NSM Migration
Before You Begin
Migrating policies from NSM requires the NSM database to be exported in .xdiff format. You must copy this file to your local machine and provide its path to migrate policies from NSM to Security Director.
Starting in Junos Space Security Director Release 16.2, you can migrate firewall and NAT policies from Network and Security Manager (NSM) to Security Director for a set of devices. All objects supported by Security Director (addresses, services, address groups, service groups, and schedulers) can be imported with the policy, with the exception of polymorphic objects. Rules referring to unsupported objects are disabled after the migration. For example, if a firewall policy rule is configured with the VPN tunnel or if a NAT pool is configured with a routing instance, such rules are disabled after the migration.
At any time, only a single migration from the NSM workflow can be triggered on Security Director. Figure 1 shows the device import workflow.
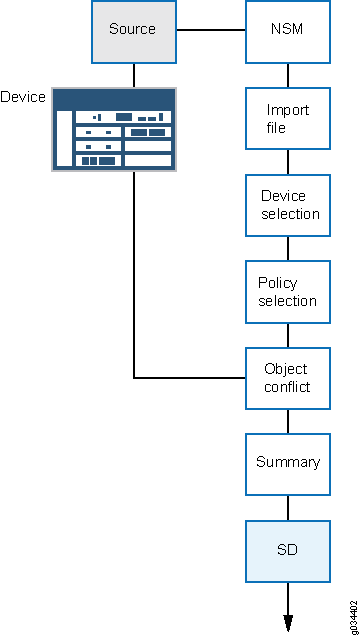
You can migrate policies from the NSM database (for the NSM Release 2010.3 to Release 2012.2) into Security Director.
The following NSM features are supported during the migration:
-
Firewall policies with global rules (including support for the global address book)
-
NAT policies with support for the global address book
-
Nested address group support (Junos OS Release 11.2 and later)
-
Negate address group support in firewall rules
-
Service offload support in firewall rules
-
Source address or source port option in static NAT
-
Source port option in source NAT
NSM to Security Director migration is not supported for ScreenOS devices.
To import policies from NSM:
-
If a group has more than 300 rules, Security Director automatically breaks the group into multiple rule groups, each containing 400 rules. The only exception is that these groups are placed last in the list of groups. The size of the last group is calculated by the upper threshold of 300 rules and lower threshold of 100 rules.
-
_DE is affixed to the device specific policies name by Security Director. You cannot directly assign device specific policies to a group policy. Assign devices to the device specific policies first, and then assign those devices to the group policies.
-
_PRE is affixed to the group policy names that are added before the device specific policies and _POST is affixed to the group policy names that are added after the device specific policies.
Change History Table
Feature support is determined by the platform and release you are using. Use Feature Explorer to determine if a feature is supported on your platform.
