AAA Servers (Datacenter Blueprint)
AAA Servers Overview
AAA servers are used with interface policies. AAA servers include the following details:
| Parameter | Description |
|---|---|
| Label | To identify the AAA server |
| Server Type |
|
| Hostname | |
| Auth Ports | |
| Accounting Port | optional |
From the blueprint, navigate to Staged > Catalog > AAA Servers to go to the AAA servers catalog. You can create, clone, edit, and delete AAA servers.
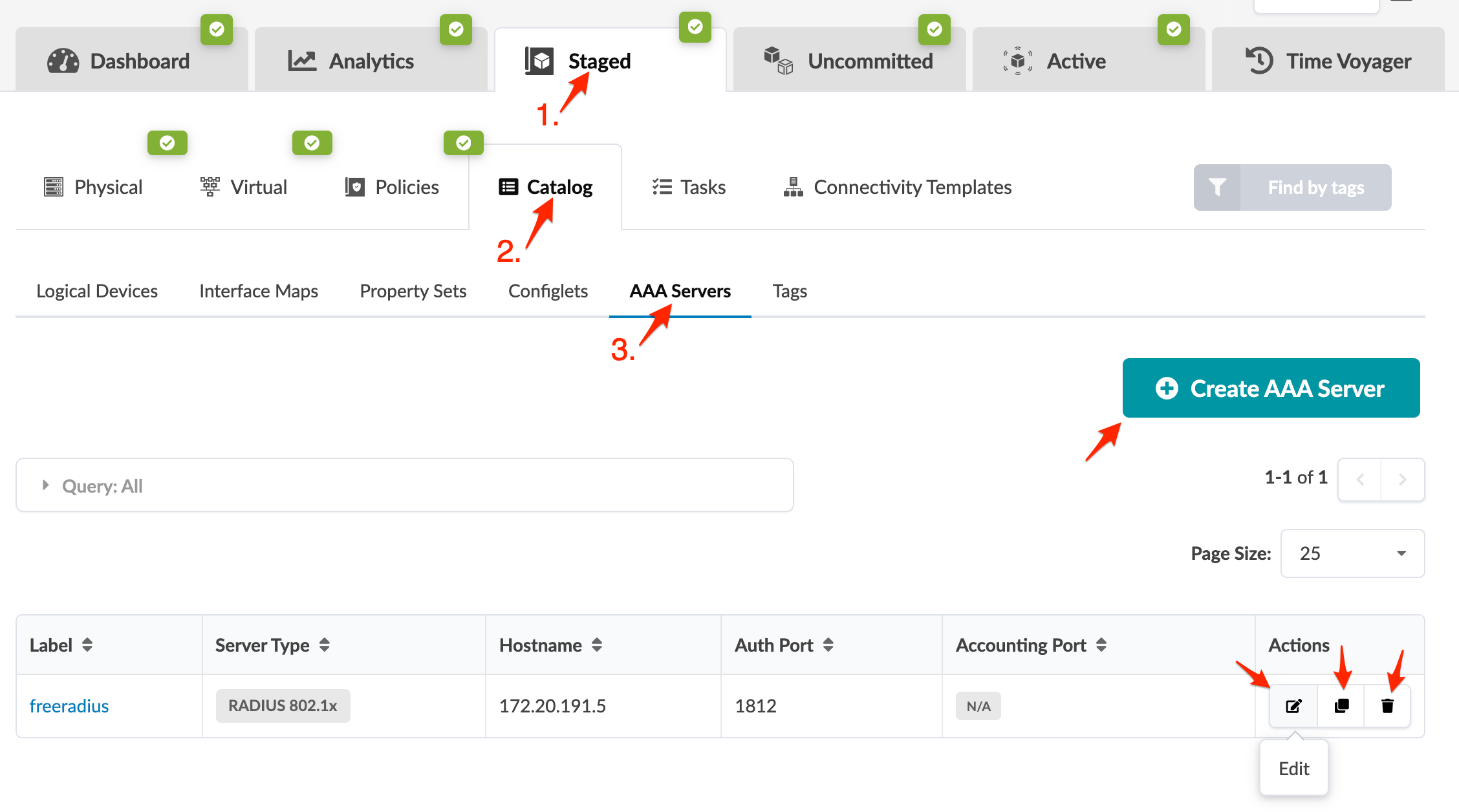
Create AAA Server
- From the blueprint, navigate to Staged > Catalog > AAA Servers and click Create AAA Server.
- Enter a label, select the server type (RADIUS 802.1x, RADIUS COA), enter a hostname, key, auth port, and (optional) accounting port.
- Click Create to stage the server and return to the table view.
Edit AAA Server
- From the blueprint, navigate to Staged > Catalog > AAA Servers and click the Edit button for the AAA server to edit.
- Make your changes, then click Update to stage the update and return to the table view.
Delete AAA Server
- From the blueprint, navigate to Staged > Catalog > AAA Servers and click the Delete button for the AAA server to delete.
- Click Delete to stage the deletion and return to the table view.
Configure AAA RADIUS Server
Configuring AAA RADIUS servers are external to Apstra software. The example below shows the files to configure for FreeRADIUS.
/etc/freeradius/clients.conf -- has credentials for each switch
client Arista-7280SR-48C6-1 {
shortname = Arista-7280SR-48C6-1
ipaddr = 172.20.191.10
secret = testing123
nastype = other
}/etc/freeradius/users -- has users and MAC addresses to authenticate. Tunnel-Private-Group-Id shows a dynamic VLAN ID, which is optional.
leaf1-server1 ClearText-Password := "password"
"52:54:00:37:d5:e1" Cleartext-Password := "52:54:00:37:d5:e1"
Tunnel-Type = VLAN,
Tunnel-Medium-Type = IEEE-802,
Tunnel-Private-Group-Id = "50"This example shows a simple credential; when you configure you may use any EAP method that both the client and RADIUS server support.
Configure Client Supplicant
Configuring client supplicant is external to Apstra software. The following is an example for wpa_supplicant.
/etc/wpa_supplicant/aos_wpa_supplicant.conf
# Ansible managed
ctrl_interface=/var/run/wpa_supplicant
# Default version is 0 - ensure we're using modern protocols.
eapol_version=2
# Don't scan for wifi.
ap_scan=0
# Hosts will be configured to authenticate with usernames that match their
# Slicer DUT name, configured in radius_server playbook.
network={
key_mgmt=IEEE8021X
eap=TTLS MD5
identity="leaf1-server1"
anonymous_identity="leaf1-server1"
password="password"
phase1="auth=MD5"
phase2="auth=PAP password=password"
eapol_flags=0
}