ON THIS PAGE
Configuring Mirroring on EX9200 Switches to Analyze Traffic (CLI Procedure)
Configuring Mirroring on EX4300 Switches to Analyze Traffic (CLI Procedure)
Configuring Port Mirroring to Analyze Traffic (CLI Procedure)
Verifying Input and Output for Port Mirroring Analyzers on EX Series Switches
Example: Configuring Port Mirroring Analyzers for Local Monitoring of Employee Resource Use
Example: Configuring Port Mirroring for Remote Monitoring of Employee Resource Use
Example: Configuring Mirroring for Local Monitoring of Employee Resource Use on EX4300 Switches
Example: Configuring Mirroring for Remote Monitoring of Employee Resource Use on EX4300 Switches
Configuring Port Mirroring and Analyzers
Understanding Port Mirroring Analyzers
Port mirroring can be used for traffic analysis on routers and switches that, unlike hubs, do not broadcast packets to every port on the destination device. Port mirroring sends copies of all packets or policy-based sample packets to local or remote analyzers where you can monitor and analyze the data.
In the context of port mirroring analyzers, we use the term switching device. The term indicates that the device (including routers) is performing a switching function.
You can use analyzers on a packet level to help you:
-
Monitor network traffic
-
Enforce network usage policies
-
Enforce file sharing policies
-
Identify the causes of problems
-
Identify stations or applications with heavy or abnormal bandwidth usage
You can configure port mirroring to mirror:
-
Bridged packets (Layer 2 packets)
-
Routed packets (Layer 3 packets)
Mirrored packets can be copied to either a local interface for local monitoring or a VLAN or bridge domain for remote monitoring.
The following packets can be copied:
-
Packets entering or exiting a port—You can mirror packets entering or exiting ports, in any combination, for up to 256 ports. For example, you can send copies of the packets entering some ports and the packets exiting other ports to the same local analyzer port or analyzer VLAN.
-
Packets entering or exiting a VLAN or bridge domain—You can mirror the packets entering or exiting a VLAN or bridge domain to either a local analyzer port or to an analyzer VLAN or bridge domain. You can configure multiple VLANs (up to 256 VLANs) or bridge domains as ingress inputs to an analyzer, including a VLAN range and private VLANs (PVLANs).
-
Policy-based sample packets—You can mirror a policy-based sample of packets that are entering a port, VLAN, or bridge domain. You configure a firewall filter with a policy to select the packets to be mirrored. You can send the sample to a port-mirroring instance or to an analyzer VLAN or bridge domain.
- Analyzer Overview
- Statistical Analyzer Overview
- Default Analyzer Overview
- Port Mirroring at a Group of Ports Bound to Multiple Statistical Analyzers
- Port Mirroring Analyzer Terminology
- Configuration Guidelines for Port Mirroring Analyzers
Analyzer Overview
You can configure an analyzer to define both the input traffic
and the output traffic in the same analyzer configuration. The input
traffic to be analyzed can be either traffic that enters or traffic
that exits an interface or VLAN. The
analyzer configuration enables you to send this traffic to an output
interface, instance, next-hop group, VLAN, or bridge domain. You can
configure an analyzer at the [edit forwarding-options
analyzer] hierarchy level.
Statistical Analyzer Overview
You can define a set of mirroring properties, such as mirroring rate and maximum packet length for traffic, that you can explicitly bind to physical ports on the router or switch. This set of mirroring properties constitutes a statistical analyzer (also called a non-default analyzer). At this level, you can bind a named instance to the physical ports associated with a specific FPC.
Default Analyzer Overview
You can configure an analyzer without configuring any mirroring properties (such as mirroring rate or maximum packet length). By default, the mirroring rate is set to 1 and the maximum packet length is set to the complete length of the packet. These properties are applied at the global level and need not be bound to a specific FPC.
Port Mirroring at a Group of Ports Bound to Multiple Statistical Analyzers
You can apply up to two statistical analyzers to the same port groups on the switching device. By applying two different statistical analyzer instances to the same FPC or Packet Forwarding Engine, you can bind two distinct Layer 2 mirroring specifications to a single port group. Mirroring properties that are bound to an FPC override any analyzer (default analyzer) properties bound at the global level on the switching device. Default analyzer properties are overridden by binding a second analyzer instance on the same port group.
Port Mirroring Analyzer Terminology
Table 1 lists some port mirroring analyzer terms and their descriptions.
| Term | Description |
|---|---|
Analyzer |
In a mirroring configuration, the analyzer includes:
|
Analyzer output interface (Also known as a monitor port) |
Interface where mirrored traffic is sent and a protocol analyzer is connected. Interfaces used as output to an analyzer must be configured
under the Analyzer output interfaces have the following limitations:
|
Analyzer VLAN or bridge domain (Also known as a monitor VLAN or bridge domain) |
VLAN or bridge domain to where mirrored traffic is sent to be used by a protocol analyzer. The member interfaces in the monitor VLAN or bridge domain are spread across the switching devices in your network. |
Bridge-domain-based analyzer |
An analyzer session configured to use bridge domains for input, output or both. |
Default analyzer |
An analyzer with default mirroring parameters. By default, the mirroring rate is 1 and the maximum packet length is the length of the complete packet. |
Input interface (Also known as mirrored ports or monitored interfaces) |
An interface on the switching device where the traffic entering or exiting this interface is mirrored. |
LAG-based analyzer |
An analyzer that has a link aggregation group (LAG) specified as the input (ingress) interface in the analyzer configuration. |
Local mirroring |
An analyzer configuration in which packets are mirrored to a local analyzer port. |
Monitoring station |
A computer running a protocol analyzer. |
Analyzer based on next-hop group |
An analyzer configuration that uses the next-hop group as the output to an analyzer. |
Port-based analyzer |
An analyzer configuration that defines interfaces for input and output. |
Protocol analyzer application |
An application used to examine packets transmitted across a network segment. Also commonly called a network analyzer, packet sniffer or probe. |
Remote mirroring |
Functions the same way as local mirroring, except that the mirrored traffic is not copied to a local analyzer port but is flooded to an analyzer VLAN or bridge domain that you create specifically for the purpose of receiving mirrored traffic. Mirrored packets have an additional outer tag of the analyzer VLAN or bridge domain. |
Statistical analyzer (Also known as a non-default analyzer) |
A set of mirroring properties that you can explicitly bind to the physical ports on the switch. This set of analyzer properties is known as a statistical analyzer. |
VLAN-based analyzer |
An analyzer configuration that uses VLANs to deliver the mirrored traffic to the analyzer. |
Configuration Guidelines for Port Mirroring Analyzers
When you configure port mirroring analyzers. we recommend that you follow these
guidelines to ensure optimum benefit. We recommend that you disable mirroring when
you are not using it, and that you select specific interfaces as input to the
analyzer rather than using the all keyword option, which enables
mirroring on all interfaces. Mirroring only necessary packets reduces any potential
performance impact.
You can also limit the amount of mirrored traffic by:
-
Using statistical sampling
-
Using a firewall filter
-
Setting a ratio to select a statistical sample
With local mirroring, traffic from multiple ports is replicated to the analyzer output interface. If the output interface for an analyzer reaches capacity, packets are dropped. You must consider whether the traffic being mirrored exceeds the capacity of the analyzer output interface.
Table 2 summarizes further configuration guidelines for analyzers.
|
Guideline |
Value or Support Information |
Comment |
|---|---|---|
|
Number of analyzers that you can enable concurrently. |
64 Default analyzers 2 per FPC–Statistical analyzer |
Statistical analyzers must be bound to an FPC for mirroring traffic on ports belonging to that FPC. Note:
Default analyzer properties are implicitly bound on the last (or second to last) instance on all FPCs in the system. Therefore, when you explicitly bind a second statistical analyzer on the FPC, the default analyzer properties are overridden. |
|
Number of interfaces, VLANs, or bridge domains that you can use as ingress input to an analyzer. |
256 |
– |
|
Types of ports on which you cannot mirror traffic. |
|
|
|
Protocol families that you can include in an analyzer. |
|
An analyzer mirrors only bridged traffic. To mirror routed
traffic, use the port mirroring configuration with
|
|
Packets with physical layer errors are not sent to the local or remote analyzer. |
Applicable |
Packets with these errors are filtered out and thus are not sent to the analyzer. |
|
Analyzer does not support line-rate traffic. |
Applicable |
Mirroring for line-rate traffic is done on a best-effort basis. |
|
Analyzer output on a LAG interface. |
Supported |
|
|
Analyzer output interface mode as trunk mode. |
Supported |
|
|
Egress mirroring of host-generated control packets. |
Not supported |
|
|
Configuring Layer 3 logical interfaces in the
|
Not supported |
|
|
The analyzer input and output stanzas containing members of the same VLAN or the VLAN itself must be avoided. |
Applicable |
|
|
Support for VLAN and its member interfaces in different analyzer sessions |
Not supported |
If mirroring is configured, either of the analyzers is active. |
|
Egress mirroring of aggregated Ethernet (ae) interfaces and its child logical interfaces configured for different analyzers. |
Not supported |
|
Configuring Mirroring on EX9200 Switches to Analyze Traffic (CLI Procedure)
EX9200 switches enable you to configure mirroring to send copies of packets to either a local interface for local monitoring or to a VLAN for remote monitoring. You can use mirroring to copy the following packets:
Packets entering or exiting a port
Packets entering or exiting a VLAN
Mirror only necessary packets to reduce potential performance impact. We recommend that you:
Disable the analyzers that you have configured when you are not using them.
Specify individual interfaces as input to analyzers rather than specifying all interfaces as input.
Limit the amount of mirrored traffic by:
Using statistical sampling.
Setting ratios to select statistical samples.
Using firewall filters.
If you want to create additional analyzers without deleting
the existing analyzers, disable the existing analyzers by using the disable analyzer analyzer-name statement
from the command-line-interface (CLI) or from the J-Web configuration
page for mirroring.
Interfaces used as output to an analyzer must be configured
under the ethernet-switching family, and must be associated
to a VLAN.
- Configuring an Analyzer for Local Traffic Analysis
- Configuring an Analyzer for Remote Traffic Analysis
- Configuring a Statistical Analyzer for Local Traffic Analysis
- Configuring a Statistical Analyzer for Remote Traffic Analysis
- Binding Statistical Analyzers to Ports Grouped at the FPC Level
- Configuring an Analyzer with Multiple Destinations by Using Next-Hop Groups
- Defining a Next-Hop Group for Layer 2 Mirroring
Configuring an Analyzer for Local Traffic Analysis
To mirror network traffic or VLAN traffic on the switch to an interface on the switch by using analyzers:
Configuring an Analyzer for Remote Traffic Analysis
To mirror traffic that is traversing interfaces or a VLAN on the switch to a VLAN used for analysis from a remote location:
Configuring a Statistical Analyzer for Local Traffic Analysis
To mirror interface traffic or VLAN traffic on the switch to an interface on the switch by using a statistical analyzer:
Configuring a Statistical Analyzer for Remote Traffic Analysis
To mirror traffic that is traversing interfaces or a VLAN on the switch to a VLAN for analysis from a remote location by using a statistical analyzer:
Binding Statistical Analyzers to Ports Grouped at the FPC Level
You can bind a statistical analyzer to a specific FPC in the switch, that is, you can bind the statistical analyzer instance at the FPC level of the switch. The mirroring properties specified in the statistical analyzer are applied to all physical ports associated with all Packet Forwarding Engines on the specified FPC.
To bind a named instance of Layer 2 analyzer to an FPC:
Enable configuration of switch chassis properties:
[edit] user@switch# edit chassis
Enable configuration of an FPC (and its installed PICs):
[edit chassis] user@switch# edit fpc slot-number
Bind a statistical analyzer instance to the FPC:
[edit chassis fpc slot-number] user@switch# set port-mirror-instance stats_analyzer-1
(Optional) To bind a second statistical analyzer instance of Layer 2 mirroring to the same FPC, repeat Step 3 and specify a different statistical analyzer name:
[edit chassis fpc slot-number] user@switch# set port-mirror-instance stats_analyzer-2
Verify the minimum configuration of the binding:
[edit chassis fpc slot-number port-mirror-instance analyzer_name] user@switch# top [edit] user@switch# show chassis chassis { fpc slot-number { # Bind two statistical analyzers or port mirroring named instances at the FPC level. port-mirror-instance stats_analyzer-1; port-mirror-instance stats_analyzer-2; } }
On binding a second instance (stats_analyzer-2 in this example), the mirroring properties of this session, if configured,
overrides any default analyzer.
Configuring an Analyzer with Multiple Destinations by Using Next-Hop Groups
You can mirror traffic to multiple destinations by configuring next-hop groups as analyzer output. The mirroring of packets to multiple destinations is also known as multipacket port mirroring.
To mirror interface traffic or VLAN traffic on the switch to an interface on the switch (by using analyzers):
Defining a Next-Hop Group for Layer 2 Mirroring
The next-hop group configuration at the [edit forwarding-options] configuration level enables you to define a next-hop group name,
the type of addresses to be used in the next-hop group, and the logical
interfaces that form the multiple destinations to which traffic can
be mirrored. By default, the next-hop group is specified using Layer
3 addresses using the [edit forwarding-options next-hop-group next-hop-group-name group-type inet] statement.
To specify a next-hop group using Layer 2 addresses instead, include
the [edit forwarding-options next-hop-group next-hop-group-name group-type layer-2] statement.
To define a next-hop group for Layer 2 mirroring:
Configuring Mirroring on EX4300 Switches to Analyze Traffic (CLI Procedure)
This task uses Junos OS for EX Series switches with support for the Enhanced Layer 2 Software (ELS) configuration style.
EX4300 switches enable you to configure mirroring to send copies of packets to either a local interface for local monitoring or to a VLAN for remote monitoring. You can use mirroring to copy these packets:
Packets entering or exiting a port
Packets entering a VLAN
Mirror only necessary packets to reduce potential performance impact. We recommend that you:
Disable your configured mirroring configurations when you are not using them.
Specify individual interfaces as input to analyzers rather than specifying all interfaces as input.
Limit the amount of mirrored traffic by using firewall filters.
If you want to create additional analyzers without deleting
the existing analyzers, then disable the existing analyzers by using
the disable analyzer analyzer-name statement from the command-line interface or the J-Web configuration
page for mirroring.
Interfaces used as output for an analyzer must be configured
under the ethernet-switching family.
- Configuring an Analyzer for Local Traffic Analysis
- Configuring an Analyzer for Remote Traffic Analysis
- Configuring Port Mirroring
Configuring an Analyzer for Local Traffic Analysis
To mirror interface traffic or VLAN traffic on the switch to an interface on the switch (by using analyzers):
Configuring an Analyzer for Remote Traffic Analysis
To mirror traffic that is traversing interfaces or a VLAN on the switch to a VLAN for analysis from a remote location (by using analyzers):
Configuring Port Mirroring
To filter packets to be mirrored to a port-mirroring instance, create the instance and then use it as the action in the firewall filter. You can use firewall filters in both local and remote mirroring configurations.
If the same port-mirroring instance is used in multiple filters or terms, the packets are copied to the analyzer output port or analyzer VLAN only once.
To filter mirrored traffic, create a port-mirroring instance
under the [edit forwarding-options] hierarchy level, and
then create a firewall filter. The filter can use any of the available
match conditions and must have port-mirror-instance instance-name as an action. This action in the firewall
filter configuration provides the input to the port-mirroring instance.
To configure a port-mirroring instance with firewall filters:
Configuring Port Mirroring to Analyze Traffic (CLI Procedure)
This configuration task uses Junos OS for EX Series switches that do not support the Enhanced Layer 2 Software (ELS) configuration style.
EX Series switches allow you to configure port mirroring to send copies of packets to either a local interface for local monitoring or to a VLAN for remote monitoring. You can use port mirroring to copy these packets:
Packets entering or exiting a port
Packets entering a VLAN on EX2200, EX3200, EX3300, EX4200, EX4500, or EX6200 switches
Packets exiting a VLAN on EX8200 switches
Mirror only necessary packets to reduce potential performance impact. We recommend that you:
Disable your configured port mirroring analyzers when you are not using them.
Specify individual interfaces as input to analyzers rather than specifying all interfaces as input.
Limit the amount of mirrored traffic by:
Using statistical sampling.
Setting ratios to select statistical samples.
Using firewall filters.
Before you begin to configure port mirroring, note the following limitations for analyzer output interfaces:
Cannot also be a source port.
Cannot be used for switching.
Do not participate in Layer 2 protocols (such as RSTP) when part of a port mirroring configuration.
Do not retain any VLAN associations they held before they were configured as analyzer output interfaces.
If you want to create additional analyzers without deleting
the existing analyzer, first disable the existing analyzer using the disable analyzer analyzer-name command
or the J-Web configuration page for port mirroring.
Interfaces used as output for an analyzer must be configured
as family ethernet-switching.
- Configuring Port Mirroring for Local Traffic Analysis
- Configuring Port Mirroring for Remote Traffic Analysis
- Filtering the Traffic Entering an Analyzer
Configuring Port Mirroring for Local Traffic Analysis
To mirror interface traffic or VLAN traffic on the switch to another interface on the switch:
Configuring Port Mirroring for Remote Traffic Analysis
To mirror traffic that is traversing interfaces or a VLAN on the switch to a VLAN for analysis from a remote location:
Filtering the Traffic Entering an Analyzer
To filter which packets are mirrored to an analyzer, create the analyzer and then use it as the action in the firewall filter. You can use firewall filters in both local and remote port mirroring configurations.
If the same analyzer is used in multiple filters or terms, the packets are copied to the analyzer output port or analyzer VLAN only once.
To filter mirrored traffic, create an analyzer and then create
a firewall filter. The filter can use any of the available match conditions
and must have an action of analyzer. The action of the
firewall filter provides the input to the analyzer.
To configure port mirroring with filters:
Verifying Input and Output for Port Mirroring Analyzers on EX Series Switches
Purpose
This verification task uses Junos OS for EX Series switches that do not support the Enhanced Layer 2 Software (ELS) configuration style.
Verify that an analyzer has been created on the switch and has the appropriate mirror input interfaces, and the appropriate analyzer output interface.
Action
You can verify the port mirror analyzer is configured
as expected by using the show analyzer command.
[edit] user@switch> show analyzer Analyzer name : employee-monitor Output VLAN : remote-analyzer Mirror ratio : 1 Loss priority : High Ingress monitored interfaces : ge-0/0/0.0 Ingress monitored interfaces : ge-0/0/1.0
You can view all of the port mirror analyzers configured
on the switch, including any that are disabled, by using the show ethernet-switching-options command in configuration mode.
user@switch# show ethernet-switching-options
inactive: analyzer employee-web-monitor {
loss-priority high;
output {
analyzer employee-monitor {
loss-priority high;
input {
ingress {
interface ge-0/0/0.0;
interface ge-0/0/1.0;
}
}
output {
vlan {
remote-analyzer;
}
}
}
Meaning
This output shows that the employee-monitor analyzer
has a ratio of 1 (mirroring every packet, the default), a loss priority
of high (set this option to high whenever the
analyzer output is to a VLAN), is mirroring the traffic entering ge-0/0/0
and ge-0/0/1, and is sending the mirrored traffic to the analyzer
called remote-analyzer.
Example: Configuring Port Mirroring Analyzers for Local Monitoring of Employee Resource Use
Juniper Networks devices allow you to configure port mirroring to send copies of packets to either a local interface for local monitoring, to a VLAN or to a bridge domain for remote monitoring. You can use mirroring to copy these packets:
Packets entering or exiting a port
Packets entering or exiting a VLAN or bridge domain
You can then analyze the mirrored traffic locally or remotely using a protocol analyzer. You can install an analyzer on a local destination interface. If you are sending mirrored traffic to an analyzer VLAN or bridge domain, you can use an analyzer on a remote monitoring station.
This topic describes how to configure local mirroring on a switching device. The examples in this topic describe how to configure a switching device to mirror traffic entering interfaces connected to employee computers to an analyzer output interface on that same device.
Requirements
Use either one of the following hardware and software components:
One EX9200 switch with Junos OS Release 13.2 or later
One MX Series router with Junos OS Release 14.1 or later
Before you configure port mirroring, be sure you have an understanding of mirroring concepts. For information about analyzers, see Understanding Port Mirroring Analyzers. For information about port mirroring, see Understanding Layer 2 Port Mirroring.
Overview and Topology
This topic describes how to mirror all traffic entering ports on the switching device to a destination interface on the same device (local mirroring). In this case, the traffic is entering ports connected to employee computers.
Mirroring all traffic requires significant bandwidth and should only be done during an active investigation.
The interfaces ge-0/0/0 and ge-0/0/1 serve as connections for employee computers.
The interface ge-0/0/10 is reserved for analysis of the mirrored traffic.
Connect a PC running a protocol analyzer to the analyzer output interface.
Multiple ports mirrored to one interface can cause buffer overflow, resulting in mirrored packets being dropped at the output interface.
Figure 1 shows the network topology for this example.
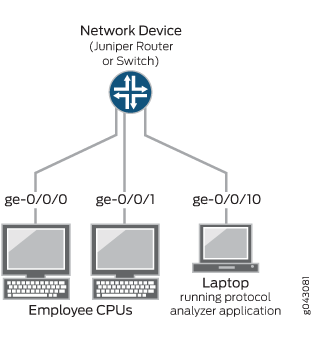
Mirroring All Employee Traffic for Local Analysis
Procedure
CLI Quick Configuration
To quickly configure local mirroring for ingress traffic sent on two ports connected to employee computers, copy either of the following commands for EX Series switches or for MX Series routers and paste them into the switching device terminal window:
EX Series
[edit] set interfaces ge-0/0/0 unit 0 family ethernet-switching set interfaces ge-0/0/1 unit 0 family ethernet-switching set forwarding-options analyzer employee-monitor input ingress interface ge-0/0/0.0 set forwarding-options analyzer employee-monitor input ingress interface ge-0/0/1.0 set forwarding-options analyzer employee-monitor output interface ge-0/0/10.0
MX Series
[edit] set interfaces ge-0/0/0 unit 0 family bridge interface-mode access vlan-id 99 set interfaces ge-0/0/1 unit 0 family bridge interface-mode access vlan-id 98 set forwarding-options analyzer employee-monitor input ingress interface ge-0/0/0.0 set forwarding-options analyzer employee-monitor input ingress interface ge-0/0/1.0 set forwarding-options analyzer employee-monitor output interface ge-0/0/10.0
Step-by-Step Procedure
To configure an analyzer called employee-monitor and specify both the input (source) interfaces and the analyzer
output interface:
Configure each interface to be used in the analyzer configuration. Use the family protocol that is correct for your platform.
EX Series [edit] set interfaces ge-0/0/0 unit 0 family ethernet-switching set interfaces ge-0/0/1 unit 0 family ethernet-switching
To configure
family bridgeon an interface, you must configureinterface-mode accessorinterface-mode trunkas well. You also must configurevlan-id.MX Series [edit] set interfaces ge-0/0/0 unit 0 family bridge interface-mode access vlan-id 99 set interfaces ge-0/0/1 unit 0 family bridge interface-mode access vlan-id 98
Configure each interface connected to employee computers as an output analyzer interface
employee-monitor.[edit forwarding-options] set analyzer employee-monitor input ingress interface ge-0/0/0.0 set analyzer employee-monitor input ingress interface ge-0/0/1.0
Configure the output analyzer interface for the
employee-monitoranalyzer.This will be the destination interface for the mirrored packets.
[edit forwarding-options] set analyzer employee-monitor output interface ge-0/0/10.0
Results
Check the results of the configuration.
[edit]
user@device# show forwarding-options
analyzer {
employee-monitor {
input {
ingress {
interface ge-0/0/0.0;
interface ge-0/0/1.0;
}
}
output {
interface ge-0/0/10.0;
}
}
}
Verification
Verifying That the Analyzer Has Been Correctly Created
Purpose
Verify that the analyzer employee-monitor has been created on the switching device with the appropriate input
interfaces and the appropriate output interface.
Action
Use the show forwarding-options analyzer operational
command to verify that an analyzer is configured as expected.
user@device> show forwarding-options analyzer Analyzer name : employee-monitor Mirror rate : 1 Maximum packet length : 0 State : up Ingress monitored interfaces : ge-0/0/0.0 Output interface : ge-0/0/10.0
Meaning
The output shows that the employee-monitor analyzer has a ratio of 1 (that is, mirroring every packet, the
default setting), the maximum size of the original packet mirrored
is 0 (indicating that the entire packet is mirrored), the state of
the configuration is up, and the analyzer
is mirroring the traffic entering the ge-0/0/0 interface, and sending
the mirrored traffic to the ge-0/0/10 interface.
If the state of the output interface is down or if the output interface is not configured, the value of State will be down indicating
that the analyzer will not be receiving mirrored traffic.
Example: Configuring Port Mirroring for Remote Monitoring of Employee Resource Use
Juniper Networks devices allow you to configure port mirroring to send copies of packets to either a local interface for local monitoring or to a VLAN or bridge domain for remote monitoring. You can use mirroring to copy these packets:
-
Packets entering or exiting a port
-
Packets entering or exiting a VLAN
-
Packets entering or exiting a bridge domain
If you are sending mirrored traffic to an analyzer VLAN or bridge domain, you can analyze the mirrored traffic by using a protocol analyzer running on a remote monitoring station.
Mirror only necessary packets to reduce potential performance impact. We recommend that you do the following:
-
Disable your configured mirroring sessions when you are not using them.
-
Specify individual interfaces as input to analyzers rather than specifying all interfaces as input.
-
Limit the amount of mirrored traffic by:
-
Using statistical sampling.
-
Setting ratios to select statistical samples.
-
Using firewall filters.
-
The examples in this topic describe how to configure remote port mirroring to analyze employee resource usage.
- Requirements
- Overview and Topology
- Mirroring Employee Traffic for Remote Analysis By Using a Statistical Analyzer
- Verification
Requirements
This example uses one of the following pairs of hardware and software components:
-
One EX9200 switch connected to another EX9200 switch, both running Junos OS Release 13.2 or later
-
One MX Series router connected to another MX Series router, both running Junos OS Release 14.1 or later
Before you configure remote mirroring, be sure that:
-
You have an understanding of mirroring concepts. For information about analyzers, see Understanding Port Mirroring Analyzers. For information about port mirroring, see Understanding Layer 2 Port Mirroring.
-
The interfaces that the analyzer will use as input interfaces have already been configured on the switching device.
Overview and Topology
This topic describes how to configure port mirroring to a remote analyzer VLAN or bridge domain so that the analysis can be done from a remote monitoring station.
Figure 2 shows the network topology for both the EX Series example and the MX Series example scenarios.
Topology
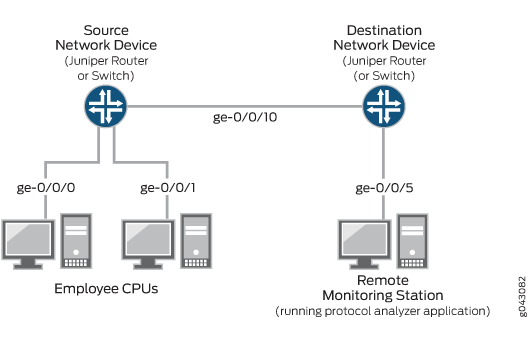
In this example:
-
Interface ge-0/0/0 is a Layer 2 interface, and interface ge-0/0/1 is a Layer 3 interface (both are interfaces on the source device) that serve as connections for employee computers.
-
Interface ge-0/0/10 is a Layer 2 interface that connects the source switching device to the destination switching device.
-
Interface ge-0/0/5 is a Layer 2 interface that connects the destination switching device to the remote monitoring station.
-
The analyzer
remote-analyzeris configured on all switching devices in the topology to carry the mirrored traffic. This topology can use either a VLAN or a bridge domain.
Mirroring Employee Traffic for Remote Analysis By Using a Statistical Analyzer
To configure a statistical analyzer for remote traffic analysis for all incoming and outgoing employee traffic, select one of the following examples:
- Mirroring Employee Traffic for Remote Analysis for EX Series Switches
- Mirroring Employee Traffic for Remote Analysis for MX Series Routers
Mirroring Employee Traffic for Remote Analysis for EX Series Switches
CLI Quick Configuration
To quickly configure a statistical analyzer for remote traffic analysis of the incoming and outgoing employee traffic, copy the following commands for EX Series switches and paste them into the correct switching device terminal window.
-
Copy and paste the following commands in the source switching device terminal window:
EX Series
[edit] set vlans remote-analyzer vlan-id 999 set interfaces ge-0/0/10 unit 0 family ethernet-switching interface-mode access set interfaces ge-0/0/10 unit 0 family ethernet-switching vlan members 999 set forwarding-options analyzer employee-monitor input ingress interface ge-0/0/0.0 set forwarding-options analyzer employee-monitor input ingress interface ge-0/0/1.0 set forwarding-options analyzer employee-monitor input egress interface ge-0/0/0.0 set forwarding-options analyzer employee-monitor input egress interface ge-0/0/1.0 set forwarding-options analyzer employee-monitor output vlan remote-analyzer set forwarding-options analyzer employee-monitor input rate 2 set forwarding-options analyzer employee-monitor input maximum-packet-length 128 set chassis fpc 0 port-mirror-instance employee-monitor
-
Copy and paste the following commands in the destination switching device terminal window:
EX Series
[edit] set vlans remote-analyzer vlan-id 999 set interfaces ge-0/0/10 unit 0 family ethernet-switching interface-mode access set interfaces ge-0/0/10 unit 0 family ethernet-switching vlan members 999 set interfaces ge-0/0/5 unit 0 family ethernet-switching interface-mode access set forwarding-options analyzer employee-monitor input ingress vlan remote-analyzer set forwarding-options analyzer employee-monitor output interface ge-0/0/5.0
Step-by-Step Procedure
To configure basic remote mirroring:
-
On the source switching device, do the following:
-
Configure the VLAN ID for the
remote-analyzerVLAN.[edit] user@device# set vlans remote-analyzer vlan-id 999
-
Configure the interface on the network port connected to the destination switching device for access mode and associate it with the
remote-analyzerVLAN.[edit] user@device# set interfaces ge-0/0/10 unit 0 family ethernet-switching interface-mode access user@device# set interfaces ge-0/0/10 unit 0 family ethernet-switching vlan members 999
-
Configure the statistical analyzer
employee-monitor.[edit forwarding-options] user@device# set analyzer employee-monitor input ingress interface ge-0/0/0.0 user@device# set analyzer employee-monitor input ingress interface ge-0/0/1.0 user@device# set analyzer employee-monitor input egress interface ge-0/0/0.0 user@device# set analyzer employee-monitor input egress interface ge-0/0/1.0 user@device# set analyzer employee-monitor output vlan remote-analyzer user@device# set analyzer employee-monitor input rate 2 user@device# set analyzer employee-monitor input maximum-packet-length 128
-
Bind the statistical analyzer to the FPC that contains the input interface.
[edit] user@device# set chassis fpc 0 port-mirror-instance employee-monitor
-
-
On the destination network device, do the following:
-
Configure the VLAN ID for the
remote-analyzerVLAN.[edit] user@device# set vlans remote-analyzer vlan-id 999
-
Configure the interface on the destination switching device for access mode and associate it with the
remote-analyzerVLAN.[edit interfaces] user@device# set ge-0/0/10 unit 0 family ethernet-switching interface-mode access user@device# set ge-0/0/10 unit 0 family ethernet-switching vlan members 999
-
Configure the interface connected to the destination switching device for access mode.
[edit interfaces] user@device# set ge-0/0/5 unit 0 family ethernet-switching interface-mode access
-
Configure the
employee-monitoranalyzer.[edit forwarding-options] user@device# set analyzer employee-monitor input ingress vlan remote-analyzer user@device# set analyzer employee-monitor output interface ge-0/0/5.0
-
Specify mirroring parameters such as rate and the maximum packet length for the
employee-monitoranalyzer.[edit] user@device# set forwarding-options analyzer employee-monitor input rate 2 user@device# set forwarding-options analyzer employee-monitor input maximum-packet-length 128
-
Bind the
employee-monitoranalyzer to the FPC containing the input ports.[edit] user@device# set chassis fpc 0 port-mirror-instance employee-monitor
-
Results
Check the results of the configuration on the source switching device:
[edit]
user@device# show
forwarding-options {
analyzer employee-monitor {
input {
ingress {
interface ge-0/0/0.0;
interface ge-0/0/1.0;
}
egress {
interface ge-0/0/0.0;
interface ge-0/0/1.0;
}
maximum-packet-length 128;
rate 2;
}
output {
vlan {
remote-analyzer;
}
}
}
}
interfaces {
ge-0/0/10 {
unit 0 {
family ethernet-switching {
interface-mode access;
vlan {
members 999;
}
}
}
}
}
vlans {
remote-analyzer {
vlan-id 999;
}
}
Check the results of the configuration on the destination switching device.
[edit]
user@device# show
interfaces {
ge0/0/5 {
unit 0 {
family ethernet-switching {
interface-mode access;
}
}
}
ge-0/0/10 {
unit 0 {
family ethernet-switching {
interface-mode access;
vlan {
members 999;
}
}
}
}
}
vlans {
remote-analyzer {
vlan-id 999;
interface {
ge-0/0/10.0;
}
}
}
forwarding-options {
analyzer employee-monitor {
input {
ingress {
vlan remote-analyzer;
}
}
output {
interface {
ge-0/0/5.0;
}
}
}
}
Mirroring Employee Traffic for Remote Analysis for MX Series Routers
CLI Quick Configuration
To quickly configure a statistical analyzer for remote traffic analysis of incoming and outgoing employee traffic, copy the following commands for MX Series routers and paste them into the correct switching device terminal window.
-
Copy and paste the following commands in the source switching device terminal window:
MX Series
[edit] set bridge-domains remote-analyzer vlan-id 999 set interfaces ge-0/0/10 unit 0 family bridge interface-mode access set interfaces ge-0/0/10 unit 0 family bridge vlan-id 999 set forwarding-options analyzer employee-monitor input ingress interface ge-0/0/0.0 set forwarding-options analyzer employee-monitor input ingress interface ge-0/0/1.0 set forwarding-options analyzer employee-monitor input egress interface ge-0/0/0.0 set forwarding-options analyzer employee-monitor input egress interface ge-0/0/1.0 set forwarding-options analyzer employee-monitor output bridge-domain remote-analyzer set forwarding-options analyzer employee-monitor input rate 2 set forwarding-options analyzer employee-monitor input maximum-packet-length 128 set chassis fpc 0 port-mirror-instance employee-monitor
-
Copy and paste the following commands in the destination switching device terminal window:
MX Series
[edit] set bridge-domains remote-analyzer vlan-id 999 set interfaces ge-0/0/10 unit 0 family bridge interface-mode access set interfaces ge-0/0/10 unit 0 family bridge vlan-id 999 set interfaces ge-0/0/5 unit 0 family bridge interface-mode access set forwarding-options analyzer employee-monitor input ingress bridge-domain remote-analyzer set forwarding-options analyzer employee-monitor output interface ge-0/0/5.0
Step-by-Step Procedure
To configure basic remote mirroring using MX Series routers:
-
On the source switching device, do the following:
-
Configure the VLAN ID for the
remote-analyzerbridge domain.[edit] user@device# set bridge-domains remote-analyzer vlan-id 999
-
Configure the interface on the network port connected to the destination switching device for access mode and associate it with the
remote-analyzerbridge domain.[edit] user@device# set interfaces ge-0/0/10 unit 0 family bridge interface-mode access user@device# set interfaces ge-0/0/10 unit 0 family bridge vlan members 999
-
Configure the statistical analyzer
employee-monitor.[edit forwarding-options] user@device# set analyzer employee-monitor input ingress interface ge-0/0/0.0 user@device# set analyzer employee-monitor input ingress interface ge-0/0/1.0 user@device# set analyzer employee-monitor input egress interface ge-0/0/0.0 user@device# set analyzer employee-monitor input egress interface ge-0/0/1.0 user@device# set analyzer employee-monitor output bridge-domain remote-analyzer user@device# set analyzer employee-monitor input rate 2 user@device# set analyzer employee-monitor input maximum-packet-length 128
-
Bind the statistical analyzer to the FPC that contains the input interface.
[edit] user@device# set chassis fpc 0 port-mirror-instance employee-monitor
-
-
On the destination switching device, do the following:
-
Configure the VLAN ID for the
remote-analyzerbridge domain.[edit bridge-domains] user@device# set remote-analyzer vlan-id 999
-
Configure the interface on the destination switching device for access mode and associate it with the
remote-analyzerbridge domain.[edit interfaces] user@device# set ge-0/0/10 unit 0 family bridge interface-mode access user@device# set ge-0/0/10 unit 0 family bridge vlan members 999
-
Configure the interface connected to the destination switching device for access mode.
[edit interfaces] user@device# set ge-0/0/5 unit 0 family bridge interface-mode access
-
Configure the
employee-monitoranalyzer.[edit forwarding-options] user@device# set analyzer employee-monitor input ingress bridge-domain remote-analyzer user@device# set analyzer employee-monitor output interface ge-0/0/5.0
Specify mirroring parameters such as rate and the maximum packet length for the employee-monitor analyzer.
[edit] user@device# set forwarding-options analyzer employee-monitor input rate 2 user@device# set forwarding-options analyzer employee-monitor input maximum-packet-length 128
-
Bind the
employee-monitoranalyzer to the FPC containing the input ports.[edit] user@device# set chassis fpc 0 port-mirror-instance employee-monitor
-
Results
Check the results of the configuration on the source switching device:
[edit]
user@device# show
bridge-domains {
remote-analyzer {
vlan-id 999;
}
}
forwarding-options {
analyzer {
employee-monitor {
input {
ingress {
interface ge-0/0/0.0;
interface ge-0/0/1.0;
}
egress {
interface ge-0/0/0.0;
interface ge-0/0/1.0;
}
rate 2;
maximum-packet-length 128;
}
output {
bridge-domain {
remote-analyzer;
}
}
}
}
}
interfaces {
ge-0/0/0 {
unit 0 {
family bridge {
interface-mode access;
vlan-id 99;
}
}
}
ge-0/0/1 {
unit 0 {
family bridge {
interface-mode access;
vlan-id 98;
}
}
}
ge-0/0/10 {
unit 0 {
family bridge {
interface-mode access;
vlan-id 999;
}
}
}
}
Check the results of the configuration on the destination switching device.
[edit]
user@device# show
bridge-domains {
remote-analyzer {
vlan-id 999;
}
}
forwarding-options {
analyzer {
employee-monitor {
input {
ingress {
interface ge-0/0/0.0;
interface ge-0/0/1.0;
bridge-domain remote-analyzer;
}
}
output {
interface ge-0/0/5.0;
}
}
}
}
interfaces {
ge-0/0/5 {
unit 0 {
family bridge {
interface-mode access;
}
}
}
}
Verification
Verifying That the Analyzer Has Been Correctly Created
Purpose
Verify that the analyzer named employee-monitor has been
created on the device with the appropriate input interfaces and the
appropriate output interface.
Action
To verify that the analyzer is configured as expected while monitoring all
employee traffic on the source switching device, run the show
forwarding-options analyzer command on the source switching
device. The following output is displayed for this configuration
example.
user@device> show forwarding-options analyzer Analyzer name : employee-monitor Mirror rate : 2 Maximum packet length : 128 State : up Ingress monitored interfaces : ge-0/0/0.0 Ingress monitored interfaces : ge-0/0/1.0 Egress monitored interfaces : ge-0/0/0.0 Egress monitored interfaces : ge-0/0/1.0 Output VLAN : default-switch/remote-analyzer
Meaning
This output shows that the employee-monitor instance has a
ratio of 2, the maximum size of the original packets that were mirrored is
128, the state of the configuration is up, which indicates
proper state and that the analyzer is programmed, and the analyzer is
mirroring the traffic entering ge-0/0/0.0 and ge-0/0/1.0 and is sending the
mirrored traffic to the VLAN called remote-analyzer.
If the state of the output interface is down or if the
output interface is not configured, the value of State will
be down and the analyzer will not be able to monitor traffic.
Example: Configuring Mirroring to Multiple Interfaces for Remote Monitoring of Employee Resource Use on EX9200 Switches
EX9200 switches allow you to configure mirroring to send copies of packets to either a local interface for local monitoring or to a VLAN for remote monitoring. You can use mirroring to copy these packets:
-
Packets entering or exiting a port
-
Packets entering or exiting a VLAN on
You can analyze the mirrored traffic using a protocol analyzer application running on a remote monitoring station if you are sending mirrored traffic to an analyzer VLAN.
Mirror only necessary packets to reduce potential performance impact. We recommend that you:
-
Disable your configured mirroring analyzers when you are not using them.
-
Specify individual interfaces as input to analyzers rather than specifying all interfaces as input.
-
Limit the amount of mirrored traffic by:
-
Using statistical sampling.
-
Setting ratios to select statistical samples.
-
Using firewall filters.
-
This example describes how to configure remote mirroring to multiple interfaces on an analyzer VLAN:
- Requirements
- Overview and Topology
- Mirroring All Employee Traffic to Multiple VLAN Member Interfaces for Remote Analysis
- Verification
Requirements
This example uses the following hardware and software components:
-
Three EX9200 switches
-
Junos OS Release 13.2 or later for EX Series switches
Before you configure remote mirroring, be sure that:
-
The interfaces that the analyzer will use as input interfaces have been configured on the switch.
Overview and Topology
This example describes how to mirror traffic entering ports on the switch to the remote analyzer VLAN so that you can perform analysis from a remote monitoring station. The remote-analyzer VLAN in this example contains multiple member interfaces. Therefore, the same traffic is mirrored to all member interfaces of the remote-analyzer VLAN so that mirrored packets can be sent to different remote monitoring stations. You can install applications, such as sniffers and intrusion detection systems, on remote monitoring stations to analyze these mirrored packets and to obtain useful statistical data. For instance, if there are two remote monitoring stations, you can install a sniffer on one remote monitoring station and an intrusion detection system on the other station. You can use a firewall filter analyzer configuration to forward a specific type of traffic to a remote monitoring station.
This example describes how to configure an analyzer to mirror traffic to multiple interfaces in the next-hop group so that traffic is sent to different monitoring stations for analysis.
Figure 3 shows the network topology for this example.
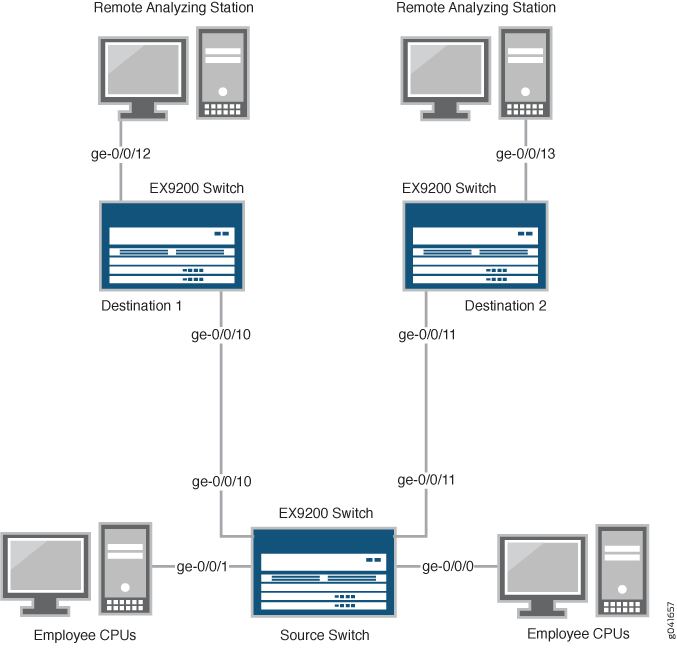
Topology
In this example:
-
Interfaces ge-0/0/0 and ge-0/0/1 are Layer 2 interfaces (both interfaces on the source switch) that serve as connections for employee computers.
-
Interfaces ge-0/0/10 and ge-0/0/11 are Layer 2 interfaces that are connected to different destination switches.
-
Interface ge-0/0/12 is a Layer 2 interface that connects the Destination 1 switch to the remote monitoring station.
-
Interface ge-0/0/13 is a Layer 2 interface that connects the Destination 2 switch to the remote monitoring station.
-
VLAN
remote-analyzeris configured on all switches in the topology to carry the mirrored traffic.
Mirroring All Employee Traffic to Multiple VLAN Member Interfaces for Remote Analysis
To configure mirroring to multiple VLAN member interfaces for remote traffic analysis for all incoming and outgoing employee traffic, perform these tasks:
Procedure
CLI Quick Configuration
To quickly configure mirroring for remote traffic analysis for incoming and outgoing employee traffic, copy the following commands and paste them into the switch terminal window:
-
In the source switch terminal window, copy and paste the following commands:
[edit] set vlans remote-analyzer vlan-id 999 set interfaces ge-0/0/10 unit 0 family ethernet-switching interface-mode access set interfaces ge-0/0/10 unit 0 family ethernet-switching vlan members 999 set interfaces ge-0/0/11 unit 0 family ethernet-switching interface-mode access set interfaces ge-0/0/11 unit 0 family ethernet-switching vlan members 999 set forwarding-options analyzer employee-monitor input ingress interface ge-0/0/0.0 set forwarding-options analyzer employee-monitor input ingress interface ge-0/0/1.0 set forwarding-options analyzer employee-monitor input egress interface ge-0/0/0.0 set forwarding-options analyzer employee-monitor input egress interface ge-0/0/1.0 set forwarding-options analyzer employee-monitor output next-hop-group remote-analyzer-nhg set forwarding-options next-hop-group remote-analyzer-nhg interface ge-0/0/10.0 set forwarding-options next-hop-group remote-analyzer-nhg interface ge-0/0/11.0 set forwarding-options next-hop-group remote-analyzer-nhg group-type layer-2
-
In the Destination 1 switch terminal window, copy and paste the following commands:
[edit] set vlans remote-analyzer vlan-id 999 set interfaces ge-0/0/10 unit 0 family ethernet-switching interface-mode acess set interfaces ge-0/0/12 unit 0 family ethernet-switching interface-mode access set forwarding-options analyzer employee-monitor input ingress vlan remote-analyzer set forwarding-options analyzer employee-monitor loss-priority high output interface ge-0/0/12.0
-
In the Destination 2 switch terminal window, copy and paste the following commands:
[edit] set vlans remote-analyzer vlan-id 999 set interfaces ge-0/0/11 unit 0 family ethernet-switching interface-mode access set interfaces ge-0/0/13 unit 0 family ethernet-switching interface-mode access set forwarding-options analyzer employee-monitor input ingress vlan remote-analyzer set forwarding-options analyzer employee-monitor loss-priority high output interface ge-0/0/13.0
Step-by-Step Procedure
To configure basic remote mirroring to two VLAN member interfaces:
-
On the source switch:
-
Configure the VLAN ID for the
remote-analyzerVLAN:[edit vlans] user@switch# set remote-analyzer vlan-id 999 -
Configure the interfaces on the network port connected to destination switches for access mode and associate it with the
remote-analyzerVLAN:[edit interfaces] user@switch# set ge-0/0/10 unit 0 family ethernet-switching interface-mode trunk user@switch# set ge-0/0/10 unit 0 family ethernet-switching vlan members 999 user@switch# set ge-0/0/11 unit 0 family ethernet-switching interface-mode trunk user@switch# set ge-0/0/11 unit 0 family ethernet-switching vlan members 999
-
Configure the
employee-monitoranalyzer:[edit forwarding-options] user@switch# set analyzer employee-monitor input ingress interface ge-0/0/0.0 user@switch# set analyzer employee-monitor input ingress interface ge-0/0/1.0 user@switch# set analyzer employee-monitor input egress interface ge-0/0/0.0 user@switch# set analyzer employee-monitor input egress interface ge-0/0/1.0 user@switch# set analyzer employee-monitor output next-hop-group remote-analyzer-nhg
In this analyzer configuration, traffic that enters and exits interfaces ge-0/0/0.0 and ge-0/0/1.0 are sent to the output destination defined by the next-hop group named
remote-analyzer-nhg. -
Configure the
remote-analyzer-nhbnext-hop group:[edit forwarding-options] user@switch# set next-hop-group remote-analyzer-nhg interface ge-0/0/10.0 user@switch# set next-hop-group remote-analyzer-nhg interface ge-0/0/11.0 user@switch# set next-hop-group remote-analyzer-nhg group-type layer-2
-
-
On the Destination 1 switch:
-
Configure the VLAN ID for the
remote-analyzerVLAN:[edit vlans] user@switch# set remote-analyzer vlan-id 999
-
Configure the ge-0/0/10 interface on the Destination 1 switch for access mode:
[edit interfaces] user@switch# set ge-0/0/10 unit 0 family ethernet-switching interface-mode access
-
Configure the interface connected to the remote monitoring station for access mode:
[edit interfaces] user@switch# set ge-0/0/12 unit 0 family ethernet-switching interface-mode access
-
Configure the
employee-monitoranalyzer:[edit forwarding-options] user@switch# set analyzer employee-monitor input ingress vlan remote-analyzer user@switch# set analyzer employee-monitor loss-priority high output interface ge-0/0/12.0
-
-
On the Destination 2 switch:
-
Configure the VLAN ID for the
remote-analyzerVLAN:[edit vlans] user@switch# set remote-analyzer vlan-id 999
-
Configure the ge-0/0/11 interface on the Destination 2 switch for access mode:
[edit interfaces] user@switch# set ge-0/0/11 unit 0 family ethernet-switching interface-mode access
-
Configure the interface connected to the remote monitoring station for access mode:
[edit interfaces] user@switch# set ge-0/0/13 unit 0 family ethernet-switching interface-mode access
-
Configure the
employee-monitoranalyzer:[edit forwarding-options] user@switch# set analyzer employee-monitor input ingress vlan remote-analyzer user@switch# set analyzer employee-monitor loss-priority high output interface ge-0/0/13.0
-
Results
Check the results of the configuration on the source switch:
[edit]
user@switch# show
forwarding-options {
analyzer employee-monitor {
input {
ingress {
interface ge-0/0/0.0;
interface ge-0/0/1.0;
}
egress {
interface ge-0/0/0.0;
interface ge-0/0/1.0;
}
}
output {
next-hop-group {
remote-analyzer-nhg;
}
}
}
}
vlans {
remote-analyzer {
vlan-id 999;
interface {
ge-0/0/10.0
ge-0/0/11.0
}
}
}
interfaces {
ge-0/0/10 {
unit 0 {
family ethernet-switching {
interface-mode access;
}
}
}
ge-0/0/11 {
unit 0 {
family ethernet-switching {
interface-mode access;
}
}
}
}
Check the results of the configuration on the Destination 1 switch:
[edit]
user@switch# show
vlans {
remote-analyzer {
vlan-id 999;
}
}
interfaces {
ge-0/0/10 {
unit 0 {
ethernet-switching {
interface-mode acess;
}
}
}
ge-0/0/12 {
unit 0 {
family ethernet-switching {
interface-mode access;
}
}
}
}
forwarding-options {
analyzer employee-monitor {
input {
ingress {
vlan remote-analyzer;
}
}
loss-priority high;
output {
interface {
ge-0/0/12.0;
}
}
}
}
Check the results of the configuration on the Destination 2 switch:
[edit]
user@switch# show
vlans {
remote-analyzer {
vlan-id 999;
interface {
ge-0/0/11.0
}
}
}
interfaces {
ge-0/0/11 {
unit 0 {
family ethernet-switching {
interface-mode access;
}
}
}
ge-0/0/13 {
unit 0 {
family ethernet-switching {
interface-mode access;
}
}
}
}
forwarding-options {
employee-monitor {
input {
ingress {
vlan remote-analyzer;
}
}
loss-priority high;
output {
interface {
ge-0/0/13.0;
}
}
}
}
Verification
To confirm that the configuration is working properly, perform these tasks:
Verifying That the Analyzer Has Been Correctly Created
Purpose
Verify that the analyzer named employee-monitor has
been created on the switch with the appropriate input interfaces and
appropriate output interface.
Action
You can verify the analyzer is configured as expected
by using the show forwarding-options analyzer command.
To verify that the analyzer is configured as expected while
monitoring all employee traffic on the source switch, run the show forwarding-options analyzer command on the source switch.
The following output is displayed for this example configuration on
the source switch:
user@switch> show forwarding-options analyzer
Analyzer name : employee-monitor
Mirror rate : 1
Maximum packet length : 0
State : up
Ingress monitored interfaces : ge-0/0/0.0
Ingress monitored interfaces : ge-0/0/1.0
Egress monitored interfaces : ge-0/0/0.0
Egress monitored interfaces : ge-0/0/1.0
Output nhg : remote-analyzer-nhg
user@switch> show forwarding-options next-hop-group
Next-hop-group: remote-analyzer-nhg
Type: layer-2
State: up
Members Interfaces:
ge-0/0/10.0
ge-0/0/11.0
Meaning
This output shows that the employee-monitor analyzer has a ratio of 1 (mirroring every packet, which is the
default behavior), the state of the configuration is up, which indicates proper state and that the analyzer
is programmed, mirrors traffic entering or exiting interfaces ge-0/0/0
and ge-0/0/1, and sends mirrored traffic to multiple interfaces ge-0/0/10.0
and ge-0/0/11.0 through the next-hop-group remote-analyzer-nhg. If the state of the output interface is down or if the output interface is not configured, the value of state
will be down and the analyzer will not be able to mirror traffic.
Example: Configuring Mirroring for Remote Monitoring of Employee Resource Use Through a Transit Switch on EX9200 Switches
EX9200 switches enable you to configure mirroring to send copies of packets to either a local interface for local monitoring or to a VLAN for remote monitoring. You can use mirroring to copy these packets:
-
Packets entering or exiting a port
-
Packets entering or exiting a VLAN
You can analyze the mirrored traffic using a protocol analyzer application running on a remote monitoring station if you are sending mirrored traffic to an analyzer VLAN.
This topic includes an example that describes how to mirror traffic entering ports on the switch to the remote-analyzer VLAN through a transit switch, so that you can perform analysis from a remote monitoring station.
Mirror only necessary packets to reduce potential performance impact. We recommend that you:
-
Disable your configured mirroring sessions when you are not using them.
-
Specify individual interfaces as input to analyzers rather than specifying all interfaces as input.
-
Limit the amount of mirrored traffic by:
-
Using statistical sampling.
-
Setting ratios to select statistical samples.
-
Using firewall filters.
-
This example describes how to configure remote mirroring through a transit switch:
- Requirements
- Overview and Topology
- Mirroring All Employee Traffic for Remote Analysis Through a Transit Switch
- Verification
Requirements
This example uses the following hardware and software components:
-
An EX9200 switch connected to another EX9200 switch through a third EX9200 switch
-
Junos OS Release 13.2 or later for EX Series switches
Before you configure remote mirroring, be sure that:
-
The interfaces that the analyzer will use as input interfaces have been configured on the switch.
Overview and Topology
This example describes how to mirror traffic entering ports
on the switch to the remote-analyzer VLAN through a transit
switch so that you can perform analysis on all traffic from employee
computers.
In this configuration, an analyzer session is required on the destination switch to mirror incoming traffic from the analyzer VLAN to the egress interface to which the remote monitoring station is connected.
Figure 4 shows the network topology for this example.
Topology
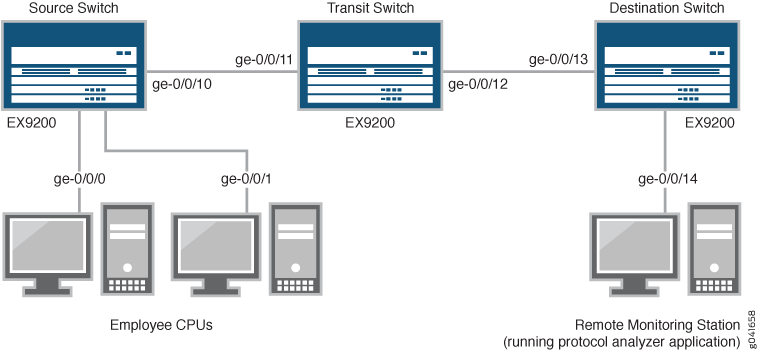
In this example:
-
Interface ge-0/0/0 is a Layer 2 interface, and interface ge-0/0/1 is a Layer 3 interface (both interfaces on the source switch) that serve as connections for employee computers.
-
Interface ge-0/0/10 is a Layer 2 interface that connects to the transit switch.
-
Interface ge-0/0/11 is a Layer 2 interface on the transit switch.
-
Interface ge-0/0/12 is a Layer 2 interface on the transit switch and connects to the destination switch.
-
Interface ge-0/0/13 is a Layer 2 interface on the destination switch.
-
Interface ge-0/0/14 is a Layer 2 interface on the destination switch and connects to the remote monitoring station.
-
VLAN
remote-analyzeris configured on all switches in the topology to carry the mirrored traffic.
Mirroring All Employee Traffic for Remote Analysis Through a Transit Switch
To configure mirroring for remote traffic analysis through a transit switch, for all incoming and outgoing employee traffic, perform these tasks:
Procedure
CLI Quick Configuration
To quickly configure mirroring for remote traffic analysis through a transit switch, for incoming and outgoing employee traffic, copy the following commands and paste them into the switch terminal window:
-
Copy and paste the following commands in the source switch (monitored switch) terminal window:
[edit] set vlans remote-analyzer vlan-id 999 set interfaces ge-0/0/10 unit 0 family ethernet-switching interface-mode access set interfaces ge-0/0/10 unit 0 family ethernet-switching vlan members 999 set forwarding-options analyzer employee-monitor input ingress interface ge-0/0/0.0 set forwarding-options analyzer employee-monitor input ingress interface ge-0/0/1.0 set forwarding-options analyzer employee-monitor input egress interface ge-0/0/0.0 set forwarding-options analyzer employee-monitor input egress interface ge-0/0/1.0 set forwarding-options analyzer employee-monitor output vlan remote-analyzer
-
Copy and paste the following commands in the transit switch window:
[edit] set vlans remote-analyzer vlan-id 999 set interfaces ge-0/0/11 unit 0 family ethernet-switching interface-mode access set vlans remote-analyzer interface ge-0/0/11 set interfaces ge-0/0/12 unit 0 family ethernet-switching interface-mode access set vlans remote-analyzer interface ge-0/0/12
-
Copy and paste the following commands in the destination switch window:
[edit] set vlans remote-analyzer vlan-id 999 set interfaces ge-0/0/13 unit 0 family ethernet-switching interface-mode access set vlans remote-analyzer interface ge-0/0/13 ingress set interfaces ge-0/0/14 unit 0 family ethernet-switching interface-mode access set forwarding-options analyzer employee-monitor input ingress vlan remote-analyzer set forwarding-options analyzer employee-monitor output interface ge-0/0/14.0
Step-by-Step Procedure
To configure remote mirroring through a transit switch:
-
On the source switch:
-
Configure the VLAN ID for the
remote-analyzerVLAN:[edit vlans] user@switch# set remote-analyzer vlan-id 999
-
Configure the interfaces on the network port connected to transit switch for access mode and associate it with the
remote-analyzerVLAN:[edit interfaces] user@switch# set ge-0/0/10 unit 0 family ethernet-switching interface-mode access user@switch# set ge-0/0/10 unit 0 family ethernet-switching vlan members 999
-
Configure the
employee-monitoranalyzer:[edit forwarding-options] user@switch# set analyzer employee-monitor input ingress interface ge-0/0/0.0 user@switch# set analyzer employee-monitor input ingress interface ge-0/0/1.0 user@switch# set analyzer employee-monitor input egress interface ge-0/0/0.0 user@switch# set analyzer employee-monitor input egress interface ge-0/0/1.0 user@switch# set analyzer employee-monitor output vlan remote-analyzer
-
-
On the transit switch:
-
Configure the VLAN ID for the
remote-analyzerVLAN:[edit vlans] user@switch# set remote-analyzer vlan-id 999
-
Configure the ge-0/0/11 interface for access mode, associate it with the
remote-analyzerVLAN:[edit interfaces] user@switch# set ge-0/0/11 unit 0 family ethernet-switching interface-mode access
-
Configure the ge-0/0/12 interface for access mode, associate it with the
remote-analyzerVLAN, and set the interface for egress traffic only:[edit interfaces] user@switch# set ge-0/0/12 unit 0 family ethernet-switching interface-mode access user@switch# set vlans remote-analyzer interface ge-0/0/12
-
-
On the destination switch:
-
Configure the VLAN ID for the
remote-analyzerVLAN:[edit vlans] user@switch# set remote-analyzer vlan-id 999
-
Configure the ge-0/0/13 interface for access mode, associate it with the
remote-analyzerVLAN, and set the interface for ingress traffic only:[edit interfaces] user@switch# set ge-0/0/13 unit 0 family ethernet-switching interface-mode access user@switch# set vlans remote-analyzer interface ge-0/0/13 ingress
-
Configure the interface connected to the remote monitoring station for access mode:
[edit interfaces] user@switch# set ge-0/0/14 unit 0 family ethernet-switching interface-mode access
-
Configure the
remote-analyzeranalyzer:[edit forwarding-options] user@switch# set analyzer employee-monitor input ingress vlan remote-analyzer user@switch# set analyzer employee-monitor output interface ge-0/0/14.0
-
Results
Check the results of the configuration on the source switch:
[edit]
user@switch> show
forwarding-options {
analyzer employee-monitor {
input {
ingress {
interface ge-0/0/0.0;
interface ge-0/0/1.0;
}
egress {
interface ge-0/0/0.0;
interface ge-0/0/1.0;
}
}
output {
vlan {
remote-analyzer;
}
}
}
}
vlans {
remote-analyzer {
vlan-id 999;
}
}
interfaces {
ge-0/0/10 {
unit 0 {
family ethernet-switching {
interface-mode access;
vlan {
member 999;
}
}
}
}
}
Check the results of the configuration on the transit switch:
[edit]
user@switch> show
vlans {
remote-analyzer {
vlan-id 999;
interface {
ge-0/0/11.0 {
}
ge-0/0/12.0 {
}
}
}
}
interfaces {
ge-0/0/11 {
unit 0 {
family ethernet-switching {
interface-mode access;
}
}
}
ge-0/0/12 {
unit 0 {
family ethernet-switching {
interface-mode access;
}
}
}
}
Check the results of the configuration on the destination switch:
[edit]
user@switch> show
vlans {
remote-analyzer {
vlan-id 999;
interface {
ge-0/0/13.0 {
ingress;
}
}
}
}
interfaces {
ge-0/0/13 {
unit 0 {
family ethernet-switching {
interface-mode access;
}
}
}
ge-0/0/14 {
unit 0 {
family ethernet-switching {
interface-mode access;
}
}
}
}
forwarding-options {
analyzer employee-monitor {
input {
ingress {
vlan remote-analyzer;
}
}
output {
interface {
ge-0/0/14.0;
}
}
}
}
Verification
To confirm that the configuration is working properly, perform these tasks:
Verifying That the Analyzer Has Been Correctly Created
Purpose
Verify that the analyzer named employee-monitor has
been created on the switch with the appropriate input interfaces and
the appropriate output interface.
Action
You can verify the analyzer is configured as expected
by using the show forwarding-options analyzer command.
To verify that the analyzer is configured as expected while
monitoring all employee traffic on the source switch, run the show forwarding-options analyzer command on the source switch.
The following output is displayed for this example configuration:
user@switch> show forwarding-options analyzer Analyzer name : employee-monitor Mirror rate : 1 Maximum packet length : 0 State : up Ingress monitored interfaces : ge-0/0/0.0 Ingress monitored interfaces : ge-0/0/1.0 Egress monitored interfaces : ge-0/0/0.0 Egress monitored interfaces : ge-0/0/1.0 Output vlan : default-switch/remote-analyzer
Meaning
This output shows that the employee-monitor analyzer
has a mirroring ratio of 1 (mirroring every packet, the default),
the state of the configuration is up, which indicates proper state and that the analyzer is programmed,
is mirroring the traffic entering ge-0/0/0 and ge-0/0/1, and is sending
the mirrored traffic to the analyzer called remote-analyzer. If the state of the output interface is down or if the output interface is not configured, the value of state
will be down and the analyzer will not be able to mirror traffic.
Example: Configuring Mirroring for Local Monitoring of Employee Resource Use on EX4300 Switches
This example uses Junos OS for EX Series switches with support for the Enhanced Layer 2 Software (ELS) configuration style. If your switch runs software that does not support ELS, see Example: Configuring Port Mirroring for Local Monitoring of Employee Resource Use on EX Series Switches. For ELS details, see Getting Started with Enhanced Layer 2 Software.
EX4300 switches enable you to configure mirroring to send copies of packets to either a local interface for local monitoring or to a VLAN for remote monitoring. You can use mirroring to copy these packets:
-
Packets entering or exiting a port
-
Packets entering a VLAN
You can analyze the mirrored traffic by using a protocol analyzer installed on a system connected to the local destination interface or a remote monitoring station if you are sending mirrored traffic to an analyzer VLAN.
This example describes how to configure local mirroring on an EX4300 switch. This example describes how to configure the switch to mirror traffic entering interfaces connected to employee computers to an analyzer output interface on the same switch.
- Requirements
- Overview and Topology
- Mirroring All Employee Traffic for Local Analysis
- Mirroring Employee-to-Web Traffic for Local Analysis
- Verification
Requirements
This example uses the following hardware and software components:
-
One EX4300 switch
-
Junos OS Release 13.2X50-D10 or later for EX Series switches
Overview and Topology
This topic includes two examples that describe how to mirror traffic entering ports on the switch to a destination interface on the same switch (local mirroring). The first example shows how to mirror all traffic entering the ports connected to employee computers. The second example shows the same scenario, but includes a filter to mirror only the employee traffic going to the Web.
The interfaces ge-0/0/0 and ge-0/0/1 serve as connections for employee computers. The interface ge0/0/10 is reserved for analysis of mirrored traffic. Connect a PC running a protocol analyzer application to the analyzer output interface to analyze the mirrored traffic.
Multiple ports mirrored to one interface can cause buffer overflow and dropped packets.
Both examples use the network topology shown in Figure 5.
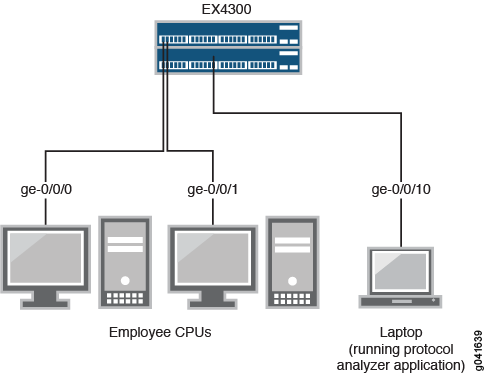
Mirroring All Employee Traffic for Local Analysis
To configure mirroring for all employee traffic for local analysis, perform these tasks:
Procedure
CLI Quick Configuration
To quickly configure local mirroring for ingress traffic to the two ports connected to employee computers, copy the following commands and paste them into the switch terminal window:
[edit] set interfaces ge-0/0/0 unit 0 family ethernet-switching set interfaces ge-0/0/1 unit 0 family inet address 192.0.2.1/24 set interfaces ge-0/0/10 unit 0 family ethernet-switching vlan members analyzer_vlan set vlans analyzer-vlan vlan-id 1000 set forwarding-options analyzer employee-monitor input ingress interface ge-0/0/0.0 set forwarding-options analyzer employee-monitor input ingress interface ge-0/0/1.0 set forwarding-options analyzer employee-monitor output interface ge-0/0/10.0
Step-by-Step Procedure
To configure an analyzer called employee-monitor and specify the input (source) interfaces and the analyzer output
interface:
-
Configure each interface connected to employee computers as an input interface for the analyzer
employee-monitor:[edit forwarding-options] user@switch# set analyzer employee-monitor input ingress interface ge–0/0/0.0 user@switch# set analyzer employee-monitor input ingress interface ge-0/0/1.0
-
Configure the output interface of the analyzer as part of a VLAN:
[edit interfaces] user@switch# set ge-0/0/10 unit 0 family ethernet-switching vlan members analyzer_vlan
[edit vlans] user@switch# set analyzer-vlan vlan-id 1000
-
Configure the output analyzer interface for the analyzer
employee-monitor. This will be the destination interface for the mirrored packets:[edit forwarding-options] user@switch# set analyzer employee-monitor output interface ge-0/0/10.0
Results
Check the results of the configuration:
[edit]
user@switch# show
forwarding-options {
analyzer employee-monitor {
input {
ingress {
interface ge-0/0/0.0;
interface ge-0/0/1.0;}
}
output {
interface {
ge-0/0/10.0;
}
}
}
}
Mirroring Employee-to-Web Traffic for Local Analysis
To configure mirroring for employee to Web traffic, perform these tasks:
Procedure
CLI Quick Configuration
To quickly configure local mirroring of traffic from the two ports connected to employee computers, filtering so that only traffic to the external Web is mirrored, copy the following commands and paste them into the switch terminal window:
[edit] set forwarding-options port-mirroring instance employee-web-monitor output interface ge-0/0/10.0 set firewall family ethernet-switching filter watch-employee term employee-to-corp from destination-address 192.0.2.16/24 set firewall family ethernet-switching filter watch-employee term employee-to-corp from source-address 192.0.2.16/24 set firewall family ethernet-switching filter watch-employee term employee-to-corp then accept set firewall family ethernet-switching filter watch-employee term employee-to-web from destination-port 80 set firewall family ethernet-switching filter watch-employee term employee-to-web then port-mirroring-instance employee-web-monitor set interfaces ge-0/0/0 unit 0 family ethernet-switching filter input watch-employee set interfaces ge-0/0/1 unit 0 family ethernet-switching filter input watch-employee
Step-by-Step Procedure
To configure local mirroring of employee to Web traffic from the two ports connected to employee computers:
-
Configure the local analyzer interface:
[edit interfaces] user@switch# set ge-0/0/10 unit 0 family ethernet-switching
-
Configure the
employee-web-monitoroutput instance (the input to the instance comes from the action of the filter):[edit forwarding-options port-mirroring] user@switch# set instance employee-web-monitor output interface ge-0/0/10.0
-
Configure a firewall filter called
watch-employeeto send mirrored copies of employee requests to the Web to theemployee-web-monitorinstance. Accept all traffic to and from the corporate subnet (destination or source address of 192.0.2.16/24). Send mirrored copies of all packets destined for the Internet (destination port 80) to theemployee-web-monitorinstance.[edit firewall family ethernet-switching] user@switch# set filter watch-employee term employee-to-corp from destination-address 192.0.2.16/24 user@switch# set filter watch-employee term employee-to-corp from source-address 192.0.2.16/24 user@switch# set filter watch-employee term employee-to-corp then accept ser@switch# set filter watch-employee term employee-to-web from destination-port 80 user@switch# set filter watch-employee term employee-to-web then port-mirroring-instance employee-web-monitor
-
Apply the
watch-employeefilter to the appropriate ports:[edit interfaces] user@switch# set ge-0/0/0 unit 0 family ethernet-switching filter input watch-employee user@switch# set ge-0/0/1 unit 0 family ethernet-switching filter input watch-employee
Results
Check the results of the configuration:
[edit]
user@switch# show
forwarding-options {
port-mirroring {
instance {
employee-web-monitor {
family ethernet-switching {
output {
interface ge-0/0/10.0;
}
}
}
}
}
}
...
firewall family ethernet-switching {
filter watch-employee {
term employee-to-corp {
from {
destination-address 192.0.2.16/24;
source-address 192.0.2.16/24;
}
then accept {
}
term employee-to-web {
from {
destination-port 80;
}
then port-mirroring-instance employee-web-monitor;
}
}
}
...
interfaces {
ge-0/0/0 {
unit 0 {
family ethernet-switching {
interface-mode trunk;
vlan members [employee-vlan, voice-vlan];
filter {
input watch-employee;
}
}
}
}
ge-0/0/1 {
family ethernet-switching {
filter {
input watch-employee;
}
}
}
}
Verification
To confirm that the configuration is correct, perform these tasks:
- Verifying That the Analyzer Has Been Correctly Created
- Verifying That The Port-Mirroring Instance Is Configured Properly
Verifying That the Analyzer Has Been Correctly Created
Purpose
Verify that the analyzer employee-monitor or employee-web-monitor has been created on the switch
with the appropriate input interfaces, and appropriate output interface.
Action
You can use the show forwarding-options analyzer command to verify that the analyzer is configured properly.
user@switch> show forwarding-options analyzer Analyzer name : employee-monitor Mirror rate : 1 Maximum packet length : 0 State : up Ingress monitored interfaces : ge-0/0/0.0 Ingress monitored interfaces : ge-0/0/1.0 Output interface : ge-0/0/10.0
Meaning
This output shows that the analyzer employee-monitor has a ratio of 1 (mirroring every packet, the default setting),
the maximum size of the original packet that was mirrored (0 indicates the entire packet), the state of the configuration
(is up indicates that the analyzer is mirroring the traffic entering
the ge-0/0/0, and ge-0/0/1 interfaces, and sending the mirrored traffic
to the ge-0/0/10 interface). If the state of the output interface
is down or if the output interface is not configured, the value of
state will be down and the analyzer will
not be programmed for mirroring.
Verifying That The Port-Mirroring Instance Is Configured Properly
Purpose
Verify that the port-mirroring instance employee-web-monitor has been configured properly on
the switch with the appropriate input interfaces.
Action
You can verify that the port-mirroring instance is configured
properly by using the show forwarding-options port-mirroring command.
user@switch> show forwarding-options port-mirroring
Instance Name: employee-web-monitor
Instance Id: 3
Input parameters:
Rate : 1
Run-length : 0
Maximum-packet-length : 0
Output parameters:
Family State Destination Next-hop
ethernet-switching up ge-0/0/10.0
Meaning
This output shows that the employee-web-monitor instance has a ratio of 1 (mirroring every packet, the default),
the maximum size of the original packet that was mirrored (0 indicates an entire packet), the state of the configuration
is up and port mirroring is programmed, and that mirrored traffic
from the firewall filter action is sent out on interface ge-0/0/10.0.
If the state of the output interface is down or if the interface is
not configured, the value for state will be down and port mirroring
will not be programmed for mirroring.
Example: Configuring Mirroring for Remote Monitoring of Employee Resource Use on EX4300 Switches
This example uses Junos OS for EX Series switches with support for the Enhanced Layer 2 Software (ELS) configuration style. If your switch runs software that does not support ELS, see Example: Configuring Mirroring for Remote Monitoring of Employee Resource Use on EX4300 Switches. For ELS details see: Getting Started with Enhanced Layer 2 Software.
EX4300 switches enable you to configure mirroring to send copies of packets to either a local interface for local monitoring or to a VLAN for remote monitoring. You can use mirroring to copy these packets:
-
Packets entering or exiting a port
-
Packets entering a VLAN on EX4300 switches
You can analyze the mirrored traffic by using a protocol analyzer application running on a remote monitoring station if you are sending mirrored traffic to an analyzer VLAN.
This topic includes two related examples that describe how to
mirror traffic entering ports on the switch to the remote-analyzer VLAN so that you can perform analysis from a remote monitoring station.
The first example shows how to mirror all traffic entering the ports
connected to employee computers. The second example shows the same
scenario but includes a filter to mirror only the employee traffic
going to the Web.
Mirror only necessary packets to reduce potential performance impact. We recommend that you:
-
Disable your configured mirroring sessions when you are not using them.
-
Specify individual interfaces as input to analyzers rather than specifying all interfaces as input.
-
Limit the amount of mirrored traffic by using firewall filters.
This example describes how to configure remote mirroring:
- Requirements
- Overview and Topology
- Mirroring All Employee Traffic for Remote Analysis
- Mirroring Employee-to-Web Traffic for Remote Analysis
- Verification
Requirements
This example uses the following hardware and software components:
-
Junos OS Release 13.2X50-D10 or later for EX Series switches
-
An EX4300 switch connected to another EX4300 switch
The diagram shows an EX4300 Virtual Chassis connected to an EX4300 destination switch.
Before you configure remote mirroring, be sure that:
-
You have an understanding of mirroring concepts.
-
The interfaces that the analyzer will use as input interfaces have been configured on the switch.
Overview and Topology
This topic includes two related examples that describe how to
configure mirroring to the remote-analyzer VLAN so that
analysis can be performed from a remote monitoring station. The first
example shows how to configure a switch to mirror all traffic from
employee computers. The second example shows the same scenario, but
the setup includes a filter to mirror only the employee traffic going
to the Web.
Figure 6 shows the network topology for both these example scenarios.
Topology
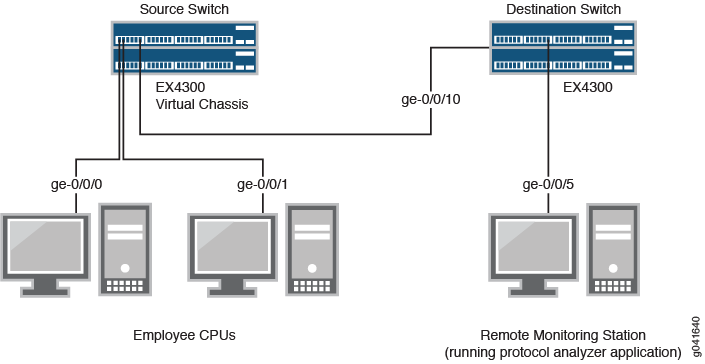
In this example:
-
Interface ge-0/0/0 is a Layer 2 interface, and interface ge-0/0/1 is a Layer 3 interface (both interfaces on the source switch) that serve as connections for employee computers.
-
Interface ge-0/0/10 is a Layer 2 interface that connects the source switch to the destination switch.
-
Interface ge-0/0/5 is a Layer 2 interface that connects the destination switch to the remote monitoring station.
-
VLAN
remote-analyzeris configured on all switches in the topology to carry the mirrored traffic.
Mirroring All Employee Traffic for Remote Analysis
To configure an analyzer for remote traffic analysis for all incoming and outgoing employee traffic, perform these tasks:
Procedure
CLI Quick Configuration
To quickly configure an analyzer for remote traffic analysis for incoming and outgoing employee traffic, copy the following commands and paste them into the switch terminal window:
-
Copy and paste the following commands in the source switch terminal window:
[edit] set vlans remote-analyzer vlan-id 999 set interfaces ge-0/0/10 unit 0 family ethernet-switching interface-mode trunk set interfaces ge-0/0/10 unit 0 family ethernet-switching vlan members 999 set forwarding-options analyzer employee-monitor input ingress interface ge-0/0/0.0 set forwarding-options analyzer employee-monitor input ingress interface ge-0/0/1.0 set forwarding-options analyzer employee-monitor input egress interface ge-0/0/0.0 set forwarding-options analyzer employee-monitor input egress interface ge-0/0/1.0 set forwarding-options analyzer employee-monitor output vlan remote-analyzer
-
Copy and paste the following commands in the destination switch terminal window:
[edit] set vlans remote-analyzer vlan-id 999 set interfaces ge-0/0/10 unit 0 family ethernet-switching interface-mode trunk set interfaces ge-0/0/10 unit 0 family ethernet-switching vlan members 999 set interfaces ge-0/0/5 unit 0 family ethernet-switching interface-mode trunk set forwarding-options analyzer employee-monitor input ingress vlan remote-analyzer set forwarding-options analyzer employee-monitor output interface ge-0/0/5.0
Step-by-Step Procedure
To configure basic remote port mirroring:
-
On the source switch:
-
Configure the VLAN ID for the
remote-analyzerVLAN:[edit vlans] user@switch# set remote-analyzer vlan-id 999 -
Configure the interface on the network port connected to the destination switch for trunk mode and associate it with the
remote-analyzerVLAN:[edit interfaces] user@switch# set ge-0/0/10 unit 0 family ethernet-switching interface-mode trunk user@switch# set ge-0/0/10 unit 0 family ethernet-switching vlan members 999
-
Configure the
employee-monitoranalyzer:[edit forwarding-options] user@switch# set analyzer employee-monitor input ingress interface ge-0/0/0.0 user@switch# set analyzer employee-monitor input ingress interface ge-0/0/1.0 user@switch# set instance employee-monitor input egress interface ge-0/0/0.0 user@switch# set analyzer employee-monitor input egress interface ge-0/0/1.0 user@switch# set analyzer employee-monitor output vlan remote-analyzer
-
-
On the destination switch:
-
Configure the VLAN ID for the
remote-analyzerVLAN:[edit vlans] user@switch# set remote-analyzer vlan-id 999
-
Configure the interface on the destination switch for trunk mode and associate it with the
remote-analyzerVLAN:[edit interfaces] user@switch# set ge-0/0/10 unit 0 family ethernet-switching interface-mode trunk user@switch# set ge-0/0/10 unit 0 family ethernet-switching vlan members 999
-
Configure the interface connected to the destination switch for trunk mode:
[edit interfaces] user@switch# set ge-0/0/5 unit 0 family ethernet-switching interface-mode trunk
-
Configure the
employee-monitoranalyzer:[edit forwarding-options] user@switch# set analyzer employee-monitor input ingress vlan remote-analyzer user@switch# set analyzer employee-monitor output interface ge-0/0/5.0
-
Results
Check the results of the configuration on the source switch:
[edit]
user@switch> show
forwarding-options {
analyzer employee-monitor {
input {
ingress {
interface ge-0/0/0.0;
interface ge-0/0/1.0;
}
egress {
interface ge-0/0/0.0;
interface ge-0/0/1.0;
}
}
output {
vlan {
remote-analyzer;
}
}
}
}
interfaces {
ge-0/0/10 {
unit 0 {
family ethernet-switching {
interface-mode trunk;
vlan {
members 999;
}
}
}
}
}
vlans {
remote-analyzer {
vlan-id 999;
interface {
ge-0/0/10.0
}
}
}
}
Check the results of the configuration on the destination switch:
[edit]
user@switch> show
interfaces {
ge0/0/5 {
unit 0 {
family ethernet-switching {
interface-mode trunk;
}
}
}
ge-0/0/10 {
unit 0 {
family ethernet-switching {
interface-mode trunk;
vlan {
members 999;
}
}
}
}
}
vlans {
remote-analyzer {
vlan-id 999;
interface {
ge-0/0/10.0
}
}
}
}
forwarding-options {
analyzer employee-monitor {
input {
ingress {
vlan remote-analyzer;
}
}
output {
interface {
ge-0/0/5.0;
}
}
}
}
Mirroring Employee-to-Web Traffic for Remote Analysis
To configure port mirroring for remote traffic analysis of employee- to- Web traffic, perform these tasks:
Procedure
CLI Quick Configuration
To quickly configure port mirroring to mirror employee traffic to the external Web, copy the following commands and paste them into the switch terminal window:
-
Copy and paste the following commands in the source switch terminal window:
[edit] user@switch# set forwarding-options port-mirroring instance employee-web-monitor output vlan 999 user@switch# set vlans remote-analyzer vlan-id 999 user@switch# set interfaces ge-0/0/10 unit 0 family ethernet-switching port mode trunk user@switch# set interfaces ge-0/0/10 unit 0 family ethernet-switching vlan members 999 user@switch# set firewall family ethernet-switching filter watch-employee term employee-to-corp from destination-address 192.0.2.16/24 user@switch# set firewall family ethernet-switching filter watch-employee term employee-to-corp from source-address 192.0.2.16/24 user@switch# set firewall family ethernet-switching filter watch-employee term employee-to-corp then accept user@switch# set firewall family ethernet-switching filter watch-employee term employee-to-web from destination-port 80 user@switch# set firewall family ethernet-switching filter watch-employee term employee-to-web then port-mirror-instance employee-web-monitor user@switch# set interfaces ge-0/0/0 unit 0 family ethernet-switching filter input watch-employee user@switch# set interfaces ge-0/0/1 unit 0 family ethernet-switching filter input watch-employee
-
Copy and paste the following commands in the destination switch terminal window:
[edit] user@switch# set vlans remote-analyzer vlan-id 999 user@switch# set interfaces ge-0/0/10 unit 0 family ethernet-switching interface-mode trunk user@switch# set interfaces ge-0/0/10 unit 0 family ethernet-switching vlan members 999 user@switch# set interfaces ge-0/0/5 unit 0 family ethernet-switching interface-mode trunk user@switch# set forwarding-options analyzer employee-web-monitor input ingress vlan remote-analyzer user@switch# set forwarding-options analyzer employee-web-monitor output interface ge-0/0/5.0
Step-by-Step Procedure
To configure port mirroring of all traffic from the two
ports connected to employee computers to the remote-analyzer VLAN for use from a remote monitoring station:
-
On the source switch:
-
Configure the
employee-web-monitorport mirroring instance:[edit ] user@switch# set interfaces ge-0/0/10 unit 0 family ethernet-switching port mode trunk user@switch# set forwarding-options port-mirroring instance employee-web-monitor output vlan 999
-
Configure the VLAN ID for the
remote-analyzerVLAN:[edit vlans] user@switch# set remote-analyzer vlan-id 999
-
Configure the interface to associate it with the
remote-analyzerVLAN:[edit interfaces] user@switch# set ge-0/0/10 unit 0 family ethernet-switching vlan members 999
-
Configure the firewall filter called
watch-employee:[edit firewall family ethernet-switching] user@switch# set filter watch-employee term employee-to-corp from destination-address 192.0.2.16/24 user@switch# set filter watch-employee term employee-to-corp from source-address 192.0.2.16/24 user@switch# set filter watch-employee term employee-to-corp then accept user@switch# set filter watch-employee term employee-to-web from destination-port 80 user@switch# set filter watch-employee term employee-to-web then port-mirror-instance employee-web-monitor
-
Apply the firewall filter to the employee interfaces:
[edit interfaces] user@switch# set ge-0/0/0 unit 0 family ethernet-switching filter input watch-employee user@switch# set ge-0/0/1 unit 0 family ethernet-switching filter input watch-employee
-
-
On the destination switch:
-
Configure the VLAN ID for the
remote-analyzerVLAN:[edit vlans] user@switch# set remote-analyzer vlan-id 999
-
Configure the interface on the destination switch for trunk mode and associate it with the
remote-analyzerVLAN:[edit interfaces] user@switch# set ge-0/0/10 unit 0 family ethernet-switching interface-mode trunk user@switch# set ge-0/0/10 unit 0 family ethernet-switching vlan members 999
-
Configure the interface connected to the destination switch for trunk mode:
[edit interfaces] user@switch# set ge-0/0/5 unit 0 family ethernet-switching interface-mode trunk
-
Configure the
employee-monitoranalyzer:[edit forwarding-options port-mirroring] user@switch# set instance employee-web-monitor input ingress vlan remote-analyzer user@switch# set instance employee-web-monitor output interface ge-0/0/5.0
-
Results
Check the results of the configuration on the source switch:
[edit]
user@switch> show
interfaces {
ge-0/0/10 {
unit 0 {
family ethernet-switching {
interface-mode trunk;
vlan {
members remote-analyzer;
}
}
}
}
ge-0/0/0 {
unit 0 {
family ethernet-switching {
filter {
input watch-employee;
}
}
}
}
ge-0/0/1 {
unit 0 {
family ethernet-switching {
filter {
input watch-employee;
}
}
}
}
}
firewall {
family ethernet-switching {
filter watch-employee {
term employee-to-corp {
from {
source-address {
192.0.2.16/24;
}
destination-address {
192.0.2.16/24;
}
}
then accept;
}
term employee-to-web {
from {
destination-port 80;
}
then port-mirror-instance employee-web-monitor;
}
}
}
}
forwarding-options {
analyzer employee-web-monitor {
output {
vlan {
999;
}
}
}
vlans {
remote-analyzer {
vlan-id 999;
}
}
Check the results of the configuration on the destination switch:
[edit]
user@switch> show
vlans {
remote-analyzer {
vlan-id 999;
}
}
interfaces {
ge-0/0/10 {
unit 0 {
family ethernet-switching {
interface-mode trunk;
vlan {
members remote-analyzer;
}
}
}
}
ge-0/0/5 {
unit 0 {
family ethernet-switching {
interface-mode trunk;
}
}
}
}
forwarding-options {
port-mirroring {
instance employee-web-monitor {
input {
ingress {
vlan remote-analyzer;
}
}
output {
interface {
ge-0/0/5.0;
}
}
}
}
Verification
To confirm that the configuration is working properly, perform these tasks:
Verifying That the Analyzer Has Been Correctly Created
Purpose
Verify that the analyzer named employee-monitor or employee-web-monitor has been created on the switch with the
appropriate input interfaces and appropriate output interface.
Action
You can verify the analyzer is configured as expected
by using the show forwarding-options analyzer command.
To view previously created analyzers that are disabled, go to the
J-Web interface.
To verify that the analyzer is configured as expected while
monitoring all employee traffic on the source switch, run the show analyzer command on the source switch. The following output
is displayed for this configuration example:
user@switch> show forwarding-options analyzer Analyzer name : employee-monitor Mirror rate : 1 Maximum packet length : 0 State : up Ingress monitored interfaces : ge-0/0/0.0 Ingress monitored interfaces : ge-0/0/1.0 Egress monitored interfaces : ge-0/0/0.0 Egress monitored interfaces : ge-0/0/1.0 Output VLAN : default-switch/remote-analyzer
Meaning
This output shows that the employee-monitor instance
has a ratio of 1 (mirroring every packet, the default), the maximum
size of the original packet that was mirrored (0 indicates the entire
packet), the state of the configuration is up (which indicates the
proper state and that the analyzer is programmed, and is mirroring
the traffic entering ge-0/0/0 and ge-0/0/1 and is sending the mirrored
traffic to the VLAN called remote-analyzer). If the state
of the output interface is down or if the output interface is not
configured, the value of state will be down and the analyzer will
not be programmed for mirroring.
Example: Configuring Mirroring for Remote Monitoring of Employee Resource Use Through a Transit Switch on EX4300 Switches
This example uses Junos OS for EX Series switches with support for the Enhanced Layer 2 Software (ELS) configuration style.
EX4300 switches enable you to configure mirroring to send copies of packets to either a local interface for local monitoring or to a VLAN for remote monitoring. You can use mirroring to copy these packets:
-
Packets entering or exiting a port
-
Packets entering a VLAN on EX4300 switches
You can analyze the mirrored traffic by using a protocol analyzer application running on a remote monitoring station if you are sending mirrored traffic to an analyzer VLAN.
This topic includes an example that describes how to mirror
traffic entering ports on the switch to the remote-analyzer VLAN through a transit switch, so that you can perform analysis
from a remote monitoring station.
Mirror only necessary packets to reduce potential performance impact. We recommend that you:
-
Disable your configured mirroring sessions when you are not using them.
-
Specify individual interfaces as input to analyzers rather than specifying all interfaces as input.
-
Limit the amount of mirrored traffic by using firewall filters.
This example describes how to configure remote mirroring through a transit switch:
- Requirements
- Overview and Topology
- Mirroring All Employee Traffic for Remote Analysis Through a Transit Switch
- Verification
Requirements
This example uses the following hardware and software components:
-
An EX4300 switch connected to another EX4300 switch through a third EX4300 switch
-
Junos OS Release 13.2X50-D10 or later for EX Series switches
Before you configure remote mirroring, be sure that:
-
You have an understanding of mirroring concepts.
-
The interfaces that the analyzer will use as input interfaces have been configured on the switch.
Overview and Topology
This example describes how to mirror traffic entering ports
on the switch to the remote-analyzer VLAN through a transit
switch so that you can perform analysis from a remote monitoring station.
The example shows how to configure a switch to mirror all traffic
from employee computers to a remote analyzer.
In this configuration, an analyzer session is required on the
destination switch to mirror incoming traffic from the analyzer VLAN
to the egress interface to which the remote monitoring station is
connected. You must disable MAC learning on the transit switch for
the remote-analyzer VLAN so that MAC learning is disabled
for all member interfaces of the remote-analyzer VLAN on
the transit switch.
Figure 7 shows the network topology for this example.
Topology
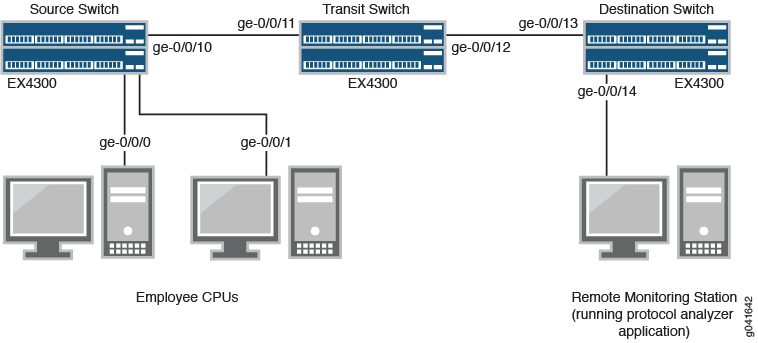
In this example:
-
Interface ge-0/0/0 is a Layer 2 interface, and interface ge-0/0/1 is a Layer 3 interface (both interfaces on the source switch) that serve as connections for employee computers.
-
Interface ge-0/0/10 is a Layer 2 interface that connects to the transit switch.
-
Interface ge-0/0/11 is a Layer 2 interface on the transit switch.
-
Interface ge-0/0/12 is a Layer 2 interface on the transit switch and connects to the destination switch.
-
Interface ge-0/0/13 is a Layer 2 interface on the destination switch .
-
Interface ge-0/0/14 is a Layer 2 interface on the destination switch and connects to the remote monitoring station.
-
VLAN
remote-analyzeris configured on all switches in the topology to carry the mirrored traffic.
Mirroring All Employee Traffic for Remote Analysis Through a Transit Switch
To configure mirroring for remote traffic analysis through a transit switch, for all incoming and outgoing employee traffic, perform these tasks:
Procedure
CLI Quick Configuration
To quickly configure mirroring for remote traffic analysis through a transit switch, for incoming and outgoing employee traffic, copy the following commands and paste them into the switch terminal window:
-
Copy and paste the following commands in the source switch (monitored switch) terminal window:
[edit] set vlans remote-analyzer vlan-id 999 set interfaces ge-0/0/10 unit 0 family ethernet-switching interface-mode trunk set interfaces ge-0/0/10 unit 0 family ethernet-switching vlan members 999 set forwarding-options analyzer employee-monitor input ingress interface ge-0/0/0.0 set forwarding-options analyzer employee-monitor input ingress interface ge-0/0/1.0 set forwarding-options analyzer employee-monitor input egress interface ge-0/0/0.0 set forwarding-options analyzer employee-monitor input egress interface ge-0/0/1.0 set forwarding-options analyzer employee-monitor output vlan remote-analyzer
-
Copy and paste the following commands in the transit switch window:
[edit] set vlans remote-analyzer vlan-id 999 set interfaces ge-0/0/11 unit 0 family ethernet-switching interface-mode trunk set vlans remote-analyzer interface ge-0/0/11 set interfaces ge-0/0/12 unit 0 family ethernet-switching interface-mode trunk set vlans remote-analyzer interface ge-0/0/12 set vlans remote-analyzer no-mac-learning
-
Copy and paste the following commands in the destination switch window:
[edit] set vlans remote-analyzer vlan-id 999 set interfaces ge-0/0/13 unit 0 family ethernet-switching interface-mode trunk set vlans remote-analyzer interface ge-0/0/13 ingress set interfaces ge-0/0/14 unit 0 family ethernet-switching interface-mode trunk set forwarding-options analyzer employee-monitor input ingress vlan remote-analyzer set forwarding-options analyzer employee-monitor output interface ge-0/0/14.0
Step-by-Step Procedure
To configure remote mirroring through a transit switch:
-
On the source switch:
-
Configure the VLAN ID for the
remote-analyzerVLAN:[edit vlans] user@switch# set remote-analyzer vlan-id 999
-
Configure the interfaces on the network port connected to transit switch for trunk mode and associate it with the
remote-analyzerVLAN:[edit interfaces] user@switch# set ge-0/0/10 unit 0 family ethernet-switching interface-mode trunk user@switch# set ge-0/0/10 unit 0 family ethernet-switching vlan members 999
-
Configure the
employee-monitoranalyzer:[edit forwarding-options] user@switch# set analyzer employee-monitor input ingress interface ge-0/0/0.0 user@switch# set analyzer employee-monitor input ingress interface ge-0/0/1.0 user@switch# set analyzer employee-monitor input egress interface ge-0/0/0.0 user@switch# set analyzer employee-monitor input egress interface ge-0/0/1.0 user@switch# set analyzer employee-monitor output vlan remote-analyzer
-
-
On the transit switch:
-
Configure the VLAN ID for the
remote-analyzerVLAN:[edit vlans] user@switch# set remote-analyzer vlan-id 999
-
Configure the ge-0/0/11 interface for trunk mode, associate it with the
remote-analyzerVLAN:[edit interfaces] user@switch# set ge-0/0/11 unit 0 family ethernet-switching interface-mode trunk
-
Configure the
ge-0/0/12interface for trunk mode, associate it with theremote-analyzerVLAN, and set the interface for egress traffic only:[edit interfaces] user@switch# set ge-0/0/12 unit 0 family ethernet-switching interface-mode trunk user@switch# set vlans remote-analyzer interface ge-0/0/12
-
Configure the
no-mac-learningoption for theremote-analyzerVLAN to disable MAC learning on all interfaces that are members of theremote-analyzerVLAN:[edit interfaces] user@switch# set vlans remote-analyzer no-mac-learning
-
-
On the destination switch:
-
Configure the VLAN ID for the
remote-analyzerVLAN:[edit vlans] user@switch# set remote-analyzer vlan-id 999
-
Configure the ge-0/0/13 interface for trunk mode, associate it with the
remote-analyzerVLAN, and set the interface for ingress traffic only:[edit interfaces] user@switch# set ge-0/0/13 unit 0 family ethernet-switching interface-mode trunk user@switch# set vlans remote-analyzer interface ge-0/0/13 ingress
-
Configure the interface connected to the remote monitoring station for trunk mode:
[edit interfaces] user@switch# set ge-0/0/14 unit 0 family ethernet-switching interface-mode trunk
-
Configure the
employee-monitoranalyzer:[edit forwarding-options] user@switch# set analyzer employee-monitor input ingress vlan remote-analyzer user@switch# set analyzer employee-monitor output interface ge-0/0/14.0
-
Results
Check the results of the configuration on the source switch:
[edit]
user@switch> show
forwarding-options {
analyzer employee-monitor {
input {
ingress {
interface ge-0/0/0.0;
interface ge-0/0/1.0;
}
egress {
interface ge-0/0/0.0;
interface ge-0/0/1.0;
}
}
output {
vlan {
remote-analyzer;
}
}
}
}
vlans {
remote-analyzer {
vlan-id 999;
}
}
interfaces {
ge-0/0/10 {
unit 0 {
family ethernet-switching {
interface-mode trunk;
vlan {
member 999;
}
}
}
}
}
Check the results of the configuration on the transit switch:
[edit]
user@switch> show
vlans {
remote-analyzer {
vlan-id 999;
interface {
ge-0/0/11.0 {
}
ge-0/0/12.0 {
}
}
no-mac-learning;
}
}
interfaces {
ge-0/0/11 {
unit 0 {
family ethernet-switching {
interface-mode trunk;
}
}
}
ge-0/0/12 {
unit 0 {
family ethernet-switching {
interface-mode trunk;
}
}
}
}
Check the results of the configuration on the destination switch:
[edit]
user@switch> show
vlans {
remote-analyzer {
vlan-id 999;
interface {
ge-0/0/13.0 {
ingress;
}
}
}
}
interfaces {
ge-0/0/13 {
unit 0 {
family ethernet-switching {
interface-mode trunk;
}
}
}
ge-0/0/14 {
unit 0 {
family ethernet-switching {
interface-mode trunk;
}
}
}
}
forwarding-options {
analyzer employee-monitor {
input {
ingress {
vlan remote-analyzer;
}
}
output {
interface {
ge-0/0/14.0;
}
}
}
}
Verification
To confirm that the configuration is working properly, perform these tasks:
Verifying That the Analyzer Has Been Correctly Created
Purpose
Verify that the analyzer named employee-monitor has
been created on the switch with the appropriate input interfaces and
the appropriate output interface.
Action
You can verify whether the analyzer is configured as
expected by using the show analyzer command. To view previously
created analyzers that are disabled, go to the J-Web interface.
To verify that the analyzer is configured as expected while
monitoring all employee traffic on the source switch, run the show analyzer command on the source switch. The following output
is displayed for this example configuration:
user@switch> show forwarding-options analyzer Analyzer name : employee-monitor Mirror rate : 1 Maximum packet length : 0 State : up Ingress monitored interfaces : ge-0/0/0.0 Ingress monitored interfaces : ge-0/0/1.0 Egress monitored interfaces : ge-0/0/0.0 Egress monitored interfaces : ge-0/0/1.0 Output vlan : default-switch/remote-analyzer
Meaning
This output shows that the employee-monitor analyzer
has a ratio of 1 (mirroring every packet, the default), is mirroring
the traffic entering ge-0/0/0 and ge-0/0/1, and sending the mirrored
traffic to the analyzer remote-analyzer.
