Reverse Shell Overview
A reverse shell allows the attacker to bypass firewalls and other security mechanisms to open the ports to the target system.
When an attacker exploits a code execution vulnerability on the target system, they will run a script that starts a reverse shell session to the Command and Control (C&C) server. It gives them remote access to the compromised system. The attackers can run any command they want and obtain its output from the system. SRX Series Firewall will analyze the traffic pattern between the client and the server over a brief period to identify the reverse shell sessions. It will then take the configured remedial action.
Benefits of reverse shell detection
Helps you to detect shell attacks and prevent potential data thefts.
To access the Reverse Shell page, navigate to .
This page provides a list of destination IP addresses, destination ports, source IP addresses and source ports that were part of the reverse shell communication. See Figure 1.
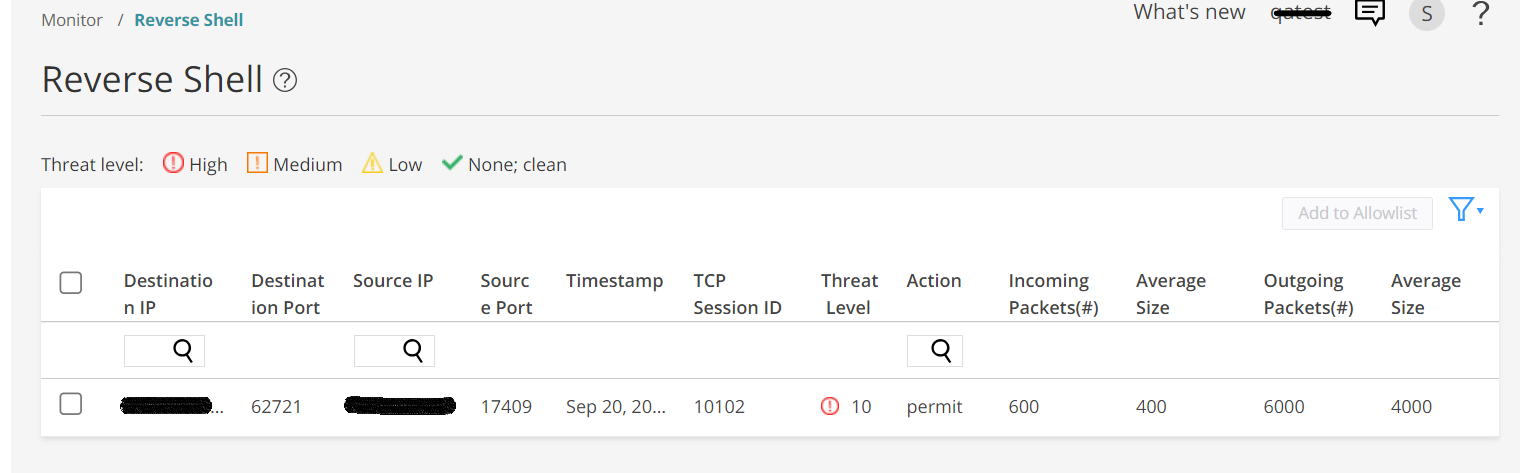
| Field | Definition |
|---|---|
| Destination IP | The IP address of the attacker's C&C server |
| Destination Port | The port of the attacker's C&C server |
| Source IP | The IP address of the target system in reverse shell session. |
| Source Port | The port the attackers used to attempt reverse shell communication. |
| Timestamp | Date and time the reverse shell session is started. |
| TCP Session ID | The session ID assigned to the attacker's C&C server |
| Threat Level | The threat level of the attacker's C&C server based on the analysis. |
| Action | The action taken on the reverse shell session: permit or block. |
| Incoming Packets(#) | The number of incoming packets to the target system. |
| Average Size | The average size of the incoming packets. |
| Outgoing Packets(#) | The number of outgoing packets from the target system. |
| Average Size | The average size of the outgoing packets. |
You can select and add the destination IP addresses to the allowlists if they are not malicious. To add the destination IP address to the allowlists:
-
Select .
The Reverse Shell page appears.
-
Select the destination IP address that you want to add to the allowlists and then click Add to Allowlist.
A pop-up appears asking you to confirm the selection.
-
Click Yes.
The selected destination IP address is added to the allowlists.
For information about configuring the reverse shell detection on SRX Series Firewalls, see Juniper Advanced Threat Prevention Administrator Guide.
