Understand vSRX Virtual Firewall Deployment with Google Cloud
Understand vSRX Virtual Firewall Deployment with Google Cloud Platform
Google Cloud Platform (GCP) is a public cloud service provided by Google. Like Amazon Web Service (AWS) and Microsoft Azure, GCP offers a suite of products and services that allow you to build and host applications and websites, store data, and analyze data on Google’s scalable infrastructure. A pay-as-you-go model is delivered and saves you from building your own private cloud using dedicated hardware.
Google’s virtual private cloud (VPC) gives you the flexibility to scale and control how workloads connect regionally and globally. When you connect your on-premises or remote resources to GCP, you will have global access to your VPCs without needing to replicate connectivity or administrative policies in each region.
vSRX Virtual Firewall in a public cloud can be used for protecting service VMs from public Internet or protecting VMs in different subnets, or used as VPN Gateways.
Like AWS, GCP allows you to build your own VPCs on top of Google’s public infrastructure. Unlike AWS, GCP uses KVM instead of modified Xen as the hypervisor for VM management.
In a Google cloud, vSRX Virtual Firewall instances run on top of Google VPCs. A Google VPC has the following properties:
Provides a global private communication space.
Supports multitenancy in an organization.
Provides private communication between Google Cloud Platform (GCP) resources, such as Computing Engine and Cloud Storage.
Provides security for configuration access using identify and access management (IAM).
Extensible across hybrid environments.
When you create a resource in GCP, you choose a network and subnet. For resources other than instance templates, you also select a zone or a region. Selecting a zone implicitly selects its parent region. Because subnets are regional objects, the region you select for a resource determines the subnets it can use.
The process of creating an instance involves selecting a zone, a network, and a subnet. The subnets available for selection are restricted to those in the selected region. GCP assigns the instance an IP address from the range of available addresses in the subnet.
The process of creating a managed instance group involves selecting a zone or region, depending on the group type, and an instance template. The instance templates available for selection are restricted to those whose defined subnets are in the same region selected for the managed instance group. Instance templates are global resources. The process of creating an instance template involves selecting a network and a subnet. If you select an auto-mode network, you can choose “auto subnet” to defer subnet selection to one that is available in the selected region of any managed instance group that would use the template, because auto-mode networks have a subnet in every region by definition.
An example of a typical Google VPC is shown in Figure 1.
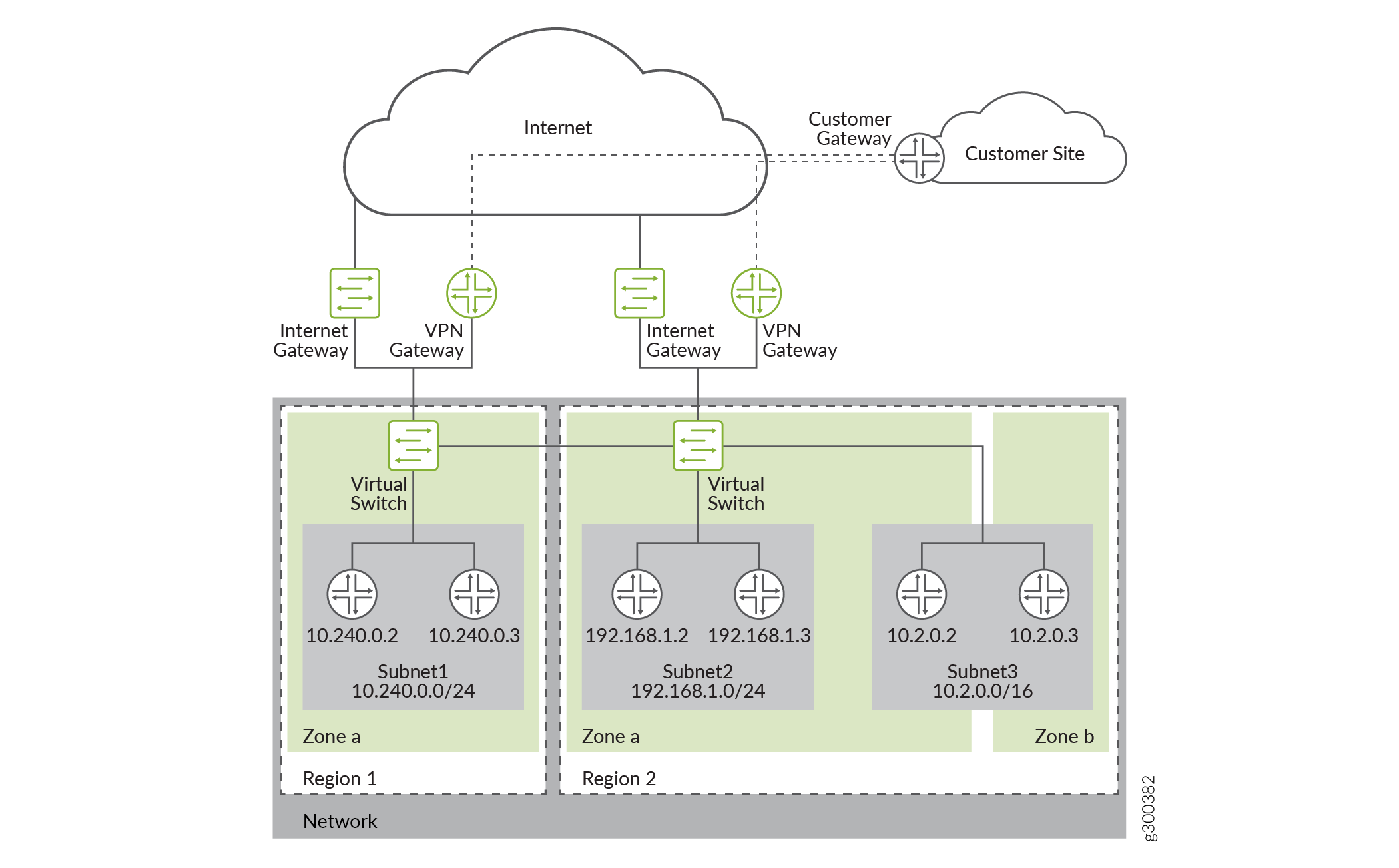
The vSRX Virtual Firewall instance is launched with multiple virtual interfaces in VPC subnets. The first interface (fxp0) will be the management interface. It is connected to the Internet gateway for public access. You can use SSH to access the interface and manage the virtual device with Junos CLI, just as you can with SRX Series Firewalls. The subsequent interfaces are revenue ports. They are managed by the flowd process running on Linux and handle all the traffic. On GCP, a maximum of 8 network interfaces are allowed per vSRX Virtual Firewall instance.
Some of the initial provisioning parameters for first boot are host name, root password, SSH public key, management interface (fxp0) IP address, and default gateway IP address.
Starting in Junos OS Release 19.2R1, vSRX Virtual Firewall instances with 2 vCPUs, 4-GB memory, and 19-GB disk space are supported on GCP.
Manage Access to Instances
To create and manage instances, you can use a variety of tools, including the Google Cloud Platform Console, the gcloud command-line tool, and the REST API. To configure applications on your instances, connect to the instance using SSH for Linux instances.
You can manage access to your instances using one of the following methods:
Linux instance:
Manage instance access using OS login, which allows you to associate SSH keys with your Google account or G Suite account and manage administrator or non-administrator access to instances through identity and access management (IAM) roles. If you connect to your instances using the gcloud command-line tool or SSH from the console, Compute Engine can automatically generate SSH keys for you and apply them to your Google account or G Suite account.
Manage your SSH keys in project or instance metadata, which grants administrator access to instances with metadata access that do not use OS Login. If you connect to your instances using the gcloud command-line tool or SSH from the console, Compute Engine can automatically generate SSH keys for you and apply them to project metadata.
Windows Server instances—Create a password for a Windows Server instance.
Access Instances
After you configure access to your instances, you can connect to your instances using one of several options. For more information about connecting your instances, see Connecting to instances.
