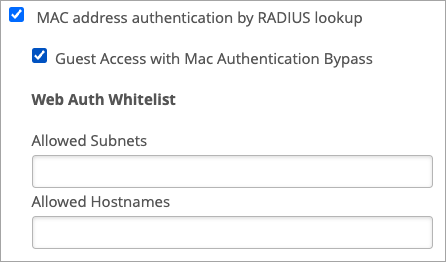
Guest Access Using RADIUS Server with MAC Authentication Bypass
Enable this option if you want to leverage RADIUS-based portals for guest access.
First get familiar with the flow of guest access using RADIUS server with MAC Authentication Bypass (MAB). Then configure your WLAN. Finally, do additional RADIUS configuration for authentication policies and authorization profiles.
Flow of Guest Access Using RADIUS Server with MAC Authentication Bypass
A WLAN is created in Juniper Mist with MAB being performed using RADIUS Lookup.
When a client associates to this WLAN, its MAC address is sent to the RADIUS server using an ACCESS_REQUEST.
The server looks for the MAC address in its database.
If the client is not found in the database, sends back an ACCESS_ACCEPT with a redirection URL to the Juniper Mist AP, and the flow continues with Step 4.
If the client is found in the database, the flow goes to Step 10.
The client is provided with limited access to the network which includes access to the BOOTP, DNS, and RADIUS server.
After the client receives an IP, the AP opens a web socket and listens to any HTTP traffic initiated from the client.
Traffic is intercepted and is responded with the redirect URL that was sent by RADIUS server.
The client is redirected to the specified URL. Based on your configured policy, it might be a sponsored portal, a self-registration portal, or a hotspot portal.
After the client provides the necessary info, the client’s MAC address is installed in the database and a CoA (Change of Authorization) request is issued to reauthorize the client.
Upon receiving the CoA request, the AP acknowledges the request and sends back the same ACCESS_REQUEST as in step 2.
The client is available in the RADIUS server database and is provided with an ACCESS-ACCEPT without any restrictions of URL-Redirect and the client has network connectivity based on your configured policies.
WLAN Configuration
RADIUS Configuration
Configure RADIUS policies and profiles to support the authentication flow.
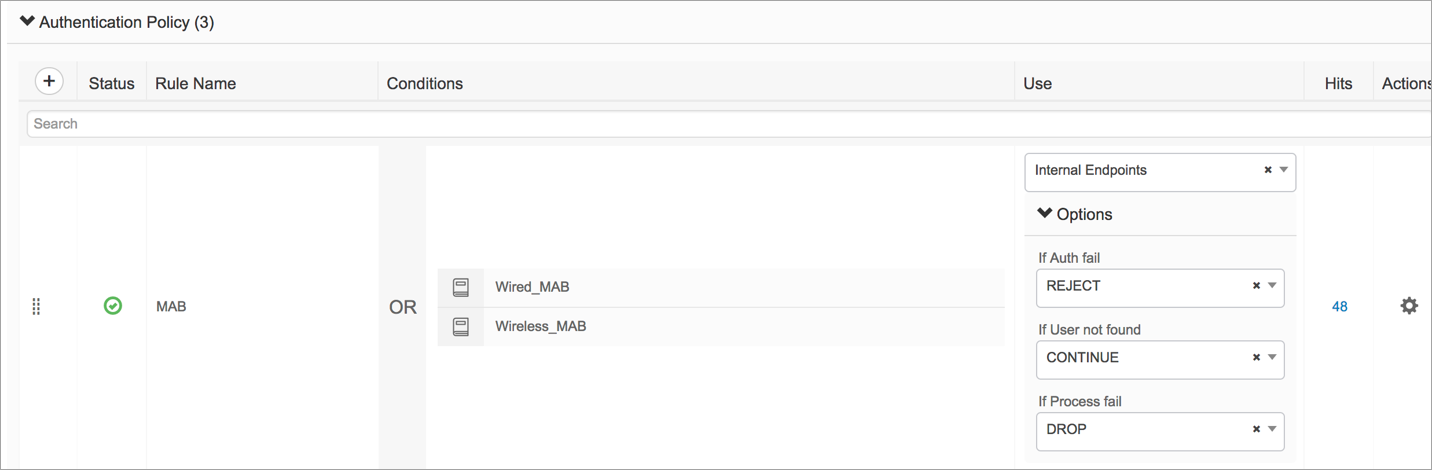
Authentication Policy—Configure an authentication policy to “continue” if the user is not found in the database. This allows the client to get an IP and be placed in the redirect state.
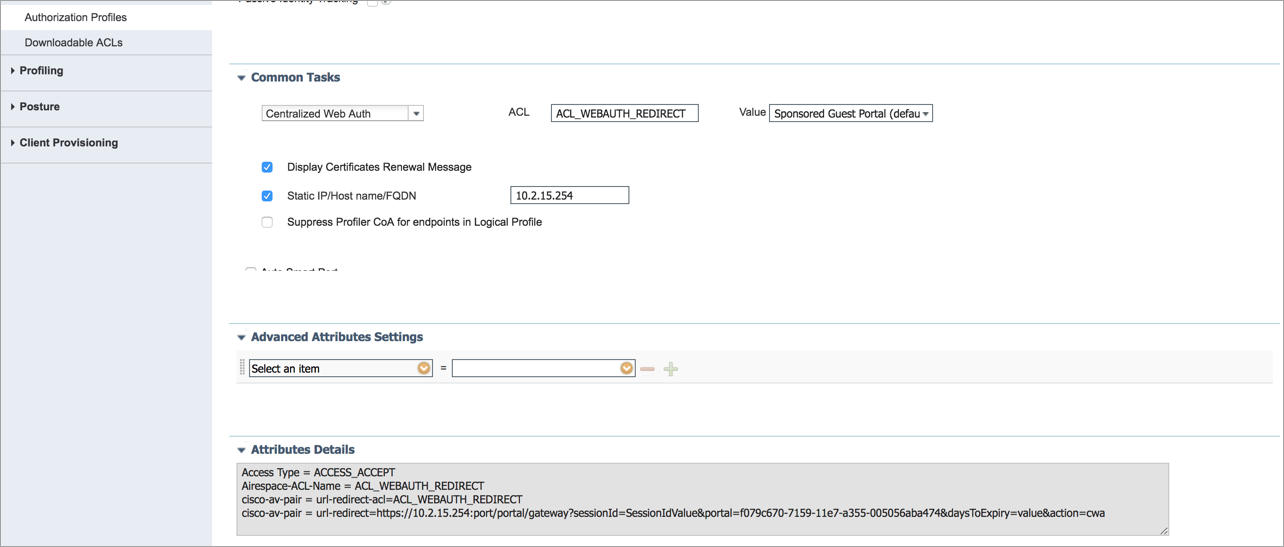
Authorization Policies: Configure two policies that will be hit during the process of the guest access flow.
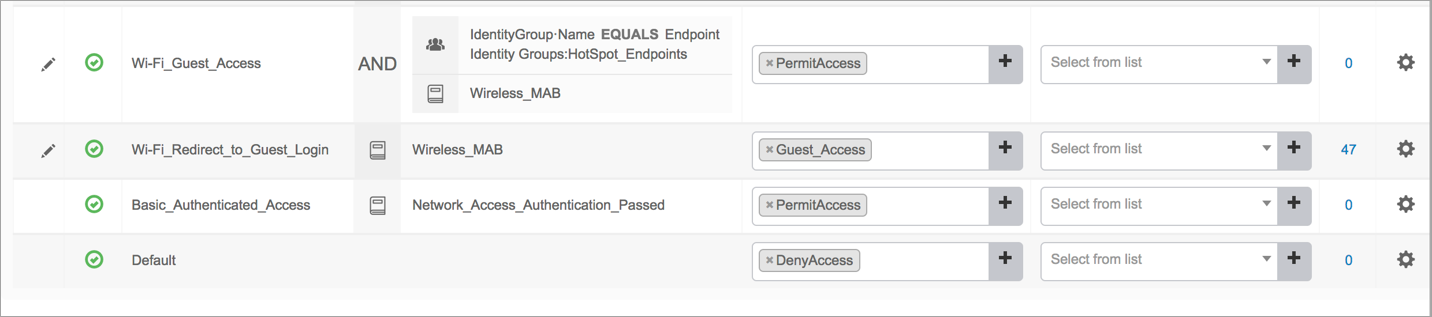
The first policy is Wifi_Redirect_to_Guest_Login, which applies when the RADIUS server receives the request. This policy provides partial access to the client. (See Steps 2-3 of the flow.)
The second policy is Wifi_Guest_Access, which applies upon successful completion of the CoA request. This policy provides the client with full access. (See Steps 9-10 of the flow.)
Authorization Profile: Configure a RADIUS authorization policy as shown in the example below. This policy provides the redirect URL for Steps 6-7 of the flow.