- play_arrow Overview
- play_arrow Platform Considerations
- play_arrow WAN Configuration for Session Smart Routers
- WAN Assurance Configuration Overview
- Configure Sites and Variables for Session Smart Routers
- Configure Networks for Session Smart Routers
- Configure Applications for Session Smart Routers
- Configure Application Policies on Session Smart Routers
- Configure Hub Profile for Session Smart Routers
- Configure Path Selection from Hub-to-Spoke with Traffic Steering
- Configure WAN Edge Templates for Session Smart Routers
- Routing Configuration on Session Smart Routers
- Onboard Session Smart Routers for WAN Configuration
- Onboard Session Smart Routers with Static IP Address
- IDP-Based Threat Detection on Session Smart Routers
- Upgrade a WAN Edge Session Smart Router
- Configure VRF Route Leaking for Session Smart Routers
- Revoke DHCP Lease on a WAN Edge Device
- Reserve DHCP IP Address
- play_arrow WAN Assurance Design
- play_arrow Secure Edge Connector
- play_arrow Cellular Edges
- play_arrow Monitor and Troubleshoot
- WAN Assurance Monitoring, SLE, and Troubleshooting Overview
- Monitor SRX Series Firewall Deployed as WAN Edge
- Monitor Session Smart Router Deployed as WAN Edge
- Service-Level Experiences for Session Smart Router Deployed as WAN Edge
- Troubleshoot Session Smart Router Deployed as WAN Edge
- Speed Tests for Session Smart Router Deployed as a WAN Edge (BETA)
- Dynamic and Manual Packet Captures
- Troubleshoot SRX Series Firewalls
- Replace a WAN Edge Device
- WAN Edge Testing Tools
Monitor the Service Status of SRX Series Firewalls
You can monitor the service status of the following features on your Juniper Networks® SRX Series Firewall in the Juniper Mist™ cloud portal:
Enhanced Web Filtering (EWF)
IDP
Application Security
You need a valid license for your SRX Series Firewall to use the feature. For more details about license requirements and installation, see Juniper Licensing User Guide.
On the SRX Series Firewall, use the show system license command to display
the license name with expiry date.
user@host> show system license
License usage:
Licenses Licenses Licenses Expiry
Feature name used installed needed
anti_spam_key_sbl 0 1 0 2022-04-28 00:00:00 UTC
idp-sig 0 1 0 2022-04-28 00:00:00 UTC
dynamic-vpn 0 2 0 permanent
av_key_sophos_engine 0 1 0 2022-04-28 00:00:00 UTC
logical-system 1 3 0 permanent
wf_key_websense_ewf 0 1 0 2022-04-28 00:00:00 UTC
remote-access-ipsec-vpn-client 0 2 0 permanent
Licenses installed:
License identifier: DemoLabJUNOS386107562
License version: 4
Valid for device: CV4720AF0436
Customer ID: Juniper Internal
Features:
av_key_sophos_engine - Anti Virus with Sophos Engine
date-based, 2021-04-27 00:00:00 UTC - 2022-04-28 00:00:00 UTC
anti_spam_key_sbl - Anti-Spam
date-based, 2021-04-27 00:00:00 UTC - 2022-04-28 00:00:00 UTC
idp-sig - IDP Signature
date-based, 2021-04-27 00:00:00 UTC - 2022-04-28 00:00:00 UTC
wf_key_websense_ewf - Web Filtering EWF
date-based, 2021-04-27 00:00:00 UTC - 2022-04-28 00:00:00 UTCCheck EWF Status
To check Enhanced Web Filtering (EWF) configuration status:
- Confirm if EWF is enabled on your SRX Series Firewall in CLI operational mode:
content_copy zoom_out_map
user@host> show security utm web-filtering status UTM web-filtering status: Server status: no-config root@00c52c4c3204>
The Server status: no-config indicates that the EWF is not configured.
- Configure EWF on your SRX Series Firewall using the CLI at the [edit] hierarchy level.
Use configuration mode and commit the configuration.Note:
We've captured the following configuration from a lab environment and provided it for reference purposes only. Your own configuration may vary based on the specific requirements of your environment.
content_copy zoom_out_map[edit] set system syslog file utm-log any any set system syslog file utm-log match RT_UTM set security utm custom-objects url-pattern blacklist value https://*.poki.com set security utm custom-objects custom-url-category restricted value blacklist set security utm default-configuration anti-virus type sophos-engine set security utm default-configuration anti-virus scan-options uri-check set security utm default-configuration anti-virus scan-options timeout 30 set security utm default-configuration anti-virus sophos-engine sxl-timeout 5 set security utm default-configuration web-filtering url-blacklist restricted set security utm default-configuration web-filtering type juniper-enhanced set security utm default-configuration web-filtering juniper-enhanced server host rp.cloud.threatseeker.com set security utm default-configuration web-filtering juniper-enhanced server port 80 set security utm default-configuration web-filtering juniper-enhanced default permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Games action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Gambling action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Abused_Drugs action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Adult_Content action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Adult_Material action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Advanced_Malware_Command_and_Control action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Advanced_Malware_Payloads action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Bot_Networks action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Compromised_Websites action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Drugs action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Emerging_Exploits action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Files_Containing_Passwords action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Hacking action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Illegal_or_Questionable action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Keyloggers action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Malicious_Embedded_Link action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Malicious_Embedded_iFrame action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Malicious_Web_Sites action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Militancy_and_Extremist action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Mobile_Malware action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Network_Errors action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Newly_Registered_Websites action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Pay_to_Surf action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Phishing_and_Other_Frauds action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Potentially_Damaging_Content action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Potentially_Exploited_Documents action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Potentially_Unwanted_Software action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Racism_and_Hate action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Spyware action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Suspicious_Content action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Suspicious_Embedded_Link action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Unauthorized_Mobile_Marketplaces action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Alcohol_and_Tobacco action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Application_and_Software_Download action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Bandwidth action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Computer_Security action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Custom_Encrypted_Payloads action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Elevated_Exposure action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Entertainment action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Entertainment_Video action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_File_Download_Servers action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Freeware_and_Software_Download action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Instant_Messaging action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Internet_Auctions action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Internet_Radio_and_TV action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Intolerance action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Lingerie_and_Swimsuit action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Marijuana action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Media_File_Download action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Message_Boards_and_Forums action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Non_Traditional_Religions action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Non_Traditional_Religions_and_Occult_and_Folklore action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Nudity action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Parked_Domain action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Peer_to_Peer_File_Sharing action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Personals_and_Dating action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Prescribed_Medications action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Private_IP_Addresses action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Pro_Choice action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Pro_Life action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Proxy_Avoidance action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Sex action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Sex_Education action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Social_Networking_and_Personal_Sites action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Surveillance action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Tasteless action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Violence action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Web_and_Email_Spam action log-and-permit set security utm utm-policy custom-utm-policy anti-virus http-profile junos-av-defaults set security utm utm-policy custom-utm-policy web-filtering http-profile wf-home
Check the status in CLI operational mode.
content_copy zoom_out_mapuser@host> show security utm web-filtering status UTM web-filtering status: Server status: Juniper Enhanced using Websense server UP
Now, the status changes to Server status: Juniper Enhanced using Websense server UP. This status indicates that the EWF service is enabled on your device.
- You can check the status in the Juniper Mist cloud portal as shown in Figure 1.
Check IDP Status
Before configuring Intrusion Detection and Prevention (IDP) you need to download and install the IDP security package using the following steps:
Download the IDP package using the instructions in request security idp security-package download command.
Install the package using the instructions in request security idp security-package install command.
This example uses the IDP templates which you download and install as follows: .
- Download IDP template using the instructions in request security idp security-package download policy-templates command.
- Install the templates using the instructions in request security idp security-package install policy-templates command.
- Activate the template commit script content_copy zoom_out_map
[edit] user@host-1# set system scripts commit file templates.xsl
The downloaded templates are saved to the Junos OS configuration database, and they are available in the CLI at the
[edit security idp idp-policy]hierarchy level. Activate the predefined policy as the active policy. In this example, you use
Recommendedpolicy as active policy.For a list of predefined IDP policy templates, see Predefined IDP Policy Templates.content_copy zoom_out_map[edit] user@host-1# set security idp default-policy Recommended user@host-1# set security idp active-policy Recommended
- Enable the IDP policy in your configuration. Following snippet shows a configuration
example.Example:content_copy zoom_out_map
set security idp idp-policy idpengine rulebase-ips rule 1 match from-zone any set security idp idp-policy idpengine rulebase-ips rule 1 match source-address any set security idp idp-policy idpengine rulebase-ips rule 1 match to-zone any set security idp idp-policy idpengine rulebase-ips rule 1 match destination-address any set security idp idp-policy idpengine rulebase-ips rule 1 match application junos-echo set security idp idp-policy idpengine rulebase-ips rule 1 match attacks predefined-attack-groups Critical
- Use the following commands in operational mode to check for the IDP policy status:
- Recommended IDP policy:
show security idp policies: - Policy name:
show security idp policies - IDP status:
show security idp status
- Check the IDP status in Juniper Mist Cloud portal as shown in Figure 1 .
- Recommended IDP policy:
Configure Application Security
On your SRX Series Firewall, Application Security is enabled by default if you have a valid license. The OC-team ensures that all devices have the most up to date application signature version. If you want to change the version or install a custom version, see Predefined Application Signatures for Application Identification.
View Security Service Status in the Juniper Mist Cloud Portal
In the Juniper Mist cloud portal, you can view the status of security services under SECURITY SERVICES panel. Table 1 provides the details of the status.
| Security Services | Display Status | Meaning |
|---|---|---|
| EWF | Enabled | Connection to the Websense server is up. |
| Disabled | EWF is not configured on your device. | |
| Down | Connection to the Websense server is down. | |
| IDP | Enabled | IDP is configured and the IDP policy is applied. |
| Disabled | IDP is not configured. In this case, the IDP policy name is displayed blank. | |
| Application Security | Enabled | Application security is enabled. The application signature version is displayed. |
| Disabled | Application security is not enabled. The application signature version is displayed as zero. |
Figure 1 shows security services status in Juniper Mist cloud portal.
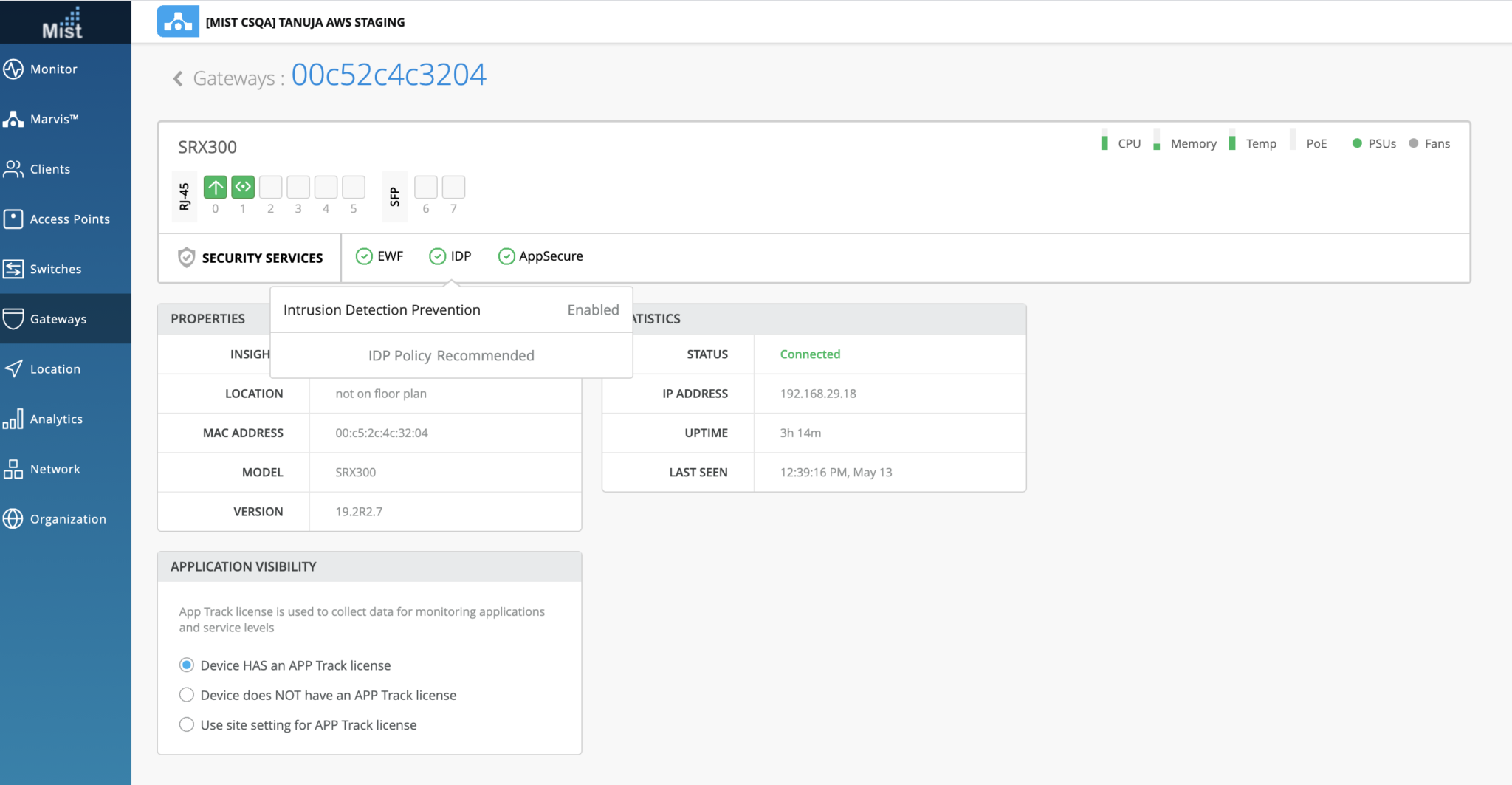
You can get details such as the presence or absence of a valid license and the status of the security services.
"service_status": {
"idp_status": "disabled", // either "enabled" or "disabled"
"idp_policy": "", // if the above is disabled this will be empty
"appid_status": "disabled", // either "enabled" or "disabled"
"ewf_status": "disabled", // either "enabled" (websense up), "disabled" (no config) or "down" (websense down)
"appid_version": 0 // this will be 0 if appid_status is disabled, as we then don't check the version number
},




















