Example: Configuring TWAMP Client and Server for SRX Series Firewalls
This example shows how to configure the Two-Way Active Measurement Protocol (TWAMP) client and TWAMP server.
Our content testing team has validated and updated this example.
Requirements
This example uses the following hardware and software components:
-
SRX Series Firewall.
-
Junos OS Release 18.1R1 and later releases.
-
Updated and revalidated using vMX on Junos OS Release 22.2R1.
-
Before you begin configuring TWAMP client and TWAMP server, ensure that you have read Understand Two-Way Active Measurement Protocol to understand how this task fits into the overall configuration process.
Overview
The TWAMP is an open protocol for measuring network performance between any two devices in a network that supports the TWAMP protocol. The TWAMP consists of TWAMP-Control protocol and TWAMP-Test protocol. The TWAMP-Control protocol is used to initiate, start and stop the test sessions between the control client. The TWAMP-Test protocol used to exchange the test packets between the session sender and the session reflector.
Figure 1 shows the TWAMP architecture composed of the following entities that are responsible for starting a monitoring session and exchanging packets:
-
The control client initiates all requested test sessions with a start sessions message, and the TWAMP server acknowledges. When necessary, the control client sends a message to stop all test sessions.
-
The session sender and the session reflector exchange test packets according to the TWAMP-Test protocol for each active session. On receiving a TWAMP-Test packet, the session reflector reflects a measurement packet and does not collect any packet statistics in TWAMP.
The TWAMP server is an end system that manages one or more TWAMP sessions and capable of configuring per-session ports. The TWAMP server listens to the TCP port. The session reflector and TWAMP server make up the TWAMP responder in an IP service-level agreement operation.
For Junos OS Release 18.1R1, both the control client and session sender resides on the same device. The client design does not mandate the TWAMP server and the session reflector to be on the same system. Hence, the Juniper TWAMP client is also capable of working with a third-party server implementation.
Configuring the TWAMP Client for SRX Series Firewalls
CLI Quick Configuration
To quickly configure this example, copy the following commands, paste them into a text file, remove any line breaks, change any details necessary to match your network configuration, copy and paste the commands into the CLI, at the [edit] hierarchy level, and then enter commit from configuration mode.
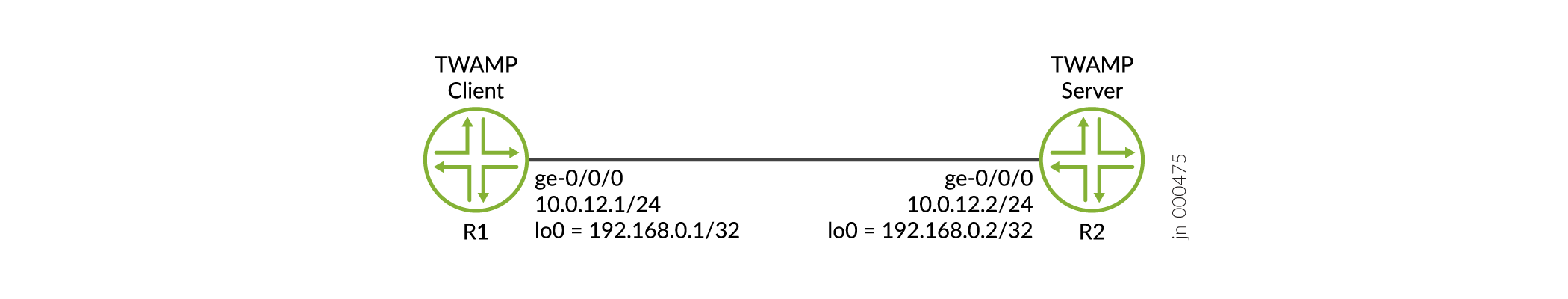
set system host-name R1 set services rpm twamp client control-connection c1 target-address 10.0.12.2 set services rpm twamp client control-connection c1 test-session t1 target-address 10.0.12.2 set services rpm twamp client control-connection c1 test-session t1 probe-count 2000 set security policies default-policy permit-all set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/0.0 set interfaces ge-0/0/0 unit 0 description "To Server R2" set interfaces ge-0/0/0 unit 0 family inet address 10.0.12.1/24 set interfaces lo0 unit 0 family inet address 192.168.0.1/32
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy.
To configure the TWAMP Client:
-
Configure the client device host name as R1.
[edit system] user@R1# set host-name R1
-
Configure Device R1 interfaces.
[edit interfaces] user@R1# set ge-0/0/0 unit 0 description "To Server R2" user@R1# set ge-0/0/0 unit 0 family inet address 10.0.12.1/24 user@R1# set lo0 unit 0 family inet address 192.168.0.1/32
-
Enable traffic flow and system services to run on Device R1, which is otherwise dropped by default.
[edit security zones] user@R1# set security-zone trust host-inbound-traffic system-services all user@R1# set security-zone trust host-inbound-traffic protocols all user@R1# set security-zone trust interfaces ge-0/0/0.0
-
Configure the control session from Device R1 to Device R2.
[edit services] user@R1# set rpm twamp client control-connection c1 target-address 10.0.12.2
-
Configure the test session from Device R1 to Device R2 for collecting probe results.
[edit services] user@R1# set rpm twamp client control-connection c1 test-session t1 target-address 10.0.12.2 user@R1# set rpm twamp client control-connection c1 test-session t1 probe-count 2000
Results
From the configuration mode on Device R1, confirm your configuration by
entering the show | no-more command. If the output does not
display the intended configuration, repeat the instructions in this example
to correct the configuration.
[edit]
user@R1# show | no-more
system {
host-name R1;
}
services {
rpm {
twamp {
client {
control-connection c1 {
target-address 10.0.12.2;
test-session t1 {
target-address 10.0.12.2;
probe-count 2000;
}
}
}
}
}
}
security {
policies {
default-policy {
permit-all;
}
}
zones {
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/0.0;
}
}
}
}
interfaces {
ge-0/0/0 {
unit 0 {
description "To Server R2";
family inet {
address 10.0.12.1/24;
}
}
}
lo0 {
unit 0 {
family inet {
address 192.168.0.1/32;
}
}
}
}Configuring the TWAMP Server for SRX Series Firewalls
CLI Quick Configuration
To quickly configure this example, copy the following commands, paste them into a text file, remove any line breaks, change any details necessary to match your network configuration, copy and paste the commands into the CLI, at the [edit] hierarchy level, and then enter commit from configuration mode.
set system host-name R2 set services rpm twamp server authentication-mode none set services rpm twamp server client-list client1 address 10.0.12.1/24 set security policies default-policy permit-all set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/0.0 set interfaces ge-0/0/0 unit 0 description "To Client R1" set interfaces ge-0/0/0 unit 0 family inet address 10.0.12.2/24 set interfaces lo0 unit 0 family inet address 192.168.0.2/32
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy.
To configure the TWAMP Server:
-
Configure the server device host name as R2.
[edit system] user@R2# set host-name R2
-
Configure Device R2 interfaces.
[edit interfaces] user@R2# set ge-0/0/0 unit 0 description "To Client R1" user@R2# set ge-0/0/0 unit 0 family inet address 10.0.12.2/24 user@R2# set lo0 unit 0 family inet address 192.168.0.2/32
-
Enable traffic flow and system services to run on Device R2, which is otherwise dropped by default.
[edit security zones] user@R2# set security-zone trust host-inbound-traffic system-services all user@R2# set security-zone trust host-inbound-traffic protocols all user@R2# set security-zone trust interfaces ge-0/0/0.0
-
Configure the client attributes for Device R2 to connect with Device R1.
[edit services] user@R2# set rpm twamp server authentication-mode none user@R2# set rpm twamp server client-list client1 address 10.0.12.1/24
Results
From the configuration mode on R2, confirm your configuration by entering the
show | no-more command. If the output does not display
the intended configuration, repeat the instructions in this example to
correct the configuration.
[edit]
user@R2# show | no-more
system {
host-name R2;
}
services {
rpm {
twamp {
server {
authentication-mode none;
client-list client1 {
address {
10.0.12.1/24;
}
}
}
}
}
}
security {
policies {
default-policy {
permit-all;
}
}
zones {
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/0.0;
}
}
}
}
interfaces {
ge-0/0/0 {
unit 0 {
description "To Client R1";
family inet {
address 10.0.12.2/24;
}
}
}
lo0 {
unit 0 {
family inet {
address 192.168.0.2/32;
}
}
}
}Verification
Confirm that the configuration is working properly.
Verifying TWAMP Client Sessions
Purpose
Verify that the TWAMP client sessions are established on Device R1.
Action
From operational mode, enter the show services rpm twamp client
session command.
user@R1>show services rpm twamp client session Connection Session Sender Sender Reflector Reflector Name Name address port address port c1 t1 10.0.12.1 10010 10.0.12.2 10010
Meaning
The configured control and test sessions (c1 and t1, respectively) are established on Device R1.
Verifying TWAMP Server Sessions
Purpose
Verify that the TWAMP server sessions are established on Device R2.
Action
From operational mode, enter the show services rpm twamp server
session command.
user@R2>show services rpm twamp server session
Session Connection Sender Sender Reflector Reflector Session Auth
ID ID address port address port state mode
11 2 10.0.12.1 10010 10.0.12.2 10010 Active UnauthenticatedMeaning
The server session on Device R2 is active with Device R1 as the sender and Device R2 as the reflector.
Verifying Test Session Results
Purpose
Verify that the TWAMP test sessions on Device R1.
Action
From operational mode, enter the show services rpm twamp client
probe-results command.
user@R1> show services rpm twamp client probe-results
Owner: c1, Test: t1
server-address: 10.0.12.2, server-port: 862, Client address: 10.0.12.1, Client port: 60732
TWAMP-Server-Status: Connected, Number-Of-Retries-With-TWAMP-Server: 38
Reflector address: 10.0.12.2, Reflector port: 10011, Sender address: 10.0.12.1, sender-port: 10011
Test size: 2000 probes
Probe results:
Response received
Probe sent time: Fri Nov 25 03:18:34 2022
Probe rcvd/timeout time: Fri Nov 25 03:18:34 2022
Rtt: 718 usec, Ingress time: 134 usec, Egress time: 584 usec, Egress jitter: 48 usec, Ingress jitter: 15 usec,
Round trip jitter: 63 usec
Egress interarrival jitter: 58 usec, Ingress interarrival jitter: 40 usec, Round trip interarrival jitter: 80 usec
...(output truncated for brevity)...Meaning
The probe-results of the TWAMP test session is generated. This shows that the client-server connection is established successfully.
