Zscaler Integration
Follow this workflow to use Zscaler as your Secure Edge provider.
Juniper Mist™ provides pre-built connectors specifically designed for the Juniper Networks® SRX Series Firewalls and Juniper® Session Smart™ Routers deployed as WAN edge devices. These connectors facilitate seamless integration with your Secure Edge (SSE) deployments. With minimal configuration, you can integrate the SSE into the Juniper Mist portal. As a result, your WAN Edge device establishes connections to the SSE using either IPsec or GRE protocols.
Overview
Juniper SD-WAN with Mist AI enhances security, and integration with Zscaler offers a top-notch SASE solution for secure access across locations. Zscaler provides comprehensive cyber-security and zero trust connectivity, all integrated seamlessly with Juniper Mist Cloud.
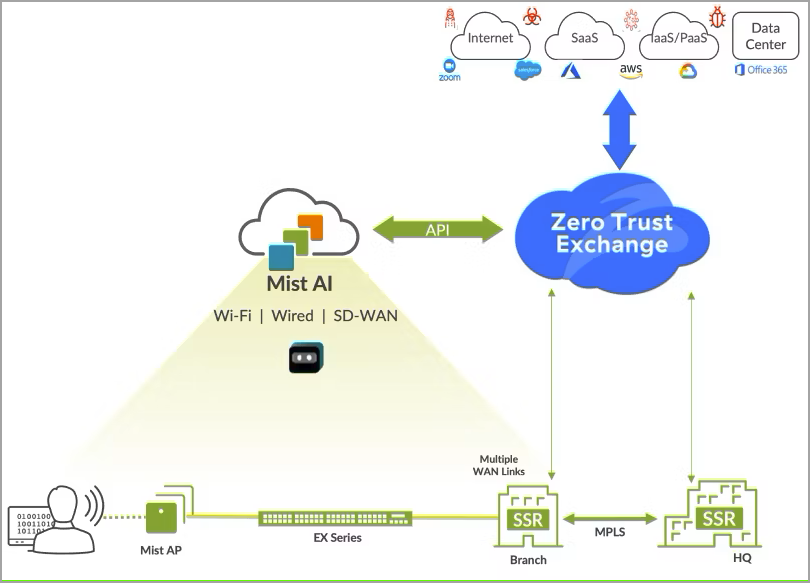
To improve cloud-to-cloud connectivity, Mist now offers automated Zscaler tunnel provisioning. WAN Assurance delivers an easy-to-use workflow for default Zscaler connections. This integration allows you to effortlessly establish connections from your devices using predefined settings. Juniper Mist Cloud portal allows simplified configuration and management of Zscaler Security Service Edge (SSE) connections—eliminating the need for additional platform logins.
Note the following about Zscaler tunnel provisioning:
- Automatic provisioning supports only IPsec tunnels.
- The tunnel auto provision process includes the creation of a new Zscaler location and VPN credential objects in the Zscaler cloud. These Zscaler resources will be deleted when the associated tunnel provider is removed from the Mist.
- Each auto orchestration requires the creation of one primary tunnel and one secondary tunnel.
Read the following topics to understand how to set up Zscaler tunnel configuration from the Juniper Mist Cloud.
Zscaler Manual Provisioning of Tunnels
Prerequisites
For IPsec Tunnels
- Zscaler cloud account
- Local ID and pre-shared key (PSK) configured from the Zscaler account. Ensure that you set the length of PSK between 6 to 255 characters.
- IP addresses or hostnames of the Zscaler public service edges tunnels (primary and secondary). See Locating the Hostnames and IP Addresses of Zscaler Enforcement Nodes (ZENs).
- Check Configuring an IPSec VPN Tunnel.
For GRE Tunnels
- Zscaler cloud account
- IP addresses or hostnames of the Zscaler public service edges tunnels (primary and secondary). See Locating the Hostnames and IP Addresses of Zscaler Enforcement Nodes (ZENs). See Configuring GRE Tunnels.
- Static IP address. See About Static IP
Configure Zscaler Tunnel Provisioning
- On Juniper Mist portal, go to Secure Edge Connector at WAN Edge Templates-level, hub profile, or at Site-level.
- Click Add Providers.
- In Add Provider window, select Zscaler for manual provisioning.
- Enter the details for Zscaler manual provisioning of tunnels.
- For IPsec TunnelsFigure 2: Add Details for Zscaler IPsec Tunnels
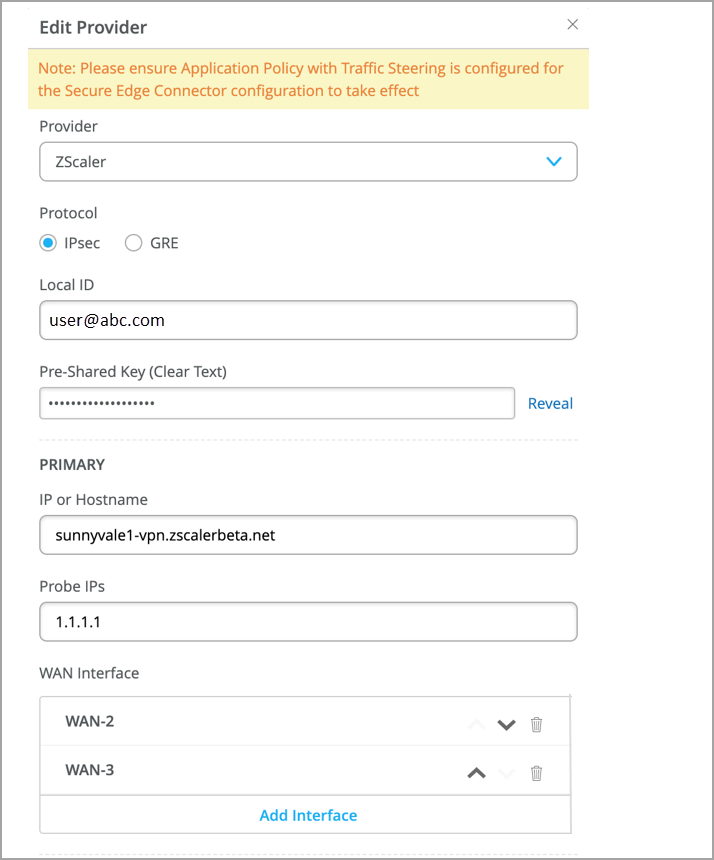
- Name—Enter the name of the service.
- Provider—Select Zscaler.
- Protocol—Select the protocol as IPsec.
- Local ID—Provide login ID of the Zscaler account.
- Preshared Key—Provide preshared key (PSK) created with Zscaler account. The length of the PSK must be between 6-255 characters.
- IP or Hostname—IP addresses or hostname of the Zscaler DC. ( See https://config.zscaler.com/zscalerbeta.net/cenr ). We recommend to add IP address of the nearest DC to your device location.
- Probe IPs—Enter probe IP address. You can use any well-known IP (Example: 8.8.8.8). You need probe IP address to monitor the status of the Zscaler IPsec tunnel using probes.
- WAN Interface—Assign WAN interfaces for provisioning of primary and secondary tunnels. You can add multiple WAN interfaces and the first interface takes the priority. If first interface is down, then system uses the second interface to establish the tunnel.
- Mode—Select active-standby option.
Configure secondary tunnel options (optional). Enter IP or Hostname, Probe IPs, WAN Interface, and Mode for the secondary tunnel.
- For GRE Tunnels:Figure 3: Add Details for Zscaler GRE Tunnels
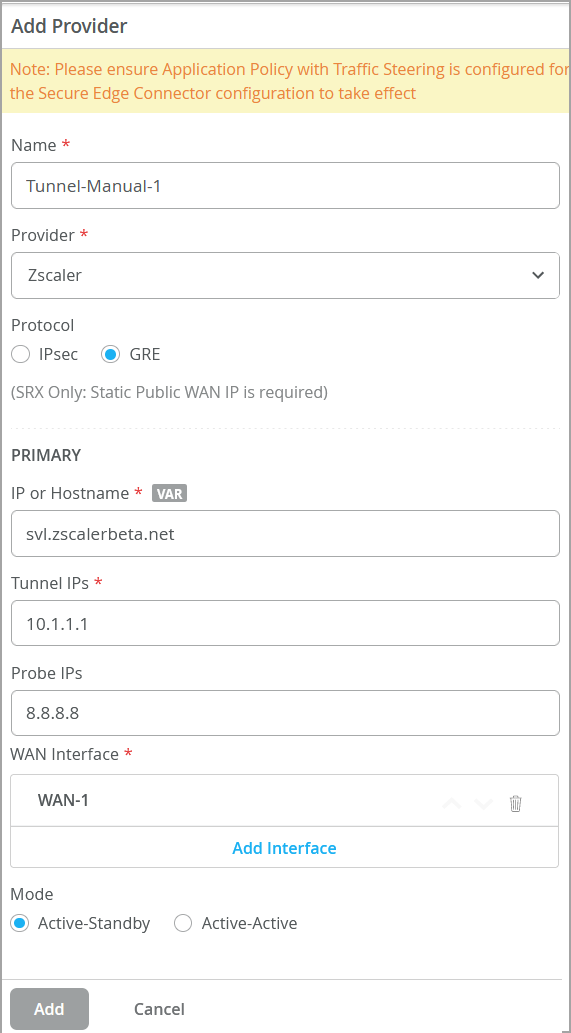
- Name—Enter the name of the service.
- Provider—Select Zscaler.
- Protocol—Select the protocol as GRE.
- IP or Hostname—IP addresses or hostname of the Zscaler DC. ( See https://config.zscaler.com/zscalerbeta.net/cenr ). We recommend to add IP address of the nearest DC to your device location.
- Tunnel IP—Static IP address created for GRE tunnel. See Configuring GRE Tunnels.
- Probe IPs—Enter probe IP address. You can use any well-known IP (Example: 8.8.8.8). You need probe IP address to monitor the status of the Zscaler IPsec tunnel using probes.
- WAN Interface—Assign WAN interfaces for provisioning of primary and secondary tunnels. You can add multiple WAN interfaces and the first interface takes the priority. If first interface is down, then system uses the second interface to establish the tunnel.
- Mode—Select active-standby option.
Enter IP or Hostname, Tunnel IP, Probe IPs, and WAN Interface for the secondary tunnel.
- For IPsec Tunnels
- Click Add to continue.
Add a traffic steering profile on the WAN Edge Templates page or on WAN Edge Device page.
Figure 4: Traffic Steering Path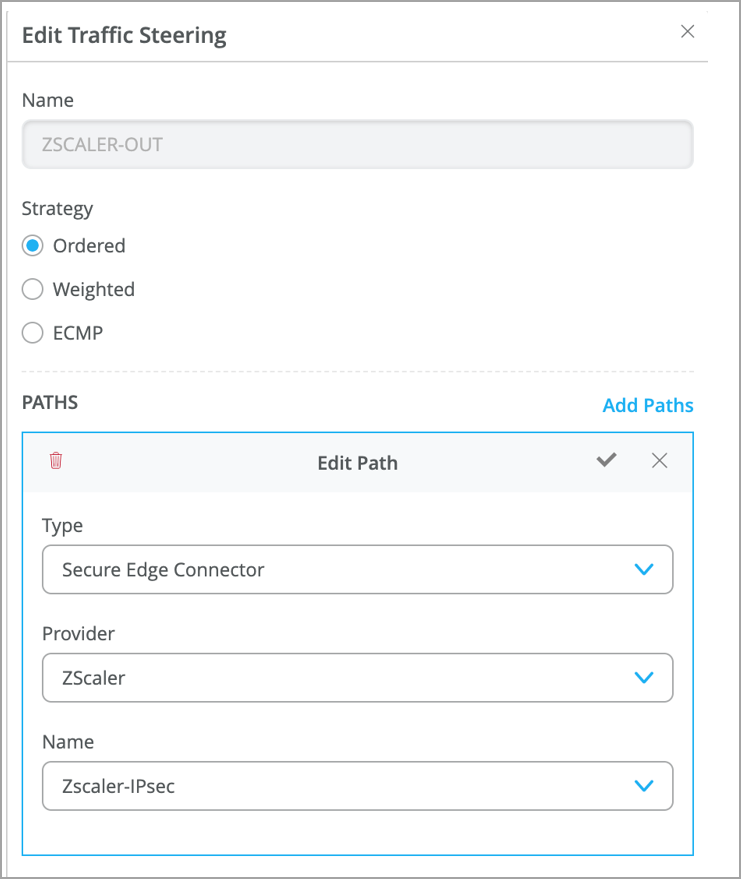
- Enter the details for the traffic-steering path:
- Name—Enter a name for the traffic-steering profile.
- Strategy—Select a strategy. You can configure the traffic steering profile with any strategy (Ordered/Weighted/ECMP), based on your topology and configuration.
- Type—Select Secure Edge Connector.
- Provider—Select Zscaler.
- Enter the details for the traffic-steering path:
- Add an application policy to refer the traffic steering profile you created.
This
step is required for provider tunnels to take effect. To
create the application policy, in the Juniper Mist cloud portal, go to
Organization > WAN >
Application Policy
Following image shows an example of application policy with traffic steering configured in previous step.
Figure 5: Application Policies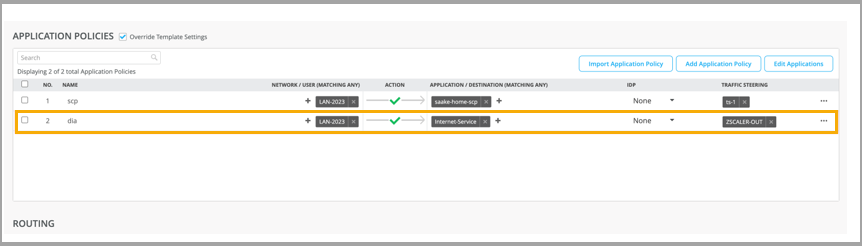
Zscaler Auto-Provisioning of Tunnels
- Prerequisites
- Add Zscaler Credentials in Juniper Mist Portal
- Configure Zscaler Auto Tunnel Provisioning
- Verify Juniper Secure Edge Tunnels
- Secure Edge Connector Auto Provision Settings
- Zscaler Auto-Tunnel Provisioning with Sub-Locations
- View Sub-Locations in Zscaler Portal
Prerequisites
You need a partner key and the partner admin login credentials in Zscaler portal for auto-provisioning of Zscaler tunnels.
Add a partner API key.
- Use your Zscaler account to login admin portal.
- Select Administration > Partner Integrations.
- Select the SD-WAN tab.
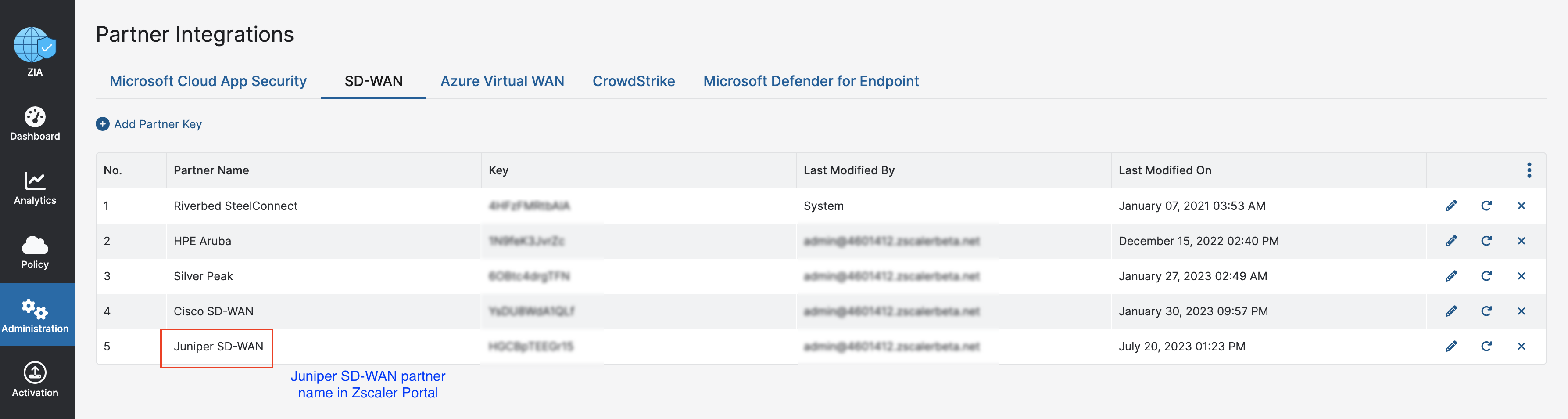
- Click Add Partner Key.
- In the Add Partner Key window, choose the partner name from a
drop-down menu and click Generate. Figure 6: Selecting SD-WAN Partner Integration
Provide credentials for the API access.
- Go to Administration > Role Management > Add Partner Administrator Role.
- Configure the following options:
- Name—Name of the administrator role.
- Access Control—Select the access control type as Full.
- Partner Access—Select the type of access categories for the access control (SD- WAN API Partner access permission).
Check Adding Partner Admin Roles for details.
Create a partner account for the SD-WAN Orchestrator. This admin user (username/password) is specifically used for SD-WAN partner authentication and it is different from Zscaler account admin user.
- Select Administration > Administrator Management > Add Partner Administrator.
- Enter the details such as login ID, email address, name, partner role, and password. See Adding Partner Admins for details.
- Find Zscaler Cloud name using What is My Cloud Name.
Add Zscaler Credentials in Juniper Mist Portal
- Provide Zscaler credential details in Juniper Mist portal to integrate
Juniper Mist cloud with Zscaler.
- On Juniper Mist portal, select Organization > Settings.
- Scroll-down to Secure WAN Edge Integration pane and click Add Credentials.
- In Add Provider window, enter the
details.Figure 7: Add Credentials for Zscaler
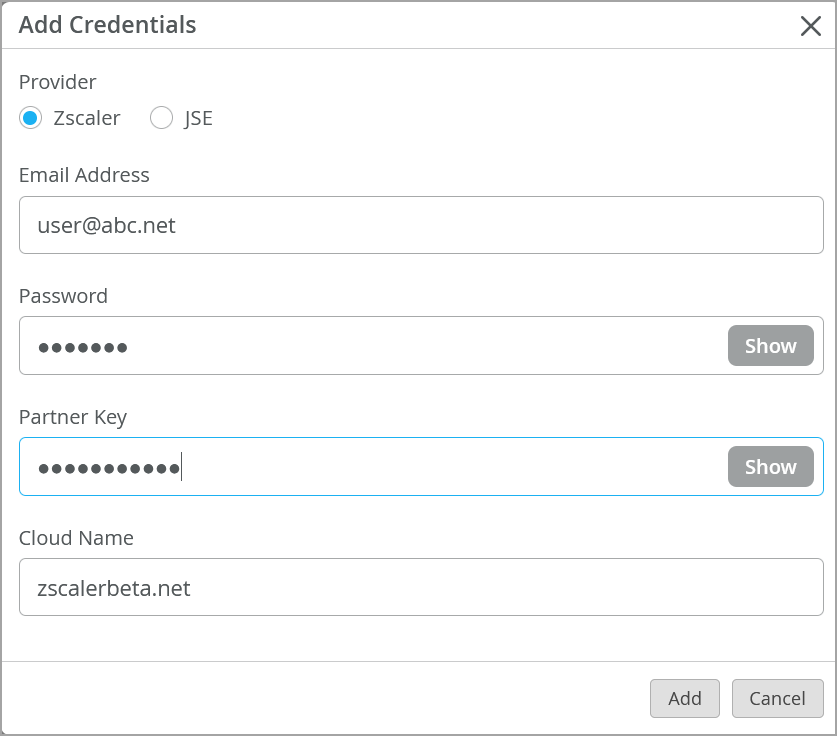
- Provider—Select Zscaler.
- Email Address—Enter username (email address) (SD WAN partner user credentials)
- Password—Enter password for the username.
- Partner Key—Input partner key you created when configuring your Zscaler account.
- Cloud Name—Zscaler cloud URL. For example, zscalerbeta.net.
- Click Add to continue.
This procedure is one-time configurations at the organization level. To automatically provision the Zscaler tunnels across several sites, Mist Cloud uses the above-mentioned credentials for the given Organization.
Configure Zscaler Auto Tunnel Provisioning
- On Juniper Mist portal, go to Secure Edge Connector at WAN Edge Templates-level or at Site-level.
- Click Add Providers.
- In Add Provider window, select Zscaler
(Auto) for auto provisioning. Figure 8: Add Details for Zscaler Tunnel Auto Provisioning
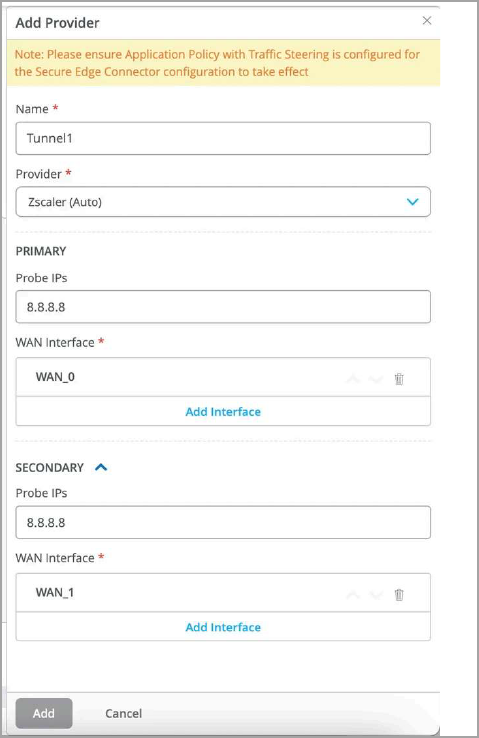
Enter the following details for Zscaler auto-provisioning:
- Name—Enter the username of the Zscaler account.
- Provider—Select Zscaler.
- Probe IPs—Enter probe IP address (primary and secondary). Enter any well-known IP address as probe IP. Example: 8.8.8.8.
- WAN Interface—Assign WAN interfaces under primary and secondary tunnel details for provisioning of primary and secondary tunnels.
- Click Add to continue.
Add a traffic steering profile on the WAN Edge Templates page or on WAN Edge Device page.
Figure 9: Traffic Steering Path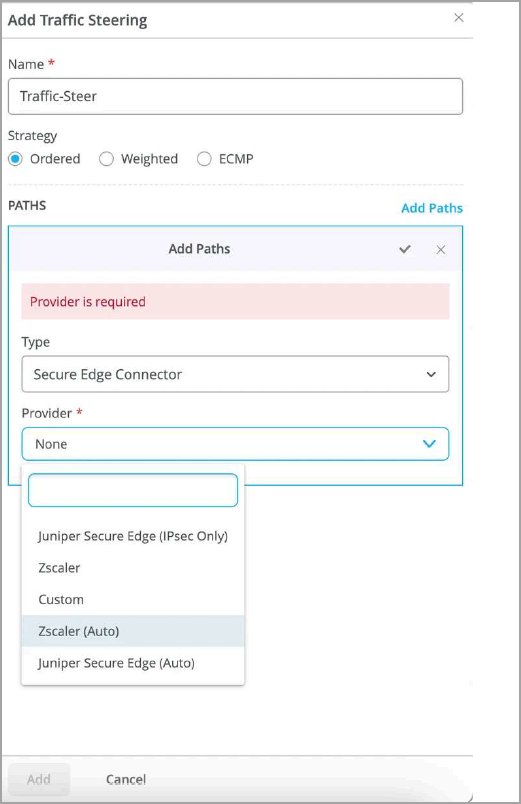
- You can add a new traffic-steering path by selecting:
Name—Enter a name for the traffic-steering profile.
Strategy—Select a strategy. You can configure the traffic steering profile with any strategy (Ordered/Weighted/ECMP), based on your topology and configuration.
Type—Select Secure Edge Connector.
Provider—Select Zscaler.
- You can add a new traffic-steering path by selecting:
- Add an application policy to refer the traffic steering profile you created.
This is required for provisioning of provider tunnels to take effect. To
create the application policy, in the Juniper Mist cloud portal, go to
Organization > WAN >
Application Policy
Following image shows an example of application policy with traffic steering configured in previous step.
Figure 10: Application Policies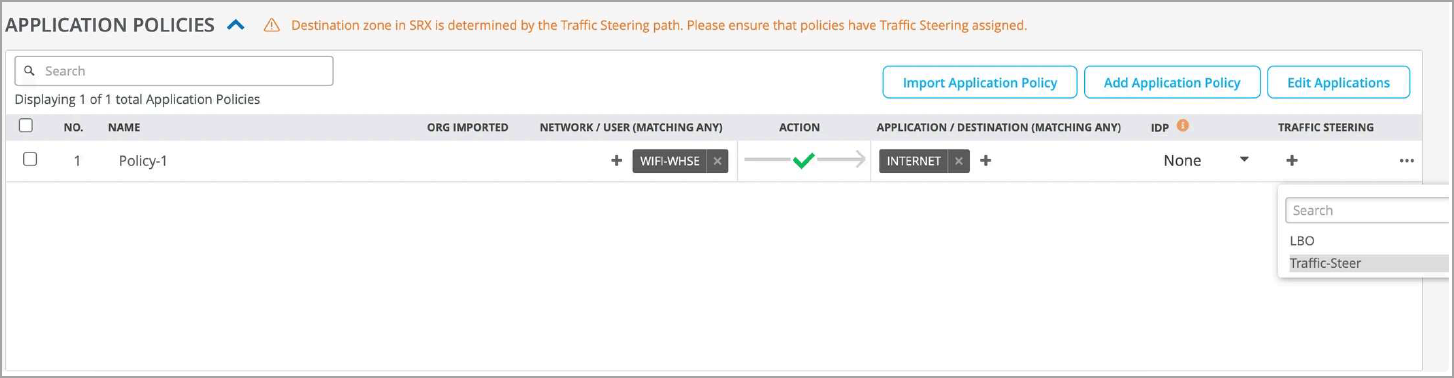
When you assign a template that is enabled with the Zscaler (Auto) option to a site, the following operations take place:
An associated Zscaler site (location object) is automatically created. You can view the location object in Administration > Location Management on Zscaler portal.
Figure 11: Location Created in Zscaler Portal
The details required for tunnel creation are exchanged between Juniper Mist cloud and Zscaler.
Tunnels are powered up from the device to the closest network point-of-presence (POP).
Verify Juniper Secure Edge Tunnels
On Juniper Mist portal, you can verify the established tunnels details in WAN Insights of the device once WAN Edge Tunnel Auto Provision Succeeded event appears under WAN Edge Events.
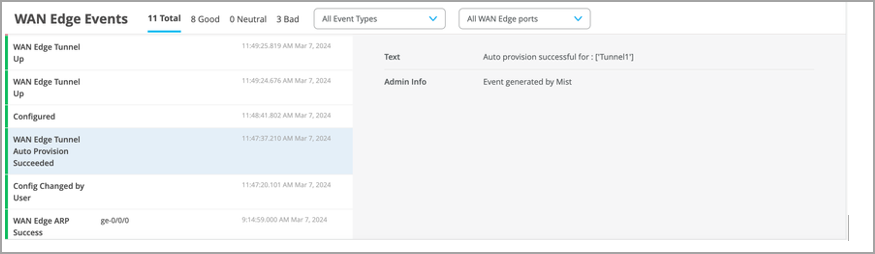
Get the established tunnels status details in WAN Edges > WAN Edge Insights page Juniper Mist cloud portal.
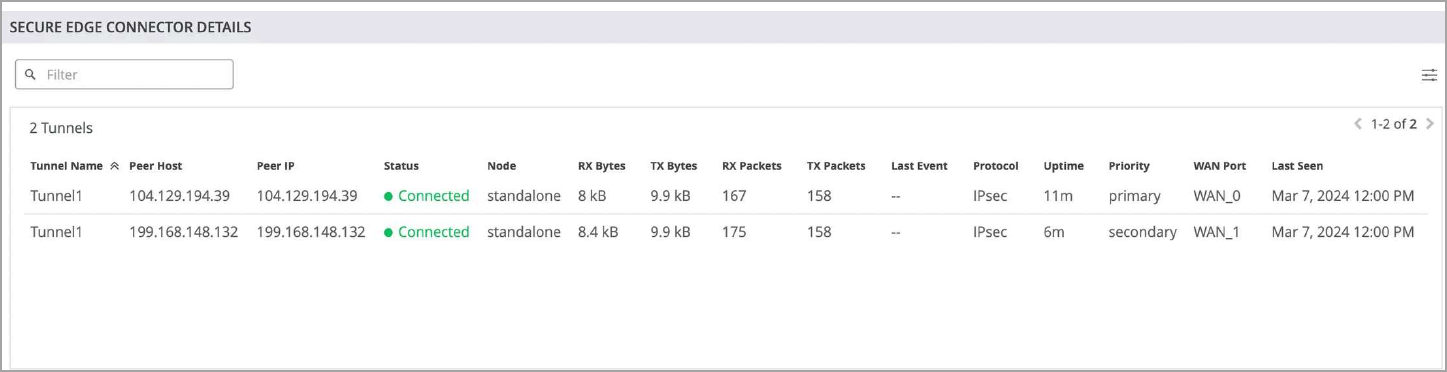
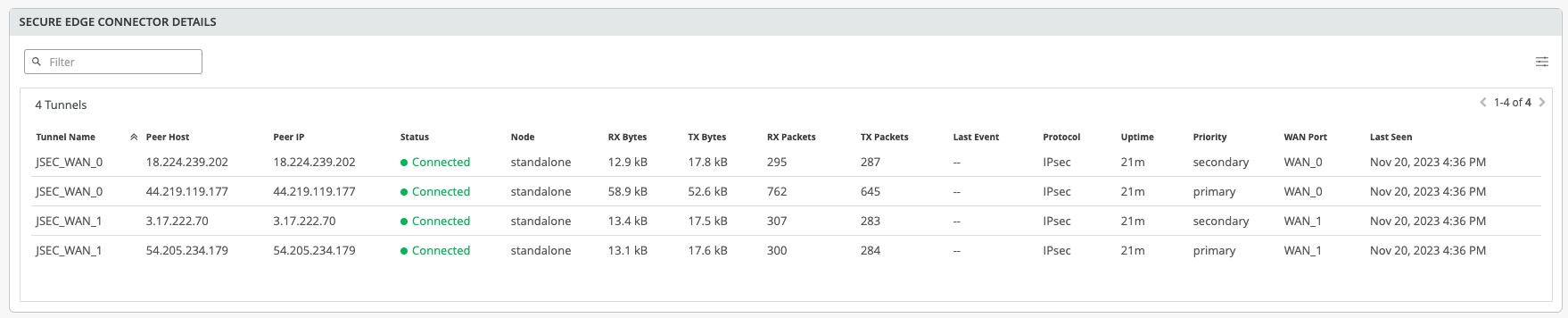
You can check the established tunnels in the Juniper Security Director Cloud dashboard and in the service location.
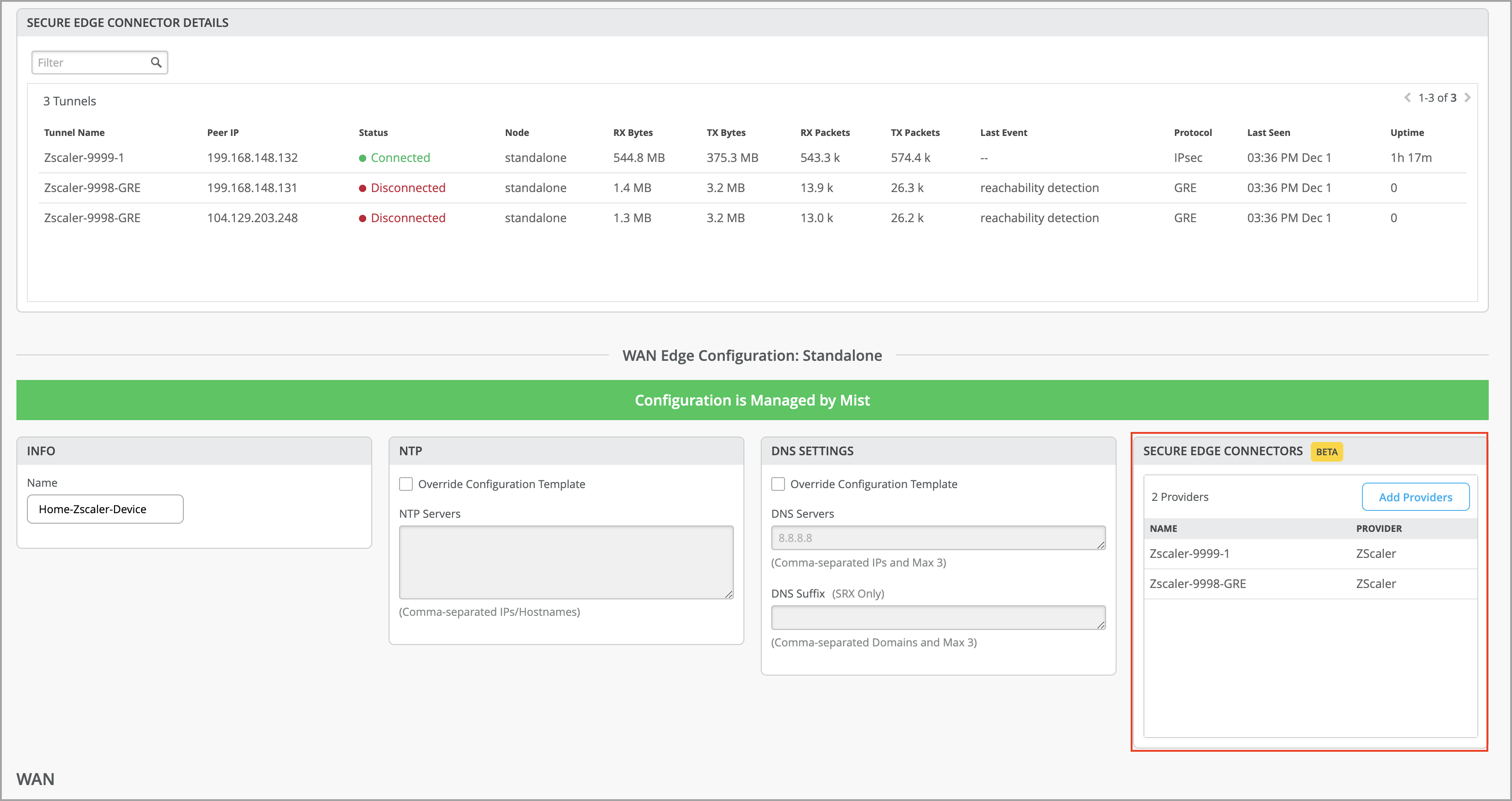
Secure Edge Connector Auto Provision Settings
You can configure gateway options per Zscaler location in Secure Edge Connector Auto Provision Settings on Juniper Mist portal. These settings offer additional control for configuring various traffic rules and policies, and they are optional parameters.
On Juniper Mist portal, select Organization > WAN Edge Templates or select WAN Edges > WAN Edges > WAN Edge Name.
- Scroll-down to Secure Edge Connectors.
- Select Zscaler (Auto) as the Secure Edge Connector. In the Secure Edge Connector Auto Provision Settings pane, you can define the gateway options.
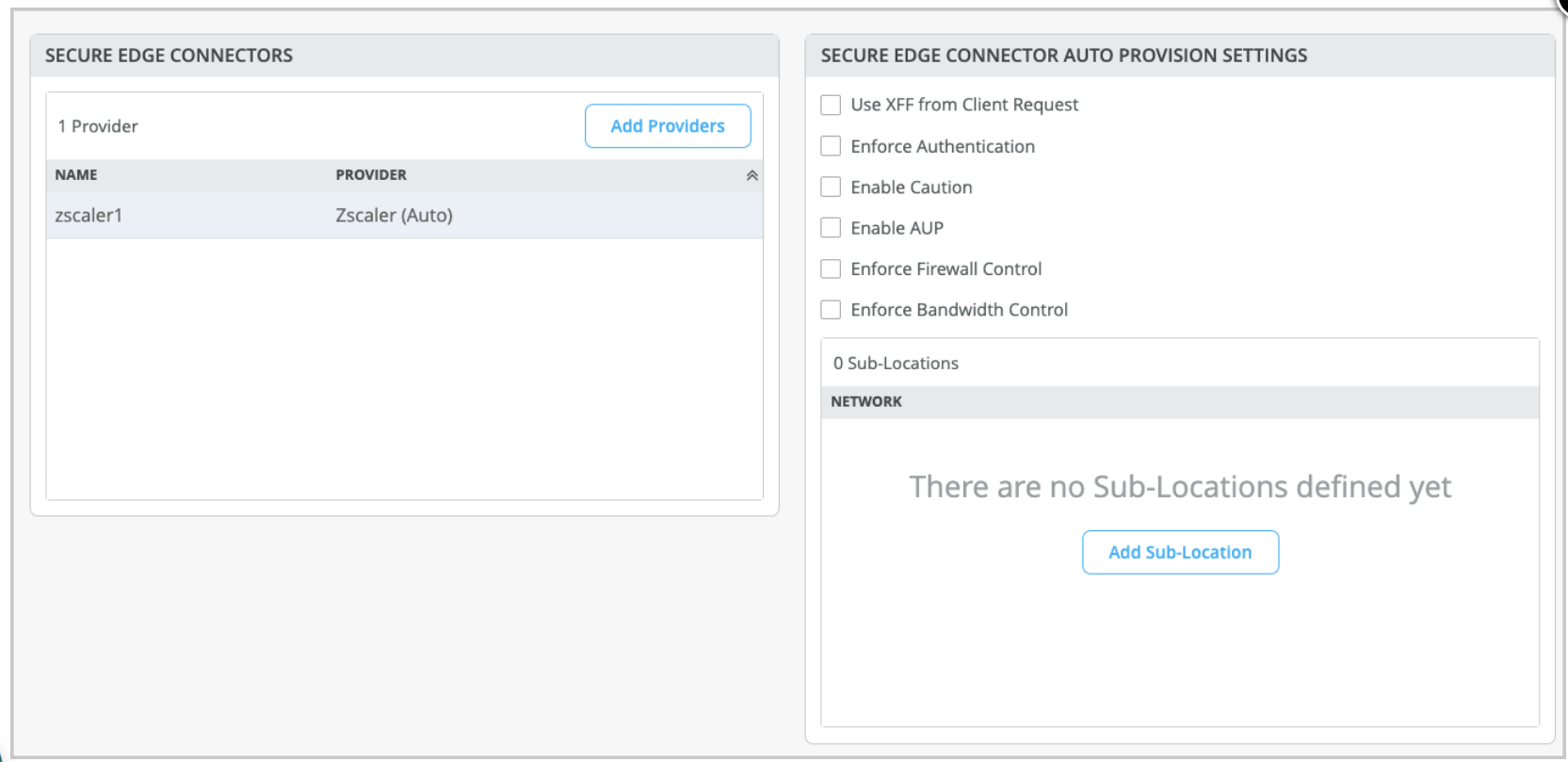
- Use XFF from Client Request—Enable this option if this location uses proxy chaining to forward traffic to the Zscaler service.
- Enforce Authentication—Enable this option if you want to authenticate users from this location.
- Enable Caution— Set the caution interval for more than one minute to display a caution notification for unauthenticated users. Use this option if you have disabled Enforce Authentication option.
- Enable AUP—Enable to display Acceptable Use Policy (AUP) for unauthenticated traffic and mandate it for the users to accept it. Use this option if you have disabled Enforce Authentication.
- Enforce Firewall Control—Enable the firewall control options.
- Bandwidth Control—Enforce bandwidth control for the location. You can specify the maximum bandwidth limits for upload and downloads.
Zscaler Auto-Tunnel Provisioning with Sub-Locations
Juniper Mist supports configuration and provisioning of Zscaler sub-locations. A Zscaler sub-location is a child entity of the location object. Locations identify the various networks from which your organization sends its Internet traffic. Sub-locations can be used for specific uses cases. For example, an organization can define a Zscaler sub-location for its corporate network, and another sub-location for its guest network, even if their traffic goes through the same IPsec tunnel.
The organization uses the sub-locations to:
- Implement different policies based on IP addresses.
- Enforce authentication for the internal corporate network, while disabling it for the guest network.
- Enforce bandwidth control for sub-locations while ensuring that unused bandwidth remains available to the parent location.
Juniper Mist supports sub-location provisioning as part of the tunnel orchestration process, and you can define the sub-location options using the Mist portal.
To configure Zscaler sub-locations:
On Juniper Mist portal, select Organization > WAN Edge Templates or select WAN Edges > WAN Edges > WAN Edge Name.
- Scroll-down to Secure Edge Connectors.
- Select Zscaler as the Secure Edge Connector. You'll see sub-location for the
site below Secure Edge Connector Auto Provision
Settings option. Figure 16: Add Sub-Location
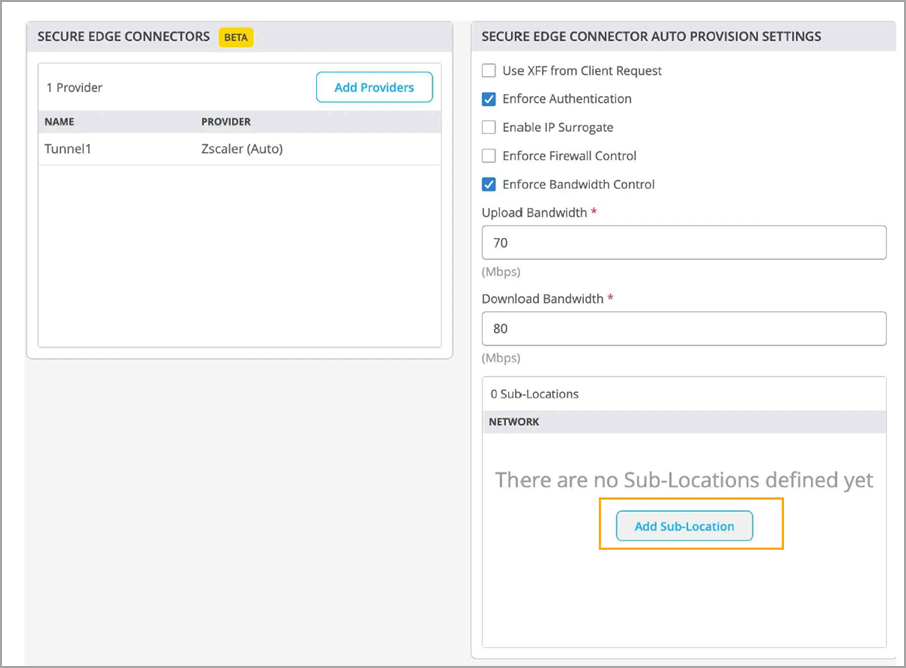
- Click Add Sub-Location to define the new sublocation.
The Add Sub-Location option is available only when you select Zscaler as the Secure Edge Connector.
- In the Add Sub-Location window, define settings for
the sub-location.Figure 17: Sub-Locations Settings
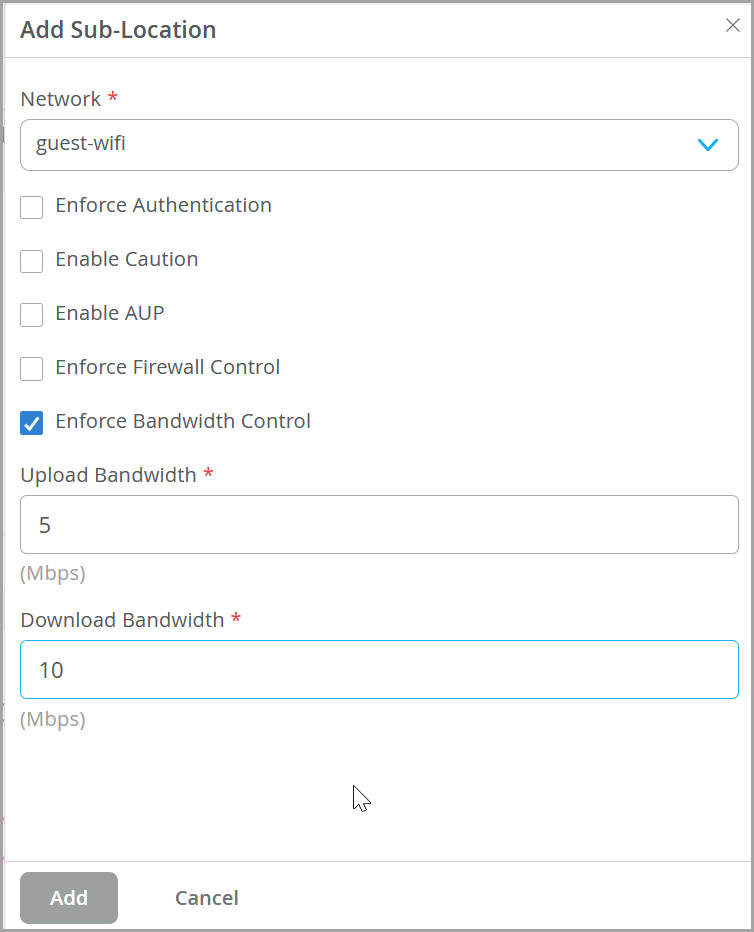
Network—Select an existing network from the drop-down box.
- Enforce Authentication—To authenticate users from this location.
- Enable Caution— Display a caution notification for unauthenticated users. Use this option if you have disabled Enforce Authentication option.
- Enable AUP—Enable to display Acceptable Use Policy (AUP) for unauthenticated traffic and mandate it for the users to accept it. Use this option if you have disabled Enforce Authentication. The custom AUP Frequency must be a number between 1 and 180.
- Enforce Firewall Control—Enable the firewall control options.
- Bandwidth Control—Enforce bandwidth control for the location. You can specify the maximum bandwidth limits for upload and downloads. Upload and download bandwidth must be a number between 0.1 and 99999.
View Sub-Locations in Zscaler Portal
You can view the newly created sub-location in Administration > Location Management on Zscaler portal. On the Locations page, when you click the sublocation's number within the table, the sub-locations for the location appear.
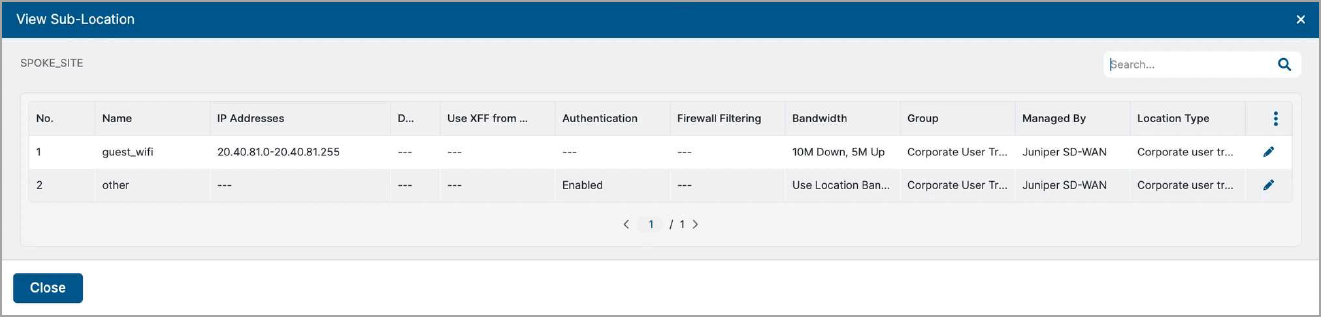
Verification and Troubleshooting
On Juniper Mist portal, you can verify the established tunnels details in WAN Insights of the device once WAN Edge Tunnel Auto Provision Succeeded event appears under WAN Edge Events.

If you are not able to establish the tunnel, the possible cause could be tunnel configuration issues or reachability issues from your device. You can use the following options to troubleshoot the issue:
- Check the Zscaler IP address or hostname configured on the Juniper Mist portal. Ensure that local ID and PSK configured on Zscaler account match with those configured on Juniper Mist portal.
- Ping the Zscaler public IP address from the WAN interface on your device and check if there are responses.
- Using the packet capture tool on the Mist portal. Run a PCAP on the WAN interface with Zscaler Public IP address as filter and check see if there is bidirectional packets. See Troubleshoot SRX Series Firewalls Using Packet Captures.
- If your security device is sending packets to Zscaler and there is no response
from the Zscaler, do following:
- Check if the Zscaler IP address is active
- Check if any uplink router is blocking the traffic flow
- Check NAT configuration if applicable
Note that the packet capture results help you to detect the above issues.
