vSRX Virtual Firewall Deployment in Oracle Cloud Infrastructure
The topics in this section help you launch vSRX Virtual Firewall instances in Oracle Cloud Infrastructure.
Overview
This topic provides you an overview and pre-requisites to deploy vSRX Virtual Firewall virtual Firewall in Oracle Cloud Infrastructure. vSRX Virtual Firewall provides security and networking services for virtualized private or public Oracle Cloud environments.
Starting in Junos OS Release 20.4R2, vSRX Virtual Firewall 3.0 is available for OCI deployments.
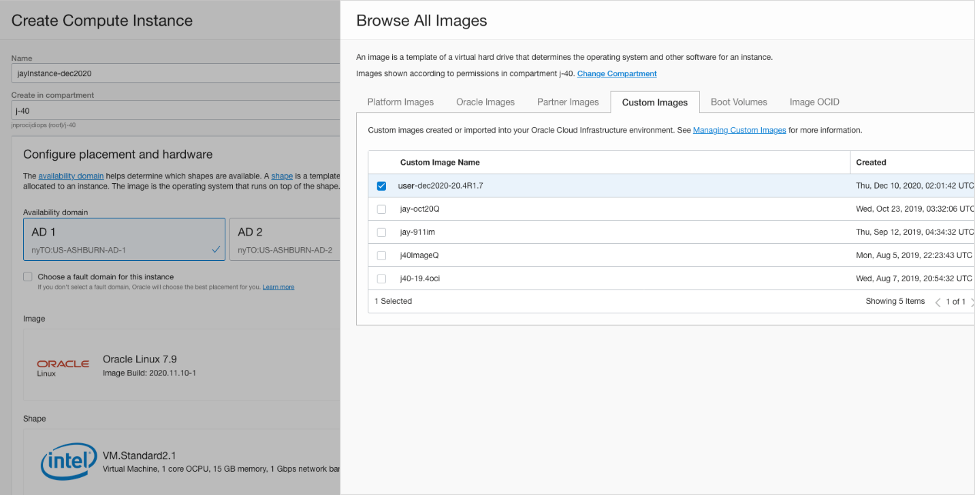
vSRX Virtual Firewall 3.0 image is not available in the OCI Marketplace. You must download the vSRX Virtual Firewall 3.0 software from Juniper Support Downloads and upload into an OCI compartment.
Pre-Requisites
-
Ensure you have proper accounts and permissions before you attempt to deploy the vSRX Virtual Firewall in OCI.
-
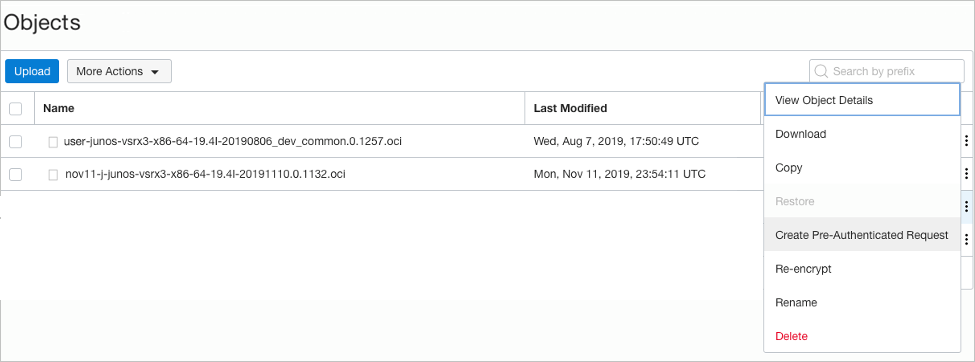
Copy the .oci image to an object storage compartment in your OCI account.
An example file name is junos-vsrx3-x86-64-xxxx.oci. After you purchase the vSRX Virtual Firewall 3.0 software you can downloaded the software from: Juniper Support page.
Note:.oci image extensions are built for the vSRX Virtual Firewall images to be deployed in OCI. This is because on OCI, when the qcow2 images are deployed, the default emulation selected for the vNIC is e-1000. The .oci images of the vSRX Virtual Firewall pass the metadata needed for the emulation type to be set to virtIO upon deployment of the vSRX Virtual Firewall which ensure a better throughput.
-
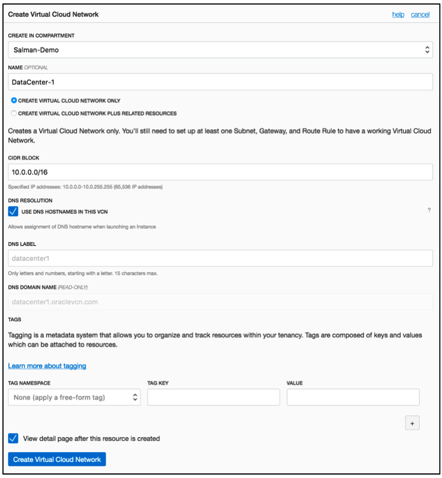
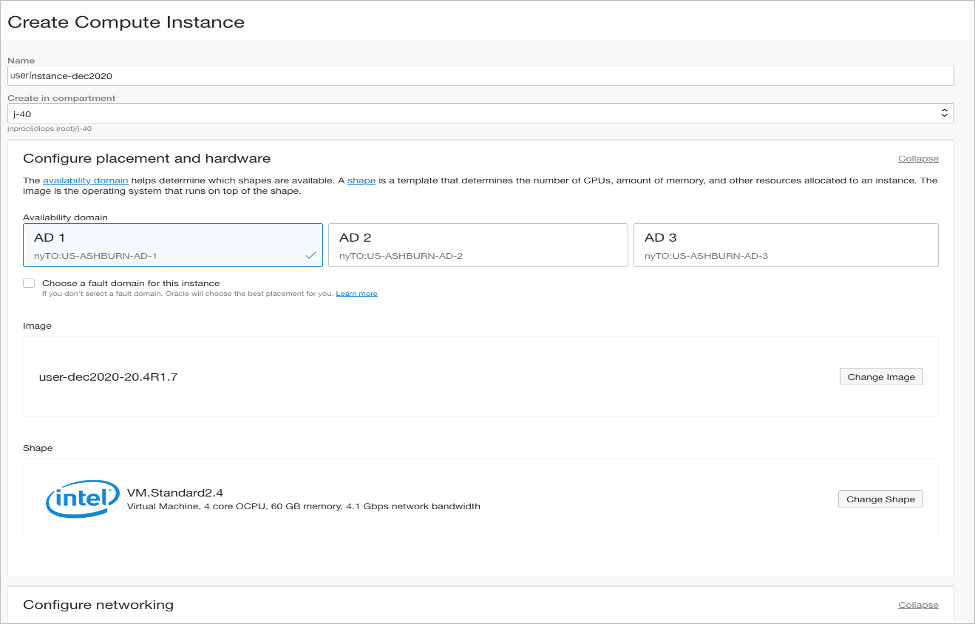
Create Virtual Network subnets for your deployment.
For better understanding of Oracle terminologies and their use in vSRX Virtual Firewall 3.0 deployments, see Understanding vSRX Virtual Firewall Deployment in Oracle Cloud Infrastructure.
Example Topology
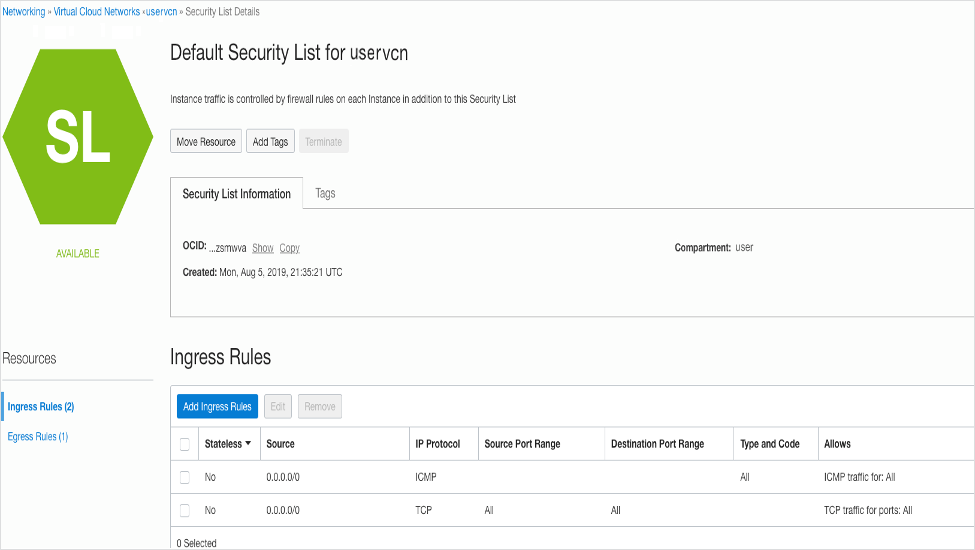
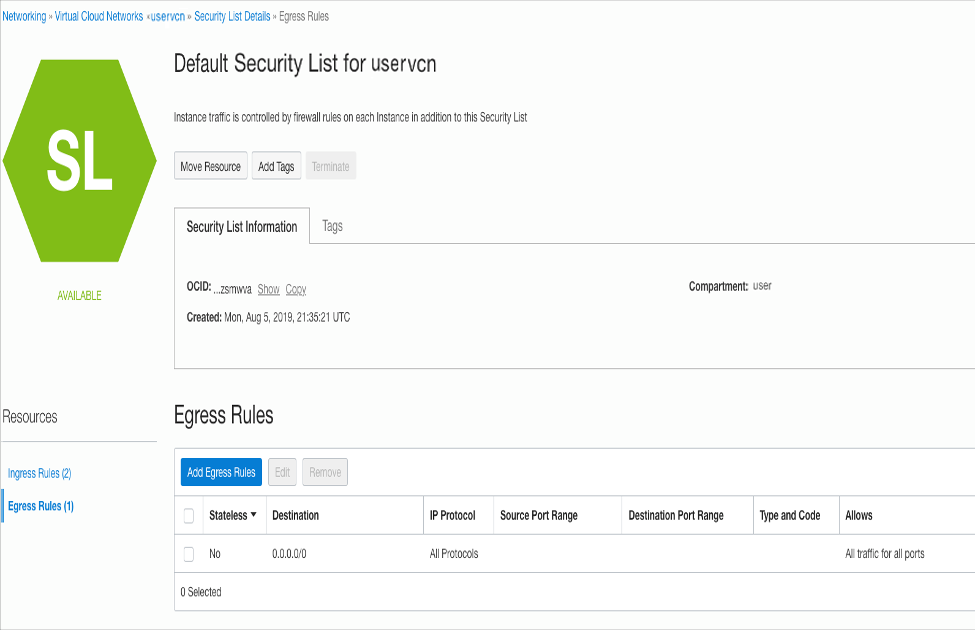
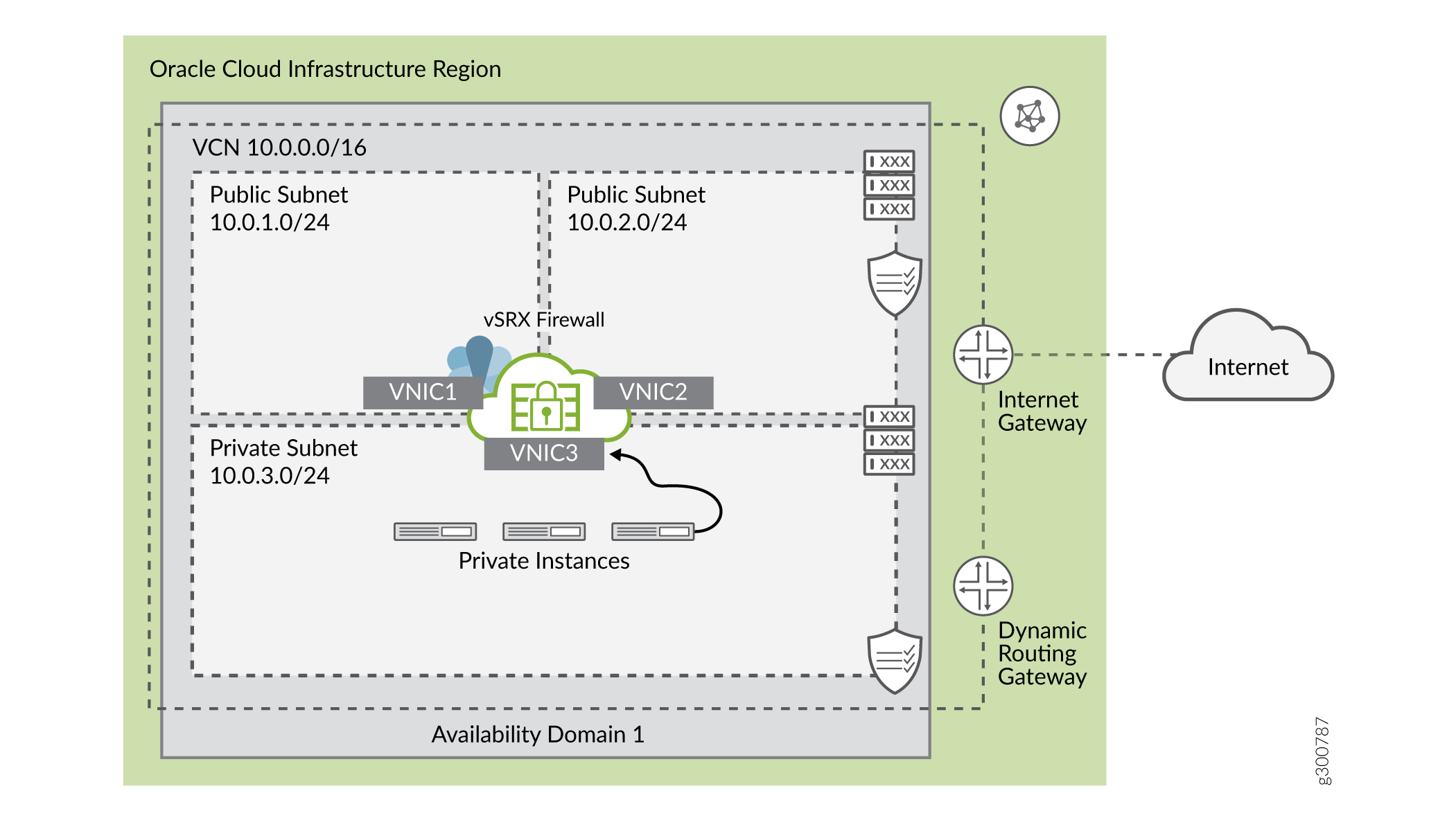
A common cloud configuration includes hosts that you want to grant access to the Internet, but you do not want anyone from outside your cloud to get access to your hosts. You can use vSRX Virtual Firewall in the OCI to NAT traffic inside the OCI from the public Internet.
The diagram shows an example VCN with three subnets:
-
Public (10.0.1.0/24), for management interfaces with access to the internet through an internet gateway
-
Public (10.0.2.0/24), for revenue (data) interfaces with access to the internet through an internet gateway
-
Private (10.0.3.0/24), a private subnet with no access to the internet
The following topology is used as an example for this deployment.
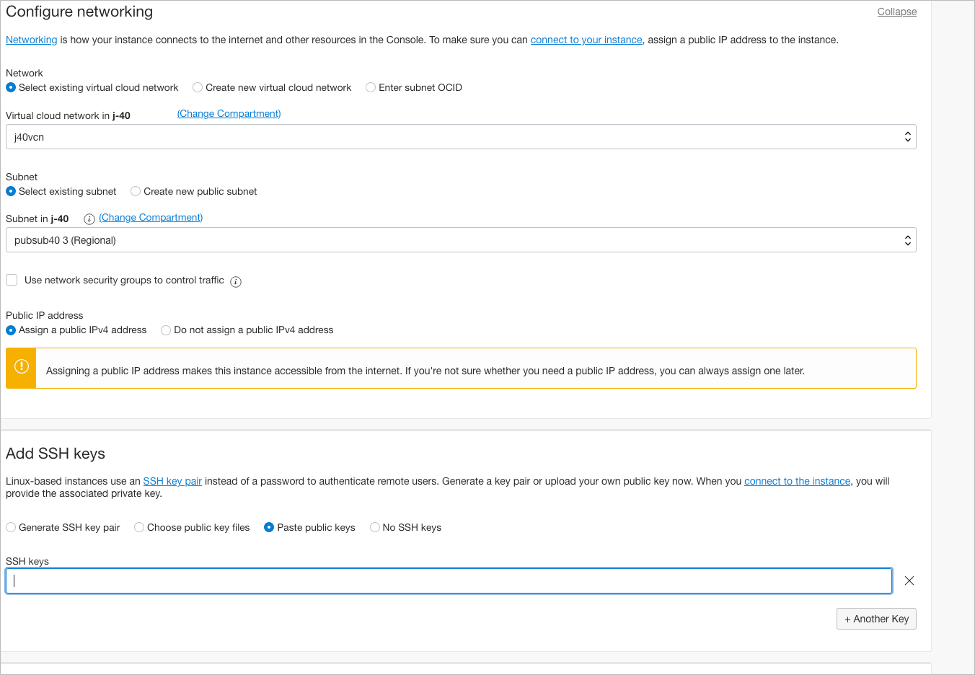
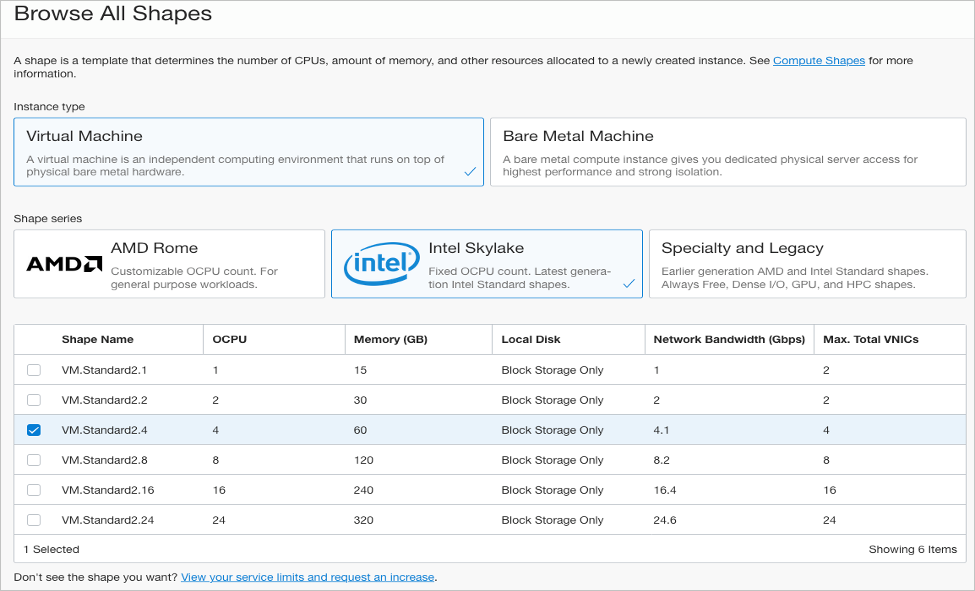
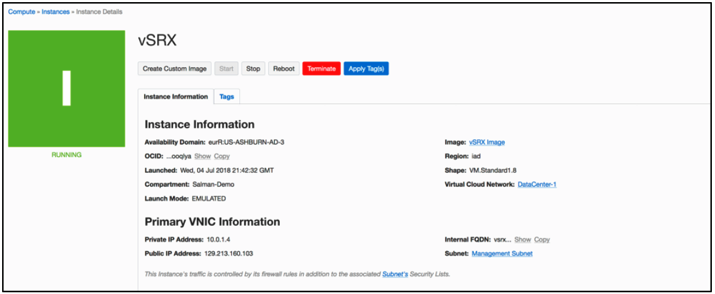
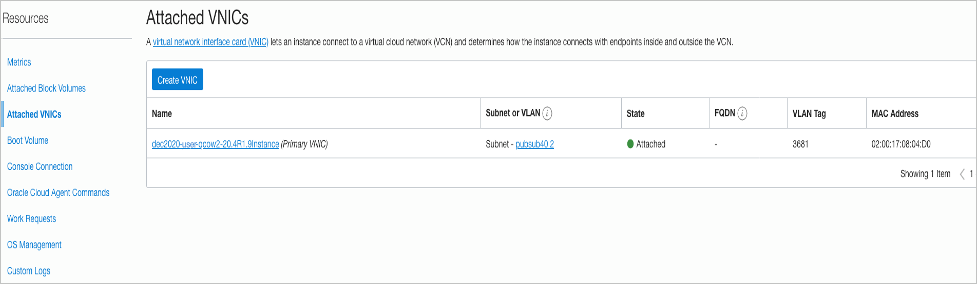
Launch vSRX Virtual Firewall Instances in the OCI
This topic provides details on how you can launch vSRX Virtual Firewall instances in the OCI.