Full Stack Design for WAN Edge Devices
Use this Full Stack guide to set up your Juniper WAN Edge devices in concert with Juniper Mist Access Points (APs) deployed in Wireless Assurance, and Juniper EX Series Switches deployed in Wired Assurance.
Overview
The Juniper Mist Full Stack enables you to expand your network capabilities by integrating Mist Access Points (APs), EX Switches, and WAN Edge devices. This design brings all your network devices into a cohesive onboarding, monitoring, and troubleshooting dashboard.
The Full Stack design begins with WAN Edge devices deployed in Mist WAN Assurance. After completing the Juniper Validated Design (JVD) topology (see SSR JVD and SRX JVD), you should already have a WAN Edge device deployed in a hub and spoke network. The WAN Edge device serves as the foundation for building out your entire network with the Full Stack. The Full Stack is specifically designed for a branch that utilizes Juniper equipment.
For successful implementation of the Full Stack, you'll need at least one Juniper EX Switch to onboard into the Mist cloud. If you plan to do advanced testing with virtual circuits, two EX Switches is ideal. Additionally, you can incorporate a Mist AP into the setup to enhance the wireless capabilities of the network. Onboarding those into your LAN network for Mist management gives administrators the ability to monitor and manage their WAN Edges, switches, and APs all from the Mist dashboard.
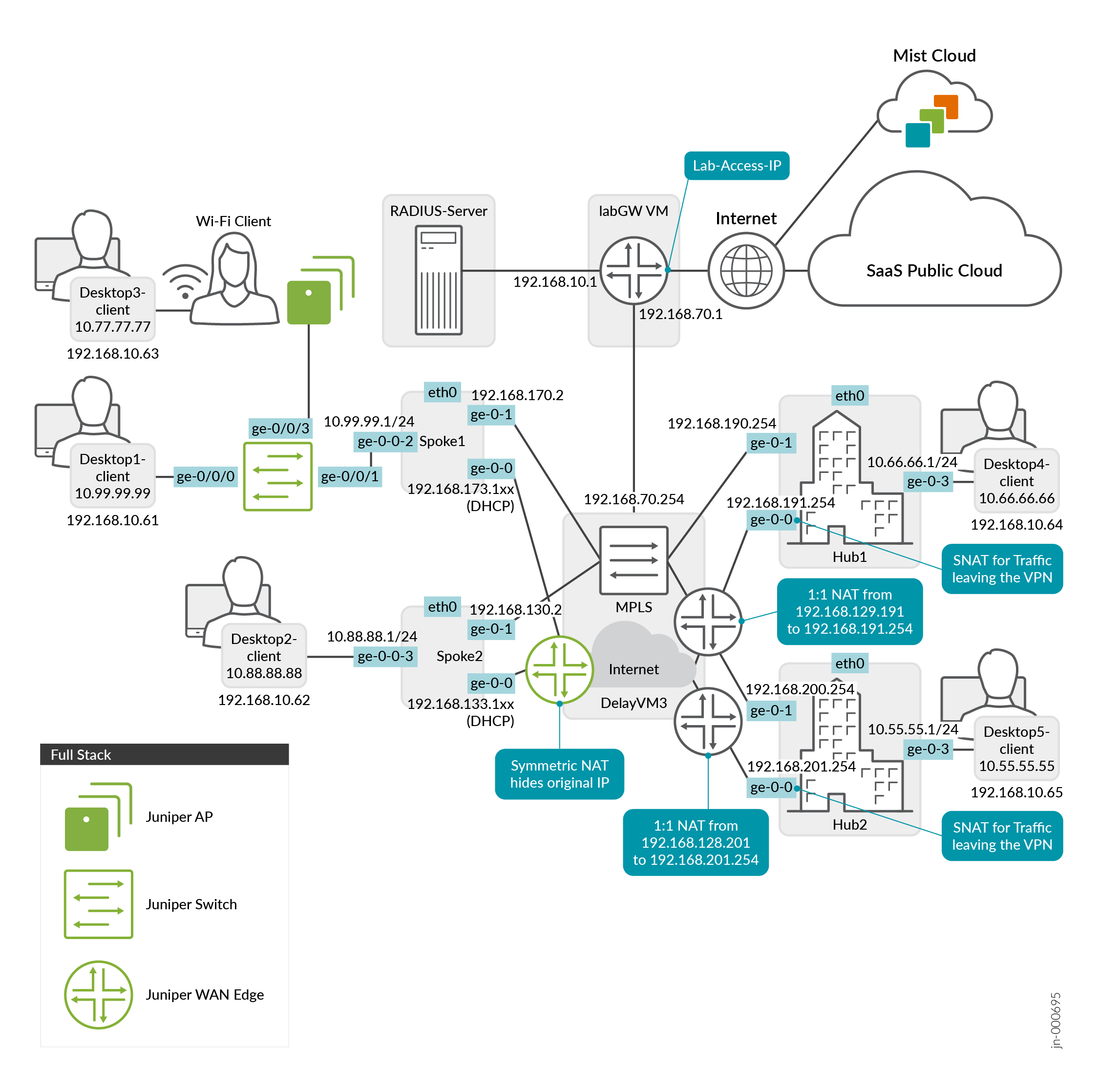
The Figure 1 shows the topology of the Juniper Mist Full Stack with WAN Assurance at its core. The devices in green are meant to show the different types of devices that make up a Full Stack. You can have a number of APs, Switches, and WAN Edges in a single Full Stack deployment.
Requirements and Considerations
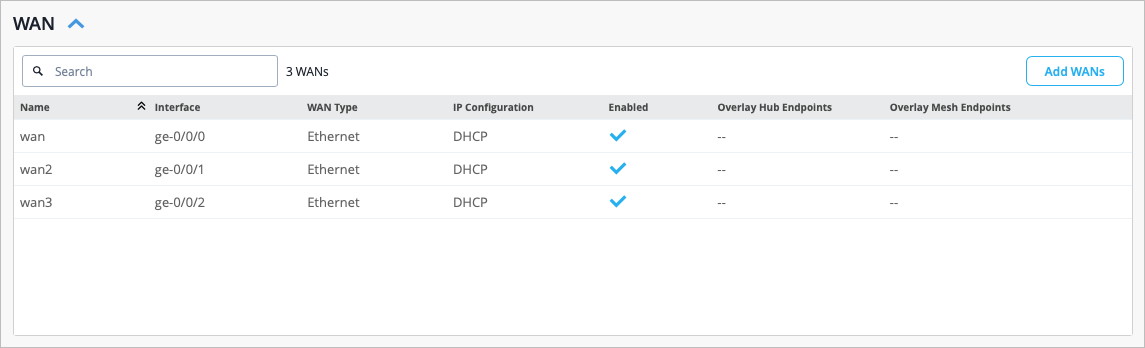
To get started, you’ll need to alter some of the interfaces found in the Juniper Mist WAN Configuration Guide topology. We’ll show you how to do this using a Spokes configuration template found in the Mist WAN Configuration Guide. See WAN Assurance Configuration Overview.
Devices are expected to get out to the Mist cloud using the on-box Internet Service Provider (ISP) link. The device will attempt to retrieve a DHCP address from that ISP. Your devices will connect to Mist on these endpoints by default out of the box. However, if the device is behind a firewall, it may not be able to reach the Mist cloud. See Juniper Mist Firewall Ports and IP Addresses for Firewall Configuration for the firewall ports to open based on your device.
The device uses a hostname to connect on and needs to resolve that hostname using outbound DNS access to 8.8.8.8. Along with the previously mentioned DNS, the SSR will attempt to use 1.1.1.1 and the SRX will attempt to use 8.8.4.4. These are used as the DNS servers over the ISP link mentioned above to resolve the endpoints. Once the device connects to the Mist cloud, your configured DNS is used by the device.
If your SRX Series Firewall is showing as disconnected when it is online and reachable locally, you can troubleshoot the issue using Troubleshoot Disconnected SRX Series Firewalls.
Onboard a WAN Edge Device
Create a Site
Create a Hub Profile
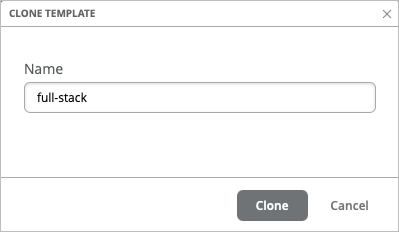
You can also Create a Hub Profile by Cloning an existing one to save time.
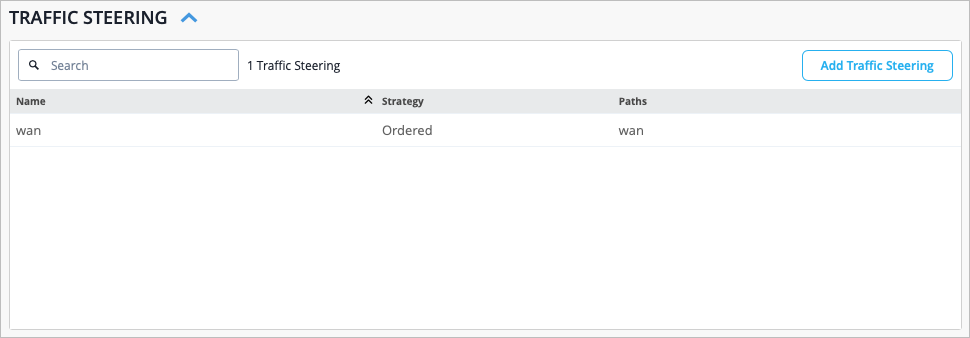
You'll create hub profiles for WAN Edge devices at hub sites. You'll create WAN Edge templates for WAN Edge devices at spoke sites. Hub WAN interfaces create overlay endpoints for spokes. Spoke WAN interfaces map the appropriate Hub WAN interfaces, defining the topology. Hub profiles drive the addition and removal of paths on your overlay.
However, if your topology does not use an overlay, skip to the Create a New Spokes Configuration Template section below.
Create a New Spokes Configuration Template
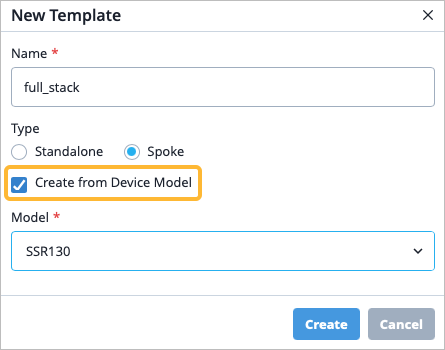
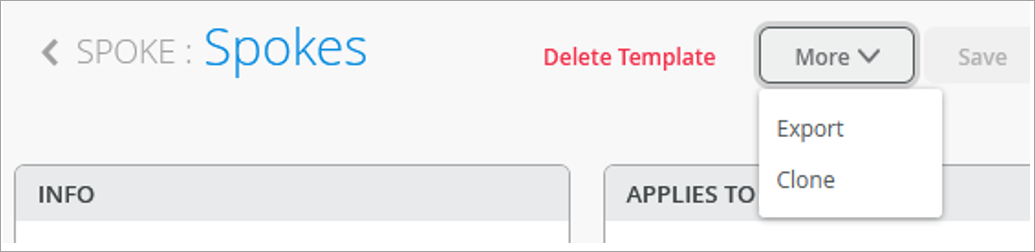
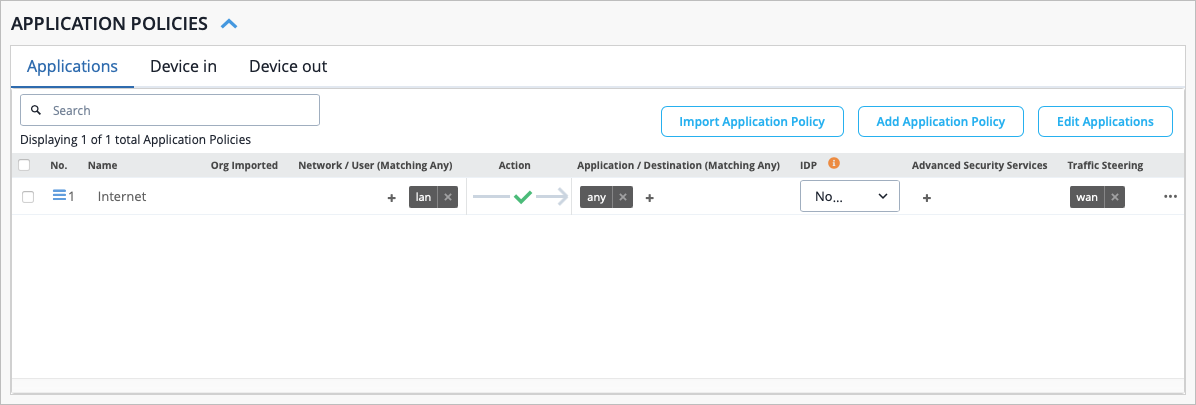
The WAN Edge device at the spoke site in your Full Stack design is configured via the WAN Edge template. You can create a new spoke WAN Edge template, or clone an existing spoke template and then make the necessary changes.
The most efficient way to configure a WAN Edge template is to create a spoke WAN Edge Template from device-model. This automatically sets the configuration for you, and you can adjust the configuration in any way necessary.
Edit the Template as Needed
Assign the New Template to a Site
Assign the WAN Edge Devices to a Site
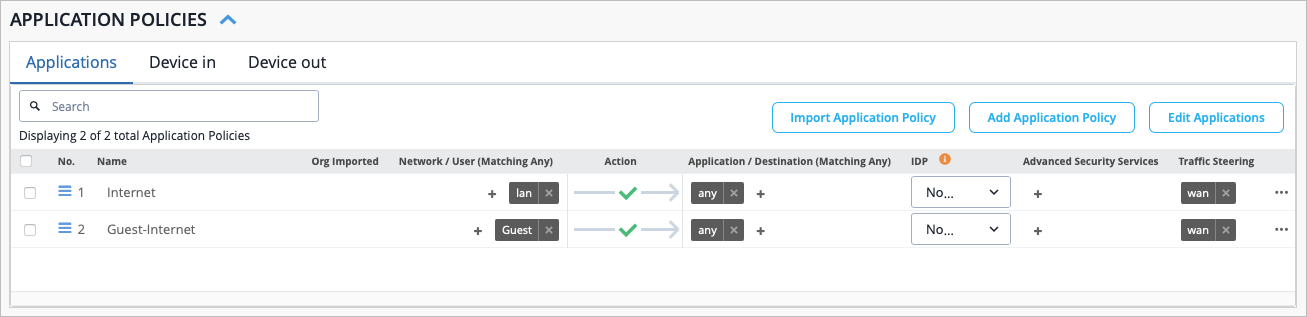
As part of completing the Full Stack design, you must now assign the WAN Edge devices to the same site you applied your template to in the previous section. This ensures that the WAN Edge devices in your Full Stack get the necessary configuration.
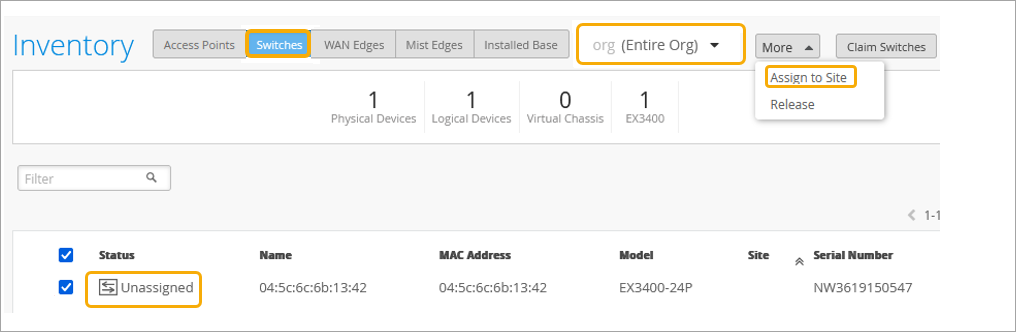
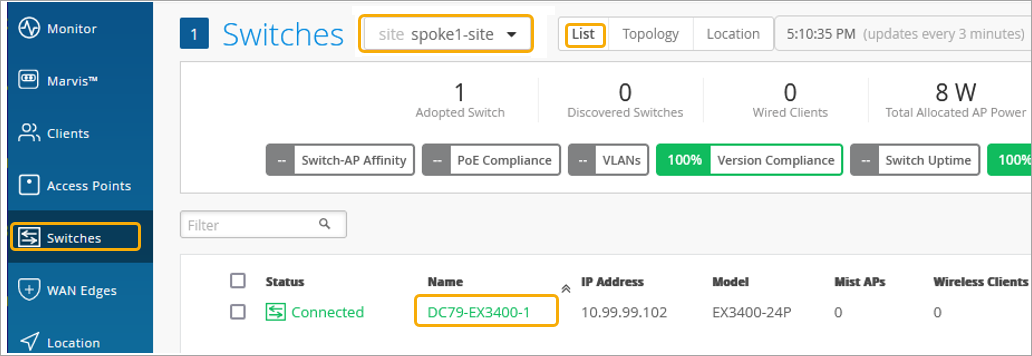
Add Your Switch to the Full Stack Design
Now it is time to onboard your switch and add it to your Full Stack design. For details on how to onboard your switch, refer to:
-
The product documentation for your switch in the Juniper TechLibrary.
-
To get a new cloud-ready EX switch up and running in the Juniper Mist cloud portal, follow the onboarding steps and links in Cloud-Ready EX and QFX Switches with Mist and Onboard Switches to Mist Cloud.
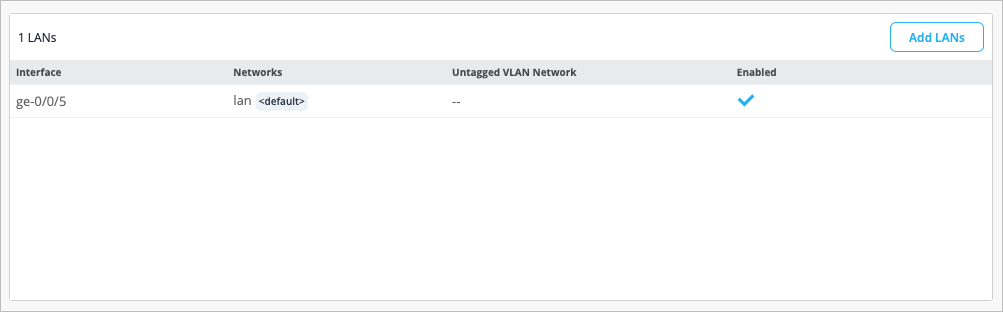
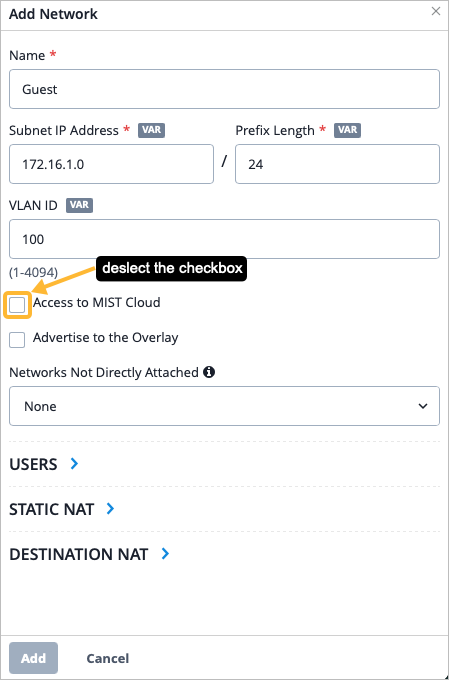
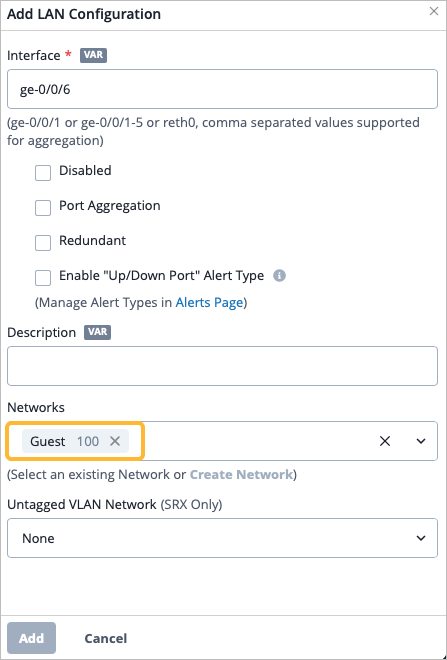
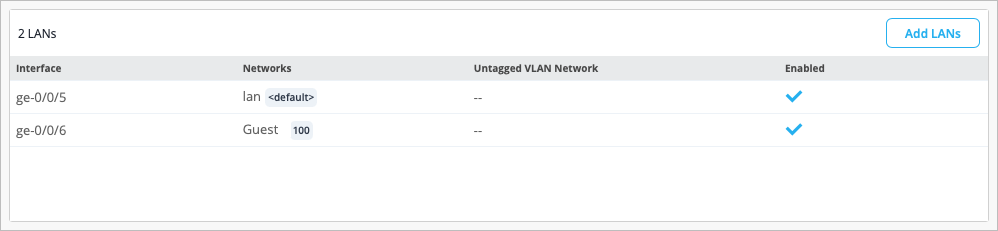
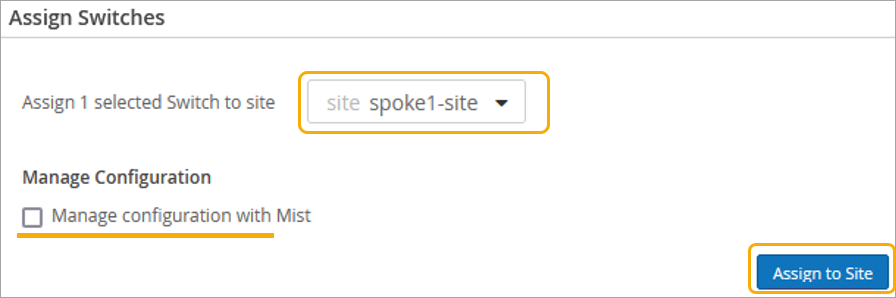
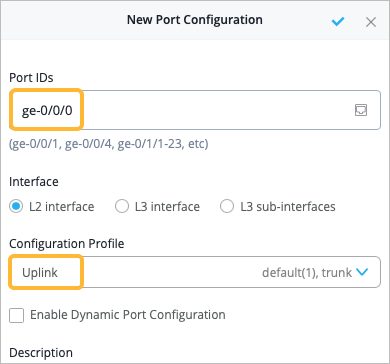
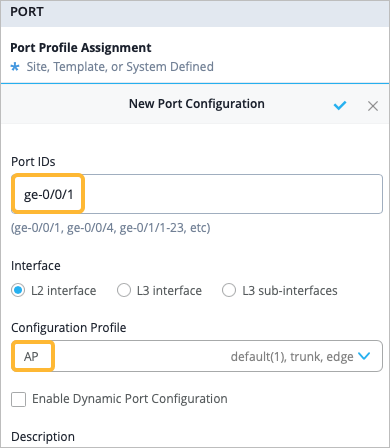
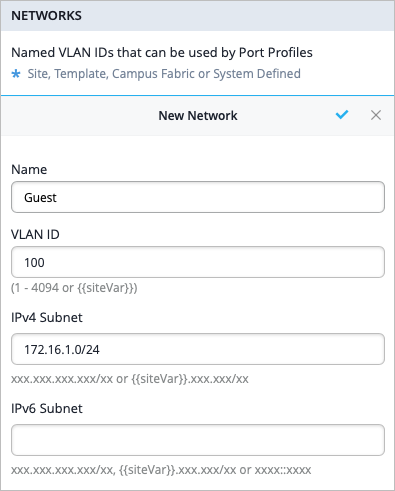
As part of completing the Full Stack design, you must now assign the switch to the same site as the other devices in the Full Stack, and must select the ports which the other devices will connect to your switch on. You must also configure the same guest network you configured on your WAN Edge.
Add Your APs to the Full Stack Design
Now it is time to onboard your AP and add it to your Full Stack design. Refer to:
-
The product documentation in the Juniper TechLibrary for details on how to onboard your AP.
- For the steps to get a new AP up and running in the Mist cloud, see the Juniper Mist Access Points Quick Start Guide.
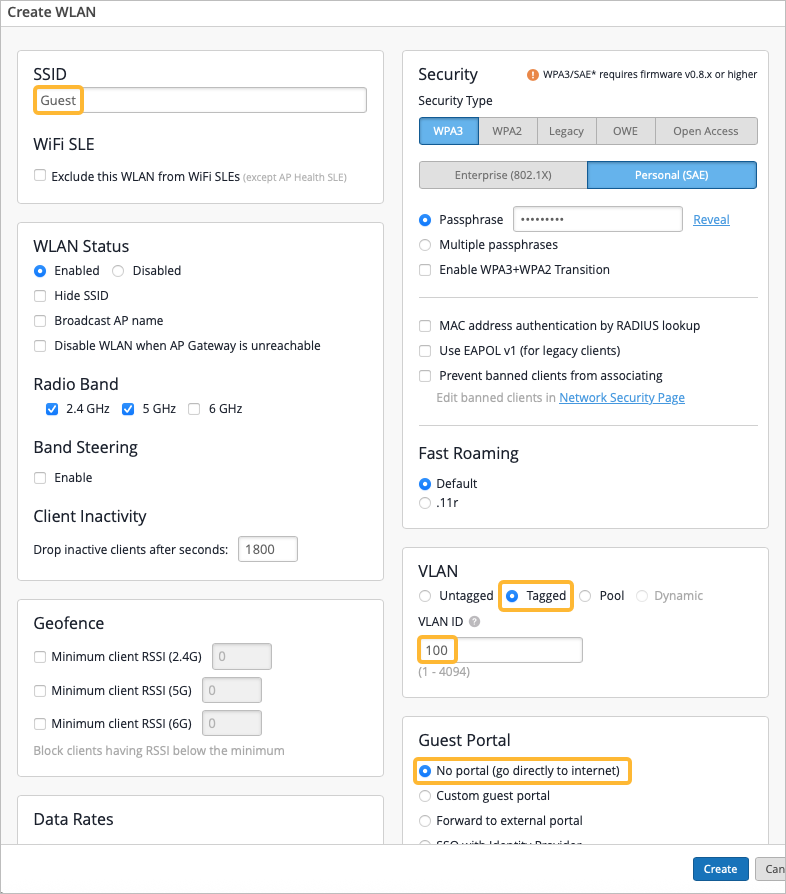
To complete the Full Stack design, you must now assign the switch to the same site as the other devices in the Full Stack. You must also configure your AP with the same guest network you configured on your WAN Edge and switch.