Trust Plans Overview
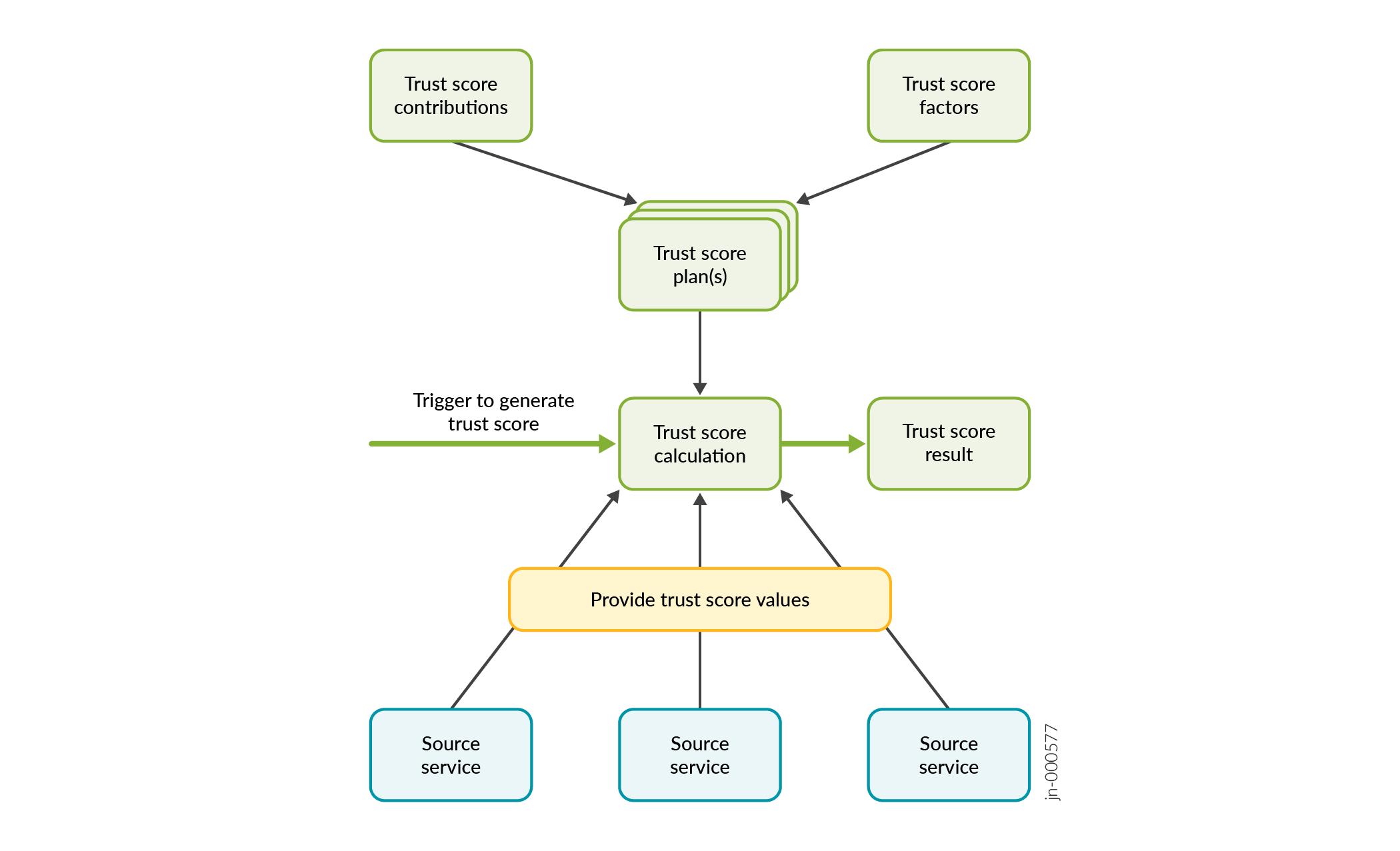
A trust plan or a score plan defines how to calculate a trust score for a network entity. It comprises a set of trust factors for each factor category.
A trust plan also defines the following:
-
Contribution values for each of the factors in the variable and reputational categories, describing the significance of the factor relative to other factors in the same category.
-
Contribution factors for the variable and reputational categories defining the percentages that each category contributes toward the total trust score.
A trust score plan is applied on a network entity by
-
Calculating the trust score based on the factors defined by the plan and the latest values of those factors for the network entity.
-
Generating and persisting a trust score result.
Contribution values are associated with the trust factors in a trust score plan and are used to define the contribution of a factor to the calculation of the trust score. How the contribution values are used depends on the type of trust factor they are associated with.
A trust factor has an implied maximum contribution and an actual contribution. The percentage score for a category is determined to be (the sum of the actual contributions for each of its factors/sum of the maximum contributions) * 100.
The overall percentage score is derived from the variable and reputational percentages, adjusted according to these category contributions.
The compliance benchmark documents provided in this initial release are based on the documents that are published by the Center for Internet Security (CIS).
The CIS Controls Implementation Groups (IGs) are divisions that are based on cybersecurity characteristics. Each group identifies a subset that is assessed to be reasonable for an organization with a similar risk profile and resources to aim to implement. These IGs represent a cross-section of the CIS Controls that are customized to different types of businesses. Each IG builds atop the previous. For example, IG2 includes IG1, and IG3 includes all the Controls in IG1 and IG2.
CIS recommends that businesses prioritize their standardization of the Controls by inheriting from the IGs. Businesses should implement Controls in IG1, followed by IG2, and later IG3. The Controls contained within IG1 are critical to success. Support for IG1 should be considered among the first things to be done as part of a cybersecurity program. CIS describes IG1 as Cyber Hygiene – the essential protections that must be enforced to defend against common attacks.
In the case of Compliance, the IGs are used as a guidance to allocate an appropriate contribution against each trust factor, or a rule in the benchmark document.