AWS Gateway Load Balancing with Geneve
Overview of AWS Gateway Load Balancer
Amazon Web Services (AWS) Gateway Load Balancer (GWLB) is a networking service with various features that help you deploy third-party appliances. GWLB gives you a single gateway for distributing traffic across multiple virtual appliances. You can scale the virtual appliances up or down according to demand. These capabilities decrease potential points of failure in your network and increase availability.You can deploy vSRX Virtual Firewall 3.0 with the AWS Gateway Load Balancer (GWLB) service that uses the Geneve protocol encapsulation for transparent load balancing and packet routing.
Using AWS GWLB, we can offer a number of managed services using vSRX Virtual Firewall 3.0 to AWS without having to separately solve for the availability, load balancing and cloud scaling for various solutions.
Starting in Junos OS Release 23.2R1, you can integrate vSRX Virtual Firewall 3.0 with AWS GWLB (with Geneve protocol support). vSRX Virtual Firewall 3.0 can decode and encode the AWS GWLB metadata and allows performing interoperability testing to identify the healthiest vSRX Virtual Firewall 3.0 in the AWS environment.
The traffic flow in AWS environment or solutions with Geneve flow support on vSRX Virtual Firewall 3.0 is as folows:
When traffic source is sending traffic to its destination and GWLB is deployed (using routing techniques), the GWLB operates as a Layer 3 (L3) gateway. The L3 characteristics of GWLB is, it can be a next hop in a route table with packet in packet out service and does not reroute a packet. .

GWLB acts as a Layer 4 (L4) load balancer for the received traffic, enabling you to easily deploy, scale, and manage vSRX Virtual Firewall 3.0. Additionally, GWLB provides stickiness of flows in both the directions. This feature enables vSRX Virtual Firewall 3.0 to see and act on the traffic in both the directions.
GWLB can perform periodic health check on vSRX Virtual Firewall 3.0 to check whether any vSRX Virtual Firewall instance is down. If any vSRX Virtual Firewall instance is down, GWLB can reroute the flows by encapsulating the original traffic in a L3 header.
vSRX Virtual Firewall 3.0 receives the original traffic in a L3 encapsulation through the Geneve protocol. The L3 packet is received by vSRX Virtual Firewall 3.0 without any change in source IP or port numbers. vSRX Virtual Firewall 3.0 then:
-
De-encapsulates the traffic.
-
Looks at and inspects the traffic.
-
Sends the traffic to its destination.
Benefits of AWS Gateway Load Balancer Service
- Improved virtual appliance availability—To ensure your virtual appliances
are available and healthy, Gateway Load Balancer runs health checks to
identify unhealthy virtual appliances.
When it detects an unhealthy virtual appliance, Gateway Load Balancer reroutes traffic away from that instance to a healthy one, so you experience graceful failover during both planned and unplanned down time.
-
Scale virtual appliances—Gateway Load Balancer automatically scales your virtual appliances up or down, based on demand.
-
Cost effective—With virtual appliances available with bring-your-own-license (BYOL) or pay-as-you-go pricing, you have the option to only pay for what you use, and reduce the cost by over provisioning.
-
Health check mechanisms—Provides better health check mechanisms that use TCP, HTTP, or HTTP. If in case there is an instance failure, these mechanisms helps you identify the healthiest vSRX Virtual Firewall 3.0 instance and you can then reroute new flows.
-
Enables transparent insertion of services—because the traffic is passing from GWLB to the appliances in a L3 encapsulation, the source and destination don’t have to change any software. The appliances simply send the traffic as if there was no node in between.
See Also
AWS GWLB with Geneve vSRX Virtual Firewall 3.0 Deployment
Overview
You can deploy vSRX Virtual Firewall 3.0 with AWS GWLB and Geneve flow support in two modes:
-
vSRX Virtual Firewall acts as a tunnel endpoint—In this deployment mode, the virtual tunnel endpoint client (vtepc) (Geneve tunnel endpoint) must ensure that packets destined to both the client and the server pass through virtual tunnel endpoint server (vteps) (vSRX Virtual Firewall 3.0). The source port is selected by the virtual tunnel endpoint (vtep).
Figure 2: vSRX Virtual Firewall 3.0 as Tunnel Endpoint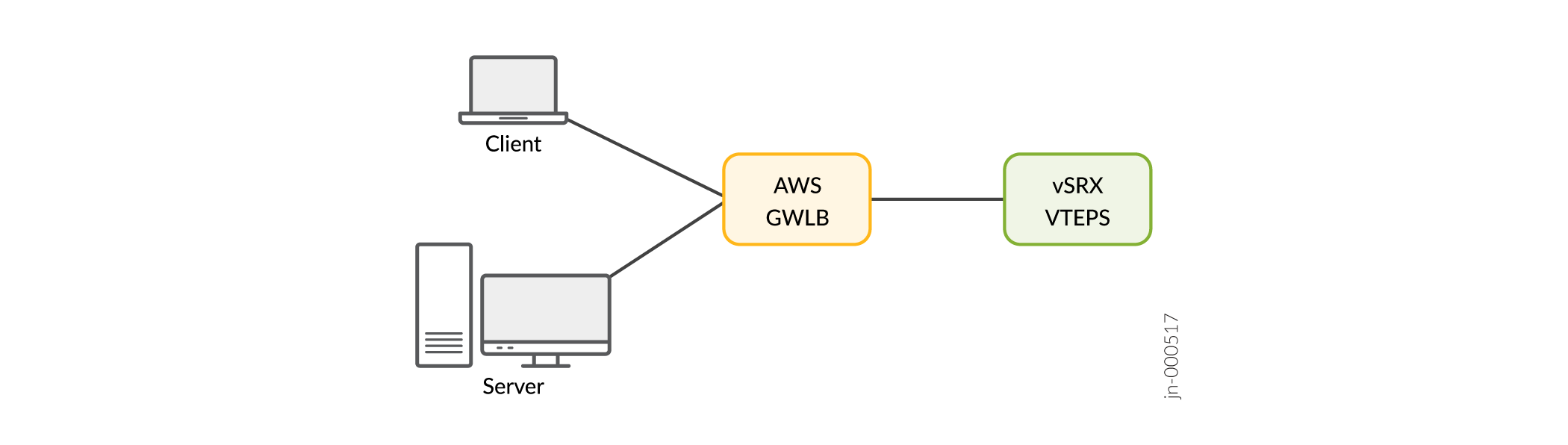
-
vSRX Virtual Firewall 3.0 as a transit router between Geneve tunnel endpoints.
Figure 3: vSRX Virtual Firewall 3.0 as Transit Router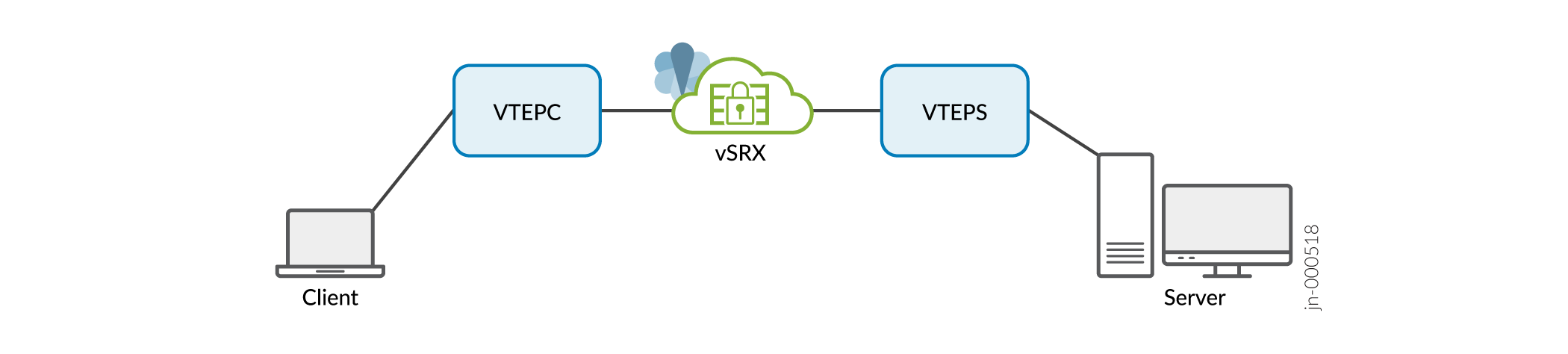
Deploy vSRX Virtual Firewall 3.0 as Tunnel Endpoint
With vSRX Virtual Firewall 3.0 as a tunnel endpoint for the traffic that is received by the GWLB in the security VPC supports encoding and decoding Geneve-related type-length-value (TLV) pairs and responds to the health check for the GWLB. This is a deployment scenario where you can launch vSRX Virtual Firewall in a security VPC with GWLB (AWS Gateway load balancer) and use the same deployment steps to launch vSRX Virtual Firewall based on your needs. The vSRX Virtual Firewall that is deployed in the security VPC must support the Geneve decapsulation, parsing header, encapsulate post inspection and forward the packet back to the AWS GWLB.
