HTTP File Download Details
To access this page, navigate to . Click the Signature ID link to go to the File Download Details page.
Use this page to view general, static analysis, behavior analysis, network activity, and malware behavior summaries for the downloaded file. This page is divided into several sections:
|
Button/Link |
Purpose |
|---|---|
|
Report False Positive |
Click this button to launch a new screen which lets you send a report to Juniper Networks, informing Juniper of a false position or a false negative. Juniper will investigate the report, however, this investigation does not change the verdict. If you want to make a correction (mark system as clean), you must do it manually. |
|
Download STIX Report |
When there is a STIX report available, a download link appears on this page. Click the link to view gathered, open-source threat information, such as blocklisted files, addresses and URLs. STIX (Structured Threat Information eXpression) is a language used for reporting and sharing threat information using TAXII (Trusted Automated eXchange of Indicator Information). TAXII is the protocol for communication over HTTPS of threat information between parties. STIX and TAXII are an open community-driven effort of specifications that assist with the automated exchange of threat information. This allows threat information to be represented in a standardized format for sharing and consuming. Juniper ATP Cloud uses this information as well as other sources. This occurs automatically. There is no administrator configuration required for STIX. STIX reports will vary. View a sample report at the bottom of this page. Note:
Juniper ATP Cloud can also share threat intelligence. You can control what threat information is shared from the Threat Sharing page. See Configure Threat Intelligence Sharing. |
|
Download Zipped Files |
(When available) Click this link to download the quarantined malware for analysis. The link allows you to download a password-protected zipped file containing the malware. The password for the zip file is the SHA256 hash of the malware exe file (64 characters long, alpha numeric string) shown in the General tab in the Juniper ATP Cloud UI for the file in question. |
|
Download PDF Report |
Click this link to download a detailed report on the file in question. The report provides details on file threat level, protocol seen, and file category and size. It also includes client IP address, username, and additional information, if available. This data is provided in a formatted PDF with a TOC. |
The top of the page provides a quick view of the following information (scroll to the right in the UI to see more boxes):
-
Threat Level—This is the threat level assigned (0-10), This box also provides the filename, and threat category.
-
Top Indicators—In this box, you will find the malware name, the signature it matches, antivirus state, and the IP address/URL from which the file originated.
-
Prevalence—This box provides information about how often this malware has been seen, how many individual hosts on the network downloaded the file, and the protocol used.
File Summary
|
Field |
Definition |
|---|---|
|
Threat Level |
This is the assigned threat level 0-10. 10 is the most malicious. |
|
Global Prevalence |
How often this file has been seen across different customers. |
|
Last Scanned |
The time and date of the last scan to detect the suspicious file |
|
File Name |
The name of the suspicious file. Examples: unzipper-setup.exe, 20160223158005.exe, wordmui.msi. |
|
Category |
The type of file Examples: PDF, executable, document |
|
Size |
The size of the downloaded file. |
|
Platform |
The target OS of the file Example: Win32 |
|
Malware Name |
If possible, Juniper ATP Cloud determines the name of the malware. |
|
Type |
If possible, Juniper ATP Cloud determines the type of threat. Example: Trojan, Application, Adware. |
|
Strain |
If possible, Juniper ATP Cloud determines the strain of malware detected. Example: Outbrowse.1198, Visicom.E, Flystudio |
|
sha256 and md5 |
One way to determine whether a file is malware is to calculate a checksum for the file and then query to see if the file has previously been identified as malware. |
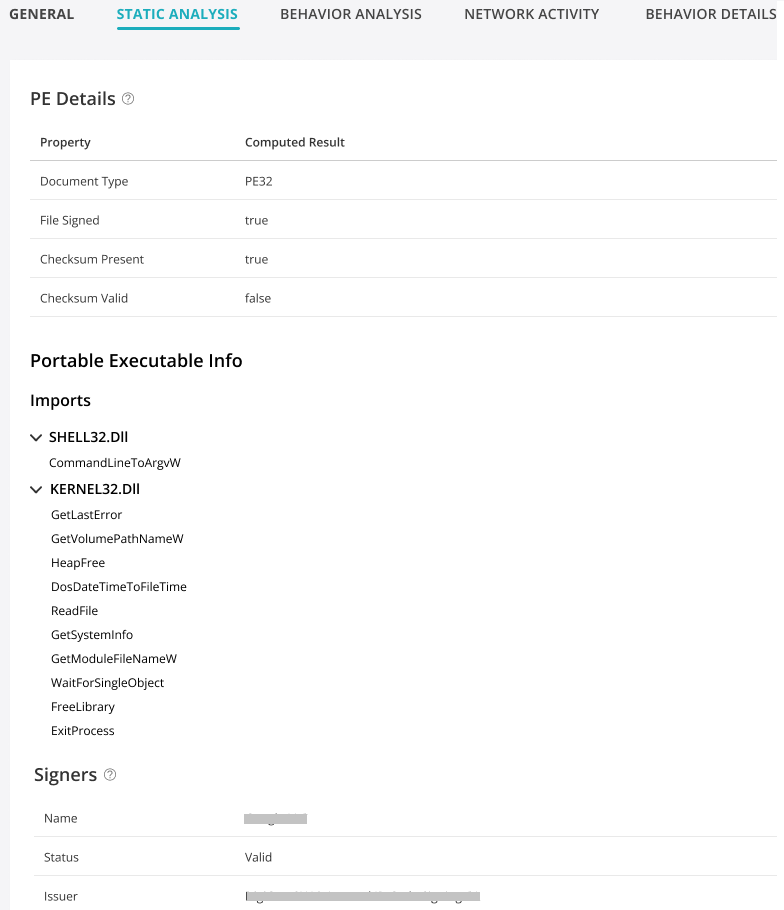
Static Analysis
Juniper ATP Cloud provides static file information such as document type, certificate details, signer information and so on for explaining potential sample capabilities.
Behavior Analysis
Juniper ATP Cloud provides network behavioral analysis and machine learning (ML) to determine if an encrypted or non-encrypted connection is benign or malicious. Please note that the SSL proxy is needed to decrypt the traffic for detection.
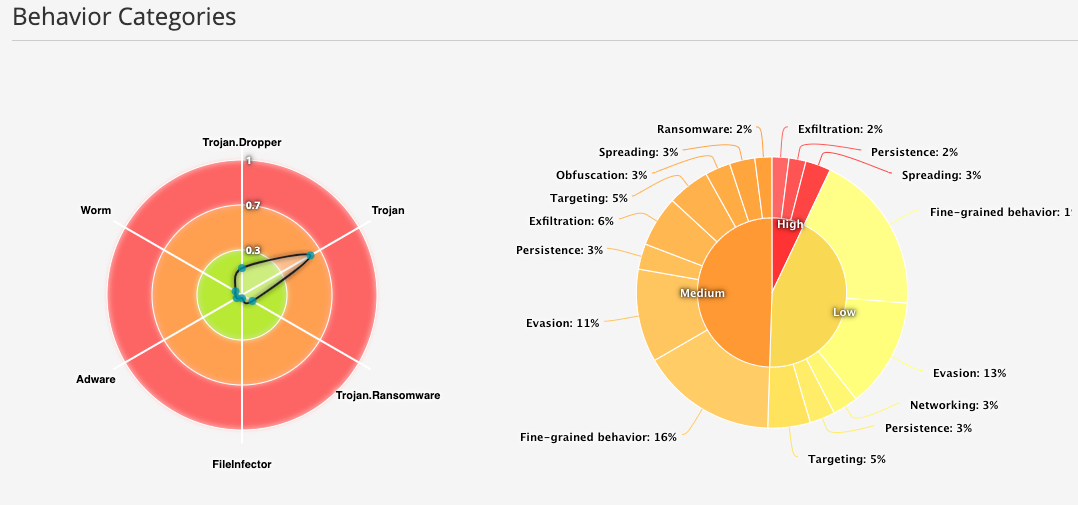
Behavior analysis tab displays the file execution behavior trends in a radar chart with malware categories or behaviors on each axis. This data helps us better identify the category of a malware and map that category to a severity.
The malware priority is classified into low, medium, and high.
In Figure 2 the radar chart on the left contains the probability of the sample that it belongs to one of these mentioned malware types. The shape point towards one specific malware type, in this case, Trojan. This indicates that the sample’s malware type is most probably Trojan. Note that this graph Figure 2 may not exist for some possibly malicious samples after sandboxing. In the chart, green indicates clean in that category, orange indicates suspicious in that category, and red indicates malicious malware in that category.
|
Behavior Category |
Sample Behavior Definition |
|---|---|
|
Targeting |
Checks volume information |
|
Fine-grained Behavior |
Contains code to communicate with device drivers. Contains code to delete services. Memory allocated in system DLL range. |
|
Obfuscation |
Utilizes known code obfuscation techniques. |
|
Evasion |
Contains code to detect VMs. Contains large amount of unused code (likely obfuscated code). Contains code to determine API calls at runtime. |
|
Persistence |
Modifies registry keys to run application during startup. |
|
Networking |
Memory or binary contains Internet addresses. |
HTTP Downloads
This section displays the list of hosts that have downloaded the suspicious file. Click the IP address to be taken to the Host Details page for this host. Click the Device Serial number to be taken to the Devices page. From there you can view device versions and version numbers for the Juniper ATP Cloud configuration, including profile, allowlist, and blocklist versions. You can also view the malware detection connection type for the device: telemetry, submission, or C&C event.
Network Activity
In the Network Activity section, you can view information in the following tabs:
-
Contacted Domains—If available, lists any domains that were contacted while executing the file in the Juniper ATP Cloud sandbox.
-
Contacted IPs—If available, lists all IPs that were contacted while executing the file, along with the destination IP’s country, ASN, and reputation. The reputation field is based on Juniper IP intelligence data destination.
-
DNS Activity— This tab lists DNS activity while executing the file, including reverse lookup to find the domain name of externally contacted servers. This tab also provides the known reputation of the destination servers.
Behavior Details
The behavior details tab displays information about suspicious activities and process details captured during the behavioral analysis. For example, if malware drops an executable file and starts a new process, these details are displayed under the behavioral details tab. Screenshots of behavioral analysis windows are also shown for the malware analysis that occurred inside the sandbox. This helps you determine whether the file is malware. If the analyzed file is ransomware, you might see its ransom message or other information displayed during the analysis in the screenshot.
Please note that the screenshots are available only for the newly analyzed files.
Sample STIX Report

