- play_arrow Overview
- play_arrow Platform Considerations
- play_arrow WAN Configuration for Session Smart Routers
- WAN Assurance Configuration Overview
- Configure Sites and Variables for Session Smart Routers
- Configure Networks for Session Smart Routers
- Configure Applications for Session Smart Routers
- Configure Application Policies on Session Smart Routers
- Configure Hub Profile for Session Smart Routers
- Configure Path Selection from Hub-to-Spoke with Traffic Steering
- Configure WAN Edge Templates for Session Smart Routers
- Routing Configuration on Session Smart Routers
- Onboard Session Smart Routers for WAN Configuration
- Onboard Session Smart Routers with Static IP Address
- IDP-Based Threat Detection on Session Smart Routers
- Upgrade a WAN Edge Session Smart Router
- Configure VRF Route Leaking for Session Smart Routers
- Revoke DHCP Lease on a WAN Edge Device
- Reserve DHCP IP Address
- play_arrow WAN Configuration for SRX Series Firewalls
- WAN Assurance Configuration Overview
- Configure Sites and Variables for SRX Series Firewalls
- Configure Applications for SRX Series Firewalls
- Configure Networks for SRX Series Firewalls
- Configure Application Policies on SRX Series Firewalls
- Configure Hub Profiles for SRX Series Firewalls
- Configure WAN Edge Templates for SRX Series Firewalls
- Routing Configuration on SRX Series Firewalls
- Onboard SRX Series Firewalls for WAN Configuration
- IDP-Based Threat Detection for SRX Series Firewalls
- Enable Application Visibility on SRX Series Firewalls
- Monitor the Service Status of SRX Series Firewalls
- Upgrade a WAN Edge SRX Series Firewalls
- Configure a Custom VR for SRX Series Firewalls
- Revoke DHCP Lease on a WAN Edge Device
- Reserve DHCP IP Address
- play_arrow Secure Edge Connector
- play_arrow Cellular Edges
- play_arrow Monitor and Troubleshoot
- WAN Assurance Monitoring, SLE, and Troubleshooting Overview
- Monitor SRX Series Firewall Deployed as WAN Edge
- Monitor Session Smart Router Deployed as WAN Edge
- Service-Level Experiences for Session Smart Router Deployed as WAN Edge
- Troubleshoot Session Smart Router Deployed as WAN Edge
- Speed Tests for Session Smart Router Deployed as a WAN Edge (BETA)
- Dynamic and Manual Packet Captures
- Troubleshoot SRX Series Firewalls
- Replace a WAN Edge Device
- WAN Edge Testing Tools
Full Stack Design for Session Smart Routers
The Juniper® SD-WAN driven by Mist AI™ Full Stack design example is a follow-up to the Session Smart™ Router Mist WAN Assurance deployment documentation found in the Juniper Mist WAN Configuration Guide.
Overview
With this example you’re expanding network capabilities by integrating Mist APs and Juniper EX Switches. This is more than just WAN Assurance, it’s the Juniper AI Driven Enterprise. This full stack guide shows you how to set up your Juniper SD-WAN Session Smart WAN edge devices in concert with Mist wireless Access Points (APs) deployed in Wireless Assurance, and Juniper EX Series Switches deployed in Wired Assurance. This brings all your network devices into a cohesive onboarding, monitoring, and troubleshooting dashboard.
The Session Smart Full Stack Guide begins at the highest level of WAN Assurance, focusing on a key component known as the Session Smart Router. After completing the Juniper Validated Design (JVD) topology found in the Juniper Mist WAN Configuration Guide, you should already have this WAN Edge device deployed in a hub and spoke network. The Session Smart Router serves as the WAN edge device and foundation for building out your entire network. We'll evaluate and test the complete end-to-end solution to further optimize your network. This test encompasses the entire technology stack and is specifically designed for a branch that utilizes Juniper equipment.
For successful implementation of this guide, you'll need at least one Juniper EX Switch to onboard into the Mist cloud. If you plan to do advanced testing with virtual circuits, two EX Switches is ideal. Additionally, you can incorporate a Mist AP into the setup to enhance the wireless capabilities of the network. Onboarding those into your LAN network for Mist management gives admins the Juniper AI Driven Enterprise to monitor and manage their WAN edge, switches, and APs all in the Mist dashboard.
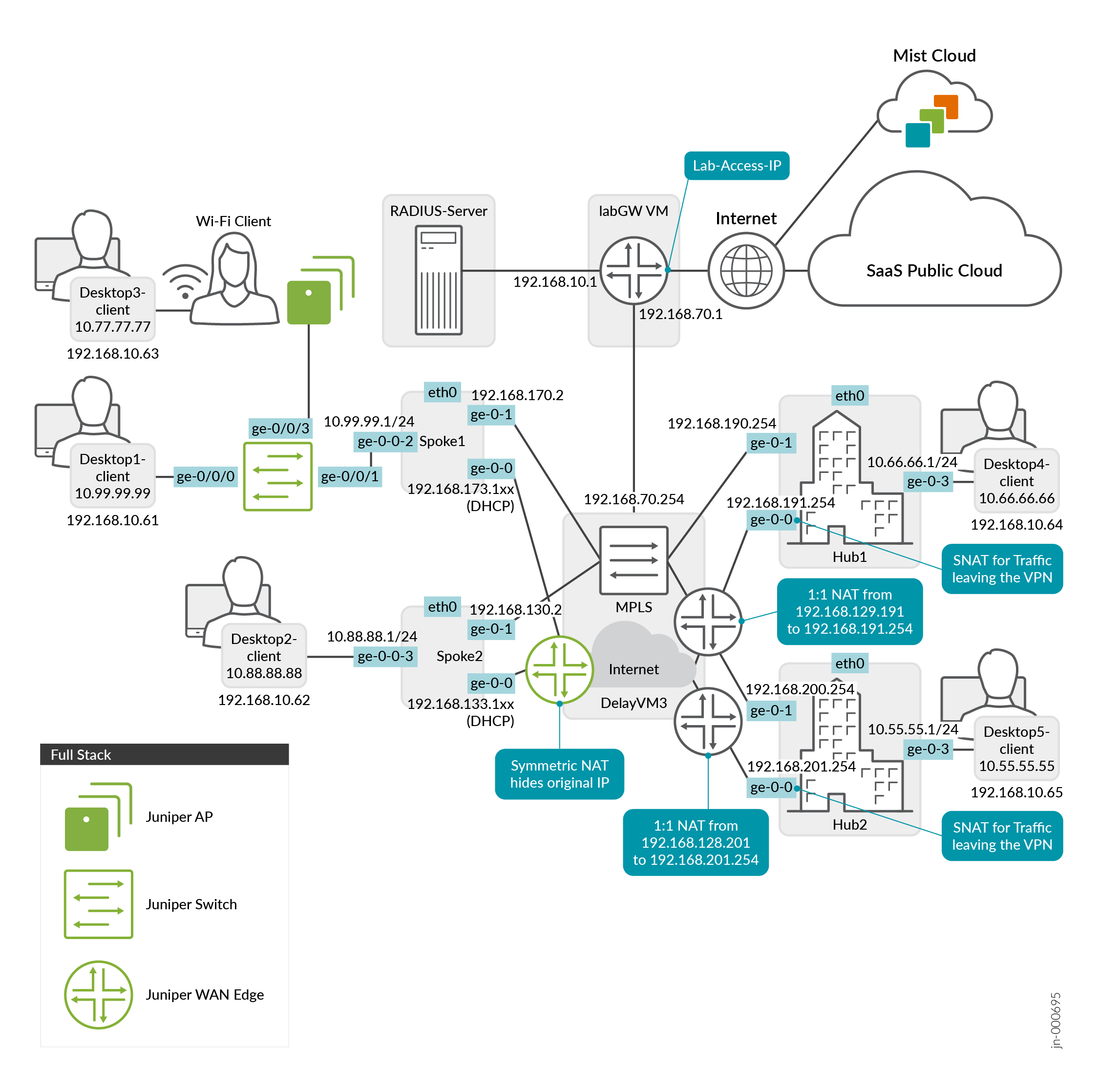
Figure 1 shows the Full Stack Juniper Mist WAN Assurance topology used in this example.
Requirements
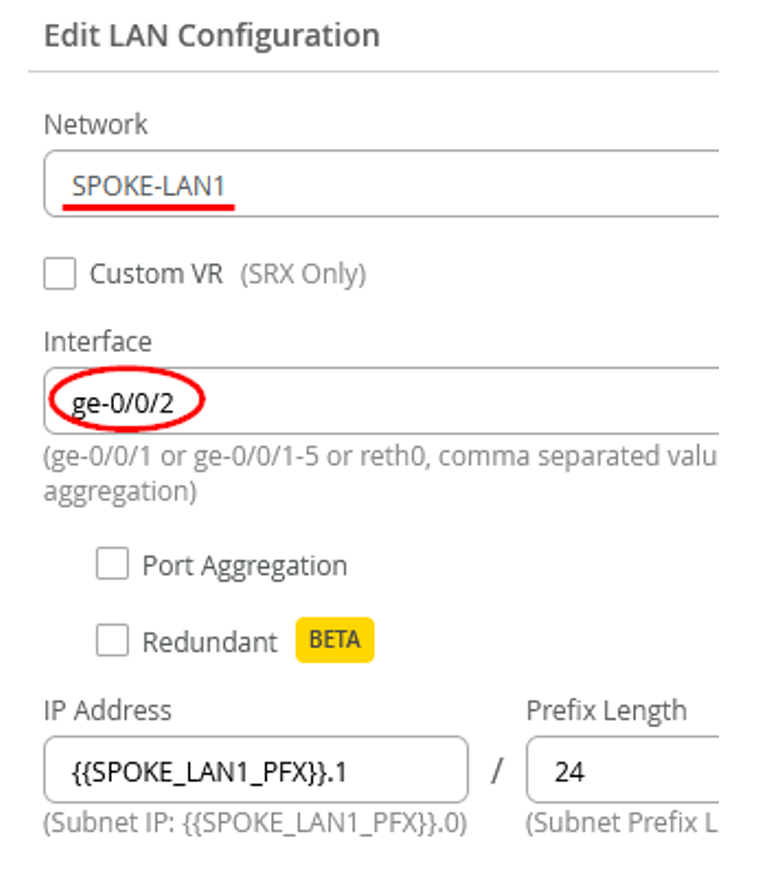
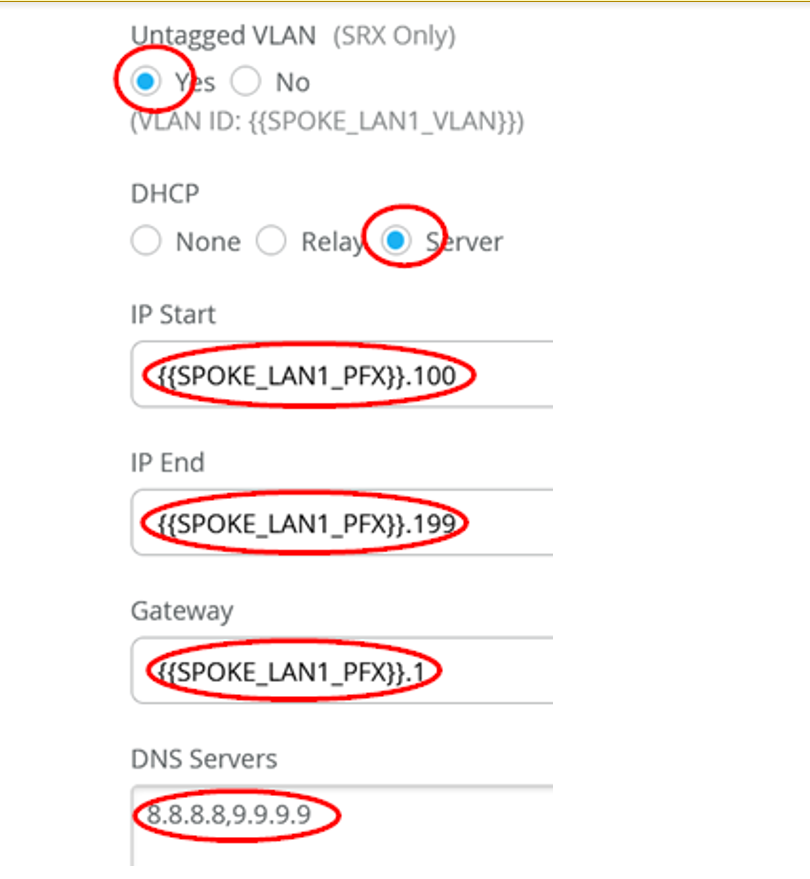
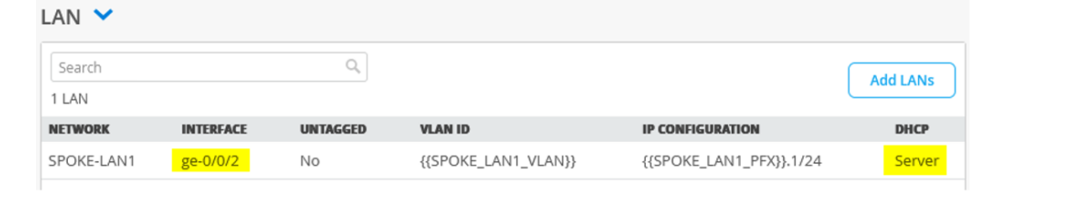
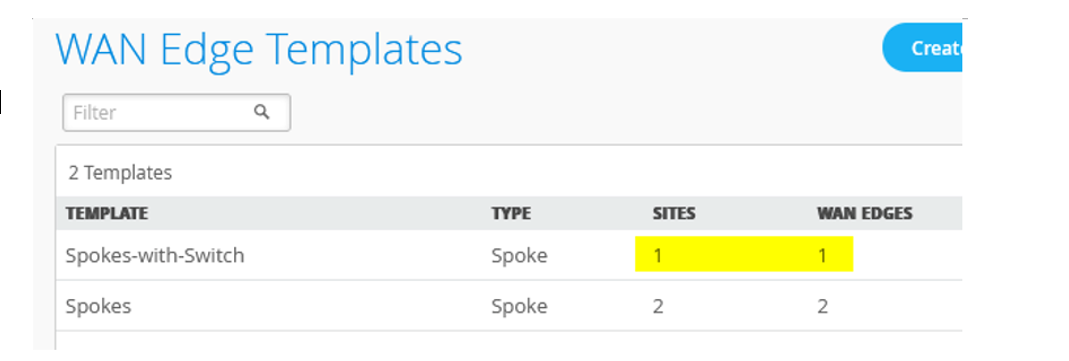
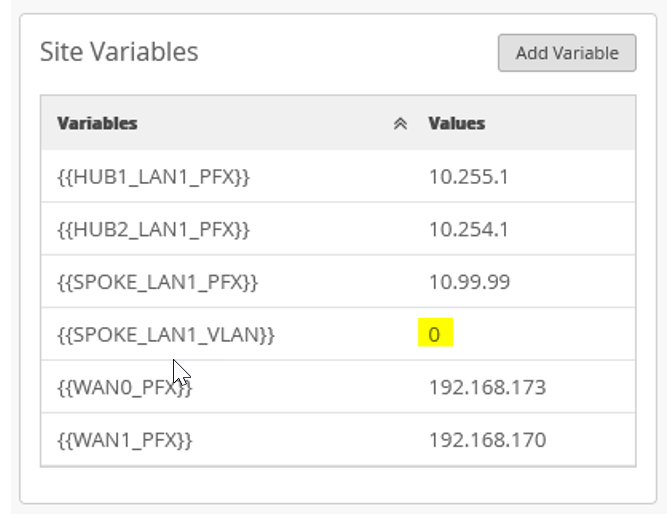
To get started, you’ll need to alter some of the interfaces found in the Juniper Mist WAN Configuration Guide topology. We’ll show you how to do this using a Spokes configuration template found in the Mist WAN Configuration Guide. See Configure WAN Edge Templates for Session Smart Routers.
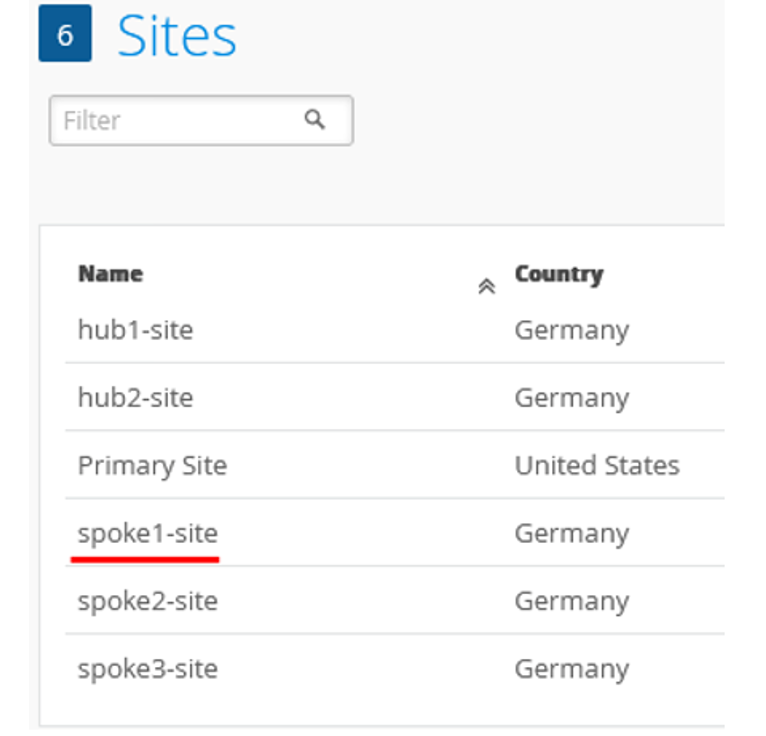
- Desktop3 VM (VLAN1077) is re-used and no longer attached to Spoke3. Desktop3 VM is now a viewer for the Raspberry Pi, the Wireless Client. Alternatively, you could use a local notebook.
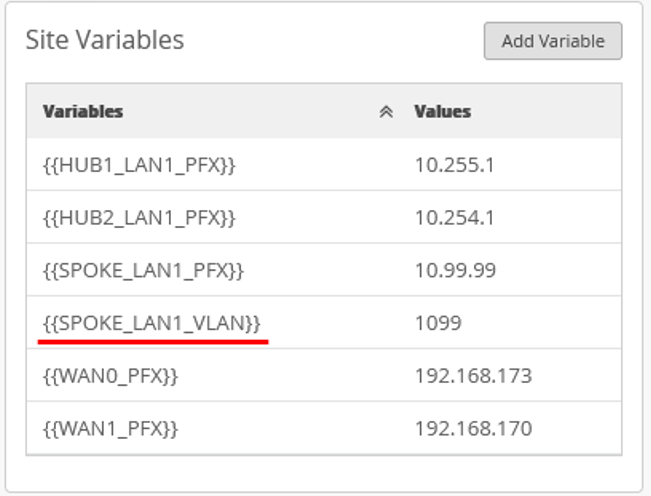
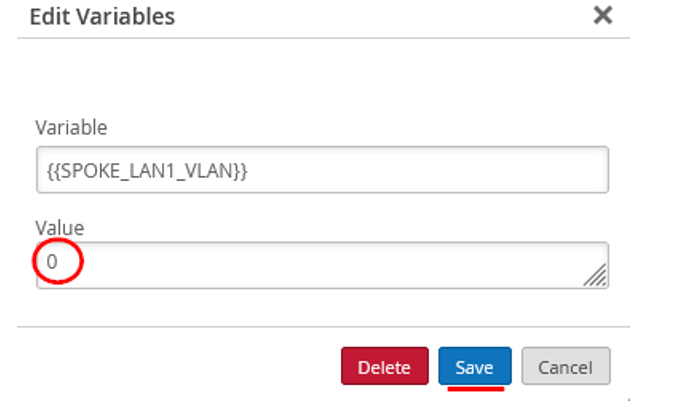
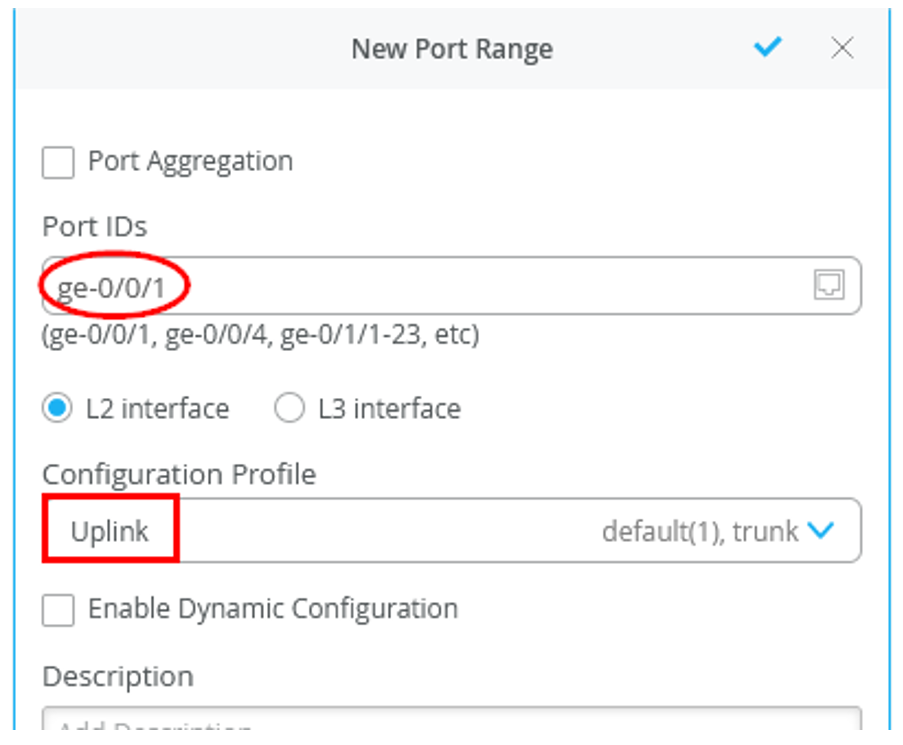
- Desktop1 VM (VLAN1099) is no longer directly attached to Spoke1 and needs to be re-attached to the interface ge-0/0/0 of the new branch switch.
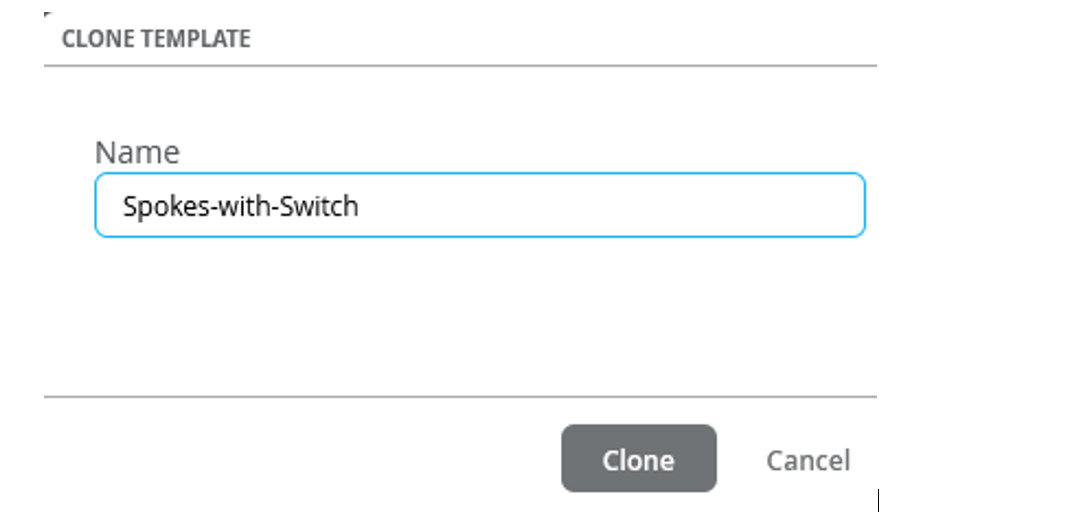
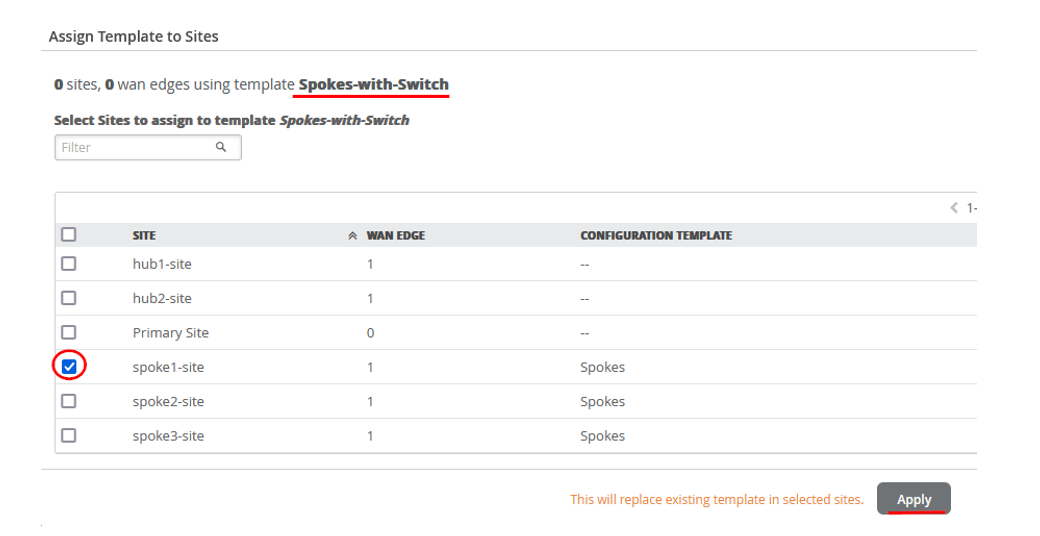
Create a New Spokes Configuration Template
To create a new spokes configuration quickly and efficiently, you can clone the template for an existing spoke and then make the necessary changes. It makes things much easier.
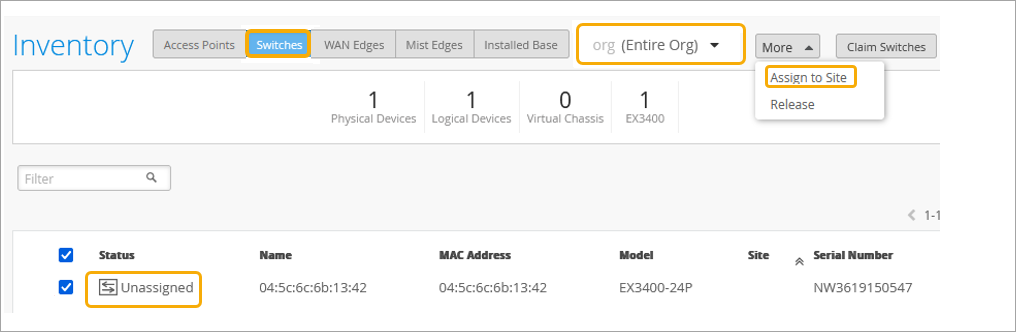
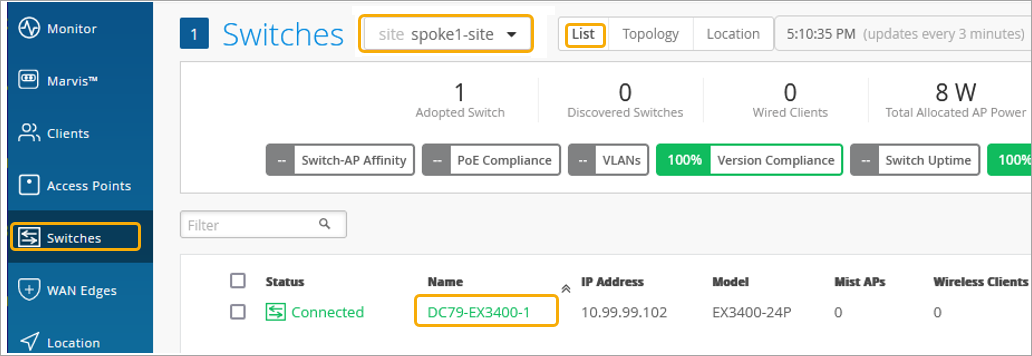
Add Your Switch to the Topology
Now it is time to onboard your switch and add it to your infrastructure. For details on how to onboard your switch, refer to the product documentation for your switch in the Juniper TechLibrary.
For details on getting a new cloud-ready EX switch up and running in the Juniper Mist AI cloud portal, see Cloud-Ready EX and QFX Switches with Mist.
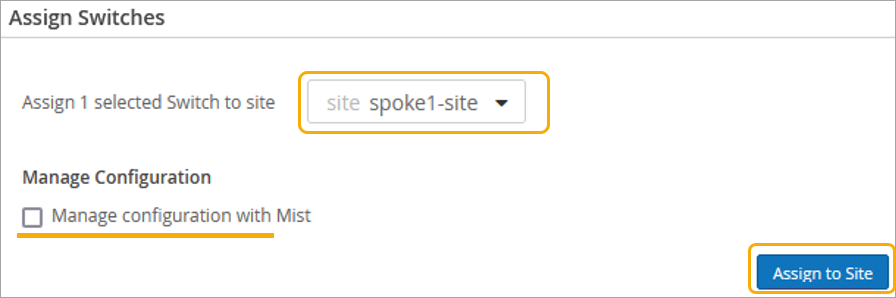
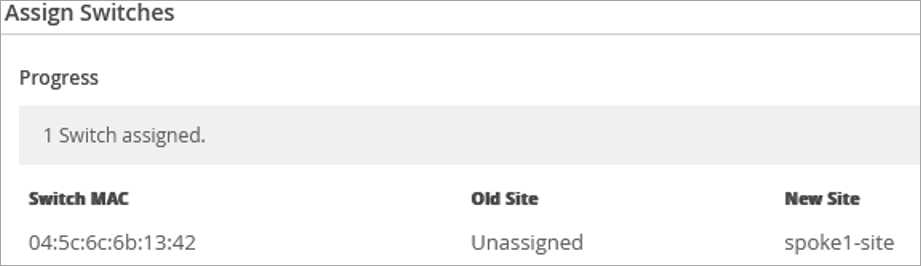
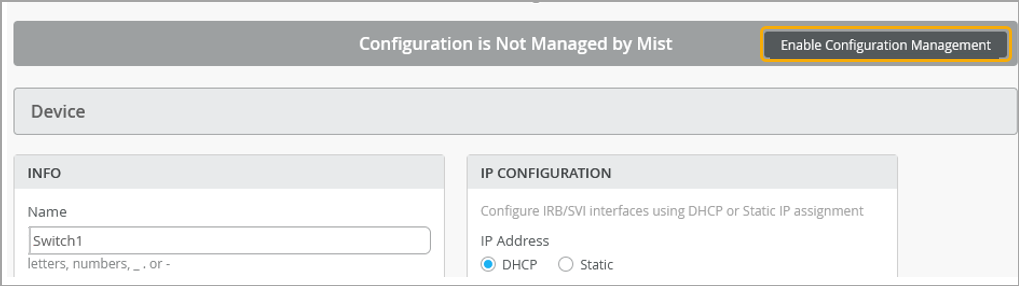
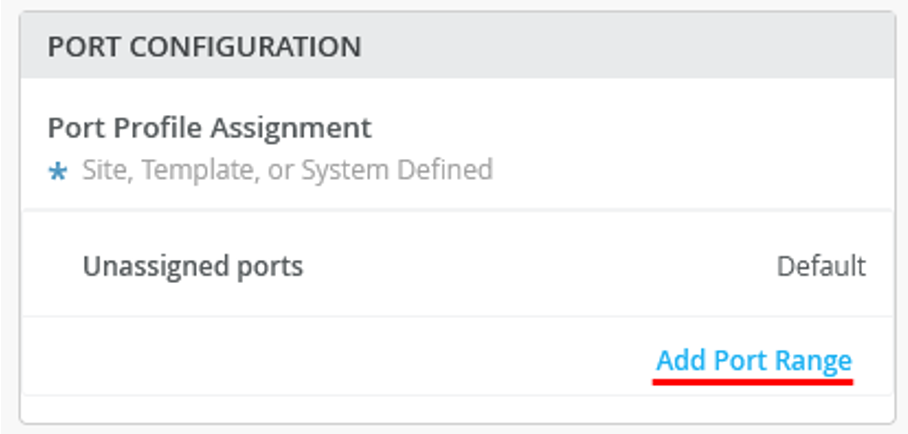
To assign a switch to a site: