Use Microsoft® Azure for Guest Portal Single Sign-On
Use this information if you want to integrate with Microsoft® Azure to authenticate guest users.
When you configure a WLAN in the Juniper Mist™ portal, you can set up a guest portal that allows users to sign on by using an Identity Provider (IdP). This topic provides tips for using Microsoft® Azure. You'd follow similar steps for other IdPs.
Set up your application in Microsoft Entra ID (previously Azure Active Directory):
-
Set up an application in Microsoft Entra ID (Azure AD) with single sign-on enabled.
-
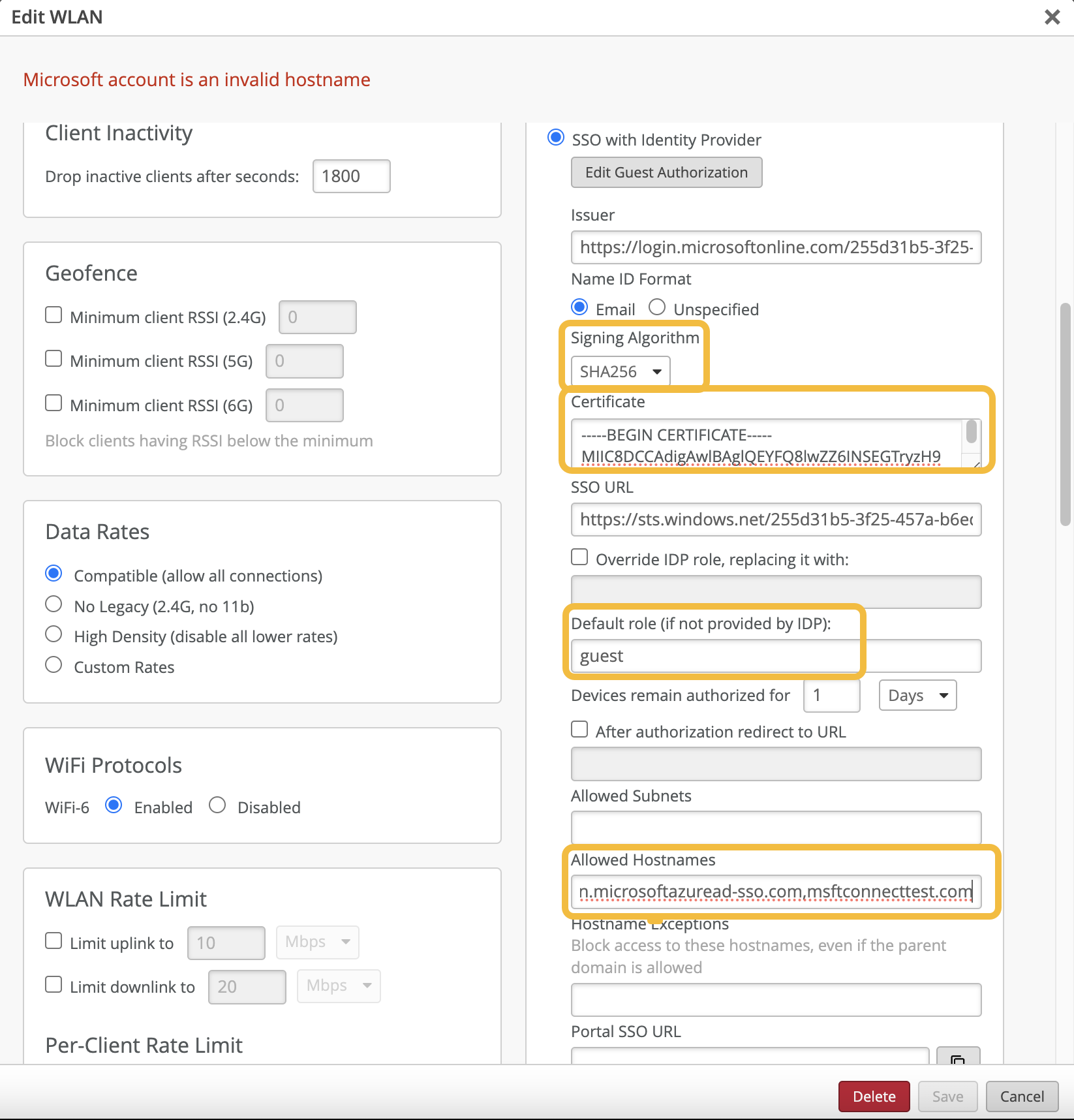
Choose SAML (Security Assertion Markup Language) as the single sign-on method.
-
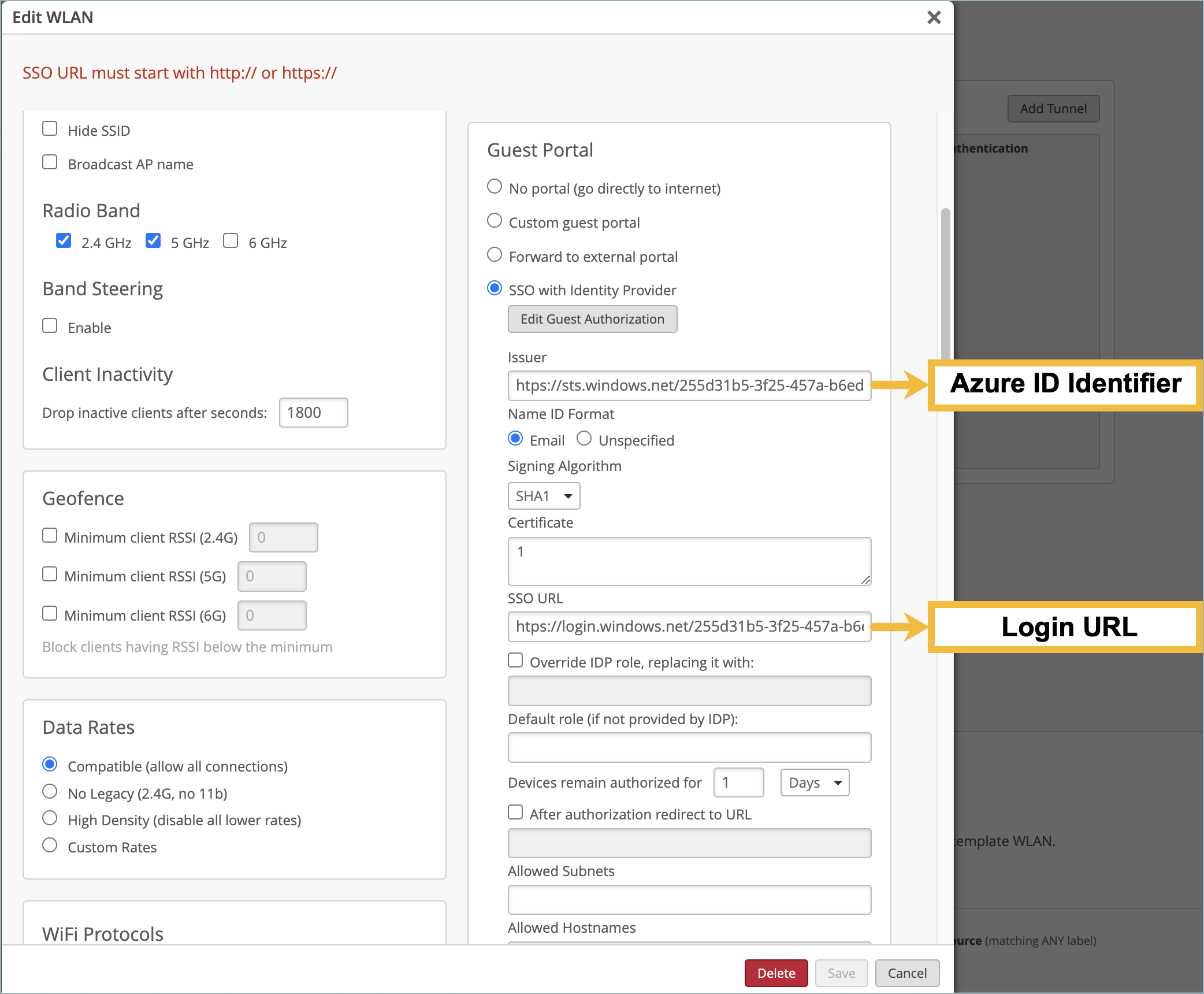
Copy and save the Microsoft Entra Identifier (Azure ID Identifier) and the Login URL.
-
Add Users or Groups and assign them to the application so that they will be able to authenticate via the SSO application.
If you need help adding a SAML application in Entra, consult your Microsoft support information. For example, consider this topic on the Microsoft site: How to Enable single sign-on for an enterprise application.
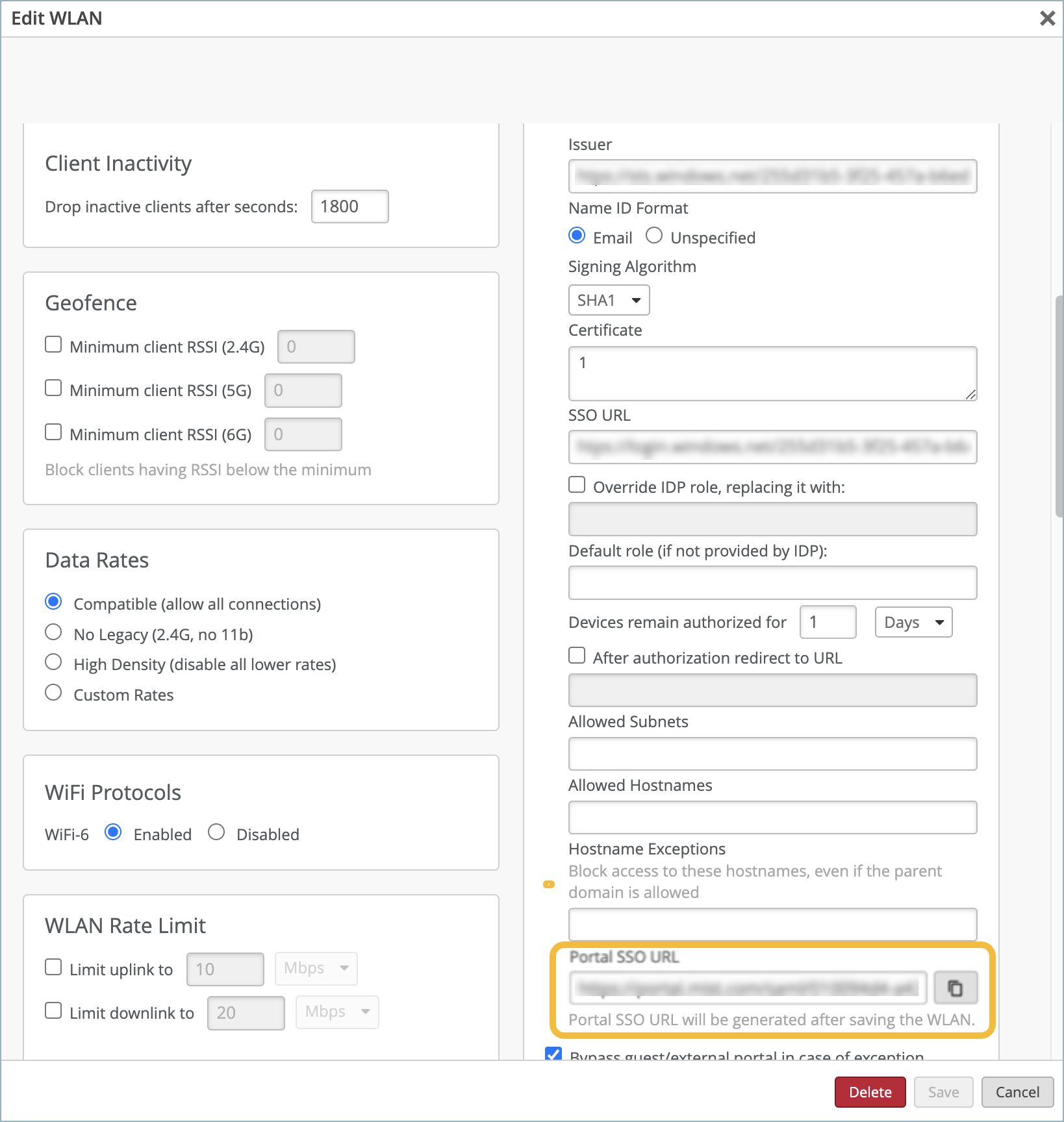
To set up your guest portal SSO with Azure: