Add Identity Providers and Users
Follow these steps to add identity providers (IdPs) to use to authenticate your portal users.
Add your IdPs to your organization and then add your custom roles, delete unneeded local accounts, and provide your users with first-time login instructions.
You need the Super User admin role to configure SSO.
To add identity providers:
- On the left menu of the Juniper Mist portal, select Organization > Admin > Settings.
-
In the Identity Providers section, click Add
IDP.
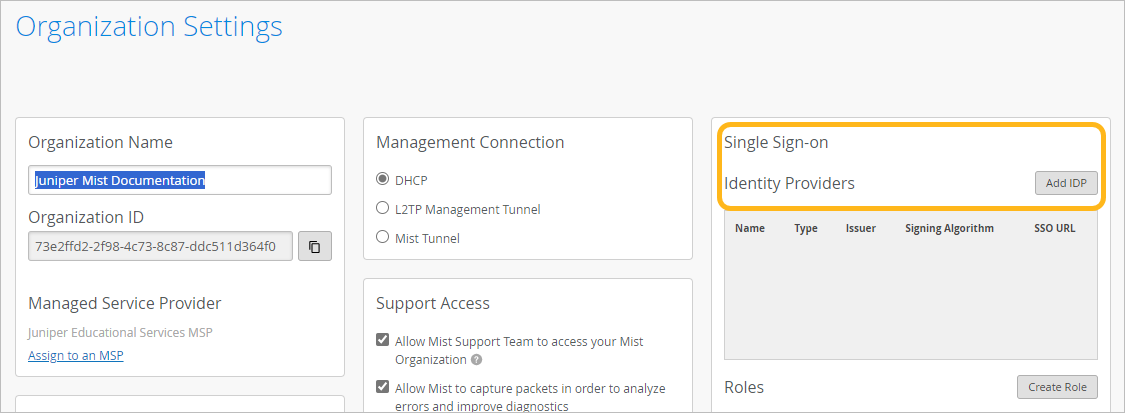
-
In the Create Identity Provider window:
- Enter a name, and then click Add.
-
For the Name ID Format, select the format that you want to
use.
Most people use the e-mail address for the name ID. If you use a different identifier for your IdP user accounts, select Unspecified.
-
Copy the ACS URL (Assertion Consumer Service URL), which
you'll need to complete the SAML 2.0 integration in your IdP's portal.
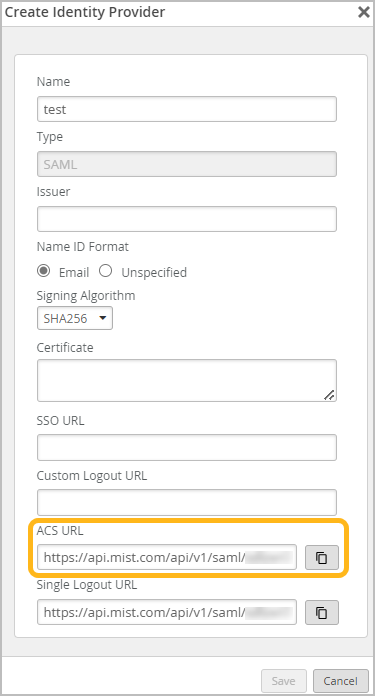
- Keep the Create Identity Provider window open so that you can return to it later in this procedure.
-
Go to your IdP portal and complete these tasks:
-
Set up the user accounts and roles for the users who will use this integration to authenticate to Juniper Mist portal.
-
Create a SAML 2.0 SSO integration for Juniper Mist.
Note:If your IdP requires metadata from Juniper Mist, see Obtain Juniper Mist Metadata for SAML 2.0 Integration.
-
Get the following information from the SAML 2.0 SSO integration:
-
Signing Algorithm
-
Issuer
-
SSO URL
-
-
Download the certificate.
-
-
Return to the Create Identity Provider in Juniper Mist, and use the information from
the SAML 2.0 SSO integration to complete these fields:
-
Signing Algorithm—Select the same signing algorithm that you selected in your IdP SAML 2.0 integration.
-
Issuer
-
SSO URL
-
Certificate—Open the certificate that you downloaded. Copy the entire text and paste it into this field. Include the BEGIN CERTIFICATE and END CERTIFICATE lines.
Example:
This example shows how you would complete the Juniper Mist fields on the left by entering the values from the Microsoft Azure fields on the right.
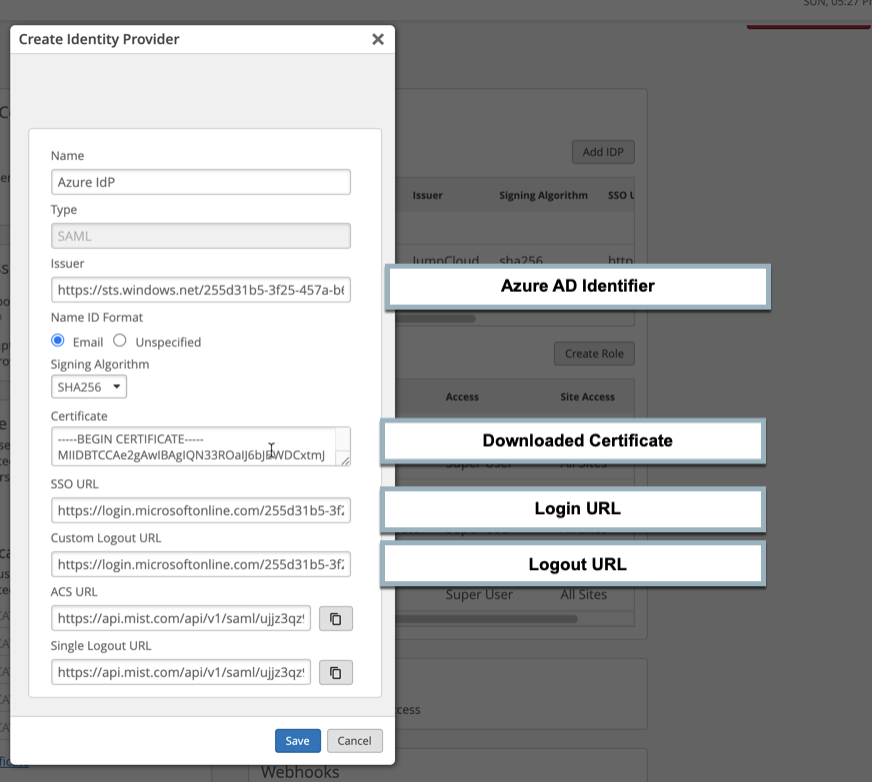
-
- Click Save to save the settings and close the window.
-
To ensure user access, complete all of the following requirements:
-
Create custom roles. Create custom roles corresponding to the IdP roles for your users who will access Juniper Mist through SSO. The user role determines which portal features the user can access. For help with custom roles, see Create Custom Roles for Single Sign-On Access.
Delete local accounts.Delete any previously created admin accounts for your Mist organization, except one Super User account.
Here's why:
Since you want to use your IdP instead of Mist to authenticate users, their previously created Mist accounts serve no purpose. When someone uses SSO to login, that email address is "linked" to the SSO IdP, and their previously created local account cannot be used unless the SSO configuration is deleted.
We recommend having one local account with the Super User role as an emergency backup. This way, in case SSO issues occur, one person is able to use their local account to access your Mist organization.
Since a person cannot use one email address for both SSO and a local account, the local account should be set up with a different email address than the one they'll use with SSO. For example, use a personal email address for the local account and use the work email address for the SSO account.
As a Super User, you can remove account. See Revoke a User's Access.
As an admin, anyone can change the email address that they use for their Mist account. See Account Settings.
Provide first-time login instructions. Ensure that your users understand the first-time login process. When they first log in to Juniper Mist, they must connect to Juniper Mist by using the SSO URL or their IdP dashboard. This step is necessary for the first login only, to establish the account as an SSO account. After that, they can use the SSO URL or go to directly to the Juniper Mist portal (manage.mist.com).
-
If errors occur, see Troubleshoot Issues with Identity Provider Setup.
