Content Security Overview
Content Security is a term used to describe the consolidation of several security features into one device to protect against multiple threat types. The advantage of Content Security is a streamlined installation and management of multiple security capabilities.
The following security features are provided as part of the Content Security solution:
-
Antispam—This feature examines transmitted messages to identify e-mail spam. E-mail spam consists of unwanted messages usually sent by commercial, malicious, or fraudulent entities. When the device detects an e-mail message deemed to be spam, it either drops the message or tags the message header or subject field with a preprogrammed string. The antispam feature uses a constantly updated Spamhaus Block List (SBL). Sophos updates and maintains the IP-based SBL.
-
Full file-based antivirus—A virus is an executable code that infects or attaches itself to other executable code to reproduce itself. Some malicious viruses erase files or lock up systems. Other viruses merely infect files and overwhelm the target host or network with bogus data. The full file-based antivirus feature provides file-based scanning on specific application layer traffic, checking for viruses against a virus signature database. The antivirus feature collects the received data packets until it has reconstructed the original application content, such as an e-mail file attachment, and then scans this content. Kaspersky Lab provides the internal scan engine.
-
Express antivirus—Express antivirus scanning is offered as a less CPU-intensive alternative to the full file-based antivirus feature. The express antivirus feature is similar to the antivirus feature in that it scans specific application layer traffic for viruses against a virus signature database. However, unlike full antivirus, express antivirus does not reconstruct the original application content. Rather, it just sends (streams) the received data packets, as is, to the scan engine. With express antivirus, the virus scanning is executed by a hardware pattern-matching engine. This improves performance while scanning is occurring, but the level of security provided is lessened. Juniper Networks provides the scan engine.
-
Content filtering—Content filtering blocks or permits certain types of traffic based on the MIME type, file extension, protocol command, and embedded object type.
-
Web filtering—Web filtering lets you manage Internet usage by preventing access to inappropriate Web content. The following types of Web filtering solutions are available:
-
Integrated Web filtering—Blocks or permits Web access after the device identifies the category for a URL either from user-defined categories or from a category server (Websense provides the SurfControl Content Portal Authority (CPA) server).
-
Redirect Web filtering—Intercepts HTTP requests and forwards the server URL to an external URL filtering server to determine whether to block or permit the requested Web access. Websense provides the URL filtering server.
-
Juniper local Web filtering—Blocks or permits Web access after the device identifies the category for a URL from user-defined categories stored on the device.
-
Content Security Licensing
All Content Security components require licenses with the exception of content filtering with custom URLs only. This is because Juniper Networks leverages third-party technology that is constantly updated to provide the most up-to-date inspection capabilities. Licenses can be purchased individually or as bundled licenses with other features like AppSecure and IPS. The licenses are term based.
Content Security Components
Content Security components include custom objects, feature profiles, and Content Security policies that can be configured on SRX Series devices. From a high-level, feature profiles specify how a feature is configured and then applied to Content Security policies, which then in turn is applied to firewall policies, as shown in Figure 1.
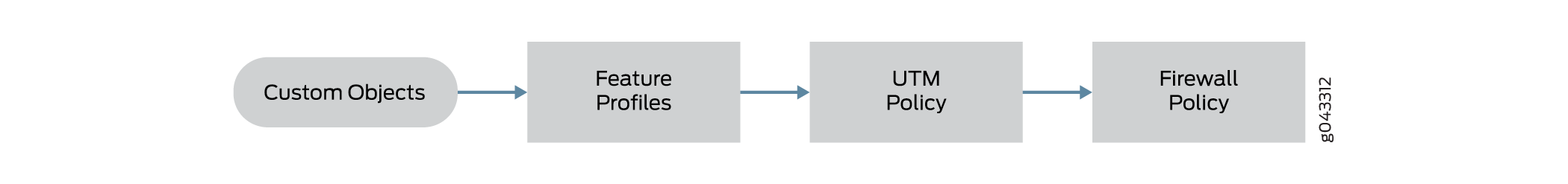
Content Security profiles do not have their own seven-tuple rulebase; in a sense they inherit the rules from the firewall rule. The strength of the Content Security feature comes from URL filtering, where you can have a separate configuration for different users or user groups.
-
Custom Object—Although SRX Series Firewalls support predefined feature profiles that can handle most typical use cases, there are some cases where you might need to define your own objects, specifically for URL filtering, antivirus filtering, and content filtering.
-
Feature Profiles—Feature profiles specify how components of each profile should function. You can configure multiple feature profiles that can be applied through different Content Security policies to firewall rules.
-
Content Security Policies—Content Security policies perform as a logical container for individual feature profiles. Content Security profiles are then applied to specific traffic flows based on the classification of rules in the firewall policy. This allows you to define separate Content Security policies per firewall rule to differentiate the enforcement per firewall rule. Essentially, the firewall rulebase acts as the match criteria, and the Content Security policy is the action to be applied.
-
Firewall Policy—You can predefine feature profiles for the Content Security policy that are then applied to the firewall rules. This gives you the advantage of using the predefined Content Security policy for that one Content Security technology (for example, antivirus or URL filtering), not both.
