ON THIS PAGE
LDAP Provider
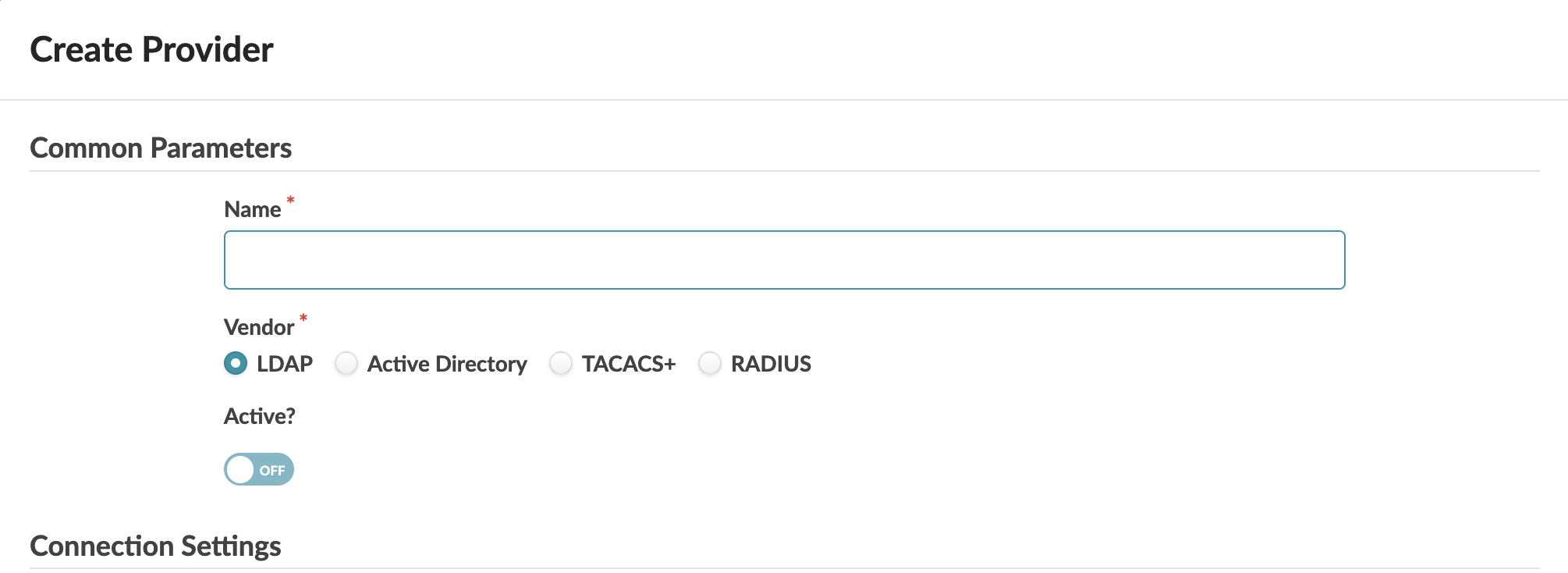
Create LDAP Provider
Lightweight Directory Access Protocol (LDAP)
Configure LDAP Provider
To authorize Apstra users via a LDAP provider, the LDAP server must be configured to properly return a provider group attribute. This attribute must be mapped to a defined Apstra Role. The example configuration below is for the open-source OpenLDAP server.
dn: ou=People,dc=example,dc=com objectClass: organizationalUnit ou: People dn: ou=Groups,dc=example,dc=com objectClass: organizationalUnit ou: Groups dn: cn=user,ou=Groups,dc=example,dc=com gidNumber: 5000 cn: user objectClass: posixGroup memberUid: USER1 dn: cn=USER1,ou=People,dc=example,dc=com cn: USER1 givenName: USER1 loginShell: /bin/sh objectClass: inetOrgPerson objectClass: posixAccount uid: USER1 userPassword: USER1 uidNumber: 10000 gidNumber: 5000 sn: USER1 homeDirectory: /home/users/USER1 mail: USER1@example.com
The user group must be mapped to a defined Apstra Role.
After configuring and activating a provider, you must map that provider to one or more user roles to give access permissions to users with those roles.