WLAN Options
Get familiar with the various options available on the WLAN settings page, and configure features such as security, radio band, geofence, peer-to-peer isolation, and more.
Navigating to the WLAN Settings Window
-
For a WLAN in a WLAN template, select Organization > Wireless | WLAN Templates from the left menu, then create a WLAN template or select an existing template. To add a WLAN to your template, click Add WLAN. To edit an existing WLAN in the WLANs list, click it.
-
For a site-level WLAN, select Site > Wireless | WLANs from the left menu, and then click Add WLAN. To edit an existing WLAN on the WLANs page, click it.
-
Some changes will reset the radio. See WLAN Changes That Reset The Radio for more information.
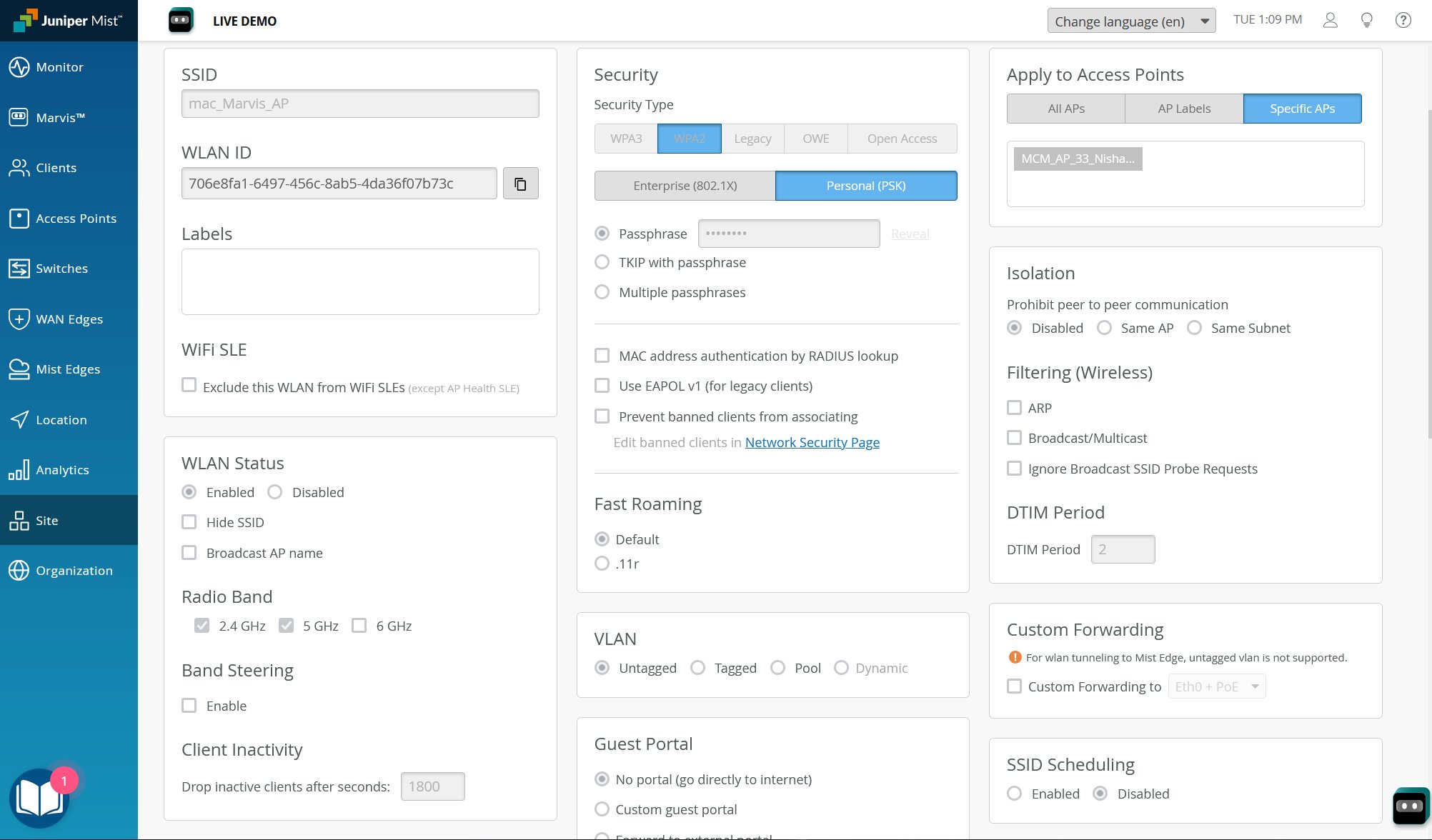
WLAN Configuration Settings
| Setting | Summary |
|---|---|
| SSID |
This is the name the WLAN will broadcast for clients to see. While you can configure as many as 15 service set identifiers (SSIDs) per radio, a good rule of thumb for device profiles and WLAN templates is to use only two or three WLANs per AP. The idea is to minimize the airtime overhead incurred by beacon management frames, which are sent every 102.4 ms per radio, at the Minimum Basic Rate (MBR). In other words, unless you are carefully considering data rates and co-channel contention in order to achieve four, six, or even eight active WLANs on an AP, we recommend two or three WLANs per AP max. |
| Wi-Fi SLE |
Select the check box if you want to mark this WLAN as an "excluded WLAN" for your Wireless Service Level Expectations (SLEs). For example, you might want to exclude a test WLAN or a new WLAN that you're fine-tuning. When viewing the Wireless SLEs dashboard, you can hide or show any excluded WLANs. This exclusion applies to all SLE metrics except AP Health, which includes all WLANs without exception. |
| WLAN Status |
Use this to set whether an AP broadcasts the WLAN. You can also do the following:
|
| Radio Band |
Choose which radio frequencies to broadcast on the WLAN: 2.4 GHz, 5 GHz, or 6 GHz. Wireless clients typically experience better performance when connected to the 5-GHz band rather than the 2.4-GHz band because the 5-GHz band has more channels, and therefore, less co-channel interference. The 6-GHz band has still more channels, wider channels, more advanced security options, and greater data rates. |
| Client Inactivity |
You configure an inactivity timer on your WLAN to prevent congestion. The AP deauthenticates inactive clients, as defined by the time you set here. The range for the inactivity timer is between 60 and 86400 seconds. The default time is 1800 seconds. |
| Geofence |
Geofencing can prevent clients with a received signal strength indicator (RSSI) below a specified level from joining the network. You can set a minimum client RSSI, per radio band, to prevent clients who are beyond a given distance or range from joining the WLAN. Geofencing applies only to the initial association. Therefore, if a client is already associate with the network, the client will not be dissociated if its RSSI value falls below the configured threshold. The default is disabled for all radio-bands. See Enable Geofencing. |
| Data Rates |
Set data rates to prevent clients with slow connections from degrading the overall WLAN performance. The default is Compatible, which allows all connections. The other options are:
|
| Wi-Fi Protocols | Enable or disable various versions of Wi-Fi. When you enable a Wi-Fi version, its features become available on the APs that support that protocol. |
| WLAN Rate Limit |
Use WLAN rate limits to set uplink and downlink limits for the WLAN bandwidth. You can configure rate limits per AP, per client, and per application. You can also limit the total bandwidth allocation for a given application. The rate limit field also supports site-level variables per WLAN and per client, as an option to hard-coding the values (that is, making them global). This is especially useful in WLAN templates, where you want to configure a core configuration for common use, but also want the flexibility of site-specific differences. You can add variables on the Organization > Admin > Site Configuration page. Note:
Depending on your exact use-case, setting a rate limit may be self-defeating in wireless networks because it can increase the client's airtime consumption. Since airtime is usually the most precious resource in wireless networks, consuming more of it by rate-limiting the comparatively plentiful bandwidth often ends up degrading your overall network performance. |
| Per-Client Rate Limit |
Set the uplink and downlink rate per client. Note:
Mist applies this rate limit to all wireless clients on the selected SSID. There is no way to tune the limits on an individual client basis. The effect of setting values in these fields is to limit each and every wireless client to the uplink and downlink values you set. |
| Application Rate Limit |
This option limits the uplink or downlink rate per client for the specified application. You must identify applications by their name or hostname. |
| Apply to Access Points |
Select the APs you want this WLAN to apply to: All, Specific, or according to the AP label. By default, all APs in a selected site or site group will get the WLAN configuration and beacon the SSID. Based on the use-case or the requirements, you can apply filters to have the WLAN configured only on AP labels or Specific APs. Note:
You can create labels at the organization or site level. From the left menu, select Organization > Wireless > Labels or select Site > Wireless > Labels. 1. Give your label a name. 2. Select a Label Type of Access Point. 3. Under Label Values, click the plus sign to Add Access Point, then select the Entire Org tab or the Site tab. 4. Select the AP Name checkbox at the top to select all APs in the org or site, or you can select the checkboxes next to whichever APs as you would like to include in this label.
5. Apply the AP label to your WLAN so that only the APs included in the label get the needed WLAN configuration. |
|
Security Types |
WPA3 is the default security type when you create a new WLAN. Both WPA3 and OWE are required for Wi-Fi 6E and Wi-Fi 7. If you want to use security modes such as WPA2 or Open, you need to disable both 6 GHz and Wi-Fi 7 in the WLAN.
|
| Other Security Options |
Depending on the selected security type, other options include:
|
|
VLAN |
|
| Isolation |
Peer-to-peer isolation prevents Layer 2 peer traffic on the same WLAN, AP, or wired or wireless subnet. This option is disabled by default. (For Layer 3 filtering, you can create WxLAN policies.) Subnet isolation requires firmware version 0.12 or later, and clients must have a DHCP address. |
Filtering (Wireless)
|
These filters reduce the amount of management frames sent by APs in the WLAN. Filtering can significantly improve performance by freeing up radio air time which is otherwise consumed as a routine part of the operational overhead.
|
| Custom Forwarding | By default, the WLAN forwards tagged or untagged client traffic
through the primary Ethernet port, Eth0. You use custom forwarding
in conjunction with Mist Edge, or for example, to ensure that guest
and corporate traffic use different networks. You can set custom
forwarding to:
|
| SSID Scheduling |
You use this option to have the WLAN broadcast the SSID only on certain days and times. When scheduled to be disabled, the AP will not broadcast the SSID (that is, the SSID will not be visible to clients searching for available networks). The change in broadcast status does not reset the radio or disable the AP. SSID scheduling supports multiple time ranges for each day. By default this mode is disabled. |
|
802.1X Web Redirect |
Applies to VLANs with security type Enterprise (802.1X). Select the Enabled check box to redirect a client to a particular web page (for example, a quarantined portal for compliance checks) after it completes the 802.1X authentication. For this feature to work, your firmware version must be 0.7 or newer. For more information, see Configure an 802.1X WLAN to Redirect Clients to Specific Web Pages. |
| QoS Priority |
Use quality of service (QoS) to prioritize traffic so that the more important traffic does not get held up in a queue during congestion. Juniper APs can prioritize wireless traffic to optimize the shared radio for maximum application performance. Wi-Fi Multimedia (WMM) is a Wi-Fi Alliance specification based on the IEEE 802.11e wireless QoS standard to support traffic prioritization. This specification uses the following access categories to prioritize transmission:
|
| Multimedia Extensions |
When multiple concurrent applications compete for network resources, Juniper APs can use MMEs to define and improve the wireless signal quality and performance. Multimedia extensions (MMEs) are architectural extensions to general-purpose processors to boost the performance of multimedia workloads. Throughput is not guaranteed by WMM. |
| AirWatch |
AirWatch™ is 3rd-party mobile device management system. When this setting is enabled, the APs allow traffic to pass only for those clients already identified in the AirWatch console. If enabled, you need to specify the AirWatch console URL, the API key, and your login credentials for the managed devices. |
| Bonjour Gateway |
Default is not configured. Configure this setting on a per WLAN basis, from either the WLAN configuration page or WLAN Templates. This feature automatically enables broadcast/multicast filtering. As such, be sure to select the option to allow mDNS frames. The following services are available, but must explicitly enabled to be discoverable:
|
| Security |
Supports WPA3, WPA2, Legacy, OWE, and Open Access, with either Enterprise (802.1X) and Personal (SAE), as well as single or multiple passphrases, TKIP, etc. See: |
| Fast Roaming |
Enable fast roaming to allow clients that are connected to the network using WPA2 or WPA3 security to remain connected as they roam between APs. With fast roaming, WPA2 and WPA3 clients do not need to re-authenticate with the authentication server every time they change APs in the same network.
|
| VLAN |
Required for each WLAN. Specify the type of VLAN the AP will use in the switch connection.
For information about using VLAN Pools with Pre-Shared Keys for segmentation, see Leveraging Roles in a PSK (Use Case). |
| Guest Portal |
You can enable guest access by creating a sign-in portal in Juniper Mist, using your own external portal, or enabling Single Sign-On. For more information, see WLAN Guest Portal. |
