Example: ES PIC Manual SA Configuration
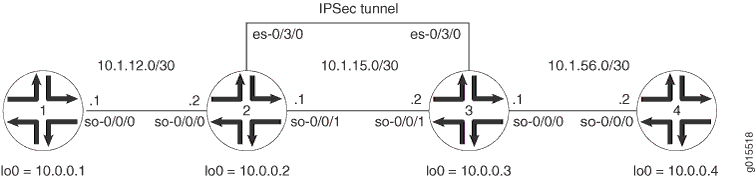
Figure 1 shows an IPSec topology containing a group of four routers. Routers 2 and 3 establish an IPSec tunnel using an ES PIC and manual SA settings. Routers 1 and 4 provide basic connectivity and are used to verify that the IPSec tunnel is operational.
On Router 1, provide basic OSPF connectivity to Router 2.
Router 1
[edit]
interfaces {
so-0/0/0 {
description "To R2 so-0/0/0";
unit 0 {
family inet {
address 10.1.12.2/30;
}
}
}
lo0 {
unit 0 {
family inet {
address 10.0.0.1/32;
}
}
}
}
routing-options {
router-id 10.0.0.1;
}
protocols {
ospf {
area 0.0.0.0 {
interface so-0/0/0.0;
interface lo0.0;
}
}
}
On Router 2, enable OSPF as the underlying routing protocol to connect to Routers 1 and 3. Configure a bidirectional manual SA called sa-manual at
the [edit security ipsec security-association] hierarchy level. Use AH for the protocol, 400 for the SPI, HMAC-MD5-96 for authentication,
and a 32-bit hexadecimal authentication key for the MD5 authentication key. (For more information about key length, see Authentication and Encryption Key Lengths.) Because you are using AH, there is no need to configure
encryption.
To direct traffic into the ES PIC and the IPSec tunnel, create two firewall filters. The es-traffic filter matches inbound traffic from Router 1 destined for Router 4, whereas the es-return filter matches the return path from Router 4 to Router 1. Apply the es-traffic filter to the so-0/0/0 interface; then apply both the es-return filter and the sa-manual SA to the es-0/3/0 interface.
Router 2
[edit]
interfaces {
so-0/0/0 {
description "To R1 so-0/0/0";
unit 0 {
family inet {
filter {
input es-traffic; # Apply a filter that sends traffic to the IPSec tunnel here.
}
address 10.1.12.1/30;
}
}
}
so-0/0/1 {
description "To R3 so-0/0/1";
unit 0 {
family inet {
address 10.1.15.1/30;
}
}
}
es-0/3/0 {
unit 0 {
tunnel { # Specify the IPSec tunnel endpoints here.
source 10.1.15.1;
destination 10.1.15.2;
}
family inet {
ipsec-sa sa-manual; # Apply the manual SA here.
filter {
input es-return; # Apply the filter that matches return IPSec traffic here.
}
}
}
}
lo0 {
unit 0 {
family inet {
address 10.0.0.2/32;
}
}
}
}
routing-options {
router-id 10.0.0.2;
}
protocols {
ospf {
area 0.0.0.0 {
interface so-0/0/0.0;
interface so-0/0/1.0;
interface lo0.0;
}
}
}
security {
ipsec {
security-association sa-manual { # Define the manual SA specifications here.
mode tunnel;
manual {
direction bidirectional {
protocol ah;
spi 400;
authentication {
algorithm hmac-md5-96;
key hexadecimal "$ABC123”;
}
}
}
}
}
}
# The 32-bit unencrypted hexadecimal key is abcdef01abcdef01abcdef01abcdef01.
firewall {
filter es-traffic { # Define a filter that sends traffic to the IPSec tunnel here.
term to-es {
from {
source-address {
10.1.12.0/24;
}
destination-address {
10.1.56.0/24;
}
}
then {
count ipsec-tunnel;
ipsec-sa sa-manual;
}
}
term other {
then accept;
}
}
filter es-return { # Define a filter that matches return IPSec traffic here.
term return {
from {
source-address {
10.1.56.0/24;
}
destination-address {
10.1.12.0/24;
}
}
then accept;
}
}
}
On Router 3, enable OSPF as the underlying routing protocol to connect to Routers 2 and 4. Configure a bidirectional manual SA called sa-manual at the [edit security ipsec security-association] hierarchy level. Use the exact same specifications that you used for the SA on Router 2: AH for the protocol, 400 for the SPI, HMAC-MD5-96 for authentication, and a 32-bit hexadecimal authentication key of abcdef01abcdef01abcdef01abcdef01 for the MD5 authentication key. (For more information about authentication key length, see Authentication and Encryption Key Lengths.) Because you are using AH, there is no need to configure an encryption algorithm.
To direct traffic into the ES PIC and the IPSec tunnel, create two firewall filters. The es-traffic filter matches inbound traffic from Router 4 destined for Router 1, whereas the es-return filter matches the return path from Router 1 to Router 4. Apply the es-traffic filter to the so-0/0/0 interface; then apply both the es-return filter and the sa-manual SA to the es-0/3/0 interface.
Router 3
[edit]
interfaces {
so-0/0/0 {
description "To R4 so-0/0/0";
unit 0 {
family inet {
filter {
input es-traffic; # Apply a filter that sends traffic to the IPSec tunnel here.
}
address 10.1.56.1/30;
}
}
}
so-0/0/1 {
description "To R2 so-0/0/1";
unit 0 {
family inet {
address 10.1.15.2/30;
}
}
}
es-0/3/0 {
unit 0 {
tunnel { # Specify the IPSec tunnel endpoints here.
source 10.1.15.2;
destination 10.1.15.1;
}
family inet {
ipsec-sa sa-manual; # Apply the manual SA here.
filter {
input es-return; # Apply the filter that matches return IPSec traffic here.
}
}
}
}
lo0 {
unit 0 {
family inet {
address 10.0.0.3/32;
}
}
}
}
routing-options {
router-id 10.0.0.3;
}
protocols {
ospf {
area 0.0.0.0 {
interface so-0/0/0.0;
interface so-0/0/1.0;
interface lo0.0;
}
}
}
security {
ipsec {
security-association sa-manual { # Define the manual SA specifications here.
mode tunnel;
manual {
direction bidirectional {
protocol ah;
spi 400;
authentication {
algorithm hmac-md5-96;
key hexadecimal "$ABC123”;
}
}
}
}
}
}
## The 32-bit unencrypted hexadecimal key is abcdef01abcdef01abcdef01abcdef01.
firewall {
filter es-traffic { # Define a filter that sends traffic to the IPSec tunnel here.
term to-es {
from {
source-address {
10.1.56.0/24;
}
destination-address {
10.1.12.0/24;
}
}
then {
count ipsec-tunnel;
ipsec-sa sa-manual;
}
}
term other {
then accept;
}
}
filter es-return { # Define a filter that matches return IPSec traffic here.
term return {
from {
source-address {
10.1.12.0/24;
}
destination-address {
10.1.56.0/24;
}
}
then accept;
}
}
}
On Router 4, provide basic OSPF connectivity to Router 3.
Router 4
[edit]
interfaces {
so-0/0/0 {
description "To R3 so-0/0/0";
unit 0 {
family inet {
address 10.1.56.2/30;
}
}
}
lo0 {
unit 0 {
family inet {
address 10.0.0.4/32;
}
}
}
}
routing-options {
router-id 10.0.0.4;
}
protocols {
ospf {
area 0.0.0.0 {
interface so-0/0/0.0;
interface lo0.ping
}
}
}
Verifying Your Work
To verify proper operation of a manual IPSec SA on the ES PIC, use the following commands:
-
ping
-
show ipsec security-associations (detail) -
traceroute
The following sections show the output of these commands used with the configuration example:
Router 1
On Router 1, issue a ping command to the
so-0/0/0 interface of Router 4 to send traffic across
the IPsec tunnel.
user@R1> ping 10.1.56.2 PING 10.1.56.2 (10.1.56.2): 56 data bytes 64 bytes from 10.1.56.2: icmp_seq=0 ttl=253 time=0.939 ms 64 bytes from 10.1.56.2: icmp_seq=1 ttl=253 time=0.886 ms 64 bytes from 10.1.56.2: icmp_seq=2 ttl=253 time=0.826 ms ^C --- 10.1.56.2 ping statistics --- 3 packets transmitted, 3 packets received, 0% packet loss round-trip min/avg/max/stddev = 0.826/0.884/0.939/0.046 ms
You can also issue the traceroute command to verify that traffic
to 10.1.56.2 travels over the IPsec tunnel between Router
2 and Router 3. Notice that the second hop does not reference
10.1.15.2—the physical interface on Router 3.
Instead, the loopback address of 10.0.0.3 on Router 3
appears as the second hop. This indicates that the IPSec tunnel is operating
correctly.
user@R1> traceroute 10.1.56.2 traceroute to 10.1.56.2 (10.1.56.2), 30 hops max, 40 byte packets 1 10.1.12.1 (10.1.12.1) 0.655 ms 0.549 ms 0.508 ms 2 10.0.0.3 (10.0.0.3) 0.833 ms 0.786 ms 0.757 ms 3 10.1.56.2 (10.1.56.2) 0.808 ms 0.741 ms 0.716 ms
Router 2
Another way to verify that matched traffic is being diverted to the bidirectional
IPsec tunnel is to view the firewall filter counter. After you issue the
ping command from Router 1 (three packets), the
es-traffic firewall filter counter looks like
this:
user@R2> show firewall filter es-traffic Filter: es-traffic Counters: Name Bytes Packets ipsec-tunnel 252 3
After you issue the ping command from both Router 1 (three
packets) and Router 4 (two packets), the es-traffic
firewall filter counter looks like this:
user@R2> show firewall filter es-traffic Filter: es-traffic Counters: Name Bytes Packets ipsec-tunnel 420 5
To verify that the IPsec security association is active, issue the show
ipsec security-associations detail command. Notice that the SA
contains the settings you specified, such as AH for the protocol and HMAC-MD5-96
for the authentication algorithm.
user@R2> show ipsec security-associations detail
Security association: sa-manual, Interface family: Up
Local gateway: 10.1.15.1, Remote gateway: 10.1.15.2
Local identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Remote identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Direction: inbound, SPI: 400, AUX-SPI: 0
Mode: tunnel, Type: manual, State: Installed
Protocol: AH, Authentication: hmac-md5-96, Encryption: None
Anti-replay service: Disabled
Direction: outbound, SPI: 400, AUX-SPI: 0
Mode: tunnel, Type: manual, State: Installed
Protocol: AH, Authentication: hmac-md5-96, Encryption: None
Anti-replay service: Disabled
Router 3
View the firewall filter counter to continue verifying that matched traffic is
being diverted to the bidirectional IPsec tunnel. After you issue the
ping command from Router 1 (three packets), the
es-traffic firewall filter counter looks like
this:
user@R3> show firewall filter es-traffic Filter: es-traffic Counters: Name Bytes Packets ipsec-tunnel 252 3
After you issue the ping command from both Router 1 (three
packets) and Router 4 (two packets), the es-traffic
firewall filter counter looks like this:
user@R3> show firewall filter es-traffic Filter: es-traffic Counters: Name Bytes Packets ipsec-tunnel 420 5
To verify that the IPsec security association is active, issue the show
ipsec security-associations detail command. Notice that the SA on
Router 3 contains the same settings you specified on Router 2.
user@R3> show ipsec security-associations detail
Security association: sa-manual, Interface family: Up
Local gateway: 10.1.15.2, Remote gateway: 10.1.15.1
Local identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Remote identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Direction: inbound, SPI: 400, AUX-SPI: 0
Mode: tunnel, Type: manual, State: Installed
Protocol: AH, Authentication: hmac-md5-96, Encryption: None
Anti-replay service: Disabled
Direction: outbound, SPI: 400, AUX-SPI: 0
Mode: tunnel, Type: manual, State: Installed
Protocol: AH, Authentication: hmac-md5-96, Encryption: None
Anti-replay service: Disabled
Router 4
On Router 4, issue a ping command to the
so-0/0/0 interface of Router 1 to send traffic across
the IPsec tunnel.
user@R4> ping 10.1.12.2 PING 10.1.12.2 (10.1.12.2): 56 data bytes 64 bytes from 10.1.12.2: icmp_seq=0 ttl=253 time=0.937 ms 64 bytes from 10.1.12.2: icmp_seq=1 ttl=253 time=0.872 ms ^C --- 10.1.12.2 ping statistics --- 2 packets transmitted, 2 packets received, 0% packet loss round-trip min/avg/max/stddev = 0.872/0.905/0.937/0.032 ms
You can also issue the traceroute command to verify that traffic
to 10.1.12.2 travels over the IPsec tunnel between Router
3 and Router 2. Notice that the second hop does not reference
10.1.15.1—the physical interface on Router 2.
Instead, the loopback address of 10.0.0.2 on Router 2
appears as the second hop. This indicates that the IPSec tunnel is operating
correctly.
user@R4> traceroute 10.1.12.2 traceroute to 10.1.12.2 (10.1.12.2), 30 hops max, 40 byte packets 1 10.1.56.1 (10.1.56.1) 0.670 ms 0.589 ms 0.548 ms 2 10.0.0.2 (10.0.0.2) 0.815 ms 0.791 ms 0.763 ms 3 10.1.12.2 (10.1.12.2) 0.798 ms 0.741 ms 0.714 ms
