Example: AS PIC IKE Dynamic SA with Digital Certificates Configuration
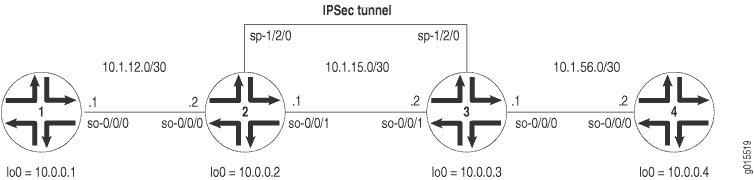
Figure 1 shows the same IPSec topology as the AS PIC dynamic SA example on Example: AS PIC IKE Dynamic SA Configuration. However, this configuration requires Routers 2 and 3 to establish an IKE-based IPSec tunnel by using digital certificates in place of preshared keys. Routers 1 and 4 continue to provide basic connectivity and are used to verify that the IPSec tunnel is operational.
On Router 1, provide basic OSPF connectivity to Router 2.
Router 1
[edit]
interfaces {
so-0/0/0 {
description "To R2 so-0/0/0";
unit 0 {
family inet {
address 10.1.12.2/30;
}
}
}
lo0 {
unit 0 {
family inet {
address 10.0.0.1/32;
}
}
}
}
routing-options {
router-id 10.0.0.1;
}
protocols {
ospf {
area 0.0.0.0 {
interface so-0/0/0.0;
interface lo0.0;
}
}
}
On Router 2, you must request a CA certificate, create a local certificate, and load these digital certificates into the router before you can reference them in your IPSec configuration. To begin, configure an IPSec profile by specifying the trusted CA and URL of the CA server that handles CA certificate processing:
[edit]
security {
pki {
ca-profile entrust {
ca-identity entrust;
enrollment {
url http://ca-1.example.com/cgi-bin/pkiclient.exe;
}
}
}
}
Certificate revocation list (CRL) verification is enabled by default. You can optionally specify the Lightweight Access Directory (LDAP) server where the CA stores the CRL. The certificate typically includes a certificate distribution point (CDP), which contains information about how to retrieve the CRL for the certificate. The router uses this information to download the CRL automatically. In this example, the LDAP URL is specified, which overrides the location provided in the certificate:
[edit]
security pki ca-profile entrust {
revocation-check {
crl {
url ldap://10.157.90.185/o=juniper,c=uscertificateRevocationListbase;
}
}
}
After you configure the CA profile, you can request a CA certificate from the trusted CA. In this example, the certificate is enrolled online and installed into the router automatically.
user@R2> request security pki ca-certificate enroll ca-profile entrust
Received following certificates:
Certificate: C=us, O=juniper
Fingerprint: 00:8e:6f:58:dd:68:bf:25:0a:e3:f9:17:70:d6:61:f3:53:a7:79:10
Certificate: C=us, O=juniper, CN=First Officer
Fingerprint: bc:78:87:9b:a7:91:13:20:71:db:ac:b5:56:71:42:ad:1a:b6:46:17
Certificate: C=us, O=juniper, CN=First Officer
Fingerprint: 46:71:15:34:f0:a6:41:76:65:81:33:4f:68:47:c4:df:78:b8:e3:3f
Do you want to load the above CA certificate ? [yes,no] (no) yes
If you obtain the CA certificate directly from the CA (for example,
as an e-mail attachment or website download), you can install it with the request security
pki ca-certificate load command.
Next, you must generate a private/public key pair before you can create a local certificate.
user@R2> request security pki generate-key-pair certificate-id local-entrust2 Generated key pair local-entrust2, key size 1024 bits
When the key pair is available, generate a local certificate request and send it to the CA for processing.
user@R2> request security pki generate-certificate-request certificate-id local-entrust2 domain-name router2.example.com filename entrust-req2 subject cn=router2.example.com Generated certificate request -----BEGIN CERTIFICATE REQUEST----- MIIBoTCCAQoCAQAwGjEYMBYGA1UEAxMPdHAxLmp1bmlwZXIubmV0MIGfMA0GCSqG SIb3DQEBAQUAA4GNADCBiQKBgQCiUFklQws1Ud+AqN5DDxRs2kVyKEhh9qoVFnz+ Hz4c9vsy3B8ElwTJlkmIt2cB3yifB6zePd+6WYpf57Crwre7YqPkiXM31F6z3YjX H+1BPNbCxNWYvyrnSyVYDbFj8o0Xyqog8ACDfVL2JBWrPNBYy7imq/K9soDBbAs6 5hZqqwIDAQABoEcwRQYJKoZIhvcNAQkOMTgwNjAOBgNVHQ8BAf8EBAMCB4AwJAYD VR0RAQH/BBowGIIWdHAxLmVuZ2xhYi5qdW5pcGVyLm5ldDANBgkqhkiG9w0BAQQF AAOBgQBc2rq1v5SOQXH7LCb/FdqAL8ZM6GoaN5d6cGwq4bB6a7UQFgtoH406gQ3G 3iH0Zfz4xMIBpJYuGd1dkqgvcDoH3AgTsLkfn7Wi3x5H2qeQVs9bvL4P5nvEZLND EIMUHwteolZCiZ70fO9Fer9cXWHSQs1UtXtgPqQJy2xIeImLgw== -----END CERTIFICATE REQUEST----- Fingerprint: 0d:90:b8:d2:56:74:fc:84:59:62:b9:78:71:9c:e4:9c:54:ba:16:97 (sha1) 1b:08:d4:f7:90:f1:c4:39:08:c9:de:76:00:86:62:b8 (md5)
You can request the creation and installation of a local certificate
online with the request security pki local-certificate enroll command. For more
information, see Generating and Enrolling a Local Digital Certificate or the Junos System Basics and Services Command Reference.
The trusted CA digitally signs the local certificate and returns it to you. Copy the certificate file into the router and load the certificate.
user@R2> request security pki local-certificate load filename /tmp/router2-cert certificate-id local-entrust2 Local certificate local-entrust2 loaded successfully
The name of the file sent to you by the CA might not match the name of the certificate identifier. However, the certificate-id name must always match the name of the key pair you generated for the router.
After the local and CA certificates have been loaded, you can reference them in your IPSec configuration.
Using default values in the AS PIC, you do not need to configure an IPSec proposal or
IPSec policy. However, you must configure an IKE proposal that specifies the use of digital
certificates, reference the IKE proposal and local certificate in an IKE policy, and apply
the CA profile to the service set. To enable an IKE proposal for digital certificates, include
the rsa-signatures statement at the [edit services ipsec-vpn ike proposal proposal-name authentication-method] hierarchy level. To reference the local
certificate in the IKE policy, include the local-certificate statement at the [edit services ipsec-vpn ike policy policy-name] hierarchy level.
To identify the CA or RA in the service set, include the trusted-ca statement at
the [edit services service-set service-set-name ipsec-vpn-options] hierarchy level.
For more information about default IKE and IPSec policies and proposals on the AS PIC, see Configuring IKE Dynamic SAs.
Optionally, you can configure automatic reenrollment of the certificate with the auto-re-enrollment statement at the [edit security pki] hierarchy level.
The remaining configuration components of your IKE-based IPSec tunnel are the same as
when you use preshared keys. Enable OSPF as the underlying routing protocol to connect to
Routers 1 and 3. Configure a bidirectional IKE dynamic SA in a rule called rule-ike at the [edit ipsec-vpn rule] hierarchy level. Reference this rule in a service
set called service-set-dynamic-BiEspsha3des at the [edit services service-set] hierarchy level.
To direct traffic into the AS PIC and the IPsec tunnel, configure a next-hop style service set and add the adaptive services logical interface used as the IPSec inside interface into the OSPF configuration.
Router 2
[edit]
interfaces {
so-0/0/0 {
description "To R1 so-0/0/0";
unit 0 {
family inet {
address 10.1.12.1/30;
}
}
}
so-0/0/1 {
description "To R3 so-0/0/1";
unit 0 {
family inet {
address 10.1.15.1/30;
}
}
}
sp-1/2/0 {
unit 0 {
family inet;
}
unit 1 { # sp-1/2/0.1 is the IPSec inside interface.
family inet;
service-domain inside;
}
unit 2 { # sp-1/2/0.2 is the IPSec outside interface.
family inet;
service-domain outside;
}
}
lo0 {
unit 0 {
family inet {
address 10.0.0.2/32;
}
}
}
}
routing-options {
router-id 10.0.0.2;
}
protocols {
ospf {
area 0.0.0.0 {
interface so-0/0/0.0;
interface sp-1/2/0.1; # This sends OSPF traffic over the IPSec tunnel.
interface lo0.0;
}
}
}
security { # Configure CA profiles here, including the URLs used to reach the CAs.
pki {
ca-profile entrust {
ca-identity entrust;
enrollment {
url http://ca-1.example.com/cgi-bin/pkiclient.exe;
}
revocation-check {
crl {
url ldap://10.157.90.185/o=juniper,c=uscertificateRevocationListbase;
# Specify the URL of the LDAP server where the CA stores the CRL.
}
}
}
ca-profile microsoft {
ca-identity microsoft;
enrollment {
url http://192.168.11.78:80/certsrv/mscep/mscep.dll;
}
}
ca-profile verisign {
ca-identity verisign;
enrollment {
url http://pilotonsiteipsec.verisign.com/cgi-bin/pkiclient.exe;
}
}
}
}
services {
service-set service-set-dynamic-BiEspsha3des { # Define your service set here.
next-hop-service { # Required for dynamic routing protocols such as OSPF.
inside-service-interface sp-1/2/0.1;
outside-service-interface sp-1/2/0.2;
}
ipsec-vpn-options {
trusted-ca entrust; # Reference the CA profile here.
local-gateway 10.1.15.1; # Specify the local IP address of the IPSec tunnel.
}
ipsec-vpn-rules rule-ike; # Reference your IPSec VPN rule here.
}
ipsec-vpn {
rule rule-ike { # Define your IPSec VPN rule here.
term term-ike {
then {
remote-gateway 10.1.15.2; # The remote IP address of the IPSec tunnel.
dynamic { # This creates a dynamic SA.
ike-policy ike-digital-certificates; # Reference your IKE policy here.
}
}
}
match-direction input; # Specify in which direction the rule should match.
}
ike {
proposal ike-proposal {
authentication-method rsa-signatures; # Uses digital certificates
}
policy ike-digital-certificates {
proposals ike-proposal; # Apply the IKE proposal here.
local-id fqdn router2.example.com; # Provide an identifier for the local router.
local-certificate local-entrust2; # Reference the local certificate here.
remote-id fqdn router3.example.com; # Provide an ID for the remote router.
}
}
establish-tunnels immediately;
}
}
On Router 3, you must repeat the digital certificate procedures you performed on Router 2. If the IPSec peers do not have a symmetrical configuration containing all the necessary components, they cannot establish a peering relationship.
You need to request a CA certificate, create a local certificate, load these digital certificates into the router, and reference them in your IPSec configuration. Begin by configuring an IPSec CA profile. Include the ca-profile statement at the [edit security pki] hierarchy level and specify the trusted CA and URL of the CA server that handles CA certificate processing. Include the CRL statements found on Router 2 to complete your CA profile on Router 3.
After you configure the CA profile, request a CA certificate from the trusted CA. In this example, the certificate is enrolled online and installed into the router automatically.
user@R3> request security pki ca-certificate enroll ca-profile entrust
Received following certificates:
Certificate: C=us, O=juniper
Fingerprint: 00:8e:6f:58:dd:68:bf:25:0a:e3:f9:17:70:d6:61:f3:53:a7:79:10
Certificate: C=us, O=juniper, CN=First Officer
Fingerprint: bc:78:87:9b:a7:91:13:20:71:db:ac:b5:56:71:42:ad:1a:b6:46:17
Certificate: C=us, O=juniper, CN=First Officer
Fingerprint: 46:71:15:34:f0:a6:41:76:65:81:33:4f:68:47:c4:df:78:b8:e3:3f
Do you want to load the above CA certificate ? [yes,no] (no) yes
If you obtain the CA certificate directly from the CA (for example,
as an e-mail attachment or website download), you can install it with the request security
pki ca-certificate load command.
Next, generate a private/public key pair.
user@R3> request security pki generate-key-pair certificate-id local-entrust3 Generated key pair local-entrust3, key size 1024 bits
When the key pair is available, you can generate a local certificate request and send it to the CA for processing.
user@R3> request security pki generate-certificate-request certificate-id local-entrust3 domain-name router3.example.com filename entrust-req3 subject cn=router3.example.com Generated certificate request -----BEGIN CERTIFICATE REQUEST----- MIIB8jCCAVsCAQAwZTEYMBYGA1UEAxMPdHA1Lmp1bmlwZXIubmV0MRQwEgYDVQQL EwtFbmdpbmVlcmluZzEQMA4GA1UEChMHSnVuaXBlcjETMBEGA1UECBMKQ2FsaWZv cm5pYTEMMAoGA1UEBhMDVVNBMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCg Wjo50w8jrnphs0sRFvqQMwC6PlYa65thrJ8nHZ2qgYgRbSrO8hdODhvU6/5VuD2/ zBtgV5ZSAOlyV6DXqlbVj/2XirQAJMRCr1eYu6DhYRBMNq/UaQv4Z8Sse1EJv+uR HTNbD7xlwpw2zwzltRuGFtFr/FrGB0hF7IE+Xm5e2wIDAQABoE0wSwYJKoZIhvcN AQkOMT4wPDAOBgNVHQ8BAf8EBAMCB4AwKgYDVR0RAQH/BCAwHocEwKhGk4IWdHA1 LmVuZ2xhYi5qdW5pcGVyLm5ldDANBgkqhkiG9w0BAQQFAAOBgQBbiJ+ZCeQ59/eY 4Rd6awIpJFTz0svRZLxxjFWogusVTmaD2dsqFBqftS1eJBdeiueRcYMF9vOn0GKm FNfouegwei5+vzdNmNo55eIb3rs4pP62q0W5CUgmbHrjtp3lyJsvuOxTTcPNY8zw b6GyM2Hdkk3Vh2ReX11tQUSqYujTjw== -----END CERTIFICATE REQUEST----- Fingerprint: 7c:e8:f9:45:93:8d:a3:92:7f:18:29:02:f1:c8:e2:85:3d:ad:df:1f (sha1) 00:4e:df:a0:6b:ad:8c:50:da:7c:a1:cf:5d:37:b0:ea (md5)
The trusted CA digitally signs the local certificate and returns it to you. Copy the certificate file into the router and load the certificate.
user@R3> request security pki local-certificate load filename /tmp/router3-cert certificate-id local-entrust3 Local certificate local-entrust3 loaded successfully
After the local and CA certificates have been loaded, you can reference them in your
IPSec configuration. Using default values in the AS PIC, you do not need to configure an IPSec
proposal or IPSec policy. However, you must configure an IKE proposal that uses digital certificates,
reference the IKE proposal and local certificate in an IKE policy, and apply the CA profile
to the service set. To enable the IKE proposal for digital certificates, include the rsa-signatures statement at the [edit services ipsec-vpn ike proposal proposal-name authentication-method] hierarchy level. To reference the local
certificate in the IKE policy, include the local-certificate statement at the [edit services ipsec-vpn ike policy policy-name] hierarchy level.
To identify the CA or RA in the service set, include the trusted-ca statement at
the [edit services service-set service-set-name ipsec-vpn-options] hierarchy level.
The remaining configuration components of your IKE-based IPsec tunnel are the same as
when you use preshared keys. Enable OSPF as the underlying routing protocol to connect to
Routers 2 and 4. Configure a bidirectional IKE dynamic SA in a rule called rule-ike at the [edit ipsec-vpn rule] hierarchy level. Reference this rule in a service
set called service-set-dynamic-BiEspsha3des at the [edit services service-set] hierarchy level.
To direct traffic into the AS PIC and the IPsec tunnel, configure a next-hop style service set and add the adaptive services logical interface used as the IPsec inside interface into the OSPF configuration.
Router 3
[edit]
interfaces {
so-0/0/0 {
description "To R4 so-0/0/0";
unit 0 {
family inet {
address 10.1.56.1/30;
}
}
}
so-0/0/1 {
description "To R2 so-0/0/1";
unit 0 {
family inet {
address 10.1.15.2/30;
}
}
}
sp-1/2/0 {
unit 0 {
family inet;
}
unit 1 { # sp-1/2/0.1 is the IPSec inside interface.
family inet;
service-domain inside;
}
unit 2 { # sp-1/2/0.2 is the IPSec outside interface.
family inet;
service-domain outside;
}
}
lo0 {
unit 0 {
family inet {
address 10.0.0.3/32;
}
}
}
}
routing-options {
router-id 10.0.0.3;
}
protocols {
ospf {
area 0.0.0.0 {
interface so-0/0/0.0;
interface sp-1/2/0.1; # This sends OSPF traffic over the IPSec tunnel.
interface lo0.0;
}
}
}
security { # Configure CA profiles here, including the URLs used to reach the CAs.
pki {
ca-profile entrust {
ca-identity entrust;
enrollment {
url http://ca-1.example.com/cgi-bin/pkiclient.exe;
}
revocation-check {
crl {
url ldap://10.157.90.185/o=juniper,c=uscertificateRevocationListbase;
# Specify the URL of the LDAP server where the CA stores the CRL.
}
}
}
ca-profile microsoft {
ca-identity microsoft;
enrollment {
url http://192.168.11.78:80/certsrv/mscep/mscep.dll;
}
}
ca-profile verisign {
ca-identity verisign;
enrollment {
url http://pilotonsiteipsec.verisign.com/cgi-bin/pkiclient.exe;
}
}
}
}
services {
service-set service-set-dynamic-BiEspsha3des { # Define your service set here.
next-hop-service { # Required for dynamic routing protocols such as OSPF.
inside-service-interface sp-1/2/0.1;
outside-service-interface sp-1/2/0.2;
}
ipsec-vpn-options {
trusted-ca entrust; # Reference the CA profile here.
local-gateway 10.1.15.2; # Specify the local IP address of the IPSec tunnel.
}
ipsec-vpn-rules rule-ike; # Reference your IPSec VPN rule here.
}
ipsec-vpn {
rule rule-ike { # Define your IPSec VPN rule here.
term term-ike {
then {
remote-gateway 10.1.15.1; # The remote IP address of the IPSec tunnel.
dynamic { # This creates a dynamic SA.
ike-policy ike-digital-certificates; # Reference your IKE policy here.
}
}
}
match-direction input; # Specify in which direction the rule should match.
}
ike {
proposal ike-proposal {
authentication-method rsa-signatures; # Uses digital certificates
}
policy ike-digital-certificates {
proposals ike-proposal; # Apply the IKE proposal here.
local-id fqdn router3.example.com; # Provide an identifier for the local router.
local-certificate local-entrust3; # Reference the local certificate here.
remote-id fqdn router2.example.com; # Provide an ID for the remote router.
}
}
establish-tunnels immediately;
}
}
On Router 4, provide basic OSPF connectivity to Router 3.
Router 4
[edit]
interfaces {
so-0/0/0 {
description "To R3 so-0/0/0";
unit 0 {
family inet {
address 10.1.56.2/30;
}
}
}
lo0 {
unit 0 {
family inet {
address 10.0.0.4/32;
}
}
}
}
routing-options {
router-id 10.0.0.4;
}
protocols {
ospf {
area 0.0.0.0 {
interface so-0/0/0.0;
interface lo0.0;
}
}
}
Verifying Your Work
To verify proper operation of an IKE-based dynamic SA on the AS PIC, use the following commands:
-
ping
-
show services ipsec-vpn certificates (detail) -
show services ipsec-vpn ike security-associations (detail) -
show services ipsec-vpn ipsec security-associations (detail) -
show services ipsec-vpn ipsec statistics -
traceroute
To verify and manage digital certificates in your router, use the following commands:
-
show security pki ca-certificate (detail) -
show security pki certificate-request (detail) -
show security pki local-certificate (detail)
The following sections show the output of these commands used with the configuration example:
Router 1
On Router 1, issue a ping command to the so-0/0/0 interface on Router 4 to send traffic across the IPSec tunnel.
user@R1> ping 10.1.56.2 PING 10.1.56.2 (10.1.56.2): 56 data bytes 64 bytes from 10.1.56.2: icmp_seq=0 ttl=254 time=1.351 ms 64 bytes from 10.1.56.2: icmp_seq=1 ttl=254 time=1.187 ms 64 bytes from 10.1.56.2: icmp_seq=2 ttl=254 time=1.172 ms 64 bytes from 10.1.56.2: icmp_seq=3 ttl=254 time=1.154 ms 64 bytes from 10.1.56.2: icmp_seq=4 ttl=254 time=1.156 ms ^C --- 10.1.56.2 ping statistics --- 5 packets transmitted, 5 packets received, 0% packet loss round-trip min/avg/max/stddev = 1.154/1.204/1.351/0.074 ms
If you ping the loopback address of Router 4, the operation succeeds because the address is part of the OSPF network configured on Router 4.
user@R1> ping 10.0.0.4 PING 10.0.0.4 (10.0.0.4): 56 data bytes 64 bytes from 10.0.0.4: icmp_seq=0 ttl=62 time=1.318 ms 64 bytes from 10.0.0.4: icmp_seq=1 ttl=62 time=1.084 ms 64 bytes from 10.0.0.4: icmp_seq=2 ttl=62 time=3.260 ms ^C --- 10.0.0.4 ping statistics --- 3 packets transmitted, 3 packets received, 0% packet loss round-trip min/avg/max/stddev = 1.084/1.887/3.260/0.975 ms
Router 2
To verify that matched traffic is being diverted to the bidirectional IPSec tunnel, view the IPSec statistics:
user@R2> show services ipsec-vpn ipsec statistics PIC: sp-1/2/0, Service set: service-set-dynamic-BiEspsha3des ESP Statistics: Encrypted bytes: 162056 Decrypted bytes: 161896 Encrypted packets: 2215 Decrypted packets: 2216 AH Statistics: Input bytes: 0 Output bytes: 0 Input packets: 0 Output packets: 0 Errors: AH authentication failures: 0, Replay errors: 0 ESP authentication failures: 0, ESP decryption failures: 0 Bad headers: 0, Bad trailers: 0
To verify that the IKE SA negotiation is successful, issue the show
services ipsec-vpn ike security-associations command:
user@R2> show services ipsec-vpn ike security-associations Remote Address State Initiator cookie Responder cookie Exchange type 10.1.15.2 Matured d82610c59114fd37 ec4391f76783ef28 Main
To verify that the IPsec security association is active, issue the show
services ipsec-vpn ipsec security-associations detail command.
Notice that the SA contains the default settings inherent in the AS PIC, such as
ESP for the protocol and HMAC-SHA1-96 for the authentication algorithm.
user@R2> show services ipsec-vpn ipsec security-associations detail
Service set: service-set-dynamic-BiEspsha3des
Rule: rule-ike, Term: term-ike, Tunnel index: 1
Local gateway: 10.1.15.1, Remote gateway: 10.1.15.2
IPSec inside interface: sp-1/2/0.1
Local identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Remote identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Direction: inbound, SPI: 857451461, AUX-SPI: 0
Mode: tunnel, Type: dynamic, State: Installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: 3des-cbc
Soft lifetime: Expires in 9052 seconds
Hard lifetime: Expires in 9187 seconds
Anti-replay service: Enabled, Replay window size: 64
Direction: outbound, SPI: 1272330309, AUX-SPI: 0
Mode: tunnel, Type: dynamic, State: Installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: 3des-cbc
Soft lifetime: Expires in 9052 seconds
Hard lifetime: Expires in 9187 seconds
Anti-replay service: Enabled, Replay window size: 64
To display the digital certificates that are used to establish the IPSec tunnel, issue the show services ipsec-vpn certificates command:
user@R2> show services ipsec-vpn certificates
Service set: service-set-dynamic-BiEspsha3des, Total entries: 3
Certificate cache entry: 3
Flags: Non-root Trusted
Issued to: router3.example.com, Issued by: juniper
Alternate subject: router3.example.com
Validity:
Not before: 2005 Nov 21st, 23:33:58 GMT
Not after: 2008 Nov 22nd, 00:03:58 GMT
Certificate cache entry: 2
Flags: Non-root Trusted
Issued to: router2.example.com, Issued by: juniper
Alternate subject: router2.example.com
Validity:
Not before: 2005 Nov 21st, 23:28:22 GMT
Not after: 2008 Nov 21st, 23:58:22 GMT
Certificate cache entry: 1
Flags: Root Trusted
Issued to: juniper, Issued by: juniper
Validity:
Not before: 2005 Oct 18th, 23:54:22 GMT
Not after: 2025 Oct 19th, 00:24:22 GMT
To display the CA certificate, issue the show security pki ca-certificate
detail command. Notice that there are three separate certificates:
one for certificate signing, one for key encipherment, and one for the CA’s
digital signature.
user@R2> show security pki ca-certificate detail
Certificate identifier: entrust
Certificate version: 3
Serial number: 4355 9235
Issuer:
Organization: juniper, Country: us
Subject:
Organization: juniper, Country: us
Validity:
Not before: 2005 Oct 18th, 23:54:22 GMT
Not after: 2025 Oct 19th, 00:24:22 GMT
Public key algorithm: rsaEncryption(1024 bits)
cb:9e:2d:c0:70:f8:ea:3c:f2:b5:f0:02:48:87:dc:68:99:a3:57:4f
0e:b9:98:0b:95:47:0d:1f:97:7c:53:17:dd:1a:f8:da:e5:08:d1:1c
78:68:1f:2f:72:9f:a2:cf:81:e3:ce:c5:56:89:ce:f0:97:93:fa:36
19:3e:18:7d:8c:9d:21:fe:1f:c3:87:8d:b3:5d:f3:03:66:9d:16:a7
bf:18:3f:f0:7a:80:f0:62:50:43:83:4f:0e:d7:c6:42:48:c0:8a:b2
c7:46:30:38:df:9b:dc:bc:b5:08:7a:f3:cd:64:db:2b:71:67:fe:d8
04:47:08:07:de:17:23:13
Signature algorithm: sha1WithRSAEncryption
Fingerprint:
00:8e:6f:58:dd:68:bf:25:0a:e3:f9:17:70:d6:61:f3:53:a7:79:10 (sha1)
71:6f:6a:76:17:9b:d6:2a:e7:5a:72:97:82:6d:26:86 (md5)
Distribution CRL:
C=us, O=juniper, CN=CRL1
http://CA-1/CRL/juniper_us_crlfile.crl
Use for key: CRL signing, Certificate signing
Certificate identifier: entrust
Certificate version: 3
Serial number: 4355 925c
Issuer:
Organization: juniper, Country: us
Subject:
Organization: juniper, Country: us, Common name: First Officer
Validity:
Not before: 2005 Oct 18th, 23:55:59 GMT
Not after: 2008 Oct 19th, 00:25:59 GMT
Public key algorithm: rsaEncryption(1024 bits)
c0:a4:21:32:95:0a:cd:ec:12:03:d1:a2:89:71:8e:ce:4e:a6:f9:2f
1a:9a:13:8c:f6:a0:3d:c9:bd:9d:c2:a0:41:77:99:1b:1e:ed:5b:80
34:46:f8:5b:28:34:38:2e:91:7d:4e:ad:14:86:78:67:e7:02:1d:2e
19:11:b7:fa:0d:ba:64:20:e1:28:4e:3e:bb:6e:64:dc:cd:b1:b4:7a
ca:8f:47:dd:40:69:c2:35:95:ce:b8:85:56:d7:0f:2d:04:4d:5d:d8
42:e1:4f:6b:bf:38:c0:45:1e:9e:f0:b4:7f:74:6f:e9:70:fd:4a:78
da:eb:10:27:bd:46:34:33
Signature algorithm: sha1WithRSAEncryption
Fingerprint:
bc:78:87:9b:a7:91:13:20:71:db:ac:b5:56:71:42:ad:1a:b6:46:17 (sha1)
23:79:40:c9:6d:a6:f0:ca:e0:13:30:d4:29:6f:86:79 (md5)
Distribution CRL:
C=us, O=juniper, CN=CRL1
http://CA-1/CRL/juniper_us_crlfile.crl
Use for key: Key encipherment
Certificate identifier: entrust
Certificate version: 3
Serial number: 4355 925b
Issuer:
Organization: juniper, Country: us
Subject:
Organization: juniper, Country: us, Common name: First Officer
Validity:
Not before: 2005 Oct 18th, 23:55:59 GMT
Not after: 2008 Oct 19th, 00:25:59 GMT
Public key algorithm: rsaEncryption(1024 bits)
ea:75:c4:f3:58:08:ea:65:5c:7e:b3:de:63:0a:cf:cf:ec:9a:82:e2
d7:e8:b9:2f:bd:4b:cd:86:2f:f1:dd:d8:a2:95:af:ab:51:a5:49:4e
00:10:c6:25:ff:b5:49:6a:99:64:74:69:e5:8c:23:5b:b4:70:62:8e
e4:f9:a2:28:d4:54:e2:0b:1f:50:a2:92:cf:6c:8f:ae:10:d4:69:3c
90:e2:1f:04:ea:ac:05:9b:3a:93:74:d0:59:24:e9:d2:9d:c2:ef:22
b9:32:c7:2c:29:4f:91:cb:5a:26:fe:1d:c0:36:dc:f4:9c:8b:f5:26
af:44:bf:53:aa:d4:5f:67
Signature algorithm: sha1WithRSAEncryption
Fingerprint:
46:71:15:34:f0:a6:41:76:65:81:33:4f:68:47:c4:df:78:b8:e3:3f (sha1)
ee:cc:c7:f4:5d:ac:65:33:0a:55:db:59:72:2c:dd:16 (md5)
Distribution CRL:
C=us, O=juniper, CN=CRL1
http://CA-1/CRL/juniper_us_crlfile.crl
Use for key: Digital signature
To display the local certificate request, issue the show security pki
certificate-request command:
user@R2> show security pki certificate-request Certificate identifier: local-entrust2 Issued to: router2.example.com Public key algorithm: rsaEncryption(1024 bits) Public key verification status: Passed
To display the local certificate, issue the show security pki
local-certificate command:
user@R2> show security pki local-certificate
Certificate identifier: local-entrust2
Issued to: router2.example.com, Issued by: juniper
Validity:
Not before: 2005 Nov 21st, 23:28:22 GMT
Not after: 2008 Nov 21st, 23:58:22 GMT
Public key algorithm: rsaEncryption(1024 bits)
Public key verification status: Passed
Router 3
To verify that matched traffic is being diverted to the bidirectional IPSec tunnel, view the IPSec statistics:
user@R3> show services ipsec-vpn ipsec statistics PIC: sp-1/2/0, Service set: service-set-dynamic-BiEspsha3des ESP Statistics: Encrypted bytes: 161896 Decrypted bytes: 162056 Encrypted packets: 2216 Decrypted packets: 2215 AH Statistics: Input bytes: 0 Output bytes: 0 Input packets: 0 Output packets: 0 Errors: AH authentication failures: 0, Replay errors: 0 ESP authentication failures: 0, ESP decryption failures: 0 Bad headers: 0, Bad trailers: 0
To verify that the IKE SA negotiation is successful, issue the show
services ipsec-vpn ike security-associations command. To be
successful, the SA on Router 3 must contain the same settings you specified on
Router 2.
user@R3> show services ipsec-vpn ike security-associations Remote Address State Initiator cookie Responder cookie Exchange type 10.1.15.1 Matured d82610c59114fd37 ec4391f76783ef28 Main
To verify that the IPsec SA is active, issue the show services ipsec-vpn
ipsec security-associations detail command. To be successful, the
SA on Router 3 must contain the same settings you specified on Router 2.
user@R3> show services ipsec-vpn ipsec security-associations detail
Service set: service-set-dynamic-BiEspsha3des
Rule: rule-ike, Term: term-ike, Tunnel index: 1
Local gateway: 10.1.15.2, Remote gateway: 10.1.15.1
IPSec inside interface: sp-1/2/0.1
Local identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Remote identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Direction: inbound, SPI: 1272330309, AUX-SPI: 0
Mode: tunnel, Type: dynamic, State: Installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: 3des-cbc
Soft lifetime: Expires in 7219 seconds
Hard lifetime: Expires in 7309 seconds
Anti-replay service: Enabled, Replay window size: 64
Direction: outbound, SPI: 857451461, AUX-SPI: 0
Mode: tunnel, Type: dynamic, State: Installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: 3des-cbc
Soft lifetime: Expires in 7219 seconds
Hard lifetime: Expires in 7309 seconds
Anti-replay service: Enabled, Replay window size: 64
To display the digital certificates that are used to establish the IPsec tunnel,
issue the show services ipsec-vpn certificates command:
user@R3> show services ipsec-vpn certificates
Service set: service-set-dynamic-BiEspsha3des, Total entries: 3
Certificate cache entry: 3
Flags: Non-root Trusted
Issued to: router3.example.com, Issued by: juniper
Alternate subject: router3.example.com
Validity:
Not before: 2005 Nov 21st, 23:33:58 GMT
Not after: 2008 Nov 22nd, 00:03:58 GMT
Certificate cache entry: 2
Flags: Non-root Trusted
Issued to: router2.example.com, Issued by: juniper
Alternate subject: router2.example.com
Validity:
Not before: 2005 Nov 21st, 23:28:22 GMT
Not after: 2008 Nov 21st, 23:58:22 GMT
Certificate cache entry: 1
Flags: Root Trusted
Issued to: juniper, Issued by: juniper
Validity:
Not before: 2005 Oct 18th, 23:54:22 GMT
Not after: 2025 Oct 19th, 00:24:22 GMT
To display the CA certificate, issue the show security pki ca-certificate
detail command. Notice that there are three separate certificates:
one for certificate signing, one for key encipherment, and one for the CA’s
digital signature.
user@R3> show security pki ca-certificate detail
Certificate identifier: entrust
Certificate version: 3
Serial number: 4355 9235
Issuer:
Organization: juniper, Country: us
Subject:
Organization: juniper, Country: us
Validity:
Not before: 2005 Oct 18th, 23:54:22 GMT
Not after: 2025 Oct 19th, 00:24:22 GMT
Public key algorithm: rsaEncryption(1024 bits)
cb:9e:2d:c0:70:f8:ea:3c:f2:b5:f0:02:48:87:dc:68:99:a3:57:4f
0e:b9:98:0b:95:47:0d:1f:97:7c:53:17:dd:1a:f8:da:e5:08:d1:1c
78:68:1f:2f:72:9f:a2:cf:81:e3:ce:c5:56:89:ce:f0:97:93:fa:36
19:3e:18:7d:8c:9d:21:fe:1f:c3:87:8d:b3:5d:f3:03:66:9d:16:a7
bf:18:3f:f0:7a:80:f0:62:50:43:83:4f:0e:d7:c6:42:48:c0:8a:b2
c7:46:30:38:df:9b:dc:bc:b5:08:7a:f3:cd:64:db:2b:71:67:fe:d8
04:47:08:07:de:17:23:13
Signature algorithm: sha1WithRSAEncryption
Fingerprint:
00:8e:6f:58:dd:68:bf:25:0a:e3:f9:17:70:d6:61:f3:53:a7:79:10 (sha1)
71:6f:6a:76:17:9b:d6:2a:e7:5a:72:97:82:6d:26:86 (md5)
Distribution CRL:
C=us, O=juniper, CN=CRL1
http://CA-1/CRL/juniper_us_crlfile.crl
Use for key: CRL signing, Certificate signing
Certificate identifier: entrust
Certificate version: 3
Serial number: 4355 925c
Issuer:
Organization: juniper, Country: us
Subject:
Organization: juniper, Country: us, Common name: First Officer
Validity:
Not before: 2005 Oct 18th, 23:55:59 GMT
Not after: 2008 Oct 19th, 00:25:59 GMT
Public key algorithm: rsaEncryption(1024 bits)
c0:a4:21:32:95:0a:cd:ec:12:03:d1:a2:89:71:8e:ce:4e:a6:f9:2f
1a:9a:13:8c:f6:a0:3d:c9:bd:9d:c2:a0:41:77:99:1b:1e:ed:5b:80
34:46:f8:5b:28:34:38:2e:91:7d:4e:ad:14:86:78:67:e7:02:1d:2e
19:11:b7:fa:0d:ba:64:20:e1:28:4e:3e:bb:6e:64:dc:cd:b1:b4:7a
ca:8f:47:dd:40:69:c2:35:95:ce:b8:85:56:d7:0f:2d:04:4d:5d:d8
42:e1:4f:6b:bf:38:c0:45:1e:9e:f0:b4:7f:74:6f:e9:70:fd:4a:78
da:eb:10:27:bd:46:34:33
Signature algorithm: sha1WithRSAEncryption
Fingerprint:
bc:78:87:9b:a7:91:13:20:71:db:ac:b5:56:71:42:ad:1a:b6:46:17 (sha1)
23:79:40:c9:6d:a6:f0:ca:e0:13:30:d4:29:6f:86:79 (md5)
Distribution CRL:
C=us, O=juniper, CN=CRL1
http://CA-1/CRL/juniper_us_crlfile.crl
Use for key: Key encipherment
Certificate identifier: entrust
Certificate version: 3
Serial number: 4355 925b
Issuer:
Organization: juniper, Country: us
Subject:
Organization: juniper, Country: us, Common name: First Officer
Validity:
Not before: 2005 Oct 18th, 23:55:59 GMT
Not after: 2008 Oct 19th, 00:25:59 GMT
Public key algorithm: rsaEncryption(1024 bits)
ea:75:c4:f3:58:08:ea:65:5c:7e:b3:de:63:0a:cf:cf:ec:9a:82:e2
d7:e8:b9:2f:bd:4b:cd:86:2f:f1:dd:d8:a2:95:af:ab:51:a5:49:4e
00:10:c6:25:ff:b5:49:6a:99:64:74:69:e5:8c:23:5b:b4:70:62:8e
e4:f9:a2:28:d4:54:e2:0b:1f:50:a2:92:cf:6c:8f:ae:10:d4:69:3c
90:e2:1f:04:ea:ac:05:9b:3a:93:74:d0:59:24:e9:d2:9d:c2:ef:22
b9:32:c7:2c:29:4f:91:cb:5a:26:fe:1d:c0:36:dc:f4:9c:8b:f5:26
af:44:bf:53:aa:d4:5f:67
Signature algorithm: sha1WithRSAEncryption
Fingerprint:
46:71:15:34:f0:a6:41:76:65:81:33:4f:68:47:c4:df:78:b8:e3:3f (sha1)
ee:cc:c7:f4:5d:ac:65:33:0a:55:db:59:72:2c:dd:16 (md5)
Distribution CRL:
C=us, O=juniper, CN=CRL1
http://CA-1/CRL/juniper_us_crlfile.crl
Use for key: Digital signature
To display the local certificate request, issue the show security pki certificate-request command:
user@R3> show security pki certificate-request Certificate identifier: local-entrust3 Issued to: router3.example.com Public key algorithm: rsaEncryption(1024 bits) Public key verification status: Passed
To display the local certificate, issue the show security pki
local-certificate command:
user@R3> show security pki local-certificate
Certificate identifier: local-entrust3
Issued to: router3.example.com, Issued by: juniper
Validity:
Not before: 2005 Nov 21st, 23:33:58 GMT
Not after: 2008 Nov 22nd, 00:03:58 GMT
Public key algorithm: rsaEncryption(1024 bits)
Public key verification status: Passed
Router 4
On Router 4, issue a ping command to the
so-0/0/0 interface on Router 1 to send traffic across
the IPsec tunnel.
user@R4> ping 10.1.12.2 PING 10.1.12.2 (10.1.12.2): 56 data bytes 64 bytes from 10.1.12.2: icmp_seq=0 ttl=254 time=1.350 ms 64 bytes from 10.1.12.2: icmp_seq=1 ttl=254 time=1.161 ms 64 bytes from 10.1.12.2: icmp_seq=2 ttl=254 time=1.124 ms 64 bytes from 10.1.12.2: icmp_seq=5 ttl=254 time=1.116 ms ^C --- 10.1.12.2 ping statistics --- 4 packets transmitted, 4 packets received, 0% packet loss round-trip min/avg/max/stddev = 1.116/1.172/1.350/0.081 ms
The final way you can confirm that traffic travels over the IPsec tunnel is by
issuing the traceroute command to the
so-0/0/0 interface on Router 1. Notice that the
physical interface between Routers 2 and 3 is not referenced in the path;
traffic enters the IPSec tunnel through the adaptive services IPSec inside
interface on Router 3, passes through the loopback interface on Router 2, and
ends at the so-0/0/0 interface on Router 1.
user@R4> traceroute 10.1.12.2 traceroute to 10.1.12.2 (10.1.12.2), 30 hops max, 40 byte packets 1 10.1.15.2 (10.1.15.2) 0.987 ms 0.630 ms 0.563 ms 2 10.0.0.2 (10.0.0.2) 1.194 ms 1.058 ms 1.033 ms 3 10.1.12.2 (10.1.12.2) 1.073 ms 0.949 ms 0.932 ms
For additional information on using digital certificates, see the Junos Services Interfaces Configuration Guide and the Junos System Basics and Services Command Reference.
