs in Group VPNv2 to extend the IP Security (IPsec) architecture to support group security associations (GSAs) that are shared by a group of routers.
Requirements
This example uses the following hardware and software components:
Two MX Series 5G Universal Routing Platforms with MS-MIC-16G or MS-MPC-PIC line cards
Reachability to one or more Cisco Group Controllers or Key Servers (GC/KS)
Junos OS Release 14.1 or later running on the MX Series routers
Before you begin:
Configure the routers for network communication.
Configure the Cisco GC/KS.
Configure the group member device interfaces.
Overview
Starting with Junos OS Release 14.1, MX Series routers with MS-MIC-16G and MS-MPC-PIC line cards provide the Group VPNv2 member functionality support with one or more Cisco Group Controllers or Key Servers (GC/KS). The group members can connect to a maximum of four Cisco GC/KSs with minimum interoperability with the cooperative servers.
This feature also provides system logging support for Group VPNv2 functionality, and routing instance support for both control and data traffic.
Topology
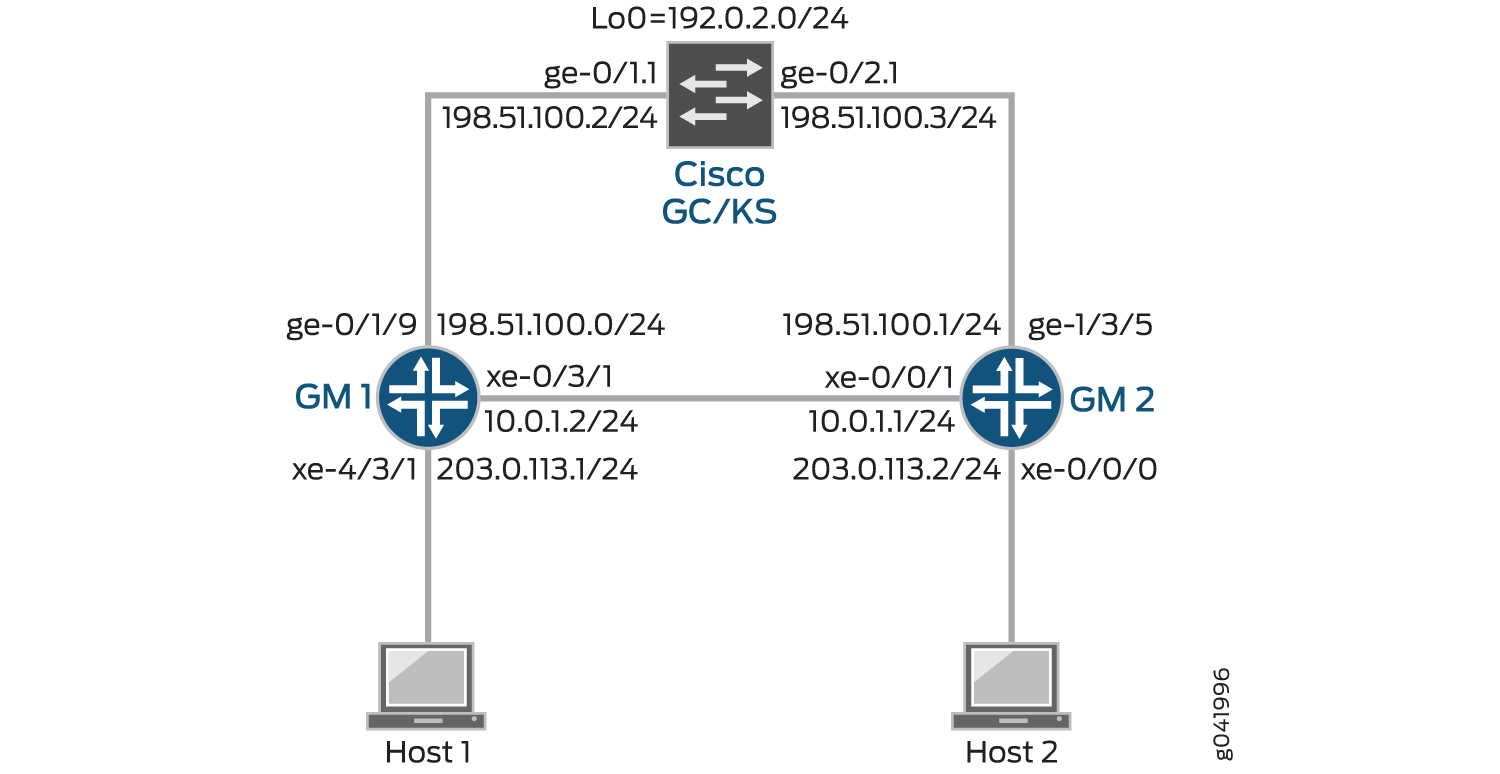
In Figure 1, a Group VPN is configured between a Cisco group server, GC/KS – and two group members, GM1 and GM2. The group members are connected to host devices.
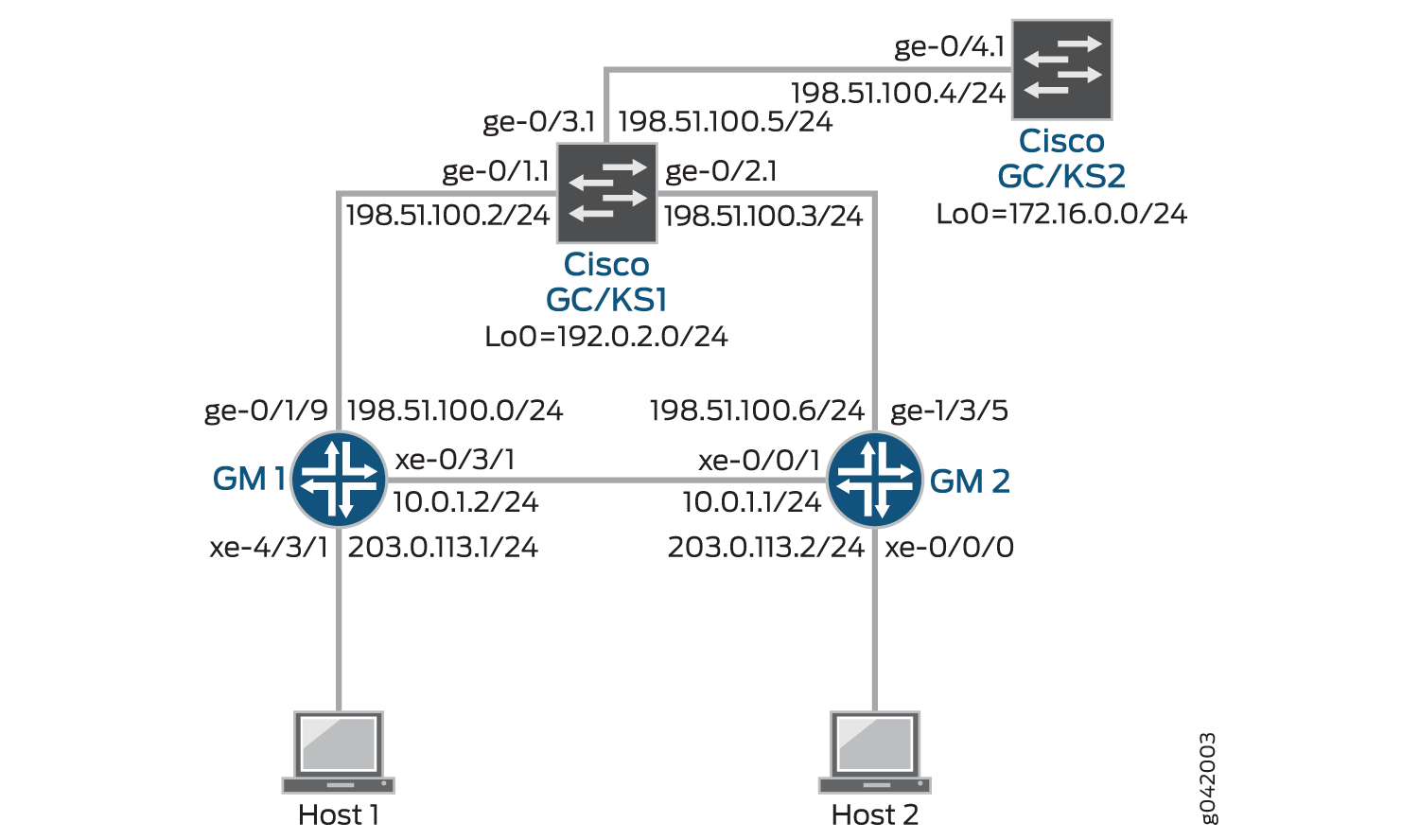
In Figure 2, a Group VPN is configured between GM1 and GM2, and GC/KS1 and GC/KS2 are the primary and secondary group servers, respectively.
Configuration
Configuring Group VPNv2 with a Single GC/KS
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then commit the configuration.
GM1
set interfaces ms-4/0/0 unit 1 family inet set interfaces ge-0/1/9 vlan-tagging set interfaces ge-0/1/9 unit 1 vlan-id 11 set interfaces ge-0/1/9 unit 1 family inet address 198.51.100.0/24 set interfaces xe-0/3/1 vlan-tagging set interfaces xe-0/3/1 unit 1 vlan-id 1 set interfaces xe-0/3/1 unit 1 family inet service input service-set gvpn-service-set set interfaces xe-0/3/1 unit 1 family inet service output service-set gvpn-service-set set interfaces xe-0/3/1 unit 1 family inet address 10.0.1.2/24 set interfaces xe-4/3/1 unit 0 family inet address 203.0.113.1/24 set routing-options static route 192.0.2.0/24 next-hop 198.51.100.2 set routing-options static route 203.0.113.0/24 next-hop 10.0.1.1 set security group-vpn member ike proposal ike-proposal authentication-method pre-shared-keys set security group-vpn member ike proposal ike-proposal dh-group group2 set security group-vpn member ike proposal ike-proposal authentication-algorithm sha1 set security group-vpn member ike proposal ike-proposal encryption-algorithm 3des-cbc set security group-vpn member ike policy ike-policy mode main set security group-vpn member ike policy ike-policy proposals ike-proposal set security group-vpn member ike policy ike-policy pre-shared-key ascii-text ""$9$QEni3/t1RSM87uO87-V4oz36" set security group-vpn member ike gateway gw-group1 ike-policy ike-policy set security group-vpn member ike gateway gw-group1 server-address 192.0.2.0 set security group-vpn member ike gateway gw-group1 local-address 198.51.100.0 set security group-vpn member ipsec vpn vpn-group1 ike-gateway gw-group1 set security group-vpn member ipsec vpn vpn-group1 group 1 set security group-vpn member ipsec vpn vpn-group1 match-direction output set services service-set gvpn-service-set interface-service service-interface ms-4/0/0.1 set services service-set gvpn-service-set ipsec-group-vpn vpn-group1
GM2
set interfaces ms-0/2/0 unit 1 family inet set interfaces xe-0/0/0 unit 0 family inet address 203.0.113.2/24 set interfaces xe-0/1/1 vlan-tagging set interfaces xe-0/1/1 unit 1 vlan-id 1 set interfaces xe-0/1/1 unit 1 family inet service input service-set gvpn-service-set set interfaces xe-0/1/1 unit 1 family inet service output service-set gvpn-service-set set interfaces xe-0/1/1 unit 1 family inet address 10.0.1.1/24 set interfaces ge-1/3/5 vlan-tagging set interfaces ge-1/3/5 unit 1 vlan-id 11 set interfaces ge-1/3/5 unit 1 family inet address 198.51.100.1/24 set routing-options static route 192.0.2.0/24 next-hop 198.51.100.3 set routing-options static route 203.0.113.2/24 next-hop 10.0.1.2 set security group-vpn member ike proposal ike-proposal authentication-method pre-shared-keys set security group-vpn member ike proposal ike-proposal dh-group group2 set security group-vpn member ike proposal ike-proposal authentication-algorithm sha1 set security group-vpn member ike proposal ike-proposal encryption-algorithm 3des-cbc set security group-vpn member ike policy ike-policy mode main set security group-vpn member ike policy ike-policy proposals ike-proposal set security group-vpn member ike policy ike-policy pre-shared-key ascii-text ""$9$QEni3/t1RSM87uO87-V4oz36" set security group-vpn member ike gateway gw-group1 ike-policy ike-policy set security group-vpn member ike gateway gw-group1 server-address 192.0.2.0 set security group-vpn member ike gateway gw-group1 local-address 198.51.100.0 set security group-vpn member ipsec vpn vpn-group1 ike-gateway gw-group1 set security group-vpn member ipsec vpn vpn-group1 group 1 set security group-vpn member ipsec vpn vpn-group1 match-direction output set services service-set gvpn-service-set interface-service service-interface ms-0/2/0.1 set services service-set gvpn-service-set ipsec-group-vpn vpn-group1
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For information about navigating the CLI, see Using the CLI Editor in Configuration Mode.
To configure GM1:
Configure the Router GM1 interfaces.
[edit interfaces]user@GM1# set ms-4/0/0 unit 1 family inet user@GM1# set ge-0/1/9 vlan-tagging user@GM1# set ge-0/1/9 unit 1 vlan-id 11 user@GM1# set ge-0/1/9 unit 1 family inet address 198.51.100.0/24 user@GM1# set xe-0/3/1 vlan-tagging user@GM1# set xe-0/3/1 unit 1 vlan-id 1 user@GM1# set xe-0/3/1 unit 1 family inet service input service-set gvpn-service-set user@GM1# set xe-0/3/1 unit 1 family inet service output service-set gvpn-service-set user@GM1# set xe-0/3/1 unit 1 family inet address 10.0.1.2/24 user@GM1# set interfaces xe-4/3/1 unit 0 family inet address 203.0.113.1/24Configure static routes to reach the group server and member 2.
[edit routing-options]user@GM1# set static route 192.0.2.0/24 next-hop 198.51.100.2 user@GM1# set static route 203.0.113.0/24 next-hop 10.0.1.1Define the IKE proposal.
[edit security]user@GM1# set group-vpn member ike proposal ike-proposalConfigure the Phase 1 SA for ike-proposal.
[edit security]user@GM1# set group-vpn member ike proposal ike-proposal authentication-method pre-shared-keys user@GM1# set group-vpn member ike proposal ike-proposal dh-group group2 user@GM1# set group-vpn member ike proposal ike-proposal authentication-algorithm sha1 user@GM1# set group-vpn member ike proposal ike-proposal encryption-algorithm 3des-cbcDefine the IKE policy.
[edit security]user@GM1# set group-vpn member ike policy ike-policy mode main user@GM1# set group-vpn member ike policy ike-policy proposals ike-proposal user@GM1# set group-vpn member ike policy ike-policy pre-shared-key ascii-text ""$9$QEni3/t1RSM87uO87-V4oz36"Set the remote gateways for gw-group1.
[edit security]user@GM1# set group-vpn member ike gateway gw-group1 ike-policy ike-policy user@GM1# set group-vpn member ike gateway gw-group1 server-address 192.0.2.0 user@GM1# set group-vpn member ike gateway gw-group1 local-address 198.51.100.0Configure the group identifier and IKE gateway for gw-group1.
[edit security]user@GM1# set group-vpn member ipsec vpn vpn-group1 ike-gateway gw-group1 user@GM1# set group-vpn member ipsec vpn vpn-group1 group 1 user@GM1# set group-vpn member ipsec vpn vpn-group1 match-direction outputConfigure the service set for gw-group1.
[edit services]user@GM1# set service-set gvpn-service-set interface-service service-interface ms-4/0/0.1 user@GM1# set service-set gvpn-service-set ipsec-group-vpn vpn-group1
Results
From configuration mode, confirm your configuration
by entering the show interfaces, show routing-options, show security, and show services commands.
If the output does not display the intended configuration, repeat
the instructions in this example to correct the configuration.
GM1
user@GM1# show interfaces
ge-0/1/9 {
vlan-tagging;
unit 1 {
vlan-id 11;
family inet {
address 198.51.100.0/24;
}
}
}
xe-0/3/1 {
vlan-tagging;
unit 1 {
vlan-id 1;
family inet {
service {
input {
service-set gvpn-service-set;
}
output {
service-set gvpn-service-set;
}
}
address 10.0.1.2/24;
}
}
}
ms-4/0/0 {
unit 1 {
family inet;
}
}
xe-4/3/1 {
unit 0 {
family inet {
address 203.0.113.1/24;
}
}
}
user@GM1# show routing-options
static {
route 192.0.2.0/24 next-hop 198.51.100.2;
route 203.0.113.0/24 next-hop 10.0.1.1;
}
user@GM1# show security
group-vpn {
member {
ike {
proposal ike-proposal {
authentication-method pre-shared-keys;
dh-group group2;
authentication-algorithm sha1;
encryption-algorithm 3des-cbc;
}
policy ike-policy {
mode main;
pre-shared-key ascii-text ""$9$QEni3/t1RSM87uO87-V4oz36"; ## SECRET-DATA
proposals ike-proposal;
}
gateway gw-group1 {
ike-policy ike-policy;
server-address 192.0.2.0;
local-address 198.51.100.0;
}
}
ipsec {
vpn vpn-group1 {
ike-gateway gw-group1;
group 1;
match-direction output;
}
}
}
}
user@GM1# show services
service-set gvpn-service-set {
interface-service {
service-interface ms-4/0/0.1;
}
ipsec-group-vpn vpn-group1;
}
Configuring Group VPNv2 with Multiple GC/KS
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then commit the configuration.
GM1
set interfaces ms-4/0/0 unit 1 family inet set interfaces ge-0/1/9 vlan-tagging set interfaces ge-0/1/9 unit 1 vlan-id 11 set interfaces ge-0/1/9 unit 1 family inet address 198.51.100.0/24 set interfaces xe-0/3/1 vlan-tagging set interfaces xe-0/3/1 unit 1 vlan-id 1 set interfaces xe-0/3/1 unit 1 family inet service input service-set gvpn-service-set set interfaces xe-0/3/1 unit 1 family inet service output service-set gvpn-service-set set interfaces xe-0/3/1 unit 1 family inet address 10.0.1.2/24 set interfaces xe-4/3/1 unit 0 family inet address 203.0.113.1/24 set routing-options static route 192.0.2.0/24 next-hop 198.51.100.2 set routing-options static route 203.0.113.0/24 next-hop 10.0.1.1 set security group-vpn member ike proposal ike-proposal authentication-method pre-shared-keys set security group-vpn member ike proposal ike-proposal dh-group group2 set security group-vpn member ike proposal ike-proposal authentication-algorithm sha1 set security group-vpn member ike proposal ike-proposal encryption-algorithm 3des-cbc set security group-vpn member ike policy ike-policy mode main set security group-vpn member ike policy ike-policy proposals ike-proposal set security group-vpn member ike policy ike-policy pre-shared-key ascii-text ""$9$QEni3/t1RSM87uO87-V4oz36" set security group-vpn member ike gateway gw-group1 ike-policy ike-policy set security group-vpn member ike gateway gw-group1 server-address 192.0.2.0 set security group-vpn member ike gateway gw-group1 server-address 172.16.0.0 set security group-vpn member ike gateway gw-group1 local-address 198.51.100.0 set security group-vpn member ipsec vpn vpn-group1 ike-gateway gw-group1 set security group-vpn member ipsec vpn vpn-group1 group 1 set security group-vpn member ipsec vpn vpn-group1 match-direction output set services service-set gvpn-service-set interface-service service-interface ms-4/0/0.1 set services service-set gvpn-service-set ipsec-group-vpn vpn-group1
GM2
set interfaces ms-0/2/0 unit 1 family inet set interfaces xe-0/0/0 unit 0 family inet address 203.0.113.2/24 set interfaces xe-0/1/1 vlan-tagging set interfaces xe-0/1/1 unit 1 vlan-id 1 set interfaces xe-0/1/1 unit 1 family inet service input service-set gvpn-service-set set interfaces xe-0/1/1 unit 1 family inet service output service-set gvpn-service-set set interfaces xe-0/1/1 unit 1 family inet address 10.0.1.1/24 set interfaces ge-1/3/5 vlan-tagging set interfaces ge-1/3/5 unit 1 vlan-id 11 set interfaces ge-1/3/5 unit 1 family inet address 198.51.100.1/24 set routing-options static route 192.0.2.0/24 next-hop 198.51.100.3 set routing-options static route 203.0.113.2/24 next-hop 10.0.1.2 set security group-vpn member ike proposal ike-proposal authentication-method pre-shared-keys set security group-vpn member ike proposal ike-proposal dh-group group2 set security group-vpn member ike proposal ike-proposal authentication-algorithm sha1 set security group-vpn member ike proposal ike-proposal encryption-algorithm 3des-cbc set security group-vpn member ike policy ike-policy mode main set security group-vpn member ike policy ike-policy proposals ike-proposal set security group-vpn member ike policy ike-policy pre-shared-key ascii-text ""$9$QEni3/t1RSM87uO87-V4oz36" set security group-vpn member ike gateway gw-group1 ike-policy ike-policy set security group-vpn member ike gateway gw-group1 server-address 192.0.2.0 set security group-vpn member ike gateway gw-group1 server-address 172.16.0.0 set security group-vpn member ike gateway gw-group1 local-address 198.51.100.1 set security group-vpn member ipsec vpn vpn-group1 ike-gateway gw-group1 set security group-vpn member ipsec vpn vpn-group1 group 1 set security group-vpn member ipsec vpn vpn-group1 match-direction output set services service-set gvpn-service-set interface-service service-interface ms-0/2/0.1 set services service-set gvpn-service-set ipsec-group-vpn vpn-group1
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For information about navigating the CLI, see Using the CLI Editor in Configuration Mode.
To configure GM1:
Configure the Router GM1 interfaces.
[edit interfaces]user@GM1# set ms-4/0/0 unit 1 family inet user@GM1# set ge-0/1/9 vlan-tagging user@GM1# set ge-0/1/9 unit 1 vlan-id 11 user@GM1# set ge-0/1/9 unit 1 family inet address 198.51.100.0/24 user@GM1# set xe-0/3/1 vlan-tagging user@GM1# set xe-0/3/1 unit 1 vlan-id 1 user@GM1# set xe-0/3/1 unit 1 family inet service input service-set gvpn-service-set user@GM1# set xe-0/3/1 unit 1 family inet service output service-set gvpn-service-set user@GM1# set xe-0/3/1 unit 1 family inet address 10.0.1.2/24 user@GM1# set xe-4/3/1 unit 0 family inet address 203.0.113.1/24Configure static routes to reach the group server and member 2.
[edit routing-options]user@GM1# set static route 192.0.2.0/24 next-hop 198.51.100.2 user@GM1# set static route 203.0.1.0/24 next-hop 10.0.1.1Define the IKE proposal.
[edit security]user@GM1# set group-vpn member ike proposal ike-proposalConfigure the Phase 1 SA for ike-proposal.
[edit security]user@GM1# set group-vpn member ike proposal ike-proposal authentication-method pre-shared-keys user@GM1# set group-vpn member ike proposal ike-proposal dh-group group2 user@GM1# set group-vpn member ike proposal ike-proposal authentication-algorithm sha1 user@GM1# set group-vpn member ike proposal ike-proposal encryption-algorithm 3des-cbcDefine the IKE policy.
[edit security]user@GM1# set group-vpn member ike policy ike-policy mode main user@GM1# set group-vpn member ike policy ike-policy proposals ike-proposal user@GM1# set group-vpn member ike policy ike-policy pre-shared-key ascii-text ""$9$QEni3/t1RSM87uO87-V4oz36"Set the remote gateways for gw-group1.
[edit security]user@GM1# set group-vpn member ike gateway gw-group1 ike-policy ike-policy user@GM1# set group-vpn member ike gateway gw-group1 server-address 192.0.2.0 user@GM1# set group-vpn member ike gateway gw-group1 server-address 172.16.0.0 user@GM1# set group-vpn member ike gateway gw-group1 local-address 198.51.100.0Configure the group identifier and IKE gateway for gw-group1.
[edit security]user@GM1# set group-vpn member ipsec vpn vpn-group1 ike-gateway gw-group1 user@GM1# set group-vpn member ipsec vpn vpn-group1 group 1 user@GM1# set group-vpn member ipsec vpn vpn-group1 match-direction outputConfigure the service set for gw-group1.
[edit services]user@GM1# set service-set gvpn-service-set interface-service service-interface ms-4/0/0.1 user@GM1# set service-set gvpn-service-set ipsec-group-vpn vpn-group1
Results
From configuration mode, confirm your configuration
by entering the show interfaces, show routing-options, show security, and show services commands.
If the output does not display the intended configuration, repeat
the instructions in this example to correct the configuration.
GM1
user@GM1# show interfaces
ge-0/1/9 {
vlan-tagging;
unit 1 {
vlan-id 11;
family inet {
address 198.51.100.0/24;
}
}
}
xe-0/3/1 {
vlan-tagging;
unit 1 {
vlan-id 1;
family inet {
service {
input {
service-set gvpn-service-set;
}
output {
service-set gvpn-service-set;
}
}
address 10.0.1.2/24;
}
}
}
ms-4/0/0 {
unit 1 {
family inet;
}
}
xe-4/3/1 {
unit 0 {
family inet {
address 203.0.113.1/24;
}
}
}
user@GM1# show routing-options
static {
route 192.0.2.0/24 next-hop 198.51.100.2;
route 203.0.113.0/24 next-hop 10.0.1.1;
}
user@GM1# show security
group-vpn {
member {
ike {
proposal ike-proposal {
authentication-method pre-shared-keys;
dh-group group2;
authentication-algorithm sha1;
encryption-algorithm 3des-cbc;
}
policy ike-policy {
mode main;
pre-shared-key ascii-text ""$9$QEni3/t1RSM87uO87-V4oz36"; ## SECRET-DATA
proposals ike-proposal;
}
gateway gw-group1 {
ike-policy ike-policy;
server-address [ 192.0.2.0 172.16.0.0 ];
local-address 198.51.100.0;
}
}
ipsec {
vpn vpn-group1 {
ike-gateway gw-group1;
group 1;
match-direction output;
}
}
}
}
user@GM1# show services
service-set gvpn-service-set {
interface-service {
service-interface ms-4/0/0.1;
}
ipsec-group-vpn vpn-group1;
}
Verification
Confirm that the configuration is working properly.
- Verifying the Group Member IKE SA
- Verifying the Group Member IPsec SA
- Verifying the Group Member IPsec Statistics
Verifying the Group Member IKE SA
Purpose
Verify the IKE SAs on Router GM1.
Action
From operational mode, run the show security group-vpn
member ike security-associations detail command.
user@GM1> show security group-vpn member ike security-associations detail IKE peer 192.0.2.0, Index 2994970, Gateway Name: gw-group1 Role: Initiator, State: UP Initiator cookie: 7fad16089a123bcd, Responder cookie: 536b33ffe89799de Exchange type: Main, Authentication method: Pre-shared-keys Local: 198.51.100.0:848, Remote: 192.0.2.0:848 Lifetime: Expires in 175 seconds Peer ike-id: 192.0.2.0 Xauth user-name: not available Xauth assigned IP: 0.0.0.0 Algorithms: Authentication : hmac-sha1-96 Encryption : 3des-cbc Pseudo random function: hmac-sha1 Diffie-Hellman group : DH-group-2 Traffic statistics: Input bytes : 752 Output bytes : 716 Input packets: 5 Output packets: 5 Flags: IKE SA is created IPSec security associations: 0 created, 0 deleted Phase 2 negotiations in progress: 0
Meaning
Router GM1 has established the IKE SA with the GC/KS for the group.
Verifying the Group Member IPsec SA
Purpose
Verify the IPsec SAs on Router GM1.
Action
From operational mode, run the show security group-vpn
member ipsec security-associations detail command.
user@GM1> show security group-vpn member ipsec security-associations detail
Virtual-system: root Group VPN Name: vpn-group1
Local Gateway: 198.51.100.1, GDOI Server: 192.0.2.0
Group Id: 1
Rule Match Direction: output, Tunnel-MTU: 1500
Routing Instance: default
DF-bit: clear
Stats:
Pull Succeeded : 18
Pull Failed : 0
Pull Timeout : 0
Pull Aborted : 0
Server Failover : 0
Delete Received : 0
Exceed Maximum Keys(4) : 0
Exceed Maximum Policies(1): 0
Unsupported Algo : 0
Flags:
Rekey Needed: no
List of policies received from server:
Tunnel-id: 10001
Source IP: ipv4_subnet(any:0,[0..7]=203.0.2.0/24)
Destination IP: ipv4_subnet(any:0,[0..7]=203.0.1.0/24)
Direction: bi-directional, SPI: e1c117c7
Protocol: ESP, Authentication: sha1, Encryption: 3des
Hard lifetime: Expires in 2526 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2366 seconds
Mode: Tunnel, Type: Group VPN, State: installed
Anti-replay service: N/A
Meaning
Router GM1 has established the IPsec SA with the GC/KS.
Verifying the Group Member IPsec Statistics
Purpose
Verify the IPsec statistics on Router GM1.
Action
From operational mode, run the show security group-vpn
member ipsec statistics command.
user@GM1> show security group-vpn member ipsec statistics PIC: ms-0/2/0, Service set: gvpn-service-set ESP Statistics: Encrypted bytes: 264 Decrypted bytes: 264 Encrypted packets: 3 Decrypted packets: 3 AH Statistics: Input bytes: 0 Output bytes: 0 Input packets: 0 Output packets: 0 Errors: AH authentication failures: 0 ESP authentication failures: 0 ESP decryption failures: 0 Bad headers: 0, Bad trailers: 0 Replay before window drops: 0, Replayed pkts: 0 IP integrity errors: 0, Exceeds tunnel MTU: 0 Rule lookup failures: 0, No SA errors: 0 Flow errors: 0, Misc errors: 0
Meaning
ESP Statistics shows that packet flows have
been encrypted and decrypted between the group members. Router GM1
has encrypted 3 packets and has received 3 decrypted packets from
Router GM2.
Troubleshooting
To troubleshoot the Group VPNv2 configuration, see:
- Negotiating the IKE SA
- Establishing the IKE SA
- Downloading the GDOI IPsec SA
- Traffic Encryption and Decryption
- Troubleshooting System Log Messages
Negotiating the IKE SA
Problem
The IKE SA negotiation is not triggered on the group member.
The output of the show ike and show security
group-vpn member ike security-associations commands does not
display the IKE negotiations.
Solution
To troubleshoot the IKE negotiation issue:
Check if the service interface status is up.
Use
show interfaces terse | match msto check if the MS interface is down. An MS interface goes down when the PIC is rebooting.Look for
Ignore gvpn vpn_name since it is inactivein the log file/var/log/gkmd.Check if the Group VPN is referenced by any service set in the configuration.
Enable
security group-vpn member ike traceoptions.Look for the following system log messages in the trace log file:
Dec 2 16:09:54 GVPN:iked_pm_gvpn_trigger called for gvpn200Dec 2 16:09:54 GVPN:PM NULL for gvpn gvpn200Dec 2 16:09:54 GVPN:Ignore gvpn gvpn200 since it is inactive
This means either the service set is inactive or the service interface is down.
Establishing the IKE SA
Problem
The IKE SA is not getting established with the GC/KS.
In this scenario, the IKE SA state is down in the show
security group-vpn member ike security-associations command
output:
user@GM1> show security group-vpn member ike security-associations
Index State Initiator cookie Responder cookie Mode Remote Address
5295626 DOWN 2d47c125d2a9805e 0000000000000000 Main 192.0.2.2
Solution
To troubleshoot the IKE SA issue:
Check if the server address configured under
[edit security group-vpn member ike gateway]is the correct one and is reachable.Use the
pingcommand between the remote devices to check network connectivity.Check if the local address in the
group-vpnconfiguration is also a configured address on any of the physical interfaces in the configuration.Check if the IKE proposals match between the group member and the GC/KS.
If there is a misconfiguration on the IKE SA negotiation, then do the following:
Enable
security group-vpn member ike traceoption.Look for the following message in the trace log file:
Dec 2 15:39:54 ikev2_fb_negotiation_done_isakmp: Entered IKE error code No proposal chosen (14), IKE SA 8dd7000 (neg 8dda800).
Look for a
No proposal chosenerror in the log file/var/log/gkmd.
Downloading the GDOI IPsec SA
Problem
The GDOI IPsec SAs are not downloaded from the GC/KS.
In this scenario, the GDOI groupkey-pull with the
configured GC/KS fails, and the show security group-vpn member
ipsec sa command output does not display anything.
Solution
To troubleshoot the GDOI IPsec SA issue:
Check if the IKE SA has been established with the GC/KS.
Check if the group ID configured on the GC/KS and the group member match.
Look for any group SA installation failures or other failures in the log file
/var/log/gkmd.Look for the following syslog messages to confirm use of an unsupported GDOI SA algorithm:
Dec 2 15:32:49 simpleman gkmd[1701]: Failed to install SA because of unsupported algo(encr: 3des-cbc, auth : (null)) for SPI 0x6645cdb5 from server 192.0.2.1Dec 2 15:32:49 simpleman gkmd[1701]: Member registration failed with key server 192.0.2.1 for group vpn gvpn200, reason SA unusable
Look for the following syslog messages to confirm use of unsupported GDOI policies:
Dec 2 15:34:34 simpleman gkmd[1701]: Failed to install SA because of too many(2) policies for SPI 0x6951550c from server 192.0.2.1Dec 2 15:34:34 simpleman gkmd[1701]: Member registration failed with key server 192.0.2.1 for group vpn gvpn200, reason SA unusable
Traffic Encryption and Decryption
Problem
The CLI shows IPsec SAs as installed, but traffic does not go through the SAs.
In this scenario, traffic matching the rules received from the
server fails to get encrypted or decrypted. The show security
group-vpn member ipsec statistics command output displays a
zero value for encrypt and decrypt packet count.
Solution
Look for Rule lookup failures counter in
the error section of the CLI output.
Troubleshooting System Log Messages
Problem
System log messages are generated to record the different Group VPNv2 events.
Solution
To interpret the system log messages, refer to the following:
Dec 2 15:29:10 simpleman gkmd[1701]: Member registration succeeded with key server 192.0.2.1 for group vpn gvpn200—GDOI pull was successful.Dec 2 15:21:18 simpleman gkmd[1701]: Member registration failed with key server 192.0.2.1 for group vpn gvpn200, reason Timed out—GDOI pull failed.Dec 2 15:34:34 simpleman gkmd[1701]: Failed to install SA because of too many(2) policies for SPI 0x6951550c from server 192.0.2.1—GDOI SA installation failed because of too many policies.Dec 2 15:21:18 simpleman gkmd[1701]: Server 192.0.2.1 is unreachable for group vpn gvpn200—Single GC/KS failed (Non-COOP).Dec 2 15:51:49 simpleman gkmd[1701]: Current key server 192.0.2.1 is unreachable and will try registering with next Key Server 192.1.1.2 for group vpn gvpn200—Particular GC/KS is not responding (COOP).Dec 2 15:56:24 simpleman gkmd[1701]: All servers are unreachable for group vpn gvpn200—None of the GC/KS are responding (COOP).Dec 2 16:01:43 simpleman gkmd[1701]: Member re-registering with Key Server 192.0.2.1 for group-vpn gvpn200—Member re-registration with the GC/KS.Dec 2 16:01:43 simpleman gkmd[1701]: Creating TEK with SPI 0xb35200ac tunnel_id 10001 for group vpn gvpn200—GDOI SA TEK creation was successful.Dec 2 16:29:01 simpleman gkmd[1701]: Deleting TEK with SPI 0x6dba2a76 tunnel_id 10001 for group vpn gvpn200 and reason cleared from CLI—GDOI SA TEK destroy was successful with reason.Different reasons for the GDOI SA TEK destroy are as follows:
Cleared from CLI
Hard lifetime expired
Too many TEKs
Configuration change
SA install error
Stale SA
Interface down
